Security Protection Mechanisms Security File systems generally contain

















- Slides: 27

Security & Protection Mechanisms

Security • File systems generally contain information that is highly valuable to their users. • Protecting this information against unauthorized usage is therefore a major concern of all file systems. Ali Akbar Mohammadi 2

The Security Environment • Nature of the threats • Nature of intruders • Accidental data loss Ali Akbar Mohammadi 3

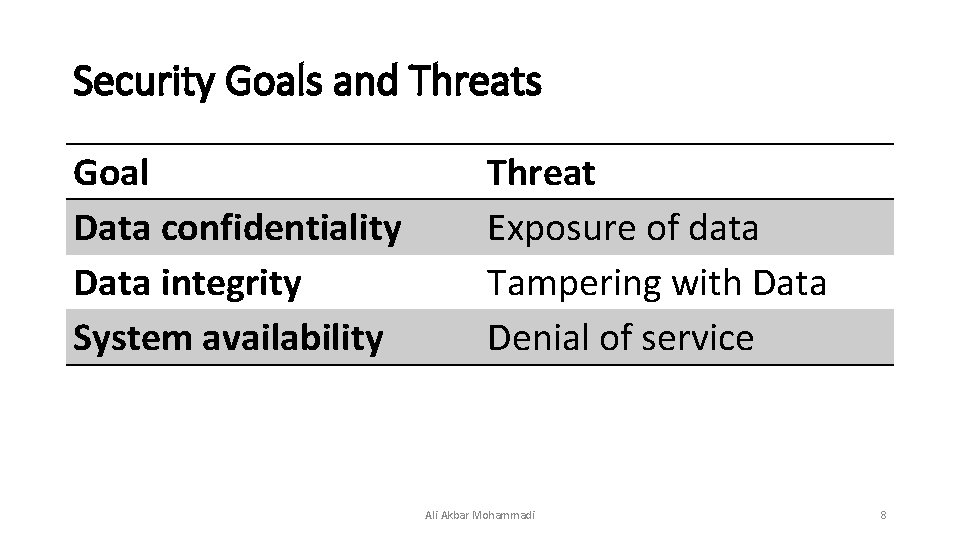
Threats • From a security perspective, computer systems have three general goals, with corresponding threats to them: • Data confidentiality • Data integrity • System availability Ali Akbar Mohammadi 4

- Data Confidentiality • Data confidentiality, is concerned with having secret data remain secret. More specifically, if the owner of some data has decided that these data are only to be made available to certain people and no others, the system should guarantee that release of the data to unauthorized people does not occur. As a bare minimum, the owner should be able to specify who can see what, and the system should enforce these specifications. Ali Akbar Mohammadi 5

-Data Integrity • Data integrity, means that unauthorized users should not be able to modify any data without the owner's permission. Data modification in this context includes not only changing the data, but also removing data and adding false data as well. If a system cannot guarantee that data deposited in it remain unchanged until the owner decides to change them, it is not worth much as an information system. Integrity is usually more important than confidentiality. Ali Akbar Mohammadi 6

-System Availability • system availability, means that nobody can disturb the system to make it unusable. • Such denial of service attacks are increasingly common. Ali Akbar Mohammadi 7

Security Goals and Threats Goal Data confidentiality Data integrity System availability Threat Exposure of data Tampering with Data Denial of service Ali Akbar Mohammadi 8

Privacy • Protecting individuals from misuse of information about them. Ali Akbar Mohammadi 9

Intruders • In the security literature, people who are nosing around places where they have no business being are called intruders or sometimes adversaries. • Intruders act in two different ways. • Passive intruders just want to read files they are not authorized to read. • Active intruders are more malicious; they want to make unauthorized changes. Ali Akbar Mohammadi 10

Malicious Programs • Another category of security pest is malicious programs, sometimes called malware. • In a sense, a writer of malware is also an intruder, often with high technical skills. • The difference between a conventional intruder and malware is that the former refers to a person who is personally trying to break into a system to cause damage whereas the latter is a program written by such a person and then released into the world. Ali Akbar Mohammadi 11

-Virus • The most well known kind of malware is the virus. Basically a virus is a piece of code that can reproduce itself by attaching a copy of itself to another program, analogous to how biological viruses reproduce. • The virus can do other things in addition to reproducing itself. For example, it can type a message, display an image on the screen, play music, or something else harmless. • Unfortunately, it can also modify, destroy, or steal files. Ali Akbar Mohammadi 12

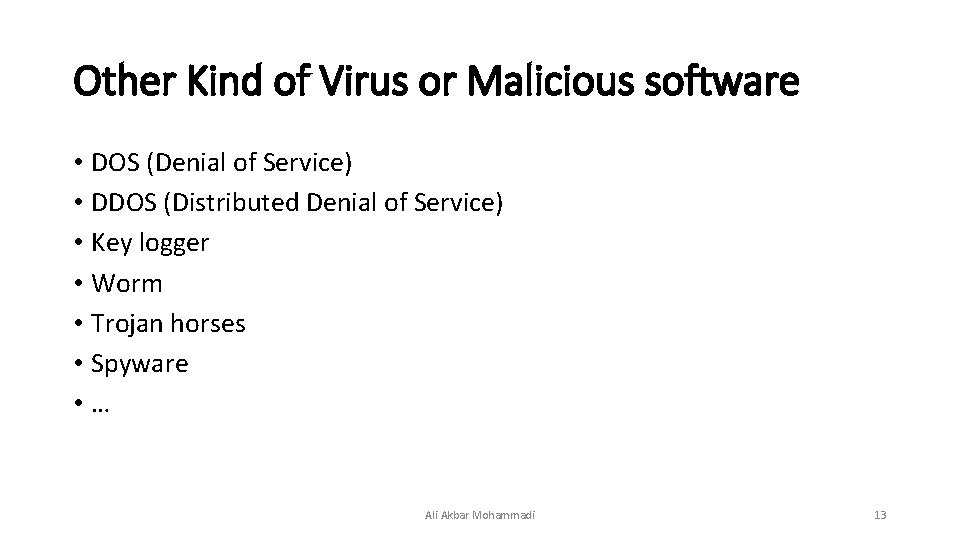
Other Kind of Virus or Malicious software • DOS (Denial of Service) • DDOS (Distributed Denial of Service) • Key logger • Worm • Trojan horses • Spyware • … Ali Akbar Mohammadi 13

Accidental Data Loss • Natural disasters: fires, floods, earthquakes, wars, riots, or rats gnawing tapes or CDs. • Hardware or software errors: CPU malfunctions, unreadable disks or tapes, telecommunication errors, program bugs. • Human errors: incorrect data entry, wrong tape or disk mounted, wrong program run, lost disk or tape, or some other mistake. • Solution? • Backups Ali Akbar Mohammadi 14

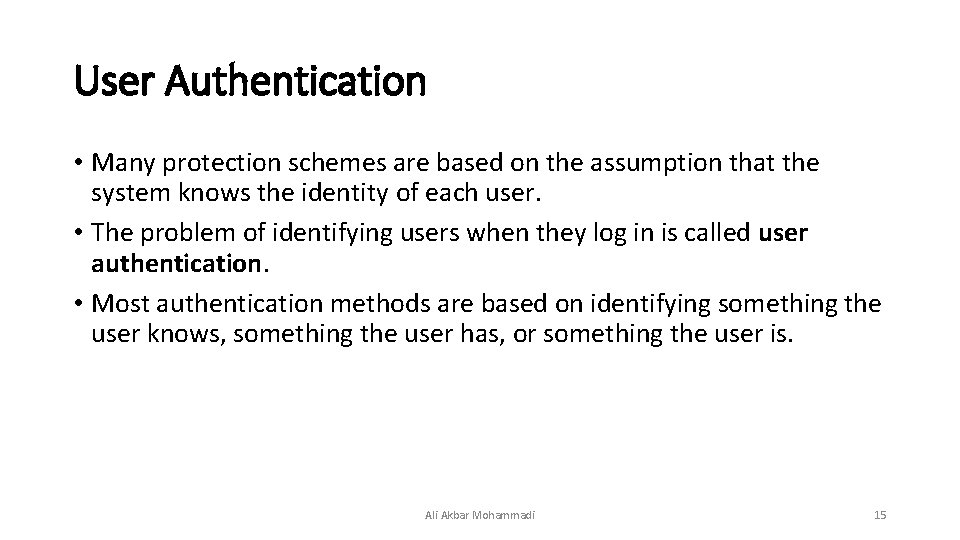
User Authentication • Many protection schemes are based on the assumption that the system knows the identity of each user. • The problem of identifying users when they log in is called user authentication. • Most authentication methods are based on identifying something the user knows, something the user has, or something the user is. Ali Akbar Mohammadi 15

Common User Authentication • Passwords • Physical Identification • Eye Scanning • Finger Print • Countermeasures Ali Akbar Mohammadi 16

Protection Mechanisms • Protection Domains • Access Control Lists • Capabilities • Covert Channels Ali Akbar Mohammadi 17

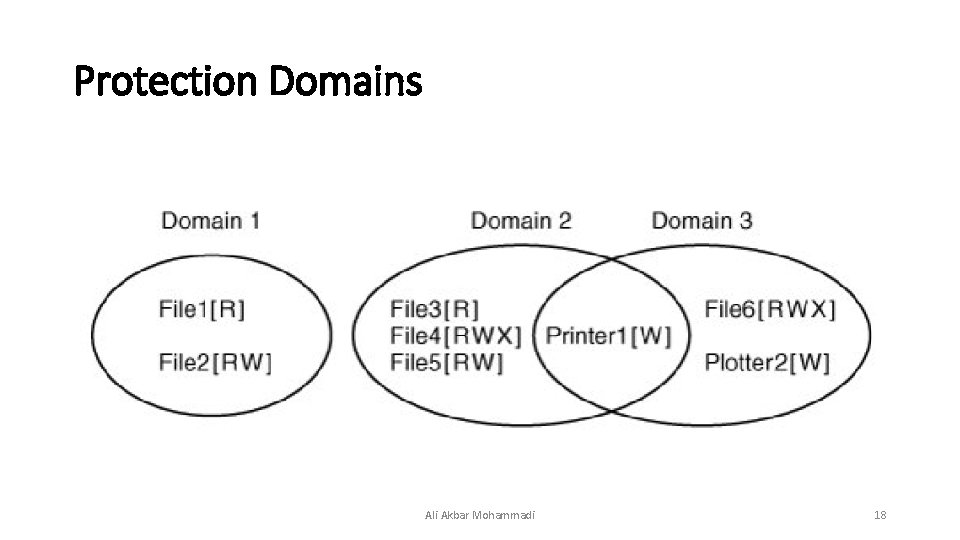
Protection Domains Ali Akbar Mohammadi 18

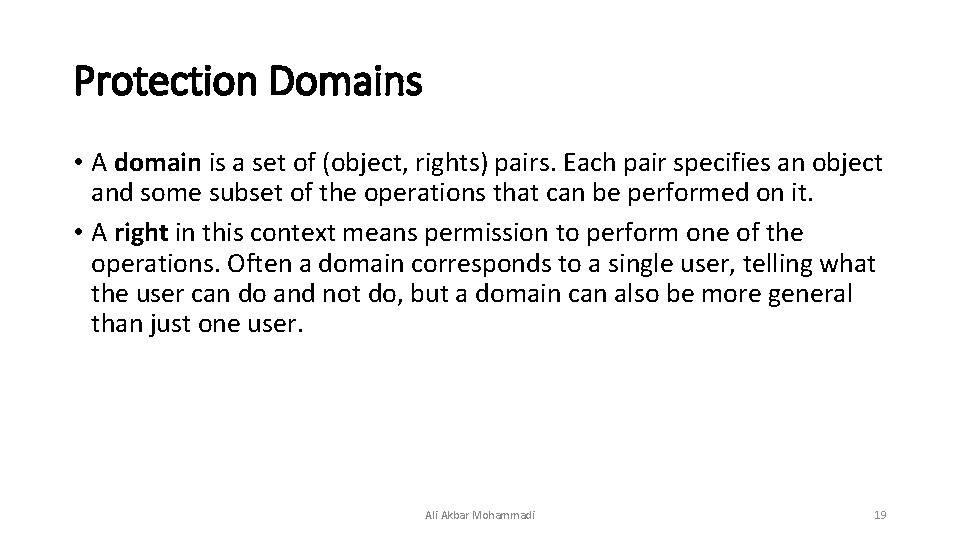
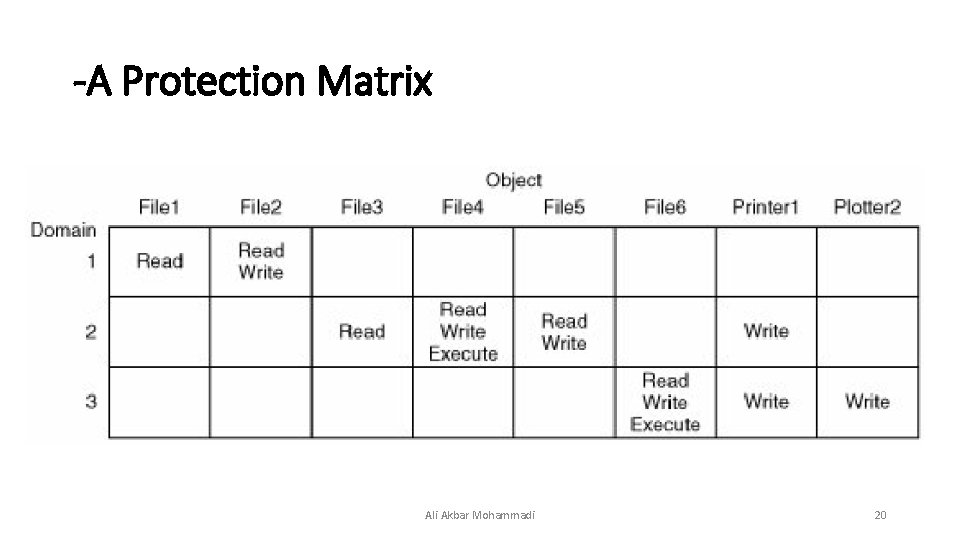
Protection Domains • A domain is a set of (object, rights) pairs. Each pair specifies an object and some subset of the operations that can be performed on it. • A right in this context means permission to perform one of the operations. Often a domain corresponds to a single user, telling what the user can do and not do, but a domain can also be more general than just one user. Ali Akbar Mohammadi 19

-A Protection Matrix Ali Akbar Mohammadi 20

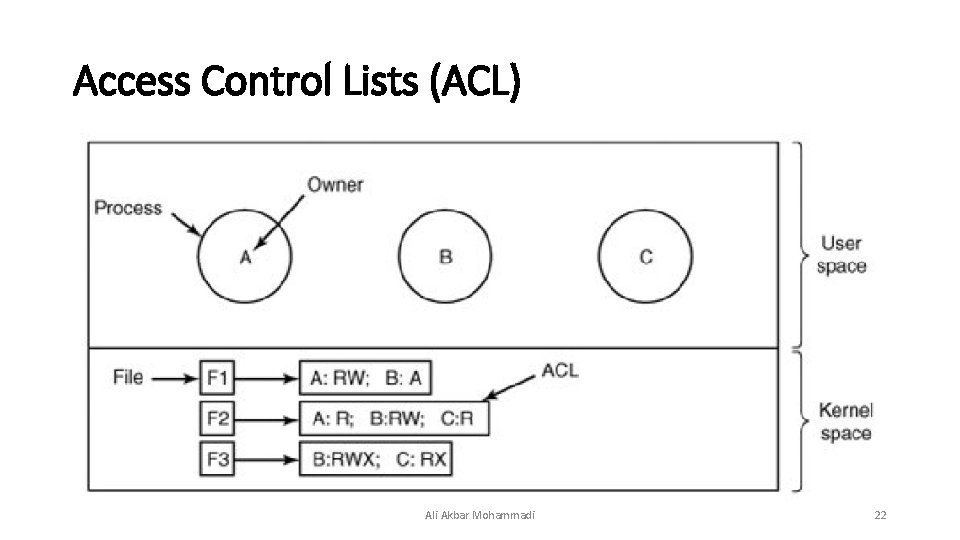
Access Control Lists (ACL) • This technique consists of associating with each object an (ordered) list containing all the domains that may access the object, and how. Ali Akbar Mohammadi 21

Access Control Lists (ACL) Ali Akbar Mohammadi 22

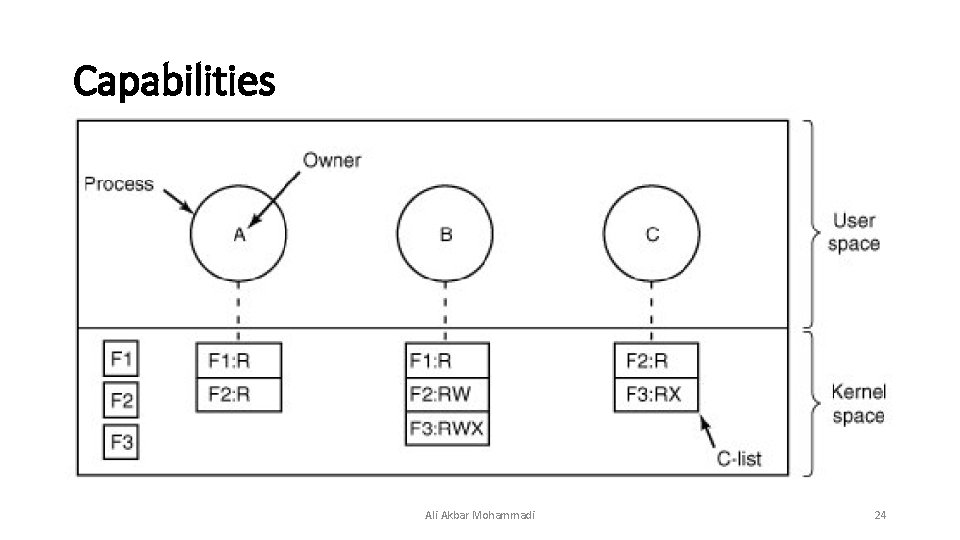
Capabilities • Associated with each process is a list of objects that may be accessed, along with an indication of which operations are permitted on each, in other words, its domain. This list is called a capability list or C-list and the individual items on it are called capabilities Ali Akbar Mohammadi 23

Capabilities Ali Akbar Mohammadi 24

Generic Rights • Copy capability: create a new capability for the same object. • Copy object: create a duplicate object with a new capability. • Remove capability: delete an entry from the C-list; object unaffected. • Destroy object: permanently remove an object and a capability. • … Ali Akbar Mohammadi 25

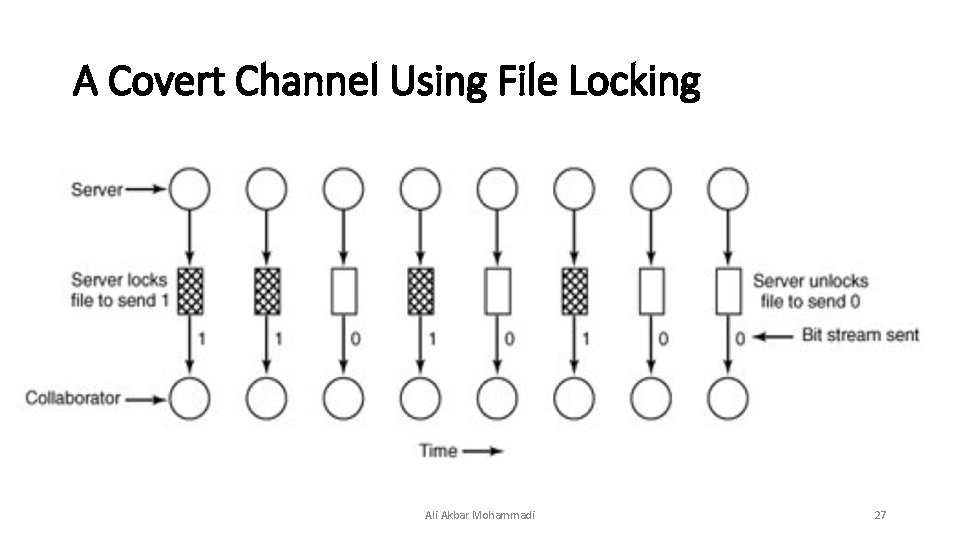
Covert Channels • It involves three processes on some protected machine. • The first process is the client, which wants some work performed by the second one, the server. The client and the server do not entirely trust each other. • The clients are worried that the server will secretly record their financial data • The third process is the collaborator, which is conspiring with the server to indeed steal the client's confidential data. The collaborator and server are typically owned by the same person. Ali Akbar Mohammadi 26

A Covert Channel Using File Locking Ali Akbar Mohammadi 27