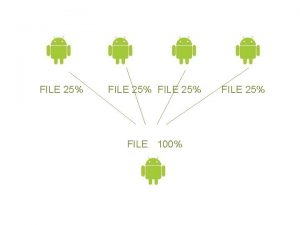
File Protection Mechanisms u AllNone Protection Lack of










- Slides: 12

File Protection Mechanisms u All-None Protection • Lack of trust • All or nothing • Timesharing issues • Complexity • File listings

File Protection Mechanisms u Group Protection • User cannot belong to two groups • Forces one person to be multiple users • Forces user to be put into all groups • Files can only be shared within groups

File Protection Mechanisms u Single Permissions • Password/Token for each file Can be lost u Inconvenient u Must be protected (if changed, must notify all users) u • Temporary Acquired Permission u UNIX’s set userid (suid)

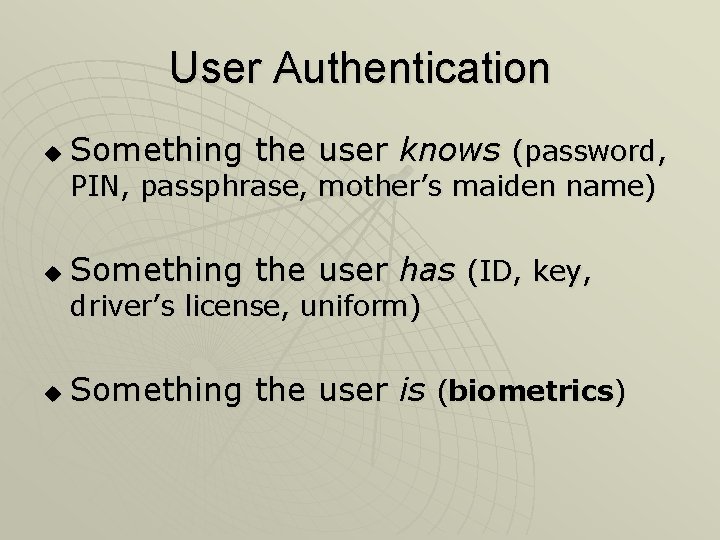
User Authentication u Something the user knows (password, PIN, passphrase, mother’s maiden name) u Something the user has (ID, key, driver’s license, uniform) u Something the user is (biometrics)

Use of Passwords Mutually agreed-upon code words, assumed known only to user and system u First line of defense u Loose-Lipped Systems u • WELCOME TO XYZ COMPUTING • ENTER USER ID: summers • INVALID USER NAME • ENTER USER ID:

Attack on Passwords u u Ask the user Search for the system list of passwords • • • Find a valid user ID Create a list of possible passwords (encrypt if needed) Rank the passwords from high to low probability Try each password If attempt fails, try again (don't exceed password lockout)

Attack on Passwords u Exhaustive Attack (brute-force) • • u 18, 278 passwords of 3 letters or less 1 password / millisecond would take 18 seconds (8 minutes for 4 letters, 3. 5 hours for 5 letters) Probable passwords (dictionary attack) • • 80, 000 word dictionary would take 80 seconds Expanded “dictionary”

Attack on Passwords u UK Study (http: //www. cnn. com/2002/TECH/ptech/03/13/dangerous. pass words/? related) • • • 50% passwords were family names Celebrities/soccer stars – 9% each Pets – 8% 10% reflect a fantasy Only 10% use cryptic combinations

Attack on Passwords u u u Look on desk… Try no password Try user ID Try user’s name Common words (password, private, secret) Short dictionary Complete English word list Common non-English dictionaries Dictionary with capitalization and substitutions (0 for o and 1 for i) Brute force (lowercase alphabet) Brute force (full character set)

Attack on Passwords u u Plaintext System Password List (MS Windows) Encrypted Password List – 1 -way (/etc/passwd) Shadow Password List (/etc/shadow) Salt – 12 -bit number formed from system time and process id; concatenated to password

Password Selection Criteria u u u u u Use characters other than A-Z Choose long passwords Avoid names and words Choose unlikely password Change password regularly (don’t reuse) Don’t write it down Don’t tell anyone http: //www. mit. edu/afs/sipb/project/doc/passwor ds/passwords. html One-time passwords

Authentication Should be slow (5 -10 seconds) u Should only allow a limited # of failures (e. g. 3) u Challenge-Response Systems u Impersonation of Login u Authentication Other than Passwords u
 File protection mechanisms
File protection mechanisms File protection mechanisms
File protection mechanisms File-file yang dibuat oleh user pada jenis file di linux
File-file yang dibuat oleh user pada jenis file di linux Community based child protection mechanisms
Community based child protection mechanisms File protection and security
File protection and security An html file is a text file containing small markup tags.
An html file is a text file containing small markup tags. Difference between logical file and physical file
Difference between logical file and physical file In a file-oriented information system, a transaction file
In a file-oriented information system, a transaction file File sharing management system
File sharing management system Remote file access in distributed file system
Remote file access in distributed file system Criminal addictive thinking
Criminal addictive thinking The lord is my shepherd
The lord is my shepherd Lack of cohesion of methods
Lack of cohesion of methods