Security in application integration Kari Nordstrm 09 08







- Slides: 23

Security in application integration Kari Nordström 09. 08. 2005

Topics l l Objectives Application integration – – l Information security – – l 2 Enterprise Application Integration – EAI Business-to-Business integration – B 2 Bi Basic concepts & ideas Network security Segmented networks Security of application integration systems Results 09. 08. 2005

Background and objectives of thesis l Find out the current level of security in the application integration systems of a certain company – l Make suggestions on improving the security level based on findings Implement improvements if possible l Supervisor: Docent Timo O. Korhonen l 3 Conduct security reviews with a panel of experts Security in application integration – Kari Nordström 09. 08. 2005

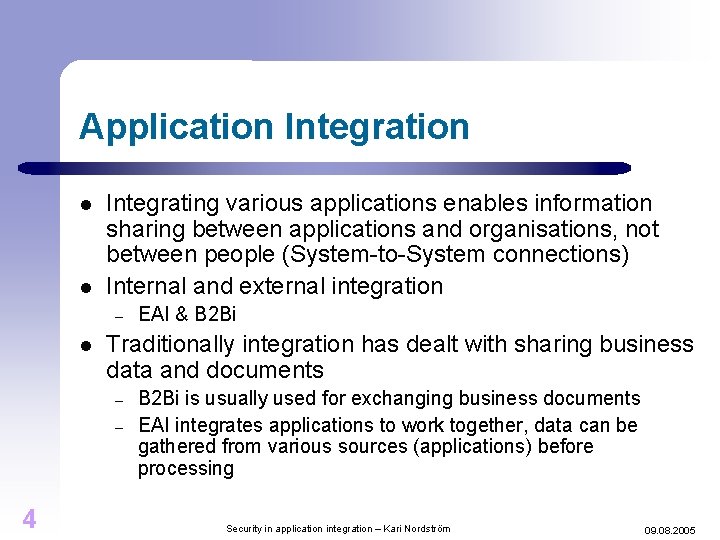
Application Integration l l Integrating various applications enables information sharing between applications and organisations, not between people (System-to-System connections) Internal and external integration – l Traditionally integration has dealt with sharing business data and documents – – 4 EAI & B 2 Bi is usually used for exchanging business documents EAI integrates applications to work together, data can be gathered from various sources (applications) before processing Security in application integration – Kari Nordström 09. 08. 2005

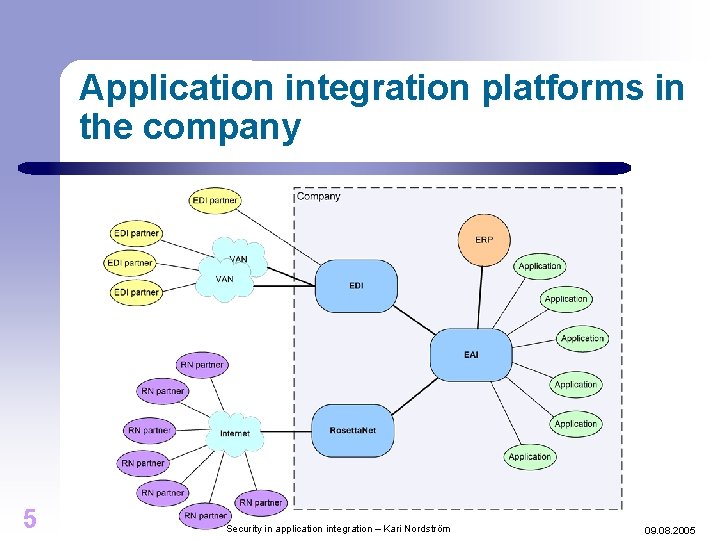
Application integration platforms in the company 5 Security in application integration – Kari Nordström 09. 08. 2005

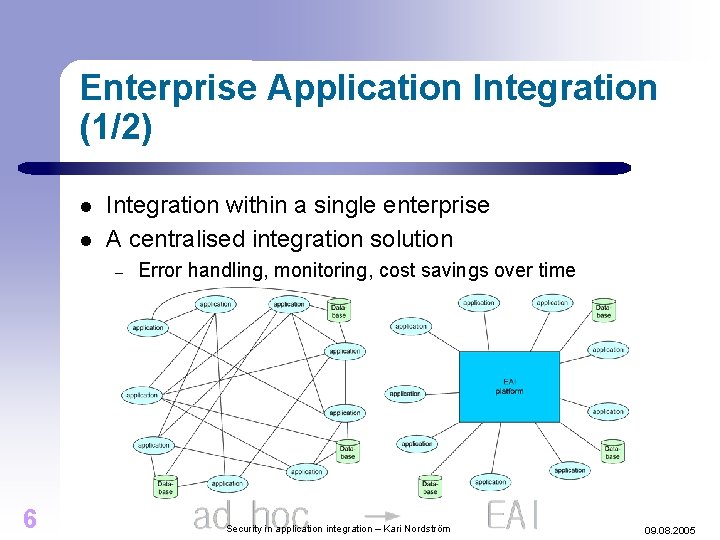
Enterprise Application Integration (1/2) l l Integration within a single enterprise A centralised integration solution – 6 Error handling, monitoring, cost savings over time Security in application integration – Kari Nordström 09. 08. 2005

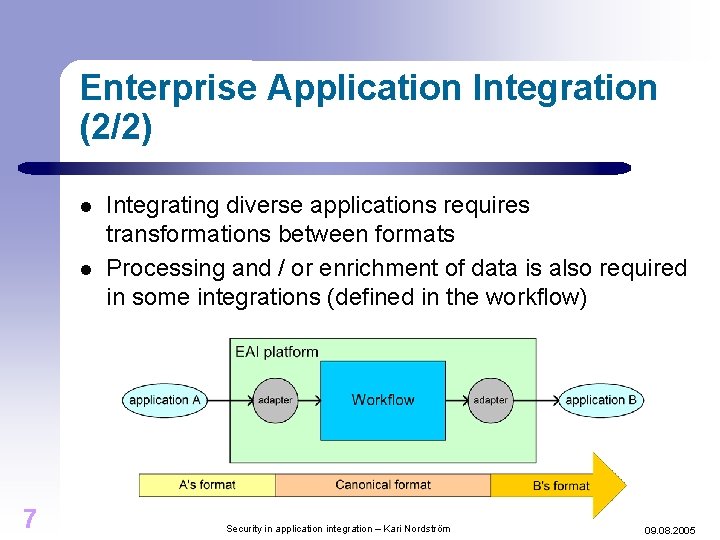
Enterprise Application Integration (2/2) l l 7 Integrating diverse applications requires transformations between formats Processing and / or enrichment of data is also required in some integrations (defined in the workflow) Security in application integration – Kari Nordström 09. 08. 2005

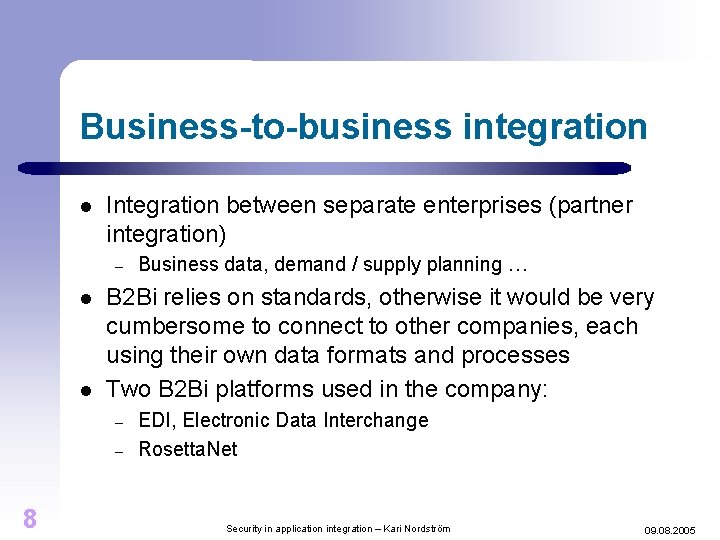
Business-to-business integration l Integration between separate enterprises (partner integration) – l l B 2 Bi relies on standards, otherwise it would be very cumbersome to connect to other companies, each using their own data formats and processes Two B 2 Bi platforms used in the company: – – 8 Business data, demand / supply planning … EDI, Electronic Data Interchange Rosetta. Net Security in application integration – Kari Nordström 09. 08. 2005

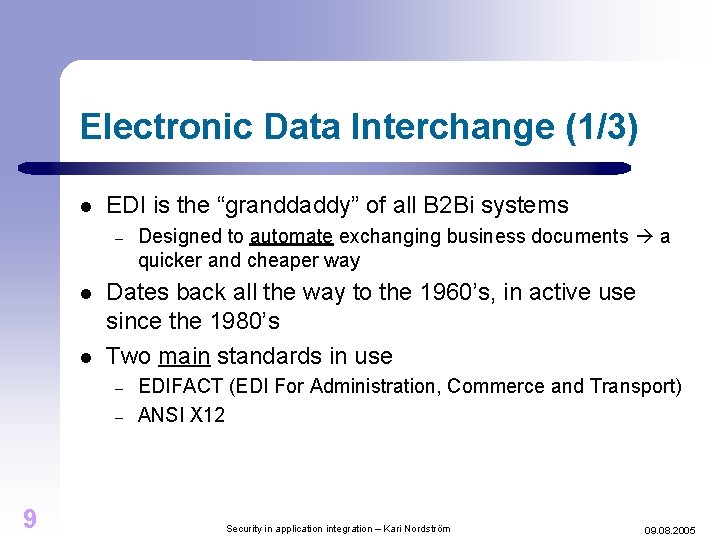
Electronic Data Interchange (1/3) l EDI is the “granddaddy” of all B 2 Bi systems – l l Dates back all the way to the 1960’s, in active use since the 1980’s Two main standards in use – – 9 Designed to automate exchanging business documents a quicker and cheaper way EDIFACT (EDI For Administration, Commerce and Transport) ANSI X 12 Security in application integration – Kari Nordström 09. 08. 2005

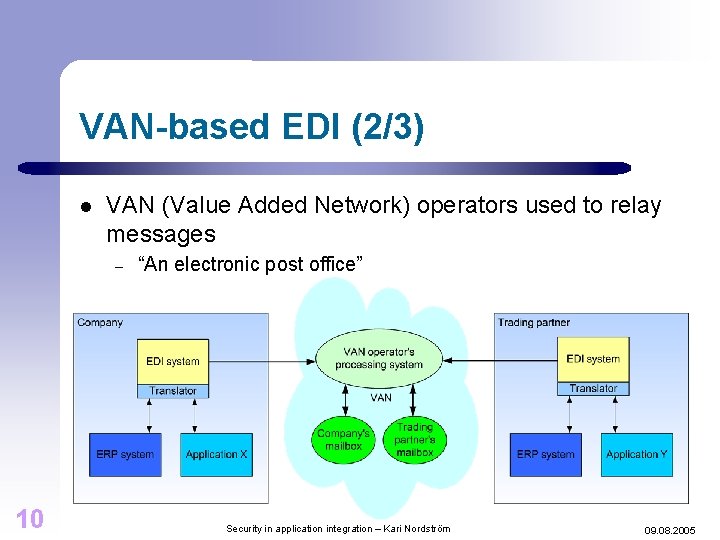
VAN-based EDI (2/3) l VAN (Value Added Network) operators used to relay messages – 10 “An electronic post office” Security in application integration – Kari Nordström 09. 08. 2005

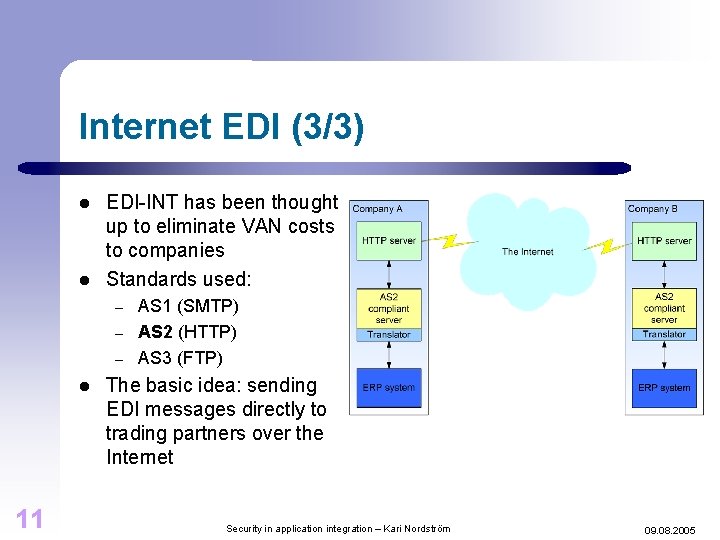
Internet EDI (3/3) l l EDI-INT has been thought up to eliminate VAN costs to companies Standards used: – – – l 11 AS 1 (SMTP) AS 2 (HTTP) AS 3 (FTP) The basic idea: sending EDI messages directly to trading partners over the Internet Security in application integration – Kari Nordström 09. 08. 2005

Rosetta. Net (1/2) l XML-based integration standard – l l l 12 Developed and maintained by the Rosetta. Net Consortium, a non-profit organisation of more than 500 corporations Integrations are based on Partner Interface Processes (PIP), which define how data is processed and the sequence of transactions between trading partners Rosetta. Net Implementation Framework (RNIF) describes the basic architecture (RNIF 1. 1 & 2. 0) Document Type Definition (DTD) describes the format of messages and data Security in application integration – Kari Nordström 09. 08. 2005

Rosetta. Net (2/2) l l Rosetta. Net aims in integrating the whole supply chain, not just passing business documents Marketed as more flexible and easier to implement than EDI – 13 Using VANs actually makes EDI more simple than Rosetta. Net where companies need to implement all connections themselves Security in application integration – Kari Nordström 09. 08. 2005

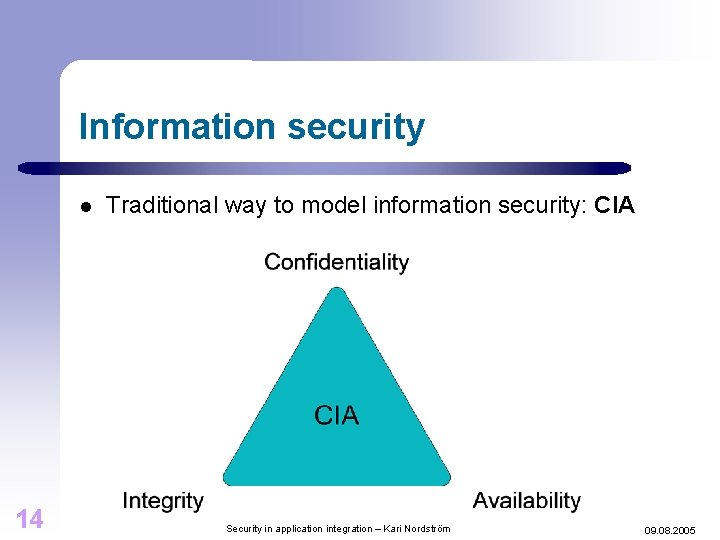
Information security l 14 Traditional way to model information security: CIA Security in application integration – Kari Nordström 09. 08. 2005

General security concepts l Authentication – l Making sure the user is who she claims to be Non-repudiation – Authorisation – l l Giving an authenticated user the right to do something l – Antivirus protection – Accounting All operations performed by users are logged l Protecting computers and network elements against malicious software Cryptography – 15 If a user performs a task, she can’t later deny having done so, the system also can’t later deny the user’s action Security in application integration – Kari Nordström Scrambling information in a way that only the correct recipient can decipher it 09. 08. 2005

Network security l l Host security vs. network security Systems are protected on the network level by controlling network traffic – l Typical misconception: network security = firewalls – 16 More cost-effective than host security Firewalls are a central part of network security, but there are numerous other things to consider (understanding the network architecture is key) Security in application integration – Kari Nordström 09. 08. 2005

A few key security strategies l Use multiple, diverse layers of security Give the lowest possible rights to users Deny everything that’s not explicitly allowed Use choke points to monitor traffic “KISS – Keep It Simple, Stupid” l Make users aware of security issues! l l – 17 The human factor is often the weakest link in security Security in application integration – Kari Nordström 09. 08. 2005

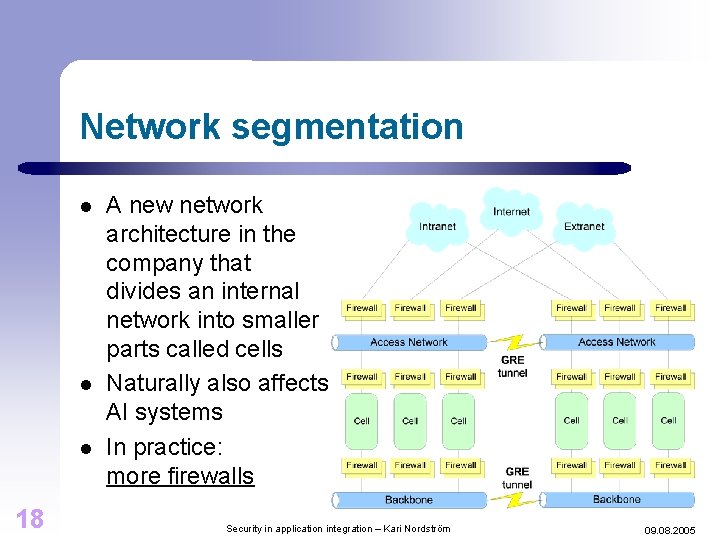
Network segmentation l l l 18 A new network architecture in the company that divides an internal network into smaller parts called cells Naturally also affects AI systems In practice: more firewalls Security in application integration – Kari Nordström 09. 08. 2005

Security requirements for application integration systems l l l An AI system is central and crucial in any network that has one Connected to many other systems attacker could gain access to virtually the whole network if e. g. the EAI system is hacked Availability requirements are very high – 19 Many other systems are dependant on integration systems Security in application integration – Kari Nordström 09. 08. 2005

Results of the security reviews l l Risk level is high for all three systems Security implementations do not match the current requirements – l Rosetta. Net was found more secure than EAI and EDI – l 20 Age, standardisation, segmented network EDI’s problem is the number of unknown factors – l Requirements have changed significantly from the 1990’s VAN operator responsible for most of the implementation EAI’s biggest problem is the lack of security standards Security in application integration – Kari Nordström 09. 08. 2005

EAI security improvements l l User management (no super-users) access control Certain authentication issues have been addressed – l l Client software used (fewer vulnerabilities) The migration to new architecture will bring major advancements in the security of the system – l 21 A component was not authenticating connections properly Border security Hosts have been hardened Security in application integration – Kari Nordström 09. 08. 2005

B 2 Bi security improvements l l It’s hard to fundamentally change security implementations in standardised systems User management has been improved vastly in EDI will also be migrated into new architecture (Rosetta. Net has already been migrated) RNIF specifies many security features, such as various forms of encryption, digital certificates and checksums – 22 They just weren’t always used in the company new policy Security in application integration – Kari Nordström 09. 08. 2005

Any questions or comments? If not, thank you! 23 Security in application integration – Kari Nordström 09. 08. 2005