Getting the most out of HP Fortify SCA








- Slides: 34

Getting the most out of HP Fortify SCA Peter Blay, HP Fortify Senior Technical Support Engineer Simon Corlett, HP Fortify Technical Account Manager © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Agenda 1. 2. 3. 4. 5. 2 Introduction The case studies Improving performance Streamlining the audit Wrap up © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

1. Introduction © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

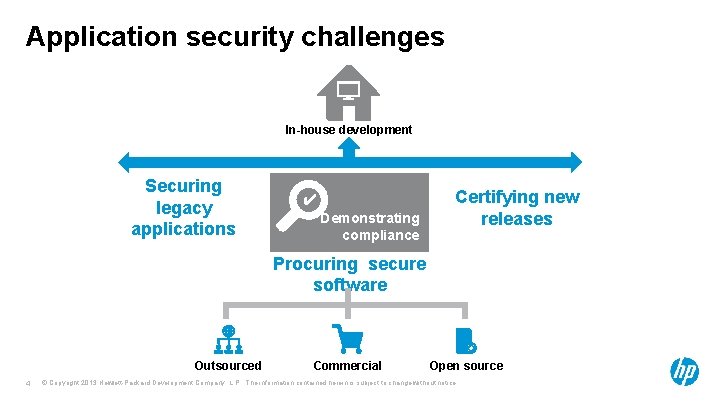
Application security challenges In-house development Securing legacy applications ✔ Demonstrating compliance Certifying new releases Procuring secure software Outsourced 4 Commercial Open source © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

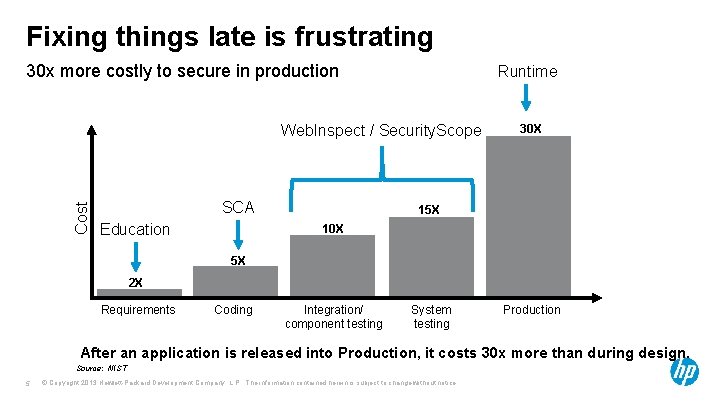
Fixing things late is frustrating 30 x more costly to secure in production Runtime Cost Web. Inspect / Security. Scope SCA Education 30 X 15 X 10 X 5 X 2 X Requirements Coding Integration/ component testing System testing Production After an application is released into Production, it costs 30 x more than during design. Source: NIST 5 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

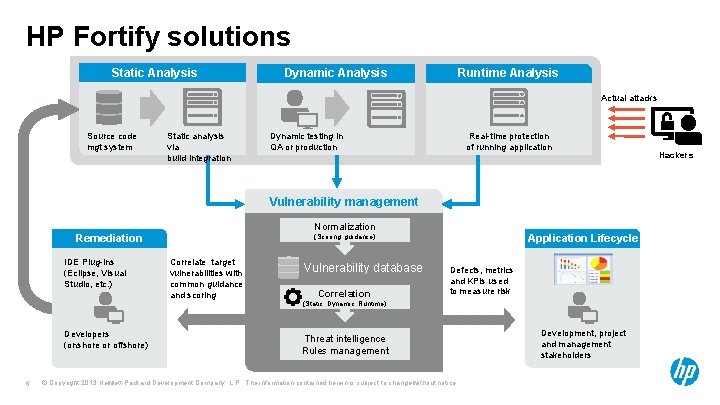
HP Fortify solutions Static Analysis Dynamic Analysis Runtime Analysis Actual attacks Source code mgt system Static analysis via build integration Dynamic testing in QA or production Real-time protection of running application Vulnerability management Normalization Remediation IDE Plug-ins (Eclipse, Visual Studio, etc. ) Application Lifecycle (Scoring, guidance) Correlate target vulnerabilities with common guidance and scoring Vulnerability database Correlation Defects, metrics and KPIs used to measure risk (Static, Dynamic, Runtime) Developers (onshore or offshore) 6 Threat intelligence Rules management © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Development, project and management stakeholders Hackers

2. The case studies © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

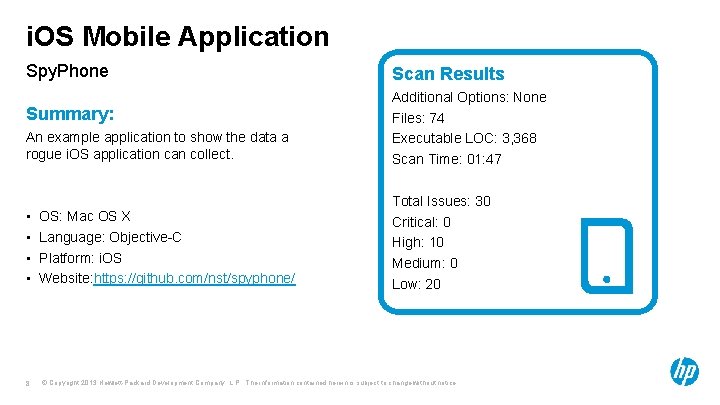
i. OS Mobile Application Spy. Phone Scan Results An example application to show the data a rogue i. OS application can collect. Additional Options: None Files: 74 Executable LOC: 3, 368 Scan Time: 01: 47 • • Total Issues: 30 Critical: 0 High: 10 Medium: 0 Low: 20 Summary: 8 OS: Mac OS X Language: Objective-C Platform: i. OS Website: https: //github. com/nst/spyphone/ © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

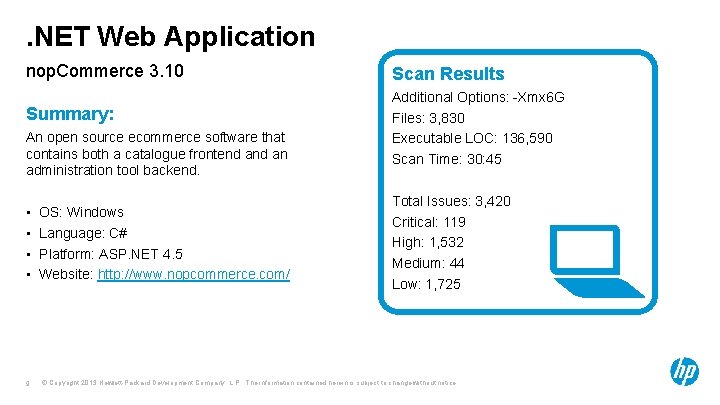
. NET Web Application nop. Commerce 3. 10 Summary: An open source ecommerce software that contains both a catalogue frontend an administration tool backend. • • 9 OS: Windows Language: C# Platform: ASP. NET 4. 5 Website: http: //www. nopcommerce. com/ Scan Results Additional Options: -Xmx 6 G Files: 3, 830 Executable LOC: 136, 590 Scan Time: 30: 45 Total Issues: 3, 420 Critical: 119 High: 1, 532 Medium: 44 Low: 1, 725 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

3. Improving results © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

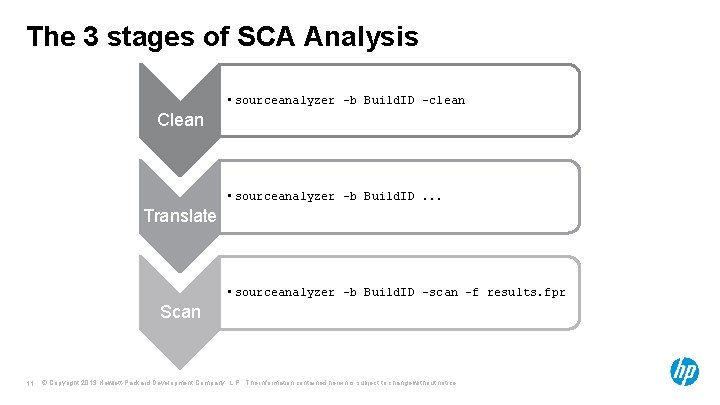
The 3 stages of SCA Analysis • sourceanalyzer –b Build. ID -clean Clean • sourceanalyzer –b Build. ID. . . Translate • sourceanalyzer –b Build. ID -scan -f results. fpr Scan 11 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

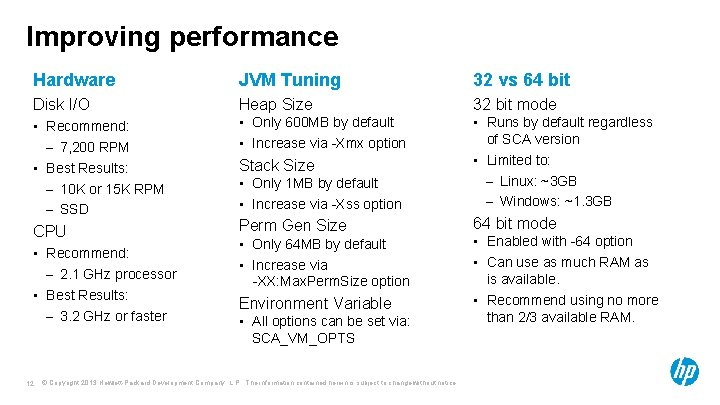
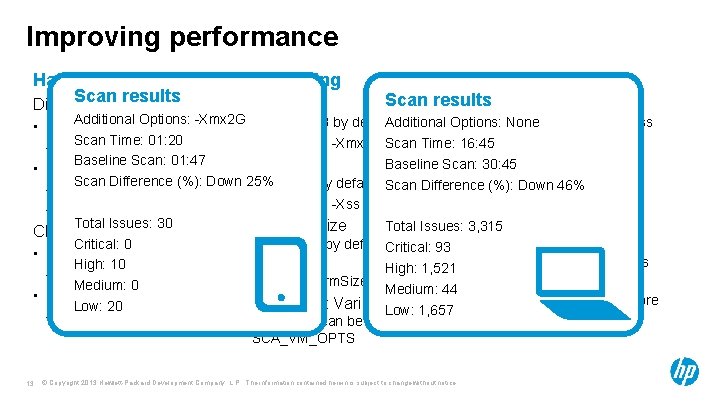
Improving performance Hardware JVM Tuning 32 vs 64 bit Disk I/O Heap Size 32 bit mode • Recommend: – 7, 200 RPM • Best Results: – 10 K or 15 K RPM – SSD • Only 600 MB by default • Increase via -Xmx option • Only 1 MB by default • Increase via -Xss option • Runs by default regardless of SCA version • Limited to: – Linux: ~3 GB – Windows: ~1. 3 GB Perm Gen Size 64 bit mode CPU • Recommend: – 2. 1 GHz processor • Best Results: – 3. 2 GHz or faster 12 Stack Size • Only 64 MB by default • Increase via -XX: Max. Perm. Size option Environment Variable • All options can be set via: SCA_VM_OPTS © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. • Enabled with -64 option • Can use as much RAM as is available. • Recommend using no more than 2/3 available RAM.

Improving performance Hardware Scan results Disk I/O JVM Tuning Heap Size 32 vs 64 bit Scan results 32 bit mode Additional Options: -Xmx 2 G • Runs by default regardless • Only 600 MB by default Additional Options: None • Recommend: of SCA version Scan Time: 01: 20 • Increase via -Xmx option Scan Time: 16: 45 – 7, 200 RPM Limited to: Baseline Scan: 01: 47 Baseline Scan: • 30: 45 Stack Size • Best Results: Linux: ~3 GB Scan Difference (%): Down • 25% Only 1 MB by default Scan Difference –(%): Down 46% – 10 K or 15 K RPM – Windows: ~1. 3 GB • Increase via -Xss option – SSD Total Issues: 30 64 bit mode Perm Gen Size Total Issues: 3, 315 CPU • Enabled with -64 option Critical: 0 • Only 64 MB by default. Critical: 93 • Recommend: High: 10 • Increase via High: 1, 521 • Can use as much RAM as – 2. 1 GHz processor is available. -XX: Max. Perm. Size option Medium: 0 Medium: 44 • Best Results: Environment Variable. Low: 1, 657 • Recommend using no more Low: 20 – 3. 2 GHz or faster than 2/3 available RAM. • All options can be set via: SCA_VM_OPTS 13 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

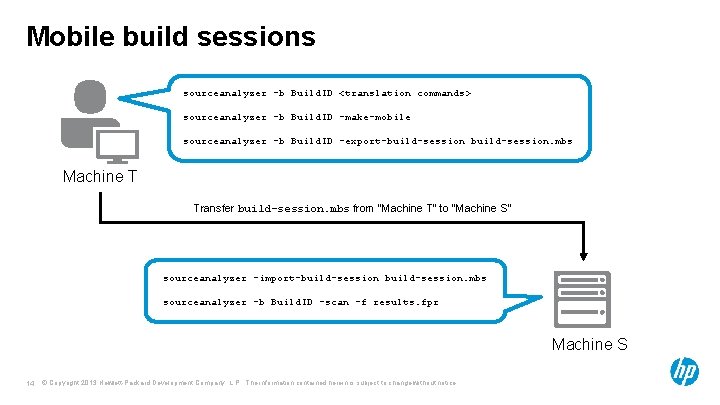
Mobile build sessions sourceanalyzer -b Build. ID <translation commands> sourceanalyzer -b Build. ID -make-mobile sourceanalyzer -b Build. ID -export-build-session. mbs Machine T Transfer build-session. mbs from “Machine T” to “Machine S” sourceanalyzer -import-build-session. mbs sourceanalyzer -b Build. ID -scan -f results. fpr Machine S 14 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

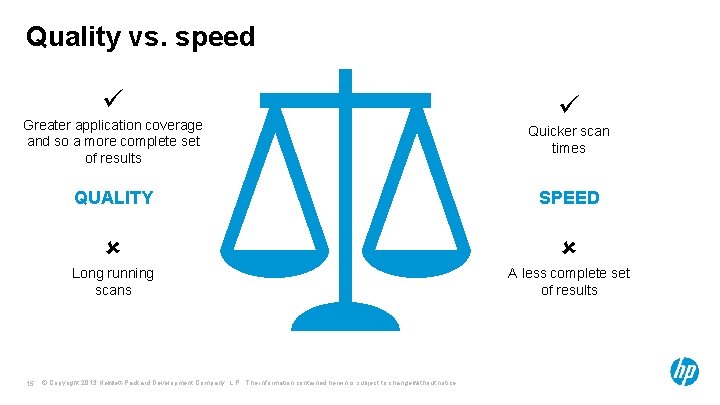
Quality vs. speed Greater application coverage and so a more complete set of results Quicker scan times QUALITY SPEED Long running scans A less complete set of results 15 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

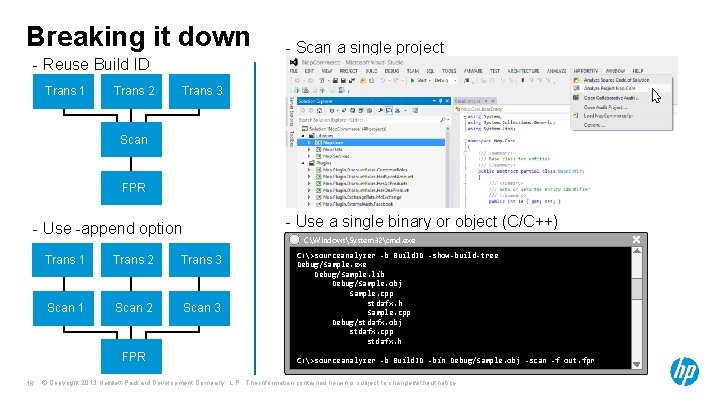
Breaking it down - Reuse Build ID Trans 1 Trans 2 - Scan a single project Trans 3 Scan FPR - Use a single binary or object (C/C++) - Use -append option Trans 1 Trans 2 Trans 3 Scan 1 Scan 2 Scan 3 FPR 16 C: WindowsSystem 32cmd. exe C: >sourceanalyzer -b Build. ID -show-build-tree Debug/Sample. exe Debug/Sample. lib Debug/Sample. obj Sample. cpp stdafx. h Sample. cpp Debug/stdafx. obj stdafx. cpp stdafx. h C: >sourceanalyzer -b Build. ID -bin Debug/Sample. obj -scan -f out. fpr © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

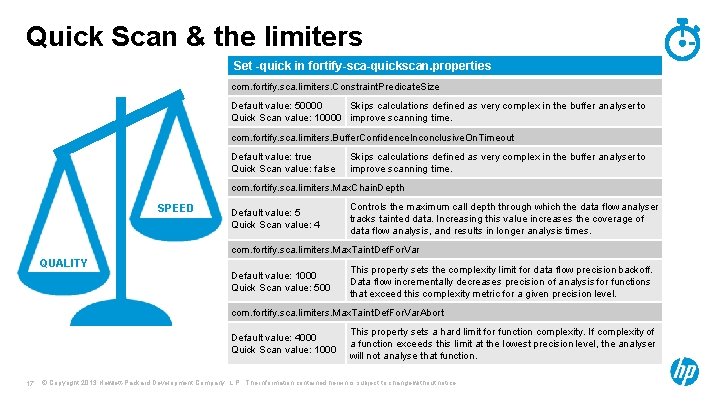
Quick Scan & the limiters Set -quick in fortify-sca-quickscan. properties com. fortify. sca. limiters. Constraint. Predicate. Size Default value: 50000 Skips calculations defined as very complex in the buffer analyser to Quick Scan value: 10000 improve scanning time. com. fortify. sca. limiters. Buffer. Confidence. Inconclusive. On. Timeout Default value: true Quick Scan value: false Skips calculations defined as very complex in the buffer analyser to improve scanning time. com. fortify. sca. limiters. Max. Chain. Depth SPEED Default value: 5 Quick Scan value: 4 Controls the maximum call depth through which the data flow analyser tracks tainted data. Increasing this value increases the coverage of data flow analysis, and results in longer analysis times. com. fortify. sca. limiters. Max. Taint. Def. For. Var QUALITY Default value: 1000 Quick Scan value: 500 This property sets the complexity limit for data flow precision backoff. Data flow incrementally decreases precision of analysis for functions that exceed this complexity metric for a given precision level. com. fortify. sca. limiters. Max. Taint. Def. For. Var. Abort Default value: 4000 Quick Scan value: 1000 17 This property sets a hard limit for function complexity. If complexity of a function exceeds this limit at the lowest precision level, the analyser will not analyse that function. © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

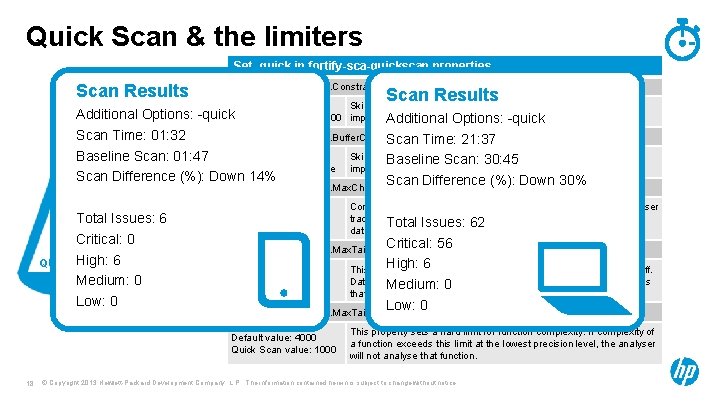
Quick Scan & the limiters Set -quick in fortify-sca-quickscan. properties Scan Results com. fortify. sca. limiters. Constraint. Predicate. Size Scan Results Default value: 50000 Skips calculations defined as very complex in the buffer analyser to -quick. Quick Scan value: 10000 improve Additional scanning time. Options: -quick Additional Options: Scan Time: 01: 32 com. fortify. sca. limiters. Buffer. Confidence. Inconclusive. On. Timeout Scan Time: 21: 37 Default value: true Skips calculations defined as very complex in the buffer analyser to Baseline Scan: 01: 47 Baseline Scan: 30: 45 Quick Scan value: false improve scanning time. Scan Difference (%): Down 14% Scan Difference (%): Down 30% com. fortify. sca. limiters. Max. Chain. Depth SPEED Total Issues: 6 Critical: 0 High: 6 QUALITY Medium: 0 Low: 0 Default value: 5 Quick Scan value: 4 Critical: 56 High: 6 the complexity limit for data flow precision backoff. This property sets Default value: 1000 Data flow. Medium: incrementally 0 decreases precision of analysis for functions Quick Scan value: 500 that exceed this complexity metric for a given precision level. Low: 0 com. fortify. sca. limiters. Max. Taint. Def. For. Var. Abort com. fortify. sca. limiters. Max. Taint. Def. For. Var Default value: 4000 Quick Scan value: 1000 18 Controls the maximum call depth through which the data flow analyser tracks tainted Increasing Totaldata. Issues: 62 this value increases the coverage of data flow analysis, and results in longer analysis times. This property sets a hard limit for function complexity. If complexity of a function exceeds this limit at the lowest precision level, the analyser will not analyse that function. © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

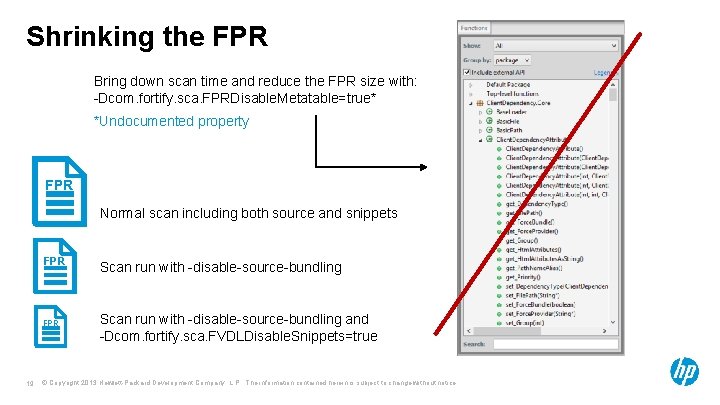
Shrinking the FPR Bring down scan time and reduce the FPR size with: -Dcom. fortify. sca. FPRDisable. Metatable=true* *Undocumented property FPR Normal scan including both source and snippets FPR 19 Scan run with -disable-source-bundling and -Dcom. fortify. sca. FVDLDisable. Snippets=true © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

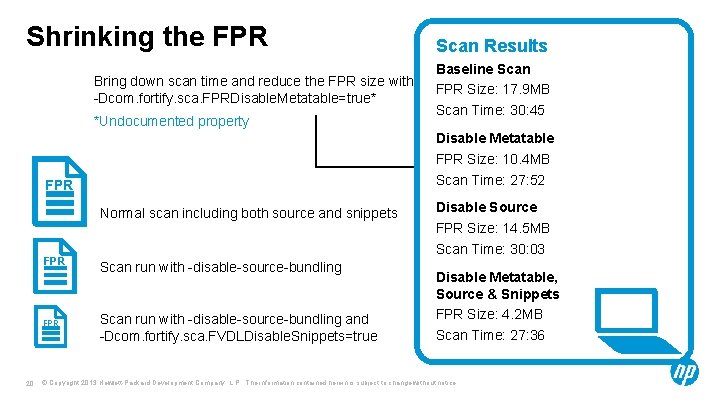
Shrinking the FPR Bring down scan time and reduce the FPR size with: -Dcom. fortify. sca. FPRDisable. Metatable=true* *Undocumented property Normal scan including both source and snippets FPR 20 Baseline Scan FPR Size: 17. 9 MB Scan Time: 30: 45 Disable Metatable FPR Size: 10. 4 MB Scan Time: 27: 52 FPR Scan Results Scan run with -disable-source-bundling and -Dcom. fortify. sca. FVDLDisable. Snippets=true Disable Source FPR Size: 14. 5 MB Scan Time: 30: 03 Disable Metatable, Source & Snippets FPR Size: 4. 2 MB Scan Time: 27: 36 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

4. Streamlining the audit © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Project templates 22 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

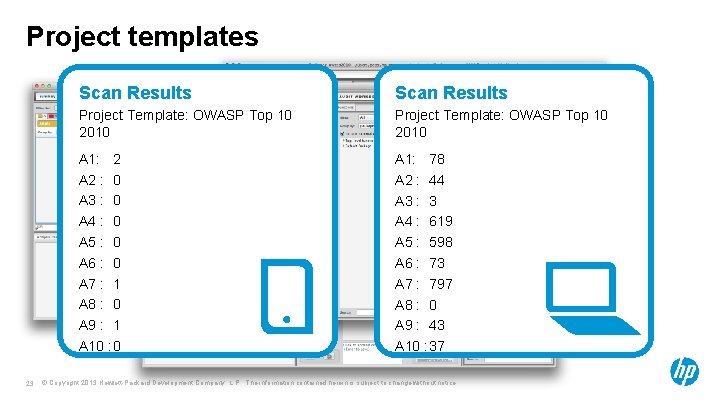
Project templates 23 Scan Results Project Template: OWASP Top 10 2010 A 1: 2 A 2 : 0 A 3 : 0 A 4 : 0 A 5 : 0 A 6 : 0 A 7 : 1 A 8 : 0 A 9 : 1 A 10 : 0 A 1: 78 A 2 : 44 A 3 : 3 A 4 : 619 A 5 : 598 A 6 : 73 A 7 : 797 A 8 : 0 A 9 : 43 A 10 : 37 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Metadata: map issues to compliance obligations Security programs benchmarking against standards • Map compliance post-scan • • Internal security standards External standards: CWE, NIST 800 -53, STIG, internal company standards, etc. • Easier to support new standards • Continually up to date by rules Issues carry more weight: You have a cross-site scripting violation on checkout. php: 72 24 Vs. Your application violates <standard> because of the cross-site scripting on checkout. php: 72 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

You can and should add your own mappings Map to your internal compliance standards. • • HP Fortify maintains base. Add new compliance mappings. Extend existing mappings. Plain-text example: CWE. Easier to add & update mappings. Easier to create & update reports. Use the base as an example, add your own. Screenshot: Notepad++ editing the XML mapping. 25 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

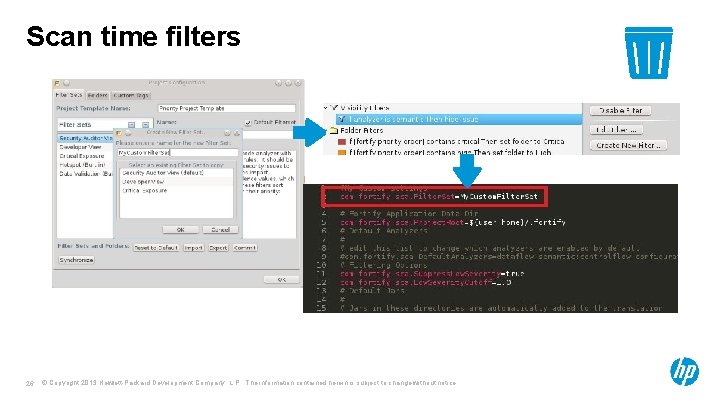
Scan time filters 26 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Collaborative audit & bug management 27 • Extra functionality • Native speed not reliant on server hardware & load • Not so reliant on uptime • Full source • More customizable experience • Native and collaborative bug tracker plugins © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

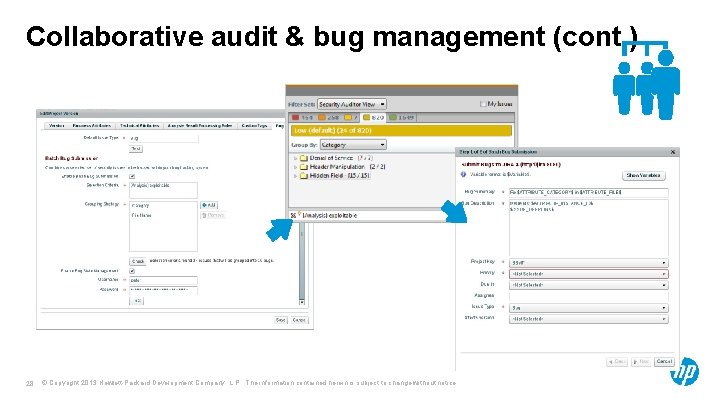
Collaborative audit & bug management (cont. ) 28 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

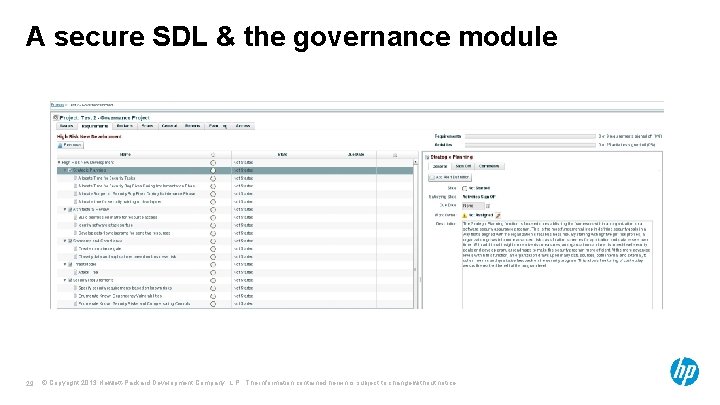
A secure SDL & the governance module 29 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

5. Wrap up © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

In summary… • • • 31 Making small changes add up to have big affects on workflow and cutting out wasted time and effort. You can customize how a lot of the software looks and feels, helping integrate SCA & SSC with your internal processes and requirements. Take a look at your internal processes now and think about how SCA & SSC currently integrates with them: • Are your developers spending too much time scanning? • Would it be worthwhile getting additional hardware for one standalone machine vs increasing hardware for all workstations? • Is it taking too long to discern which are the most important problems for your business? © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Any questions? 32 © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Thank you © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Security for the new reality © Copyright 2013 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.