Secure Multifactor Remote User Authentication Scheme for Internet


- Slides: 15

Secure Multi‐factor Remote User Authentication Scheme for Internet of Things Environments u. Source : International Journal of Communication Systems, In Press, 2017 u. Authors : Parwinder Kaur Dhillon and Sheetal Kalra u. Speaker : Hsiao-Ling Wu u. Date: 2017/09/07 1

Outline Introduction Proposed scheme Security analysis Performance analysis Conclusions 2

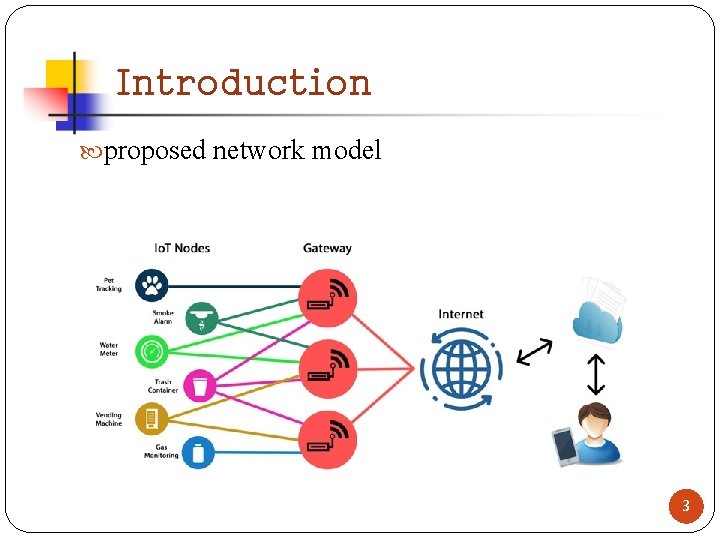
Introduction proposed network model 3

Proposed scheme(1/9) The registration phase The login phase The authentication phase Password change phase User Gateway Sensor 4

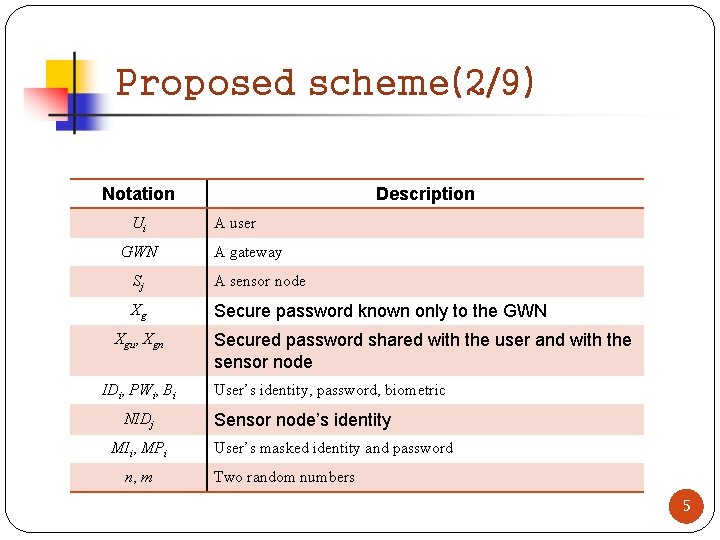
Proposed scheme(2/9) Notation Ui GWN Description A user A gateway Sj A sensor node Xg Secure password known only to the GWN Xgu, Xgn IDi, PWi, Bi NIDj MIi, MPi n, m Secured password shared with the user and with the sensor node User’s identity, password, biometric Sensor node’s identity User’s masked identity and password Two random numbers 5

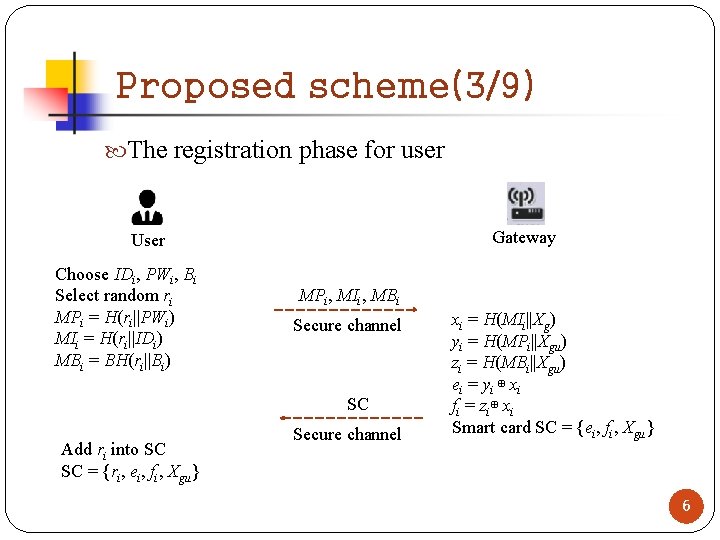
Proposed scheme(3/9) The registration phase for user Gateway User Choose IDi, PWi, Bi Select random ri MPi = H(ri||PWi) MIi = H(ri||IDi) MBi = BH(ri||Bi) MPi, MIi, MBi Secure channel SC Add ri into SC SC = {ri, ei, fi, Xgu} Secure channel xi = H(MIi||Xg) yi = H(MPi||Xgu) zi = H(MBi||Xgu) ei = yi ⊕ xi fi = zi⊕ xi Smart card SC = {ei, fi, Xgu} 6

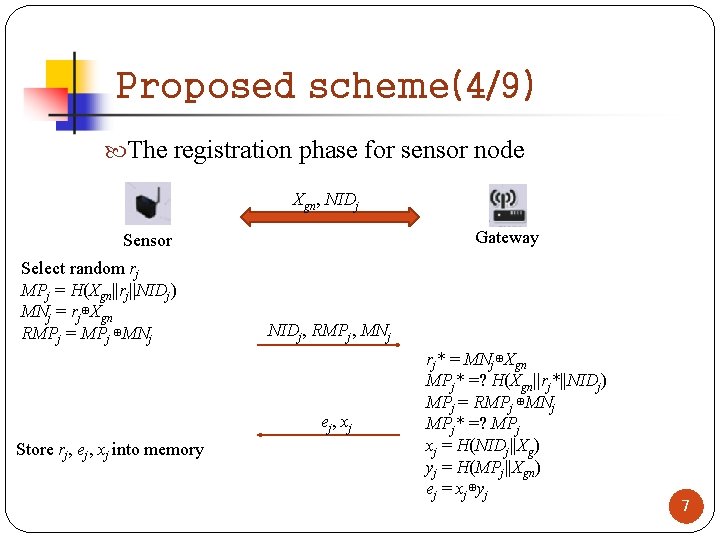
Proposed scheme(4/9) The registration phase for sensor node Xgn, NIDj Gateway Sensor Select random rj MPj = H(Xgn||rj||NIDj) MNj = rj⊕Xgn RMPj = MPj ⊕MNj NIDj, RMPj, MNj ej, xj Store rj, ej, xj into memory rj* = MNj⊕Xgn MPj* =? H(Xgn||rj*||NIDj) MPj = RMPj ⊕MNj MPj* =? MPj xj = H(NIDj||Xg) yj = H(MPj||Xgn) ej = xj⊕yj 7

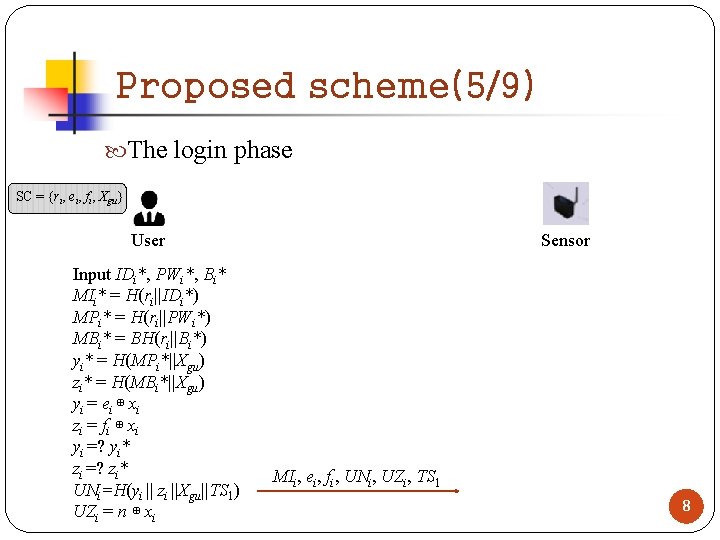
Proposed scheme(5/9) The login phase SC = {ri, ei, fi, Xgu} User Input IDi*, PWi*, Bi* MIi* = H(ri||IDi*) MPi* = H(ri||PWi*) MBi* = BH(ri||Bi*) yi* = H(MPi*||Xgu) zi* = H(MBi*||Xgu) yi = ei ⊕ xi zi = f i ⊕ x i yi =? yi* zi =? zi* UNi=H(yi || zi ||Xgu||TS 1) UZi = n ⊕ xi Sensor MIi, ei, fi, UNi, UZi, TS 1 8

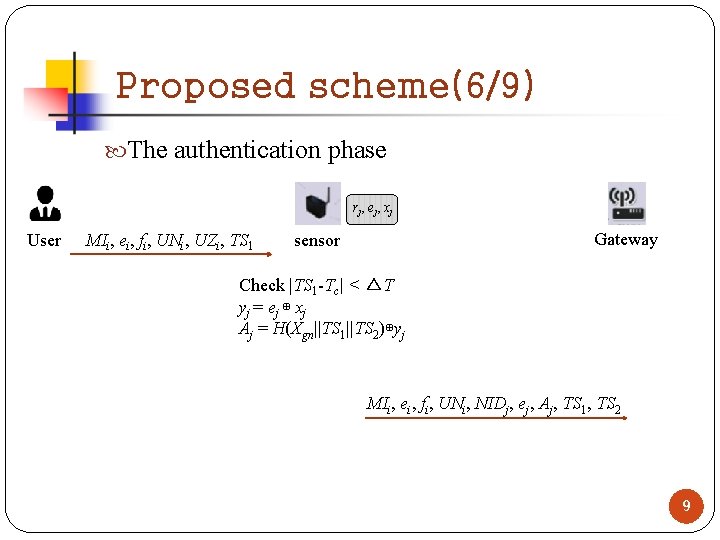
Proposed scheme(6/9) The authentication phase rj , e j , x j User MIi, ei, fi, UNi, UZi, TS 1 Gateway sensor Check |TS 1 -Tc| < △T yj = ej ⊕ xj Aj = H(Xgn||TS 1||TS 2)⊕yj MIi, ei, fi, UNi, NIDj, ej, Aj, TS 1, TS 2 9

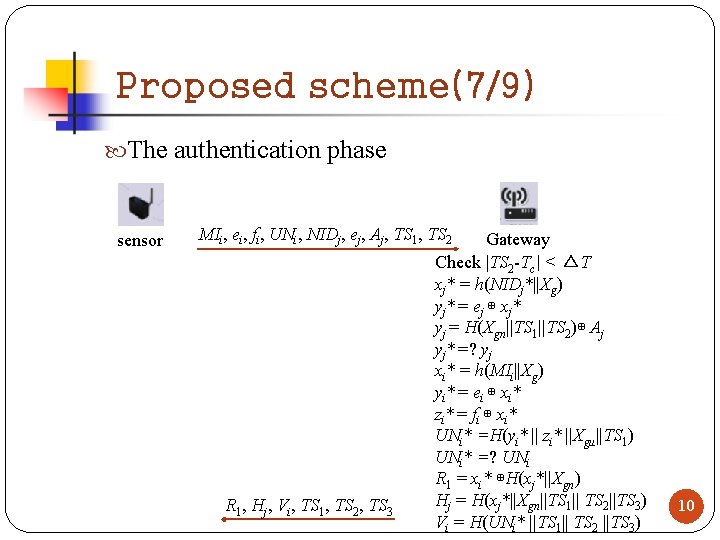
Proposed scheme(7/9) The authentication phase sensor MIi, ei, fi, UNi, NIDj, ej, Aj, TS 1, TS 2 R 1, Hj, Vi, TS 1, TS 2, TS 3 Gateway Check |TS 2 -Tc| < △T xj* = h(NIDj*||Xg) yj* = ej ⊕ xj* yj = H(Xgn||TS 1||TS 2)⊕ Aj yj* =? yj xi* = h(MIi||Xg) yi* = ei ⊕ xi* zi* = fi ⊕ xi* UNi* =H(yi* || zi* ||Xgu||TS 1) UNi* =? UNi R 1 = xi* ⊕H(xj*||Xgn) Hj = H(xj*||Xgn||TS 1|| TS 2||TS 3) Vi = H(UNi* ||TS 1|| TS 2 ||TS 3) 10

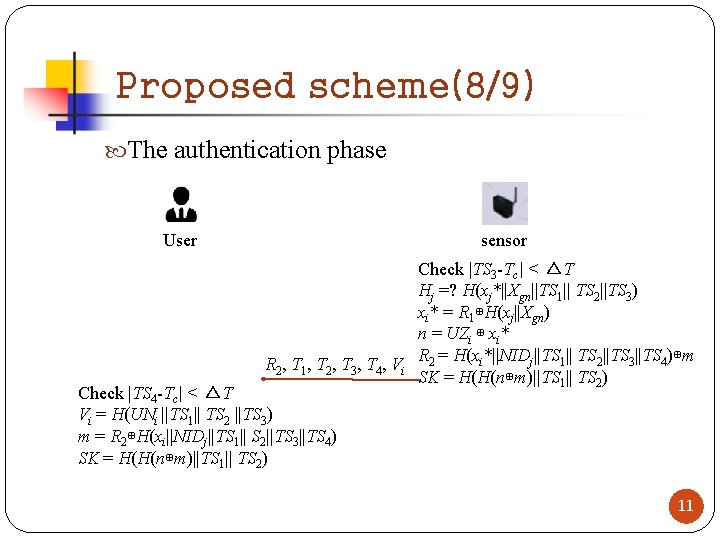
Proposed scheme(8/9) The authentication phase User sensor Check |TS 3 -Tc| < △T Hj =? H(xj*||Xgn||TS 1|| TS 2||TS 3) xi* = R 1⊕H(xj||Xgn) n = UZi ⊕ xi* R = H(xi*||NIDj||TS 1|| TS 2||TS 3||TS 4)⊕m R 2 , T 1 , T 2 , T 3 , T 4 , V i 2 SK = H(H(n⊕m)||TS 1|| TS 2) Check |TS 4 -Tc| < △T Vi = H(UNi ||TS 1|| TS 2 ||TS 3) m = R 2⊕H(xi||NIDj||TS 1|| S 2||TS 3||TS 4) SK = H(H(n⊕m)||TS 1|| TS 2) 11

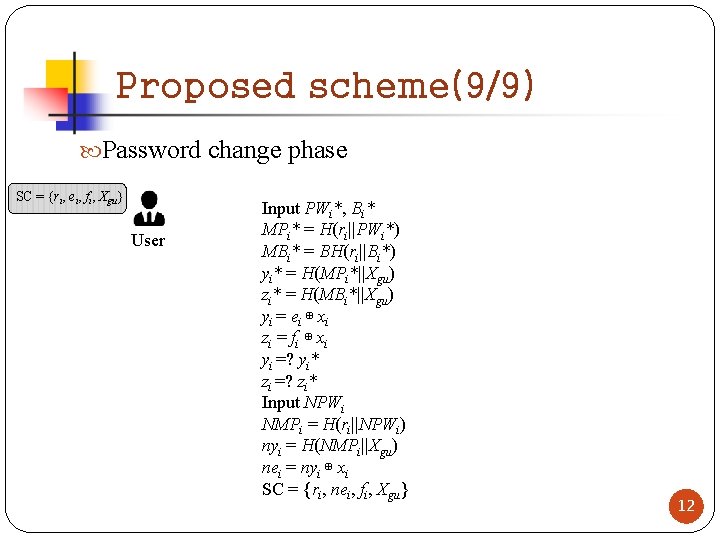
Proposed scheme(9/9) Password change phase SC = {ri, ei, fi, Xgu} User Input PWi*, Bi* MPi* = H(ri||PWi*) MBi* = BH(ri||Bi*) yi* = H(MPi*||Xgu) zi* = H(MBi*||Xgu) yi = ei ⊕ xi zi = f i ⊕ x i yi =? yi* zi =? zi* Input NPWi NMPi = H(ri||NPWi) nyi = H(NMPi||Xgu) nei = nyi ⊕ xi SC = {ri, nei, fi, Xgu} 12

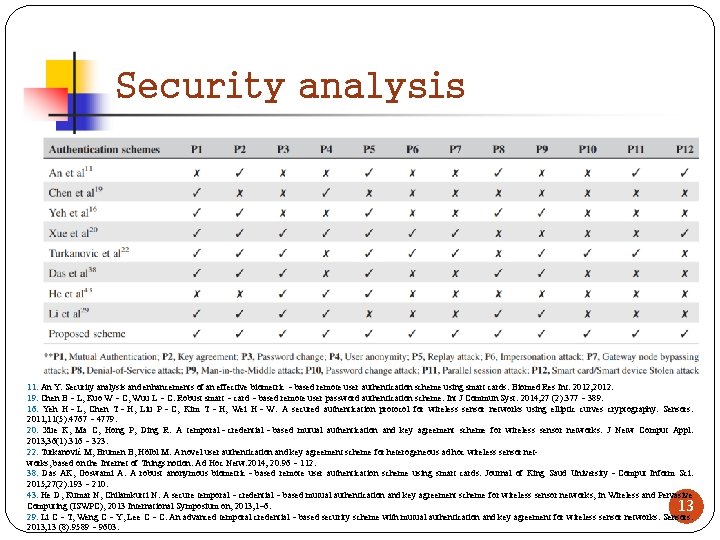
Security analysis 11. An Y. Security analysis and enhancements of an effective biometric‐based remote user authentication scheme using smart cards. Biomed Res Int. 2012; 2012. 19. Chen B‐L, Kuo W‐C, Wuu L‐C. Robust smart‐card‐based remote user password authentication scheme. Int J Commun Syst. 2014; 27 (2): 377‐ 389. 16. Yeh H‐L, Chen T‐H, Liu P‐C, Kim T‐H, Wei H‐W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011; 11(5): 4767‐ 4779. 20. Xue K, Ma C, Hong P, Ding R. A temporal‐credential‐based mutual authentication and key agreement scheme for wireless sensor networks. J Netw Comput Appl. 2013; 36(1): 316‐ 323. 22. Turkanović M, Brumen B, Hölbl M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014; 20: 96‐ 112. 38. Das AK, Goswami A. A robust anonymous biometric‐based remote user authentication scheme using smart cards. Journal of King Saud University‐Comput Inform Sci. 2015; 27(2): 193‐ 210. 43. He D, Kumar N, Chilamkurti N. A secure temporal‐credential‐based mutual authentication and key agreement scheme for wireless sensor networks, in Wireless and Pervasive Computing (ISWPC), 2013 International Symposium on, 2013; 1– 6. 13 29. Li C‐T, Weng C‐Y, Lee C‐C. An advanced temporal credential‐based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors. 2013; 13 (8): 9589‐ 9603.

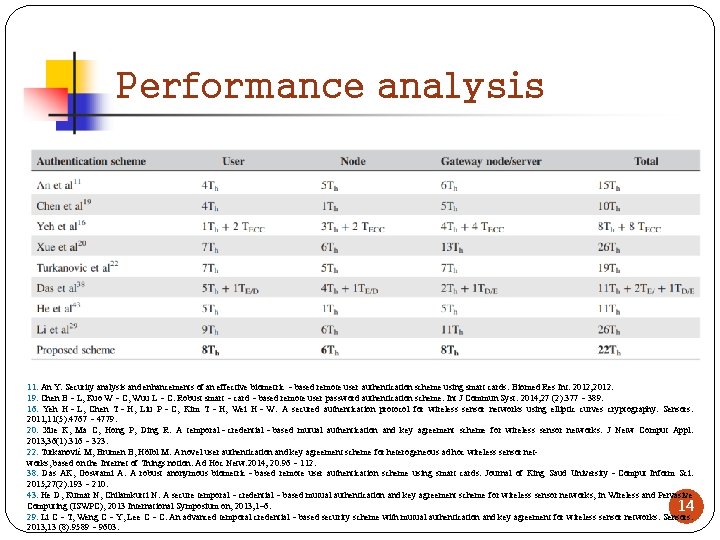
Performance analysis 11. An Y. Security analysis and enhancements of an effective biometric‐based remote user authentication scheme using smart cards. Biomed Res Int. 2012; 2012. 19. Chen B‐L, Kuo W‐C, Wuu L‐C. Robust smart‐card‐based remote user password authentication scheme. Int J Commun Syst. 2014; 27 (2): 377‐ 389. 16. Yeh H‐L, Chen T‐H, Liu P‐C, Kim T‐H, Wei H‐W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011; 11(5): 4767‐ 4779. 20. Xue K, Ma C, Hong P, Ding R. A temporal‐credential‐based mutual authentication and key agreement scheme for wireless sensor networks. J Netw Comput Appl. 2013; 36(1): 316‐ 323. 22. Turkanović M, Brumen B, Hölbl M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014; 20: 96‐ 112. 38. Das AK, Goswami A. A robust anonymous biometric‐based remote user authentication scheme using smart cards. Journal of King Saud University‐Comput Inform Sci. 2015; 27(2): 193‐ 210. 43. He D, Kumar N, Chilamkurti N. A secure temporal‐credential‐based mutual authentication and key agreement scheme for wireless sensor networks, in Wireless and Pervasive Computing (ISWPC), 2013 International Symposium on, 2013; 1– 6. 14 29. Li C‐T, Weng C‐Y, Lee C‐C. An advanced temporal credential‐based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors. 2013; 13 (8): 9589‐ 9603.

Conclusions Multi‐factor authentication scheme High security level lightweight Less storage 15