Sectoral operational programme Increase of economic competitiveness Investments














- Slides: 39

Sectoral operational programme „Increase of economic competitiveness” „Investments for your future” Automated system of authenticating through biometric signature - ATHOS Project co-financed by the European Regional Development Fund ATHOS Team July 15, 2013 “The content of this material does not necessarily represent the official position of the European Union or the Romanian Government”

Automated system of authenticating through biometric signature Introduction Slides before 1 st Section Divider Overview Technical Description Demo

Motivation �Considering that virtual attacks take place more and more often, with increasing damage, there is a need to increase the safety degree of applications representing targets for the attackers.

The project objective �the inclusion of the signature based authentication procedure, to increase the security degree of on-line authentication �the reduction of the implementation time allotted to execute the authentication system by the developers for this type of solution

Where did we start from? SISEB BIOACS Patent for signature authentication system ATHOS bases

What have we reached? � Project eligible expenses financed from public funds : 912. 843 RON � New jobs created due to the project: 3 � Patent applications resulted from the project: 1 � Scientific publications resulted from the project: 3 � Private financial contribution of the applicant: 1. 386. 648 RON � Project eligible expenses made by SOFTWIN: 2. 118. 250 RON

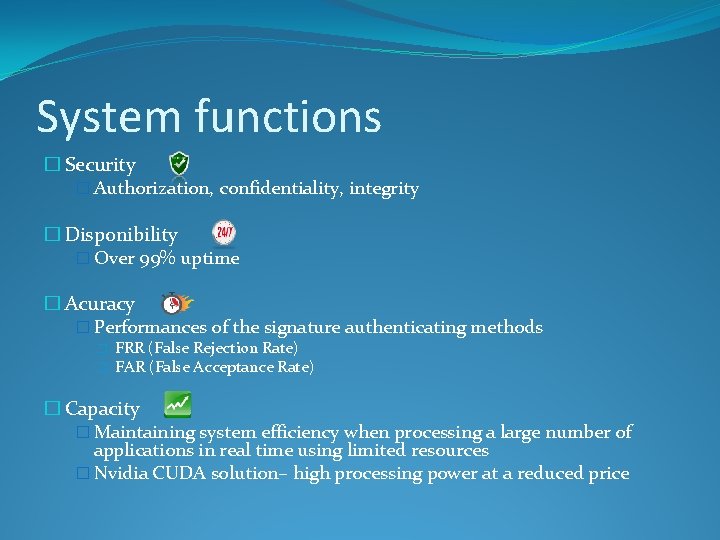
System functions � Security � Authorization, confidentiality, integrity � Disponibility � Over 99% uptime � Acuracy � Performances of the signature authenticating methods � � FRR (False Rejection Rate) FAR (False Acceptance Rate) � Capacity � Maintaining system efficiency when processing a large number of applications in real time using limited resources � Nvidia CUDA solution– high processing power at a reduced price

System functions �Modifiability �Treating a high number of requests from customers in different geographical regions – replication �Interoperability �Modifiable architecture– multiple biometric technologies can be used �Scalability �Optimal distribution of tasks by resources �Reduced time to design and implement the solution

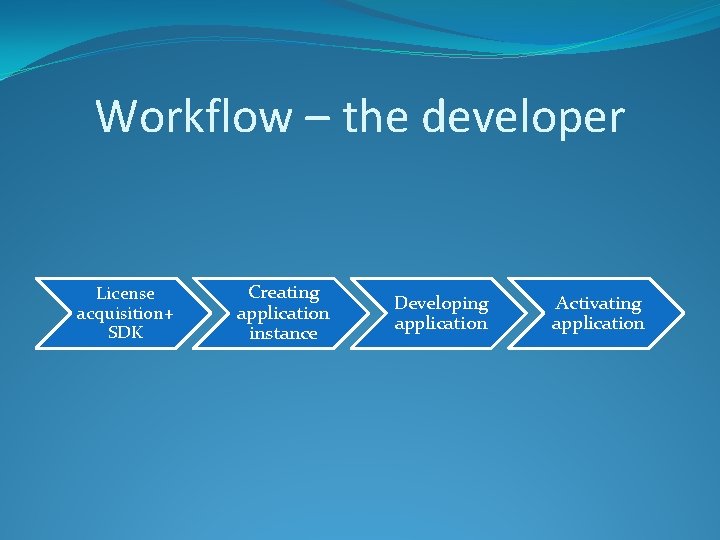
Workflow – the developer License acquisition+ SDK Creating application instance Developing application Activating application

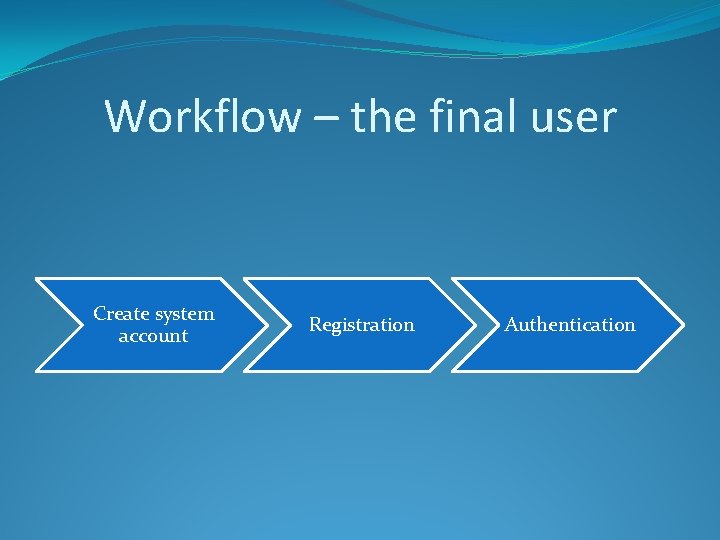
Workflow – the final user Create system account Registration Authentication

Licensing mode �Requirement of SLA (Service Level Agreement) �Maximum response time �Maximum number of requests per minute �Maximum number of users registered in the system �Example: �E-banking application vs timesheet application

Commercial package 1) Selling authentication services to developers: �Subscription fee 2) Pay-per-use: �Fee for each authentication �Package content: �Client SDK �User manuals �Development licenses + production

Performances* �Security level �FRR: max. 10 -15% �FAR: max. 1% �Response time: 1 -5 seconds �Number of requests per minute: thousandstens of thousands** * only with the purchased license and while the system is not overloaded ** depending on hardware configuration

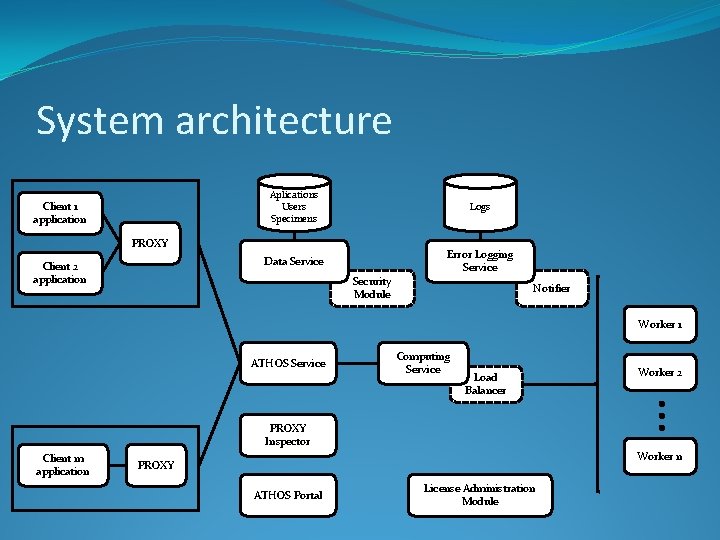
System architecture Client 1 application Aplications Users Specimens Logs Data Service Error Logging Service PROXY Client 2 application Security Module Notifier Worker 1 ATHOS Service Computing Service Load Balancer Worker 2 PROXY Inspector Client m application Worker n PROXY ATHOS Portal License Administration Module

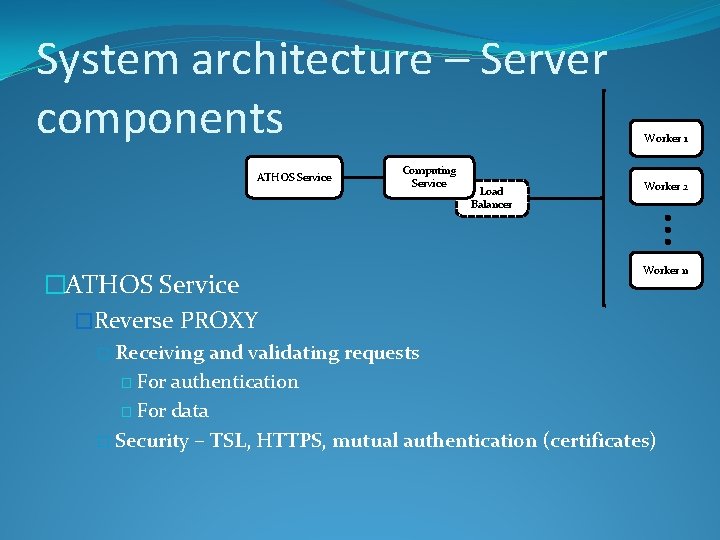
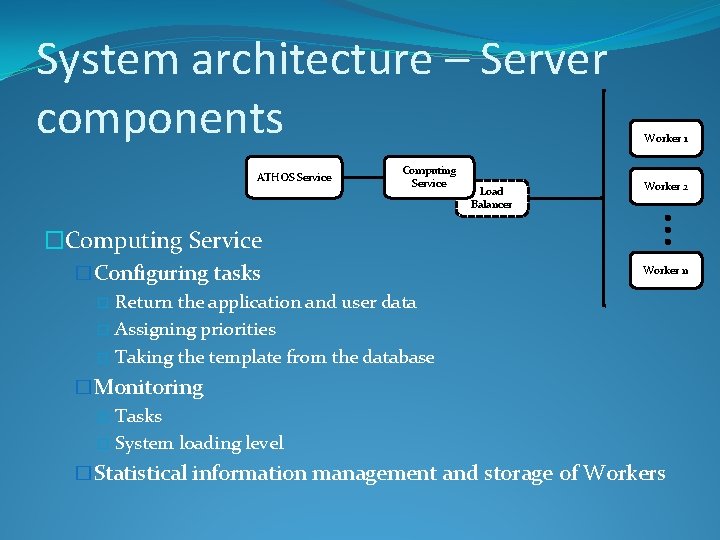
System architecture – Server components ATHOS Service �Reverse PROXY � Receiving Computing Service Load Balancer Worker 1 Worker 2 Worker n and validating requests � For authentication � For data � Security – TSL, HTTPS, mutual authentication (certificates)

System architecture – Server components ATHOS Service Computing Service Load Balancer Worker 1 Worker 2 �Computing Service �Configuring tasks � Return the application and user data � Assigning priorities � Taking the template from the database Worker n �Monitoring � Tasks � System loading level �Statistical information management and storage of Workers

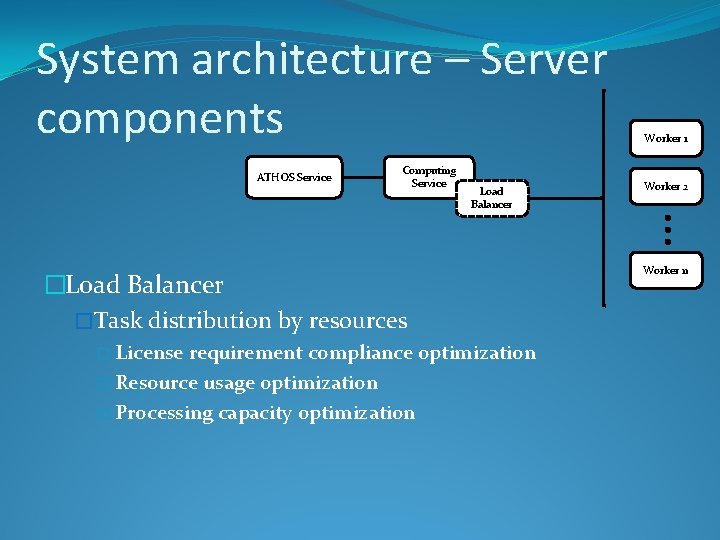
System architecture – Server components ATHOS Service Computing Service Load Balancer �Task distribution by resources � License requirement compliance optimization � Resource usage optimization � Processing capacity optimization Worker 1 Worker 2 Worker n

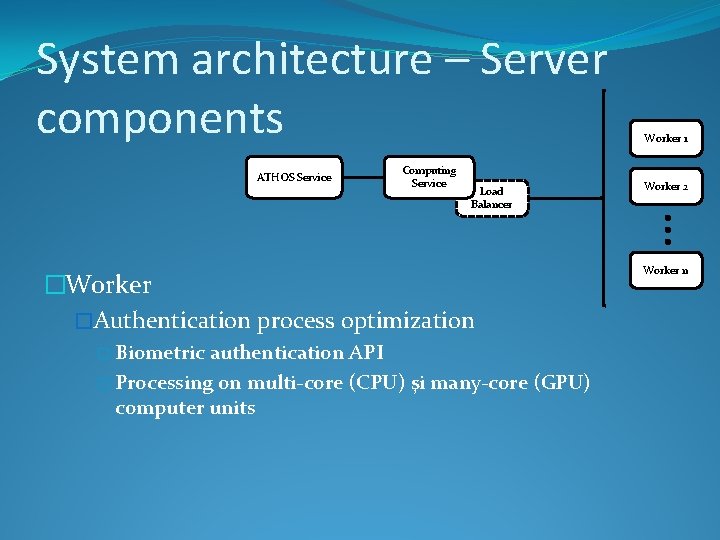
System architecture – Server components ATHOS Service Computing Service Load Balancer �Worker �Authentication process optimization � Biometric authentication API � Processing on multi-core (CPU) şi many-core (GPU) computer units Worker 1 Worker 2 Worker n

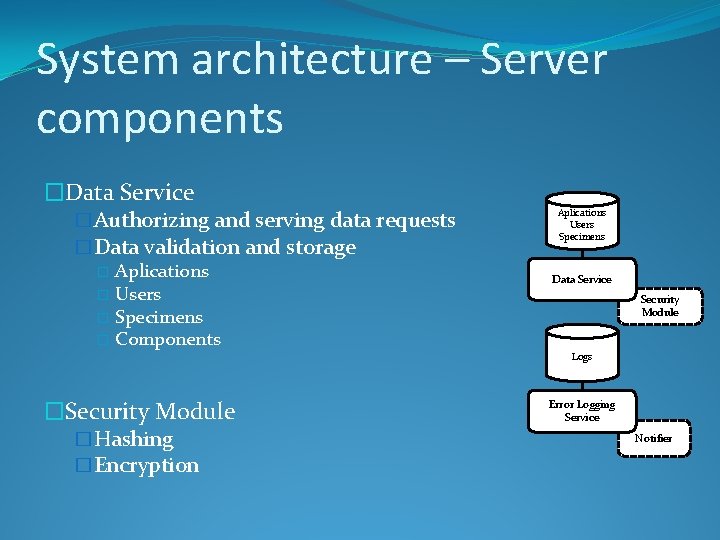
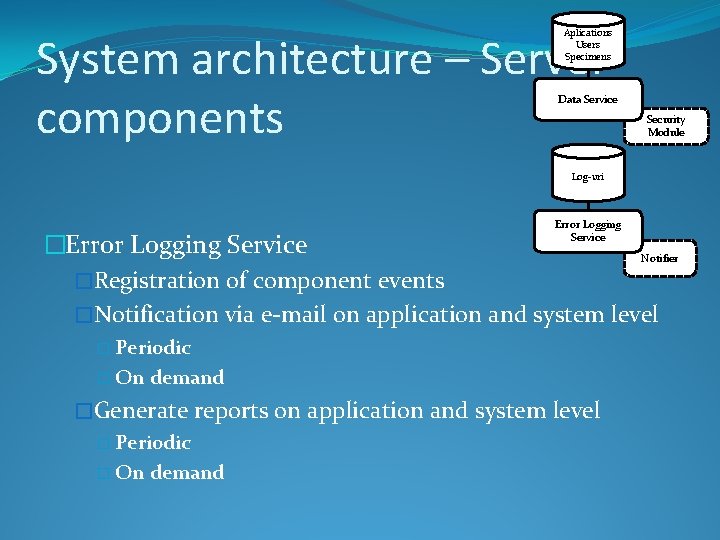
System architecture – Server components �Data Service �Authorizing and serving data requests �Data validation and storage � Aplications � Users � Specimens � Components �Security Module �Hashing �Encryption Aplications Users Specimens Data Service Security Module Logs Error Logging Service Notifier

Aplications Users Specimens System architecture – Server components Data Service Security Module Log-uri Error Logging Service �Error Logging Service Notifier �Registration of component events �Notification via e-mail on application and system level � Periodic � On demand �Generate reports on application and system level � Periodic � On demand

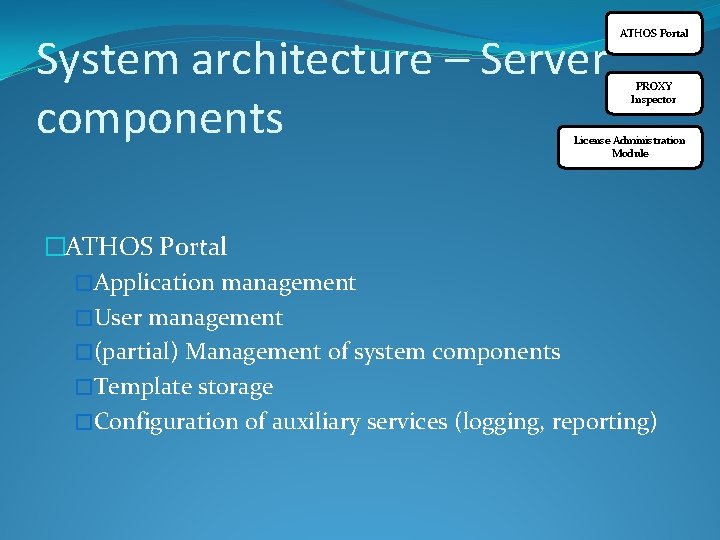
System architecture – Server components ATHOS Portal PROXY Inspector License Administration Module �ATHOS Portal �Application management �User management �(partial) Management of system components �Template storage �Configuration of auxiliary services (logging, reporting)

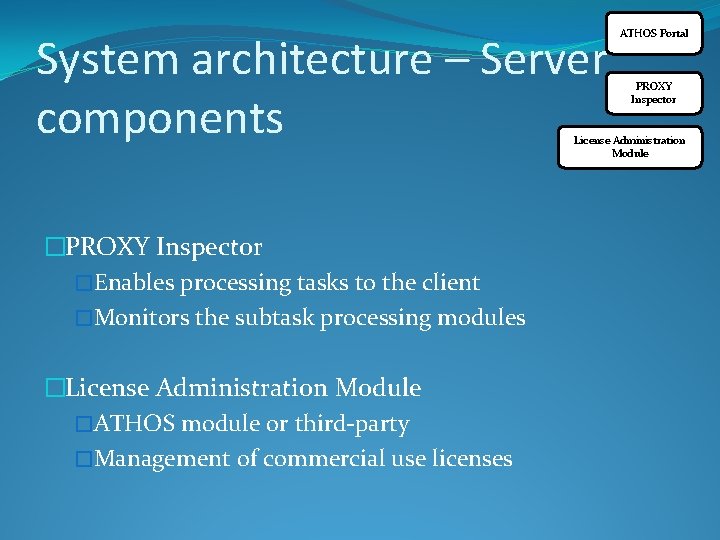
System architecture – Server components ATHOS Portal PROXY Inspector License Administration Module �PROXY Inspector �Enables processing tasks to the client �Monitors the subtask processing modules �License Administration Module �ATHOS module or third-party �Management of commercial use licenses

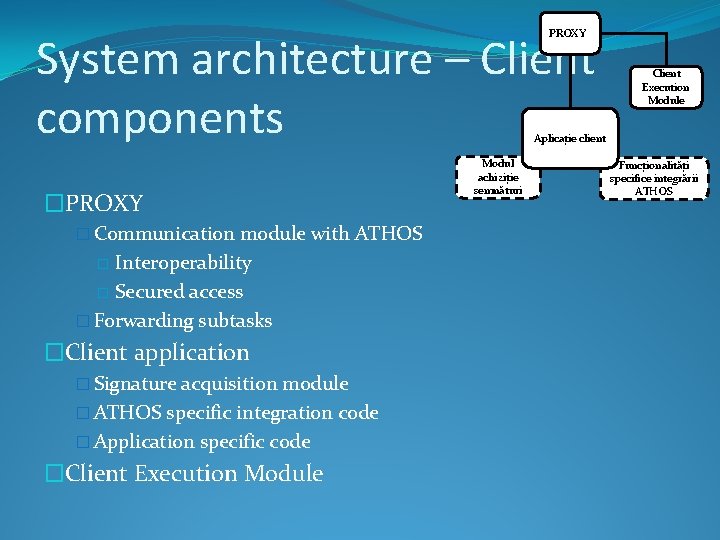
PROXY System architecture – Client components Client Execution Module Aplicație client �PROXY � Communication module with ATHOS Interoperability � Secured access � Forwarding subtasks � �Client application � Signature acquisition module � ATHOS specific integration code � Application specific code �Client Execution Module Modul achiziție semnături Funcționalități specifice integrării ATHOS

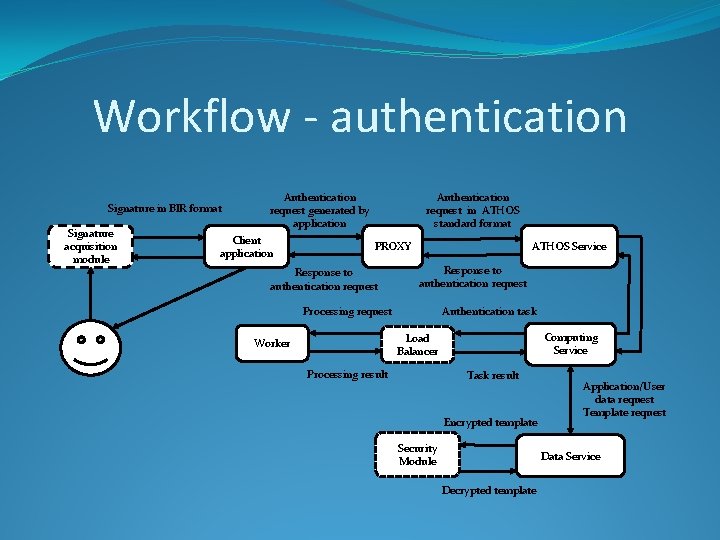
Workflow - authentication Signature in BIR format Signature acquisition module Authentication request in ATHOS standard format Authentication request generated by application Client application ATHOS Service PROXY Response to authentication request Authentication task Processing request Computing Service Load Balancer Worker Processing result Task result Encrypted template Security Module Application/User data request Template request Data Service Decrypted template

Scheduling algorithm �Algorithm developed by SOFTWIN team, patent pending (US PTO) �Authentication task distribution by available resources �SLA compliance �Efficient resource usage �Uniform decrease of performances when loading

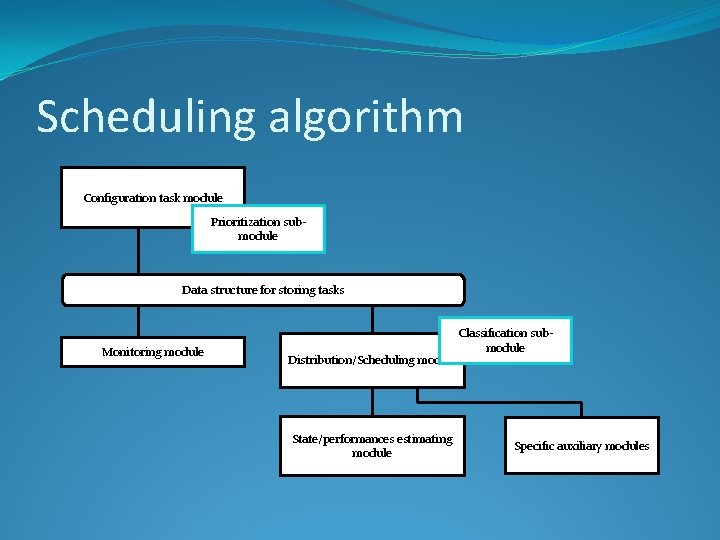
Scheduling algorithm Configuration task module Prioritization submodule Data structure for storing tasks Monitoring module Distribution/Scheduling module State/performances estimating module Classification submodule Specific auxiliary modules

Scheduling algorithm �Prioritization scheme based on SLA �Determining the proportionality between urgent and non-urgent tasks �Resource classification based on task proportionality �Capacity �Processing power �Confidence level

Security �Secured connection between clients and ATHOS core (TSL) �Template encrypted storage(AES) �Authentication and authorization on ATHOS service level

Technologies

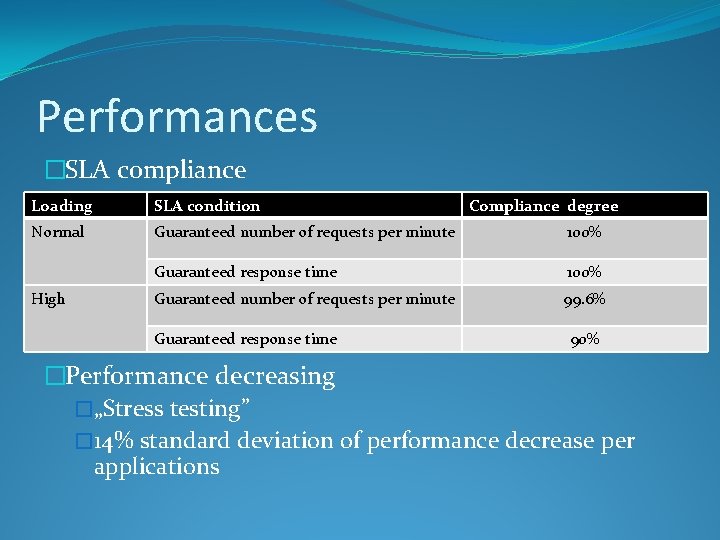
Performances �SLA compliance Loading SLA condition Normal Guaranteed number of requests per minute 100% Guaranteed response time 100% Guaranteed number of requests per minute 99. 6% High Guaranteed response time Compliance degree 90% �Performance decreasing �„Stress testing” � 14% standard deviation of performance decrease per applications

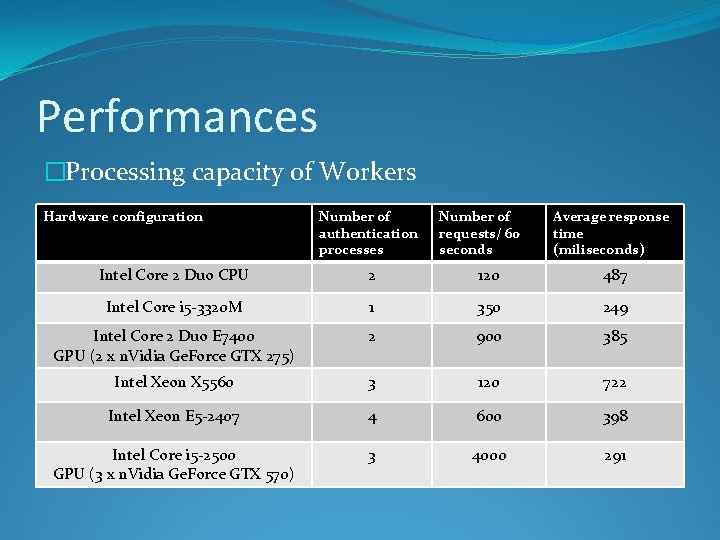
Performances �Processing capacity of Workers Hardware configuration Number of authentication processes Number of requests/ 60 seconds Average response time (miliseconds) Intel Core 2 Duo CPU 2 120 487 Intel Core i 5 -3320 M 1 350 249 Intel Core 2 Duo E 7400 GPU (2 x n. Vidia Ge. Force GTX 275) 2 900 385 Intel Xeon X 5560 3 120 722 Intel Xeon E 5 -2407 4 600 398 Intel Core i 5 -2500 GPU (3 x n. Vidia Ge. Force GTX 570) 3 4000 291

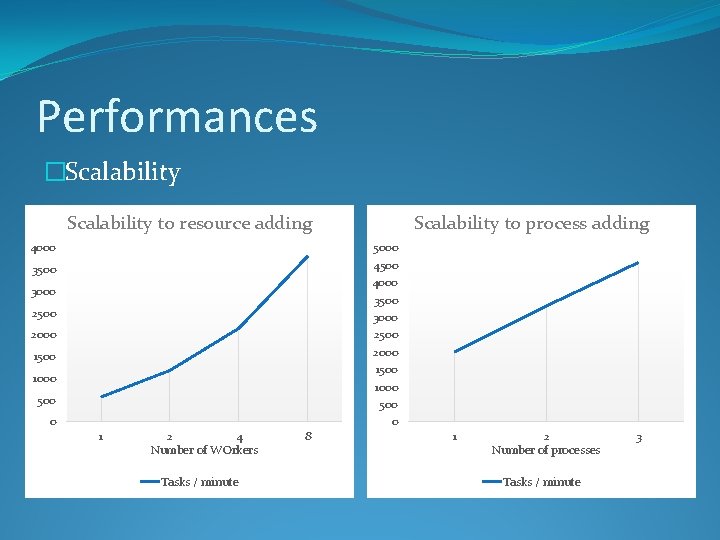
Performances �Scalability to resource adding 4000 Scalability to process adding 5000 4500 4000 3500 3000 2500 2000 1500 1000 500 0 1 2 4 Number of WOrkers Tasks / minute 8 1 2 Number of processes Tasks / minute 3

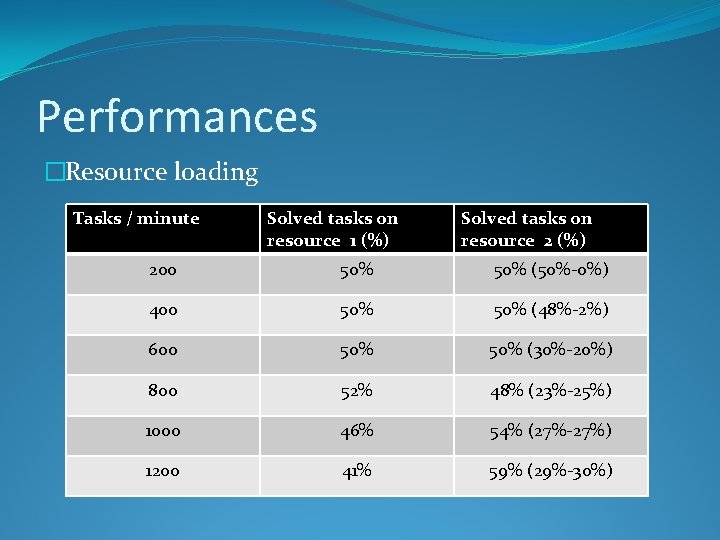
Performances �Resource loading Tasks / minute Solved tasks on resource 1 (%) Solved tasks on resource 2 (%) 200 50% (50%-0%) 400 50% (48%-2%) 600 50% (30%-20%) 800 52% 48% (23%-25%) 1000 46% 54% (27%-27%) 1200 41% 59% (29%-30%)

Performances �Up to 5000 requests per minute(7, 2 million requests/day) �Data server � Intel Xeon E 5 -2407, CPU: 2. 40 GHz, 2 proc. x 8 core x 1 thread �Central server � Intel Xeon E 7302, CPU: 2. 13 GHz, 4 core X 4 threads �Workers � Intel Core 2 Duo CPU � 3 x Intel Core i 5 -3320 M � Intel Core 2 Duo E 7400, GPU (2 x n. Vidia Ge. Force GTX 275) � Intel Core i 5 -2500, GPU (3 x n. Vidia Ge. Force GTX 570)

Additional information � A. Salinca, S. M. Rusu, Ș. Diaconescu: An approach to data collection in an online signature verification system, 8 th International Conference on Web Information Systems and Technologies, Porto, Portugal 18 – 21 April 2012, WEBIST � A. Salinca, S. M. Rusu, A. M. Pricochi: SOA–Based Authentication System for Dynamic Handwritten Signature, Advances in Information Systems and Technologies, 735 -744, Springer Berlin Heidelberg, 2013 � A. M. Pricochi, A. Salinca, S. M. Rusu, B. Ivașcu: A Dynamic Load Balancing Strategy for a Distributed Biometric Authentication System, 9 th International Conference on Web Information Systems and Technologies, Aachen, Germany 8 – 10 May 2013, WEBIST

Demo ATHOS Home. Banktype Demo Athos Portal

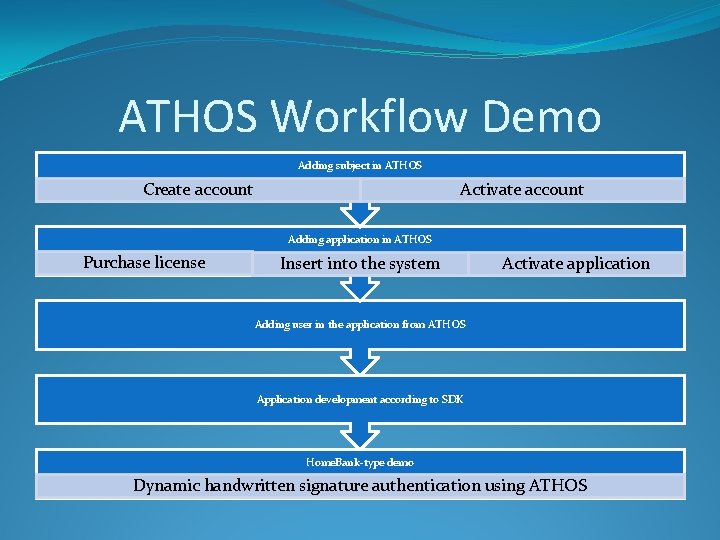
ATHOS Workflow Demo Adding subject in ATHOS Create account Activate account Adding application in ATHOS Purchase license Insert into the system Activate application Adding user in the application from ATHOS Application development according to SDK Home. Bank-type demo Dynamic handwritten signature authentication using ATHOS

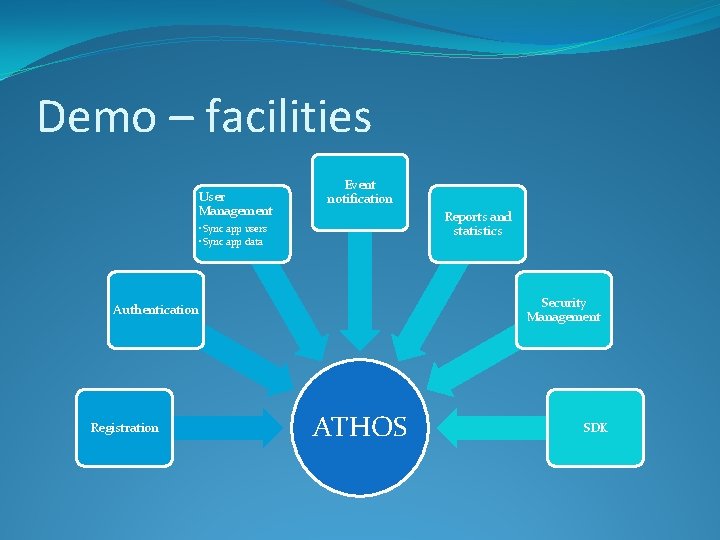
Demo – facilities User Management Event notification Reports and statistics • Sync app users • Sync app data Security Management Authentication Registration ATHOS SDK

Q&A Thank you!
 National manufacturing competitiveness programme
National manufacturing competitiveness programme Sectoral training
Sectoral training Intra sectoral coordination
Intra sectoral coordination Blueprint for sectoral cooperation on skills
Blueprint for sectoral cooperation on skills Economic growth vs economic development
Economic growth vs economic development Conclusion of growth and development
Conclusion of growth and development Chapter 1 lesson 2 our economic choices worksheet answers
Chapter 1 lesson 2 our economic choices worksheet answers Strategic management and strategic competitiveness
Strategic management and strategic competitiveness Competitiveness strategy and productivity
Competitiveness strategy and productivity Defining competitiveness
Defining competitiveness What is external competitiveness
What is external competitiveness Apec services competitiveness roadmap
Apec services competitiveness roadmap Productivity and competitiveness in operations management
Productivity and competitiveness in operations management The best known framework for analyzing competitiveness is
The best known framework for analyzing competitiveness is What is strategic competitiveness
What is strategic competitiveness Chapter 2 operations strategy and competitiveness
Chapter 2 operations strategy and competitiveness Internal competitiveness
Internal competitiveness Productivity and competitiveness in operations management
Productivity and competitiveness in operations management Competitiveness strategy and productivity
Competitiveness strategy and productivity What shapes external competitiveness
What shapes external competitiveness Chapter 2 operations strategy and competitiveness
Chapter 2 operations strategy and competitiveness Technological competitiveness
Technological competitiveness How do you measure productivity
How do you measure productivity Strategic competitiveness
Strategic competitiveness The methods and actions taken to accomplish strategies
The methods and actions taken to accomplish strategies Competitiveness strategy
Competitiveness strategy Lean manufacturing competitiveness scheme
Lean manufacturing competitiveness scheme Bodie et al
Bodie et al Outlook for alternative investments
Outlook for alternative investments Intercorporate investments
Intercorporate investments Capricorn private equity
Capricorn private equity Chapter 10 basics of saving and investing
Chapter 10 basics of saving and investing Interregional innovation investments
Interregional innovation investments Investments and securities tribunal
Investments and securities tribunal Ag respons
Ag respons James barber russell investments
James barber russell investments 3-7 future value of investments answers
3-7 future value of investments answers Bus-123 introduction to investments
Bus-123 introduction to investments Dms strategie consulting
Dms strategie consulting Intercorporate investments
Intercorporate investments