Searching Over Encrypted Data Charalampos Papamanthou cpapumd edu







- Slides: 15

Searching Over Encrypted Data Charalampos Papamanthou cpap@umd. edu ECE and UMIACS University of Maryland, College Park Research Supported By

Cloud computing today Clients § Industries § Federal government § Universities PROVIDERS § Google § Yahoo! § Amazon

Is there any privacy? § Cloud provider uses its own keys to encrypt the clients’ data § So, rest assured…?

Where we want to get at in the future § We want clients to be in control of their data § Encrypt at the client’s machine § Cloud only gets to see the ciphertext! § Google and Yahoo! already moving forward with such an approach § See end-to-end (https: //github. com/google/end -to-end)

How about searching? § In theory possible, but impractical § Fully-homomorphic encryption § Oblivious RAM § Two-party computation § My group’s approach § Theory: Searchable encryption § Practice: Pmail (demo in the end)

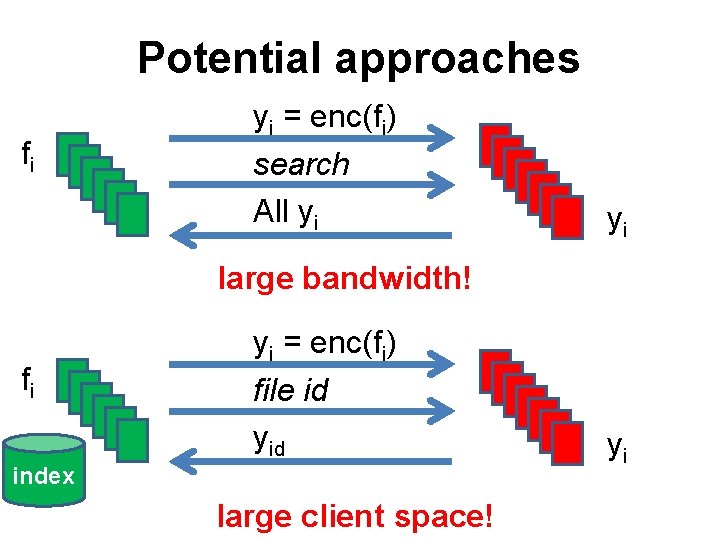
Potential approaches fi yi = enc(fi) search All yi yi large bandwidth! fi yi = enc(fi) file id yid index large client space! yi

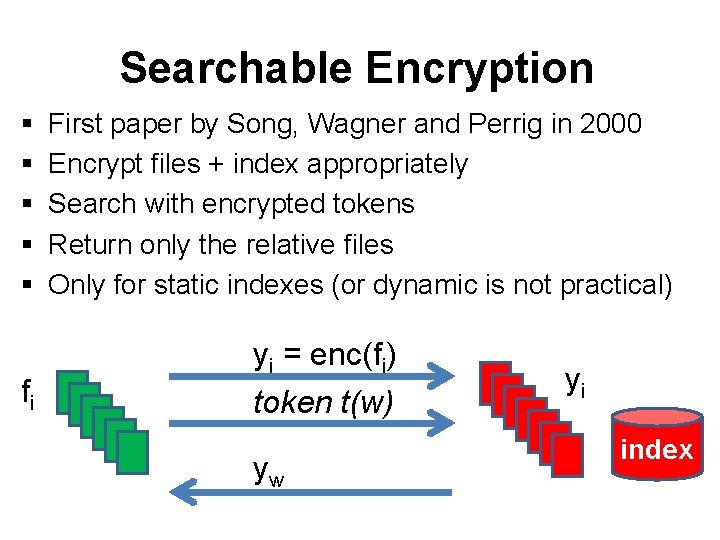
Searchable Encryption § § § fi First paper by Song, Wagner and Perrig in 2000 Encrypt files + index appropriately Search with encrypted tokens Return only the relative files Only for static indexes (or dynamic is not practical) yi = enc(fi) token t(w) yw yi index

Caveat • Searchable encryption leaks information – Search pattern – Access pattern

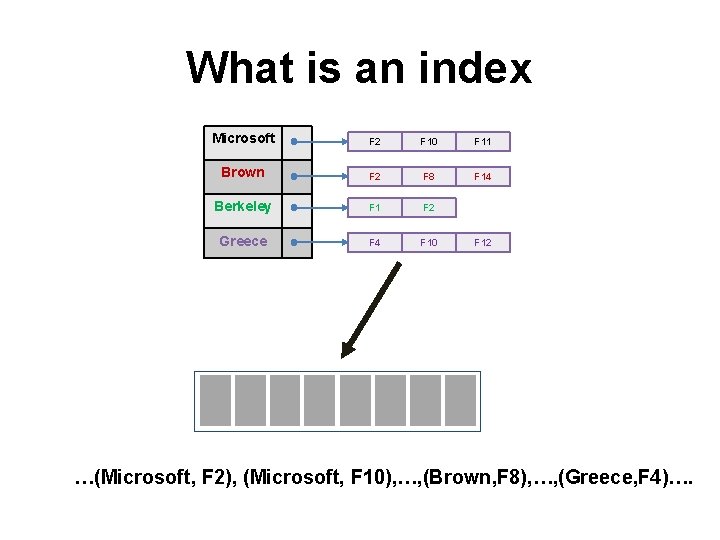
What is an index Microsoft F 2 F 10 F 11 Brown F 2 F 8 F 14 Berkeley F 1 F 2 Greece F 4 F 10 F 12 …(Microsoft, F 2), (Microsoft, F 10), …, (Brown, F 8), …, (Greece, F 4)….

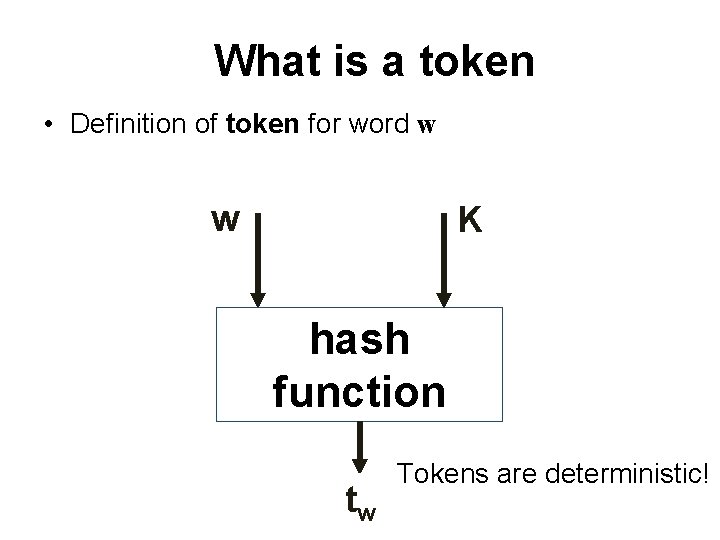
What is a token • Definition of token for word w w K hash function tw Tokens are deterministic!

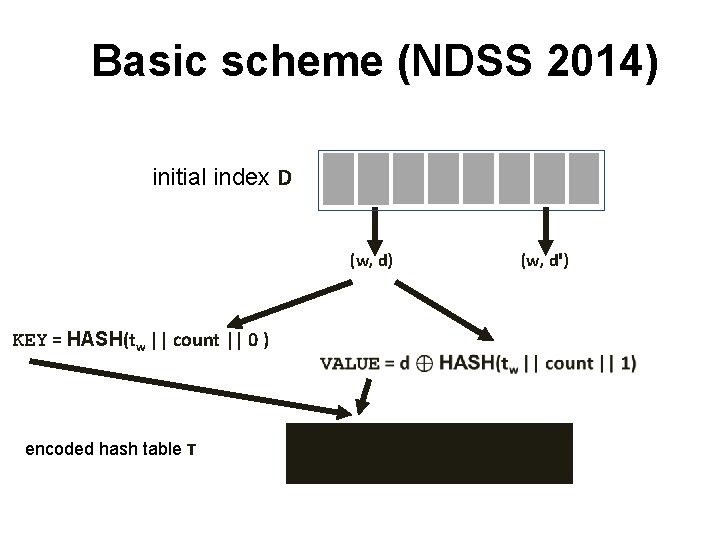
Basic scheme (NDSS 2014) initial index D (w, d) KEY = HASH(tw || count || 0 ) encoded hash table T (w, dꞌ)

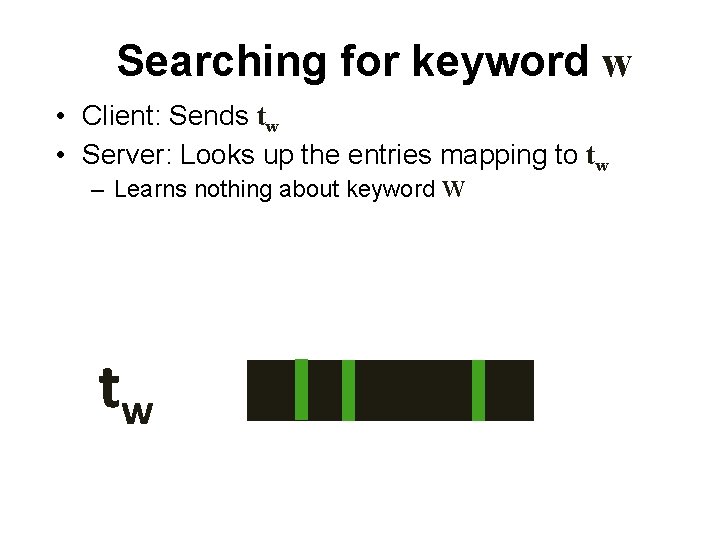
Searching for keyword w • Client: Sends tw • Server: Looks up the entries mapping to tw – Learns nothing about keyword W tw

Updating the index • Important: Old tokens should not work for new files – Addressed in our NDSS 2014 paper

Research in my group • Searchable encryption with support for updates (CCS 2012, NDSS 2014) • Parallel algorithms for searchable encryption (FC 2013) • [Ongoing research] – [Theory] New searchable encryption schemes that • • are more expressive (range and conjunctive search) leak less information (eliminating search pattern leakage) support more efficient updates (improving the polylogn bound) use weaker cryptographic assumptions (removing the random oracle) – [Practice] Devoping Pmail (plugin for Gmail) • Pick the right SE scheme • Web security issues (how to integrate securely with Gmail API) • Usability issues (how can we design the interface so that more people can use it)

Pmail Demo