Research Progress Report Advisor Frank YeongSung Lin Presented






















- Slides: 40

Research Progress Report Advisor: Frank, Yeong-Sung Lin Presented by Jia-Ling Pan 2021/2/26 NTUIM OPLAB 1

Agenda �Previous comments �Introduction �Problem Description 2021/2/26 NTUIM OPLAB 2

Previous comments �Epidemic model �Initial resource allocation �Resource deployment adjustment �Defense strategies ◦ over reacted v. s insensitive 2021/2/26 NTUIM OPLAB 3

Introduction 2021/2/26 NTUIM OPLAB 4

Epidemic model �The SIR Model(Kermack-Mckendrick model) ◦ Any time point an individual is either susceptible (S), infected and infectious (I) or recovered and immune (R). �S(t): the number of individuals not yet infected with the disease at time t, or those susceptible to the disease. �I(t): the number of individuals who have been infected with the disease and are capable of spreading the disease to those in the susceptible category. �R(t) is the compartment used for those individuals who have been infected and then recovered from the disease. Those in this category are not able to be infected again or to transmit the infection to others. 2021/2/26 NTUIM OPLAB 5

Epidemic model �The SIR Model(Kermack-Mckendrick model) ◦ Only susceptible individuals can get infected. ◦ After having been infectious for some time, an individual recovers and becomes completely immune for the remainder of the study period. ◦ There are no births, deaths, immigration or emigration during the study period. ◦ A consequence of the assumptions is that individuals can only make two moves: from S to I and from I to R. ◦ The flow of this model may be considered as follows: S→I→R 2021/2/26 NTUIM OPLAB 6

Worm Propagation Model �Simple Epidemic Model ◦ Each host is in one of the two states: susceptible or infectious. ◦ The model assumes that the system is homogeneous, each host has the equal probability to contact any other hosts in the Internet. ◦ The model also assumes that once infected by a worm, the host remains in the infectious state forever. ◦ Thus the transition procedure is: S→I ◦ Can describe the propagation status in initial stages, but is difficult to match the propagation status later. 2021/2/26 NTUIM OPLAB 7

Worm Propagation Model �The SIR Model(Kermack-Mckendrick model) ◦ Maintains one of three states: susceptible, infectious or removed. ◦ It assumes that during an epidemic of a contagious disease, some infectious hosts either recover or die. ◦ The hosts are in “removed” state after they recover or die from the disease. ◦ Any host in the system has either the state transition S→I→R or stays in S state 2021/2/26 NTUIM OPLAB 8

Worm Propagation Model �The SIR Model(Kermack-Mckendrick model) ◦ Improves the classical simple epidemic model by considering that some infectious hosts either recover or die after some time. ◦ However in the Internet, cleaning, patching, and filtering countermeasures against worms will remove both susceptible hosts and infectious hosts from circulation. ◦ The model assumes the infection rate to be constant, which isn’t true for a rampantly spreading Internet worm. 2021/2/26 NTUIM OPLAB 9

Worm Propagation Model �Two-Factor model ◦ Human countermeasures �Cleaning compromised computers. �Patching or upgrading susceptible computers. �Setting up filters to block the worm traffic on firewalls or edge routers. �Disconnecting their computers from Internet. ◦ Decreased infection rate β(t) �The large-scale worm propagation have caused congestion and troubles to some Internet routers, thus slowed down the worm scanning process. 2021/2/26 NTUIM OPLAB 10

Worm Propagation Model �Two-Factor model ◦ d. R(t)/dt=γI(t) (1) ◦ d. Q(t)/dt=μS(t)J(t) (2) ◦ J(t)=I(t)+R(t) η ◦ β(t)= β 0[1 -I(t)/N] (4) ◦ N=S(t)+I(t)+R(t)+Q(t) (5) ◦ d. S(t)/dt= -β(t)S(t)I(t)-d. Q(t)/dt 2021/2/26 NTUIM OPLAB (3) 11

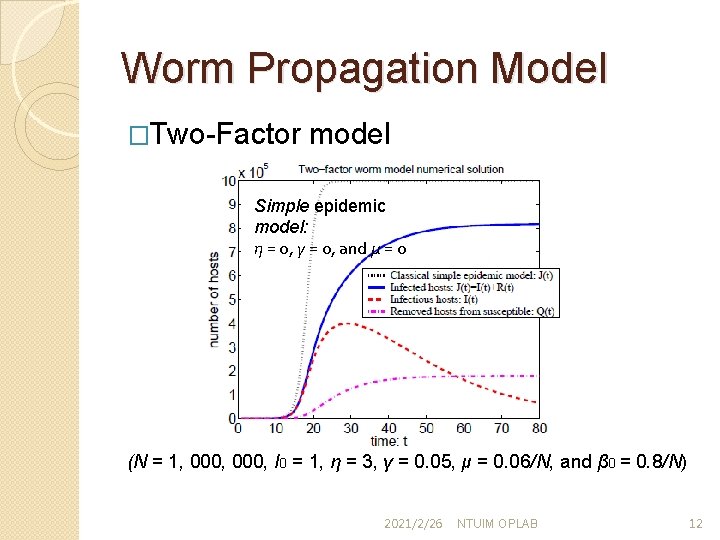
Worm Propagation Model �Two-Factor model Simple epidemic model: η = 0, γ = 0, and μ = 0 (N = 1, 000, I 0 = 1, η = 3, γ = 0. 05, μ = 0. 06/N, and β 0 = 0. 8/N) 2021/2/26 NTUIM OPLAB 12

Worm Propagation Model �Two-Factor model ◦ Takes more factors into consideration, such as human countermeasures and network congestion. ◦ It can be used to analyze more complex worm propagation scene. ◦ However, the effect of topology on worm propagation is still an unsolvable problem. � [1] Sihan Qing and Weiping Wen, “A survey and trends on Internet worms”, Computers & Security, 2005 � [2] Su Fei 1, Lin Zhaowen and Ma Yan, “A Survey of Internet Worm Propagation Models”, Proceedings of ICBNMT 2009 2021/2/26 NTUIM OPLAB 13

New worm types � Self disciplinary worms ◦ Adapts its propagation patterns to defensive countermeasures, aiming to avoid or delay detection, and ultimately, to infect more computers. � Static self-disciplinary worms ◦ Intelligently select a propagation speed at the initial time of attack but nevertheless maintain the same strategy during the attack session. � Dynamic self-disciplinary worm ◦ Dynamically adjust its propagation speed during the attack session. � [3] Wei Yu, Nan Zhang, Xinwen Fu and Wei Zhao, ”Self- Disciplinary Worms and Countermeasures: Modeling and Analysis”, Parallel and Distributed Systems, IEEE Transactions on, 2010 2021/2/26 NTUIM OPLAB 14

Worm Scanning Strategy � One of the biggest problems a worm faces in achieving a very rapid rate of infection is “getting off the ground. ” � Before initiating an attack, the worm should probe the system vulnerabilities of the target hosts. � Blind scan ◦ Many worms in the wild use this scanning strategy. They choose a new host to scan in a random, permutation or sequential way. � Hit-list scan ◦ Creates a target list which includes those hosts potentially infected before searching the susceptible hosts. � [4] Stuart Staniford, Vern Paxsony and Nicholas Weaver, “How to 0 wn the Internet in Your Spare Time”, Proceedings of the 11 th USENIX Security Symposium, 2002 2021/2/26 NTUIM OPLAB 15

Defending Against Internet Worms �Worm Detection ◦ Signature-Based ◦ Anomaly-Based �Worm Containment ◦ Slowing Down Infection �Rate limiting ◦ Blocking �Address Blocking �Content Blocking � [5]Pele Li, Mehdi Salour and Xiao Su, “A Survey of Internet Worm Detection and Containment”, IEEE Communications Surveys & Tutorials, 2008 2021/2/26 NTUIM OPLAB 16

Problem Description 2021/2/26 NTUIM OPLAB 17

Problem Description �Attacker attributes �Defender attributes �Attack-defense scenarios 2021/2/26 NTUIM OPLAB 18

Attacker attributes �Objective ◦ Using worms to get a clearer map of network topology information or vulnerability, and eventually compromise core nodes. 2021/2/26 NTUIM OPLAB 19

Attacker attributes �Budget ◦ Preparing phase �Worm purchasing v. s development �Social engineering ◦ Attacking phase �Node compromising �Worm injection 2021/2/26 NTUIM OPLAB 20

Attacker attributes �Preparing phase ◦ Worm attributes �Scanning method: blind v. s hitlist �Propagation rate: static v. s dynamic �Capability: basic v. s advanced ◦ Social engineering �Number of edge nodes �Number of hops from each core node 2021/2/26 NTUIM OPLAB 21

Attacker attributes �Attacking phase ◦ Node compromising �Next hop selection criteria: �Link degree �High link degree ─ information seeking �Link utilization �Low link utilization ─ stealth strategy ◦ Worm injection �Candidate selection criteria: �Link traffic �High link traffic ─ high rate worm �Low link traffic ─ low rate worm �Node defense resource �β(t) �Defense resource 2021/2/26 NTUIM OPLAB 22

Defender attributes �Objective ◦ Protect core nodes �Budget ◦ Planning phase ◦ Defending phase 2021/2/26 NTUIM OPLAB 23

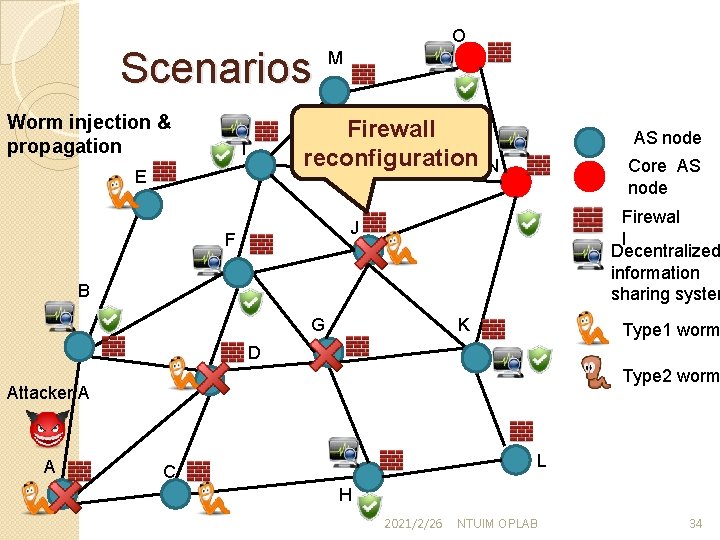
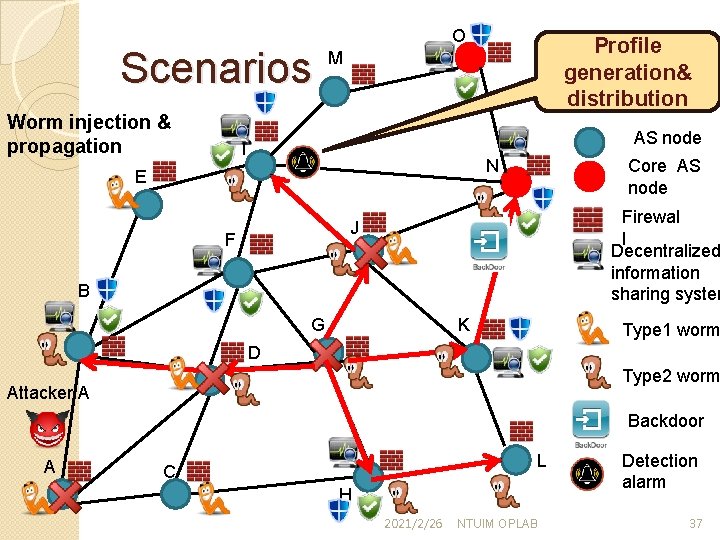
Defender attributes �Planning phase ◦ Node protection �General defense resources allocation(ex: Firewall, IDS) ◦ Decentralized information sharing system deployment �Defending phase ◦ Decentralized information sharing system ◦ ◦ �Unknown worm detection & profile distribution Worm origin identification Rate limiting Firewall reconfiguration Dynamic topology reconfiguration 2021/2/26 NTUIM OPLAB 24

Attack-defense scenarios 2021/2/26 NTUIM OPLAB 25

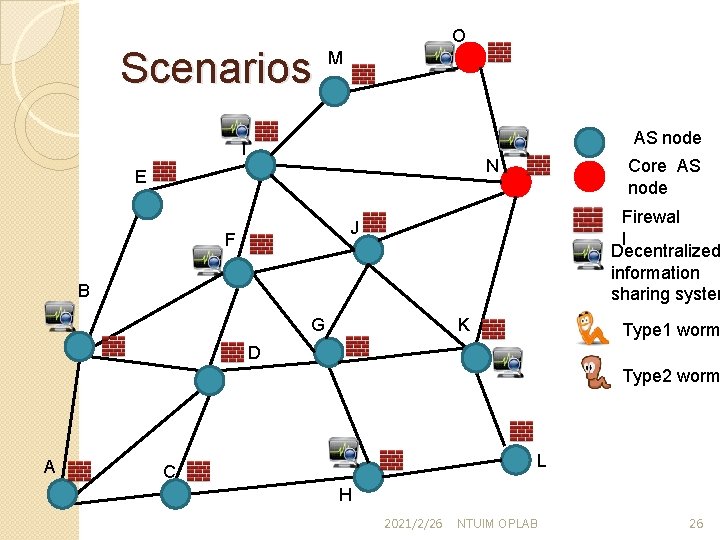
Scenarios O M AS node I Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm A L C H 2021/2/26 NTUIM OPLAB 26

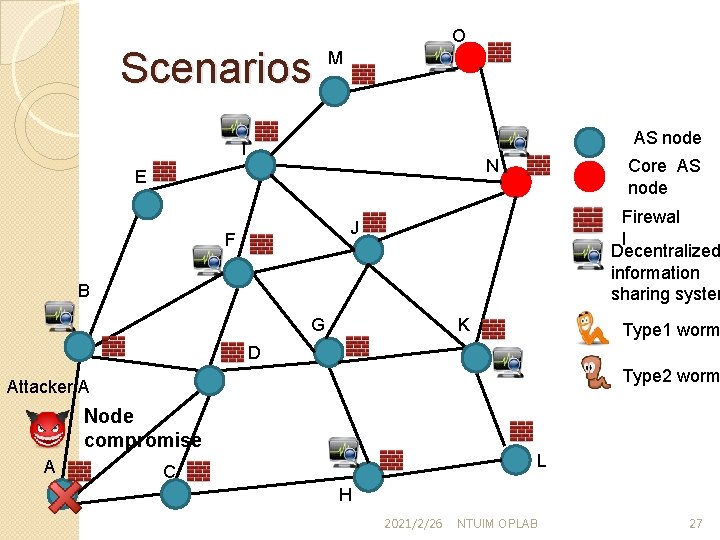
Scenarios O M AS node I Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A Node compromise A L C H 2021/2/26 NTUIM OPLAB 27

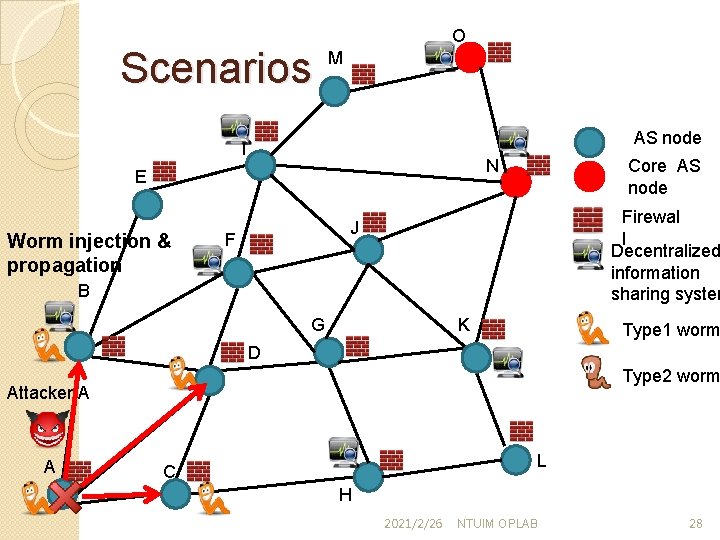
Scenarios O M AS node I Worm injection & propagation Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 28

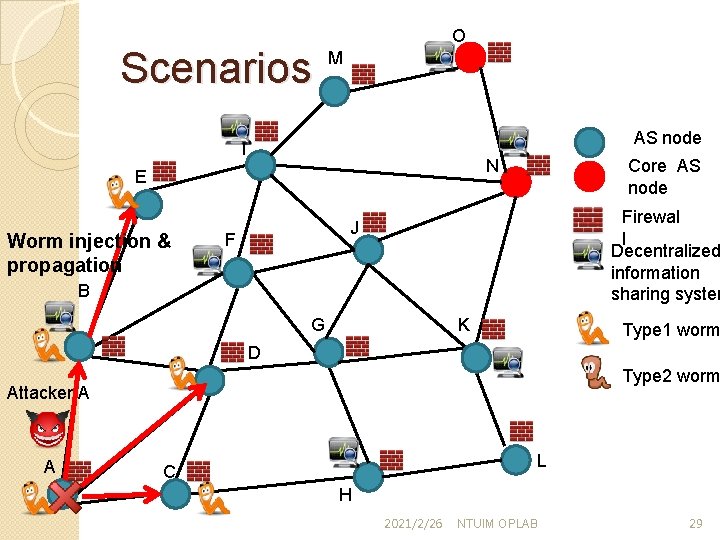
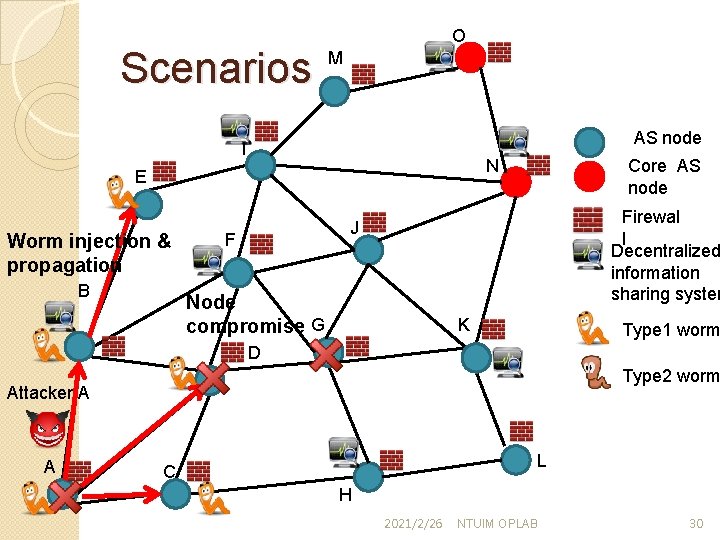
Scenarios O M AS node I Worm injection & propagation Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 29

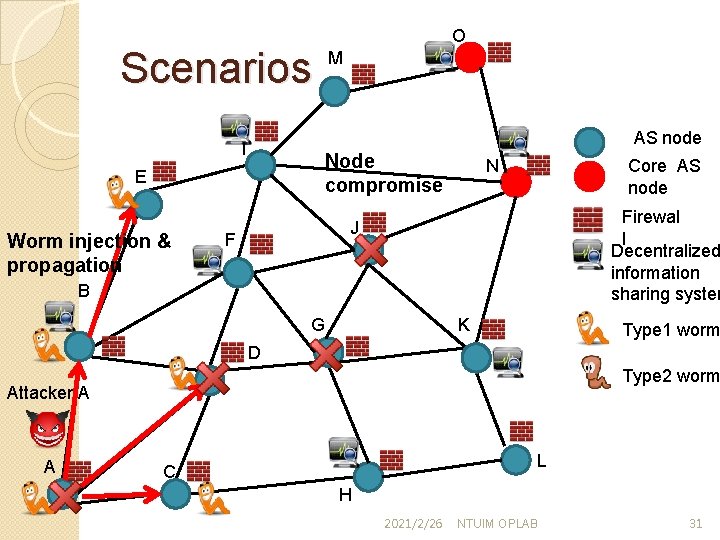
Scenarios O M AS node I Worm injection & propagation B Core AS node N E Firewal l Decentralized information sharing system J F Node compromise G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 30

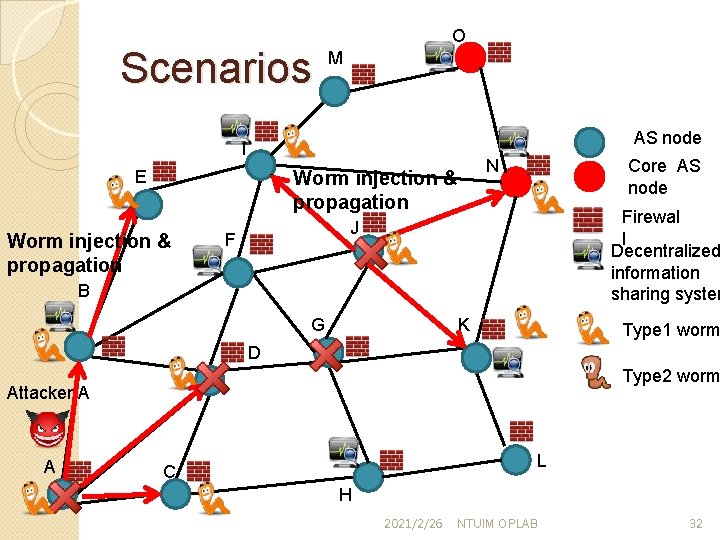
Scenarios M AS node I Node compromise E Worm injection & propagation O Core AS node N Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 31

Scenarios O M AS node I E Worm injection & propagation Core AS node N Worm injection & propagation Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 32

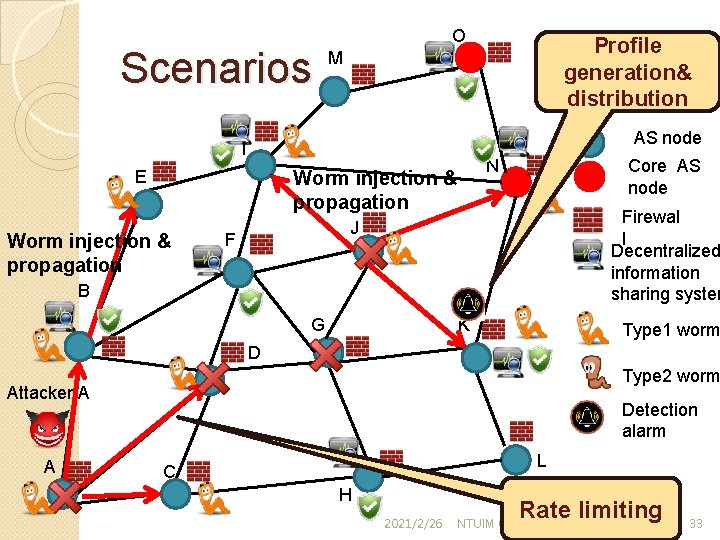
Scenarios O AS node I E Core AS node N Worm injection & propagation Profile generation& distribution M Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A Detection alarm L C H 2021/2/26 Rate limiting NTUIM OPLAB 33

Scenarios Worm injection & propagation O M Firewall reconfiguration I E AS node Core AS node N Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 34

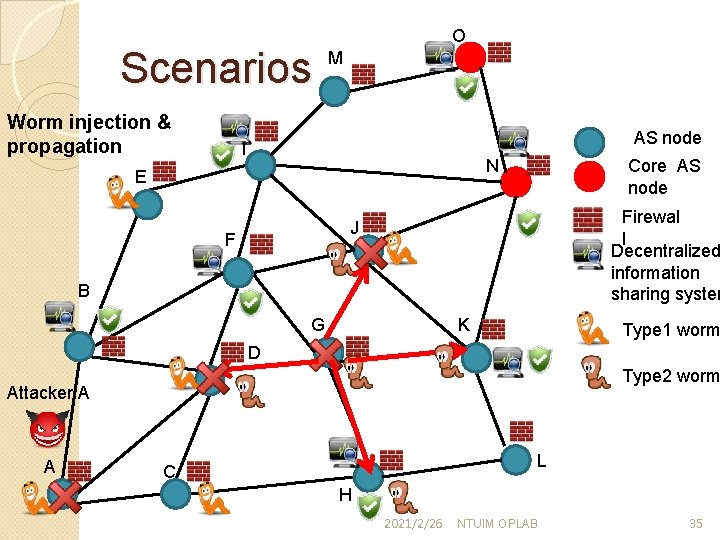
Scenarios Worm injection & propagation O M AS node I Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A L C H 2021/2/26 NTUIM OPLAB 35

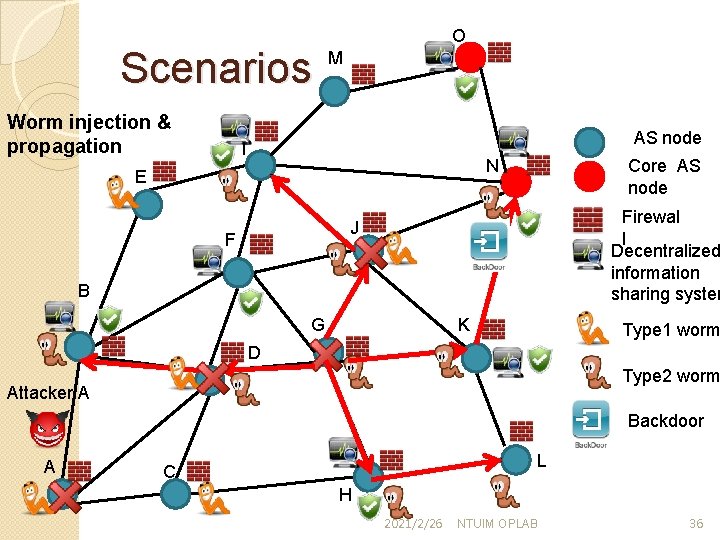
Scenarios Worm injection & propagation O M AS node I Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A Backdoor A L C H 2021/2/26 NTUIM OPLAB 36

Scenarios Worm injection & propagation O Profile generation& distribution M AS node I Core AS node N E Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A Backdoor A L C H 2021/2/26 NTUIM OPLAB Detection alarm 37

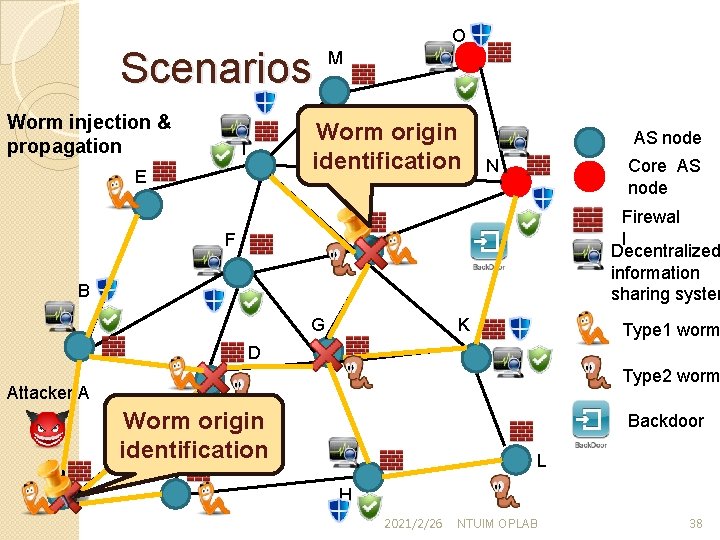
Scenarios Worm injection & propagation O M Worm origin identification I E AS node Core AS node N Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A A Worm origin identification Backdoor L C H 2021/2/26 NTUIM OPLAB 38

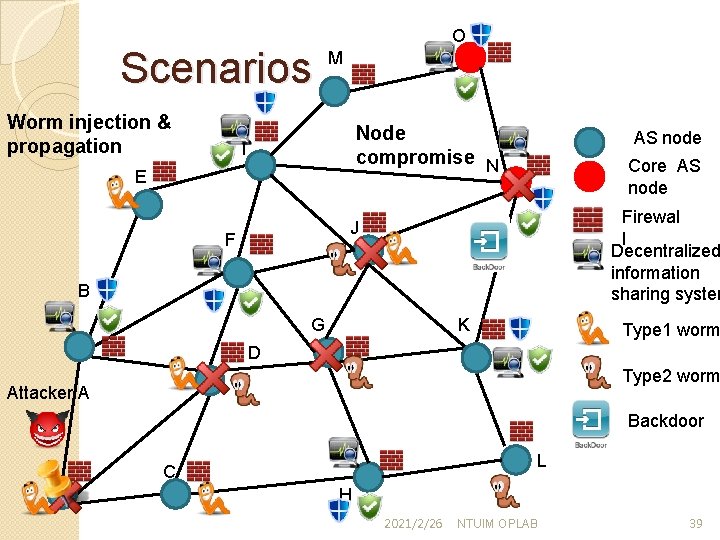
Scenarios Worm injection & propagation O M Node compromise N I E AS node Core AS node Firewal l Decentralized information sharing system J F B G K Type 1 worm D Type 2 worm Attacker A Backdoor A L C H 2021/2/26 NTUIM OPLAB 39

Thanks for your listening 2021/2/26 NTUIM OPLAB 40