Ransomware Prevention Introducing odix ltd Jan 2020 Successful







- Slides: 17

Ransomware Prevention Introducing odix ltd ©Jan 2020

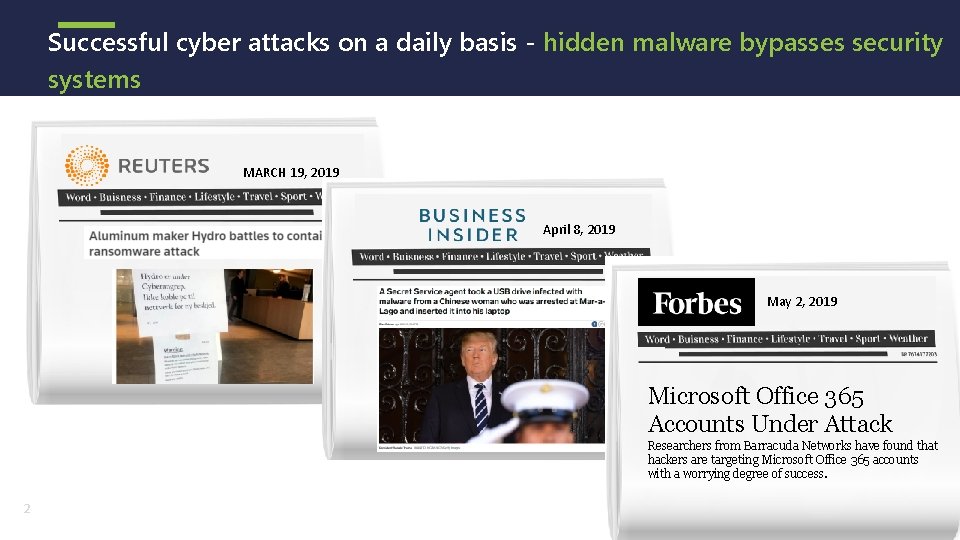
Successful cyber attacks on a daily basis - hidden malware bypasses security systems MARCH 19, 2019 April 8, 2019 “IBM Warns Customers After Shipping Them Infected USB Drives” May 2, 2019 “IBM Warns Customers After Microsoft Office 365 Shipping Them Infected USB Accounts Under Attack Drives” Researchers from Barracuda Networks have found that hackers are targeting Microsoft Office 365 accounts with a worrying degree of success. 2

odix concept is simple: Instead of trying to DETECT malware odix DISARMS malware from files 3

odix True. CDR™ highlights • Detection-less process that removes all types of malicious codes hidden within files – eliminates both known and UNKNOWN malware attacks. • Sophisticated algorithms ensure that any foreign code within a file will be “deactivated” • Support all common file types including media, documents and archives • Sanitized files retain their original format and original functionality! • Fully Support of nested documents and archives (files within files) • Zero integration • Full enforcement of company’s security policy, delivered with the odix Management Server 4

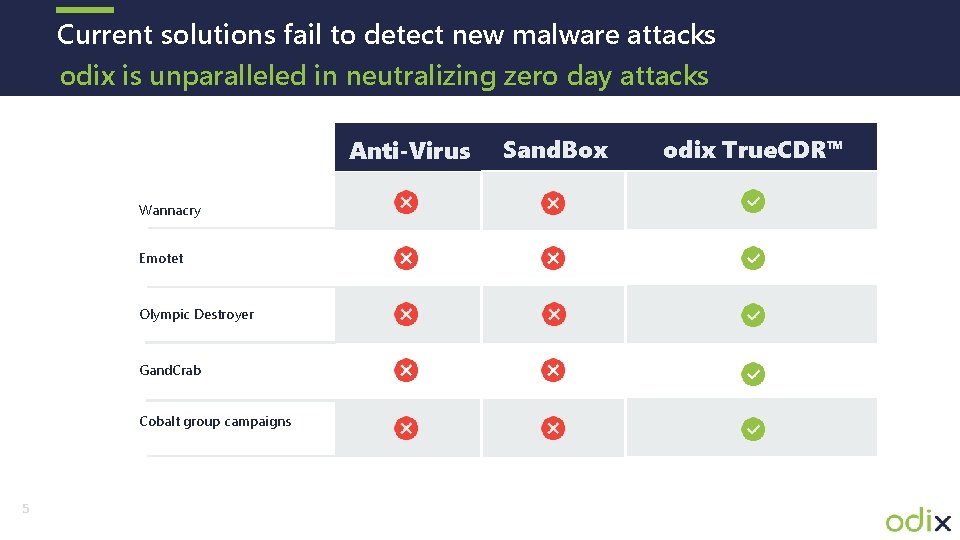
Current solutions fail to detect new malware attacks odix is unparalleled in neutralizing zero day attacks Anti-Virus Wannacry Emotet Olympic Destroyer Gand. Crab Cobalt group campaigns 5 Sand. Box odix True. CDR™

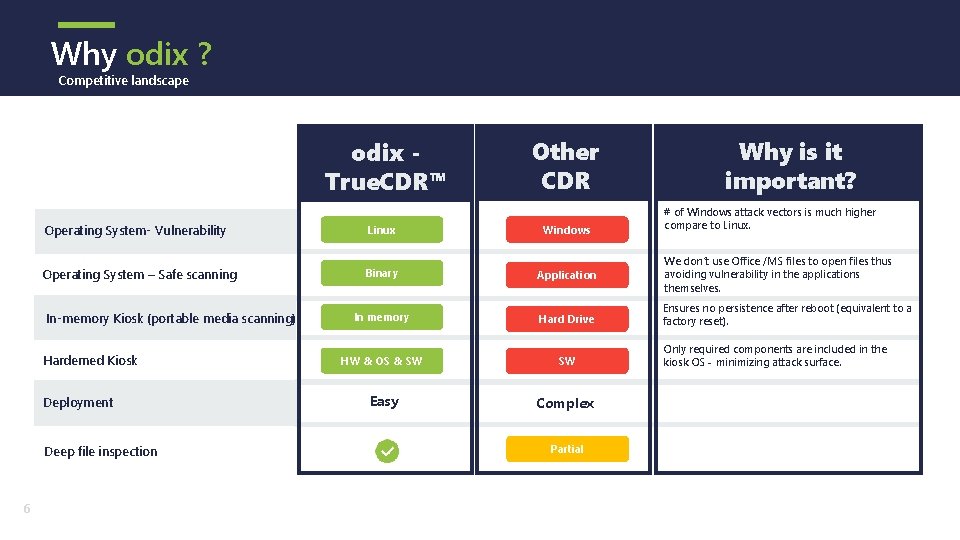
Why odix ? Competitive landscape odix True. CDR™ Why is it important? # of Windows attack vectors is much higher compare to Linux. Operating System- Vulnerability Linux Windows Operating System – Safe scanning Binary Application We don’t use Office /MS files to open files thus avoiding vulnerability in the applications themselves. In memory Hard Drive Ensures no persistence after reboot (equivalent to a factory reset). HW & OS & SW SW Easy Complex In-memory Kiosk (portable media scanning) Harderned Kiosk Deployment Deep file inspection 6 Other CDR ! Partial ! Only required components are included in the kiosk OS - minimizing attack surface.

How is it done? odix malware prevention solutions are based on its proprietary patented True. CDR™ (Content Disarmed & Reconstruction) * technology *CDR term was determined by Gartner “CDR can be used as a supplement or replacement for network sandboxing, depending on the use case” 7 “Differentiating Capabilities" listed in the "Market Analysis“ by Gartner

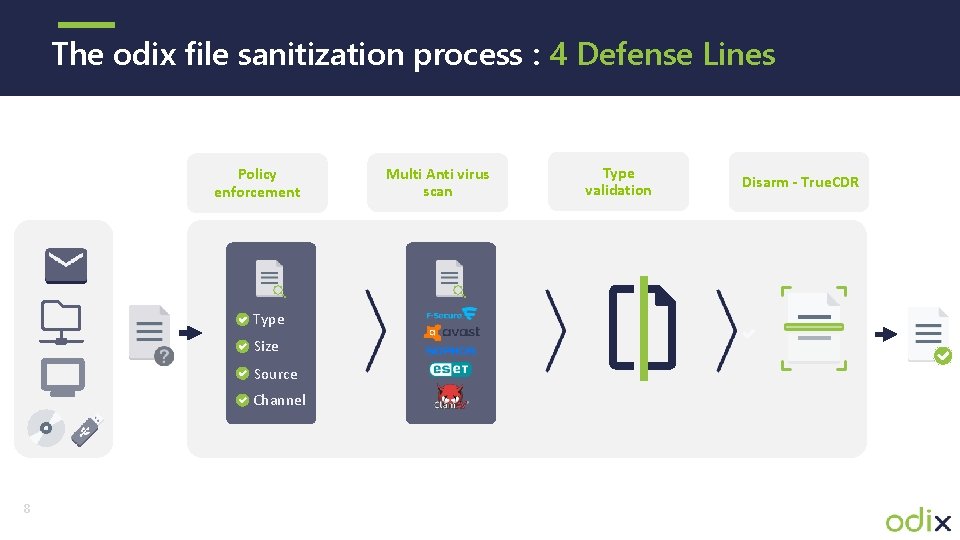
The odix file sanitization process : 4 Defense Lines Policy enforcement Type Size Source Channel 8 Multi Anti virus scan Type validation Disarm - True. CDR

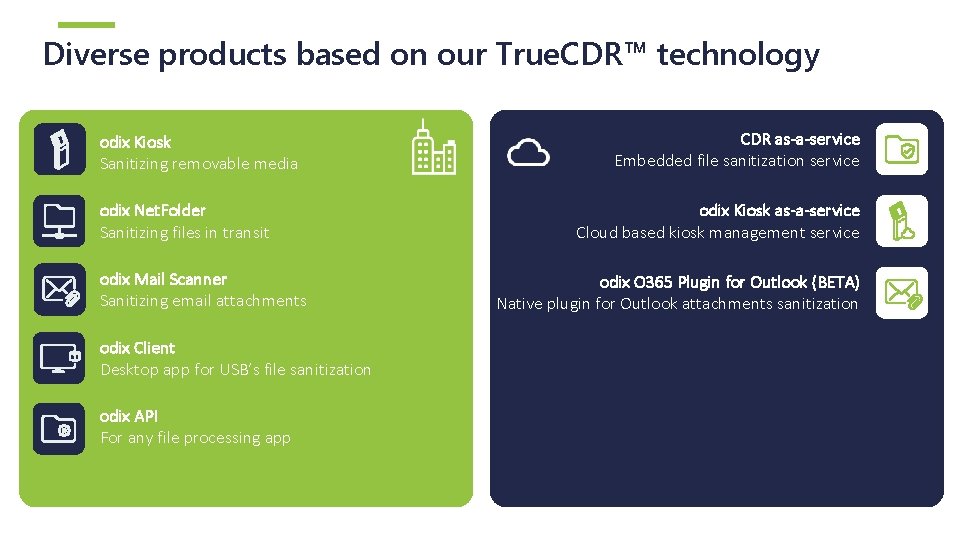
Diverse products based on our True. CDR™ technology odix Kiosk Sanitizing removable media odix Net. Folder Sanitizing files in transit odix Mail Scanner Sanitizing email attachments odix Client Desktop app for USB’s file sanitization odix API For any file processing app CDR as-a-service Embedded file sanitization service odix Kiosk as-a-service Cloud based kiosk management service odix O 365 Plugin for Outlook (BETA) Native plugin for Outlook attachments sanitization

odix ecosystem Approved and certified by leading cyber security labs 10 Channels& partners in the USA, Europe and APAC

Cross industry Customers ICS – Industrial Control Systems Digital Health Other 11 Fintech & Insurtech

odix for Office 365 12

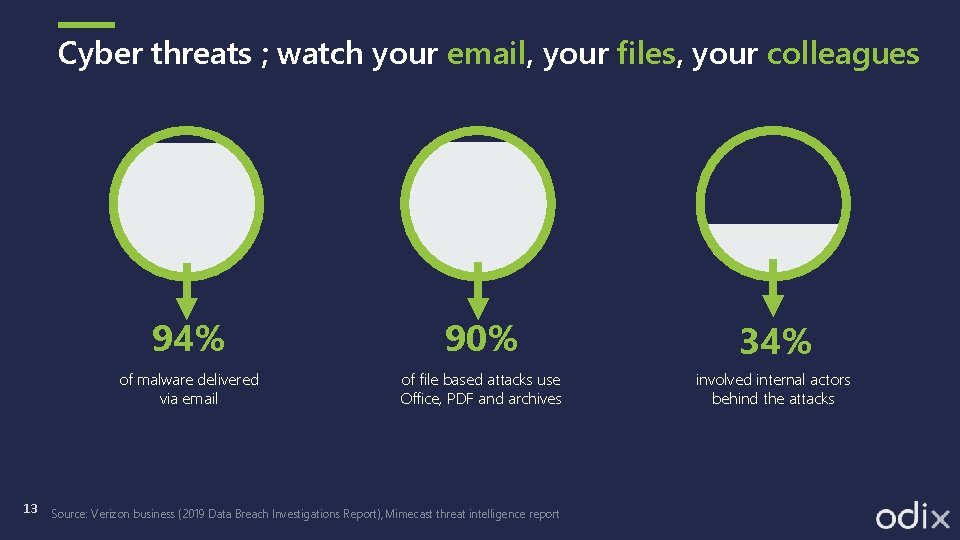
Cyber threats ; watch your email, your files, your colleagues 13 94% 90% 34% of malware delivered via email of file based attacks use Office, PDF and archives involved internal actors behind the attacks Source: Verizon business (2019 Data Breach Investigations Report), Mimecast threat intelligence report

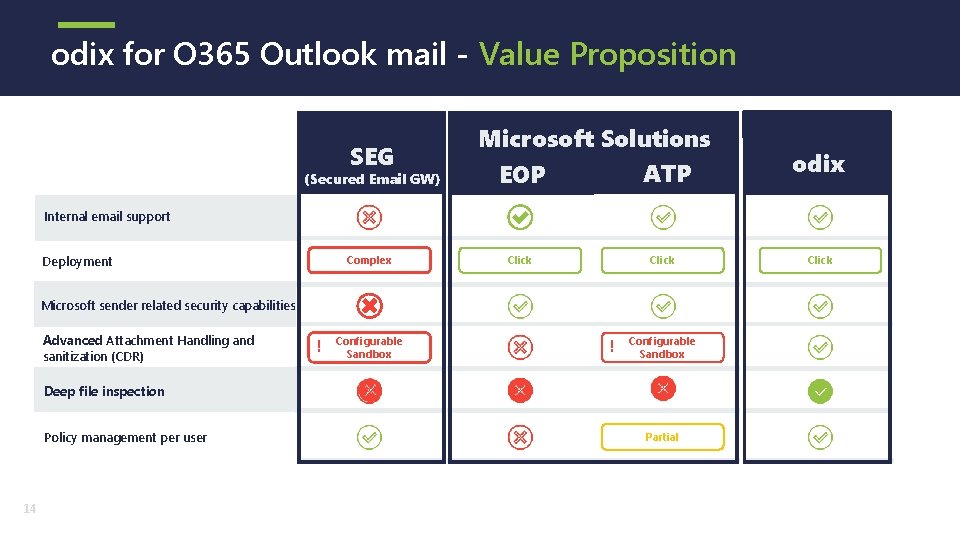
odix for O 365 Outlook mail - Value Proposition SEG (Secured Email GW) Microsoft Solutions ATP EOP odix Internal email support Deployment Complex Click Microsoft sender related security capabilities Advanced Attachment Handling and sanitization (CDR) ! Configurable Sandbox Deep file inspection Policy management per user 14 Partial Click

About odix • Privately-owned cyber security company, founded by • Dr. Oren Eytan (ret. Col. ) formerly Head of the Cyber Defense & Information Security Unit of the IDF • Mr. David Geva (ret. Col. ) formerly Head of the IDF C 4 I and Cyber Academy. • Patented unique technology : odix revolutionizes the malware prevention market with True. CDR™ disruptive technology. Sanitizing incoming/outgoing files from known and unknown malware. • Awarded € 2 M grant from the European Commission HORIZON 2020/ SMEi program • HQ in Israel, offices in USA & Luxemburg 15

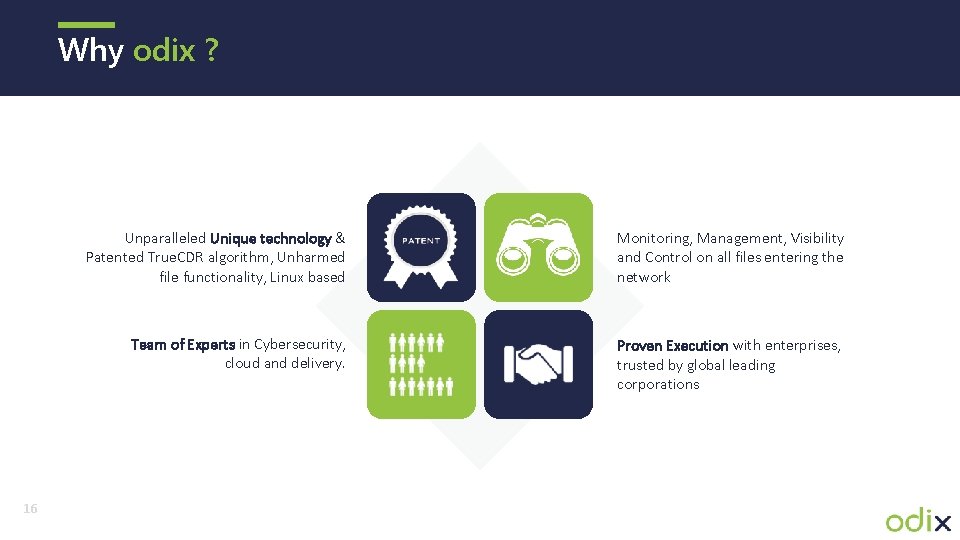
Why odix ? 16 Unparalleled Unique technology & Patented True. CDR algorithm, Unharmed file functionality, Linux based Monitoring, Management, Visibility and Control on all files entering the network Team of Experts in Cybersecurity, cloud and delivery. Proven Execution with enterprises, trusted by global leading corporations

Thank You Visit us at www. odi-x. com Contact us: info@odi-x. com Locally: karen@wriskgroupllc. com
 Primary prevention secondary prevention tertiary prevention
Primary prevention secondary prevention tertiary prevention Odix competitors
Odix competitors Cisco ransomware defense
Cisco ransomware defense Rrcc ransomware
Rrcc ransomware Ransomware auris
Ransomware auris Redoc ransomware
Redoc ransomware Chad rikansrud
Chad rikansrud Ransomware detection rogers
Ransomware detection rogers Futm ransomware
Futm ransomware Executech ransomware
Executech ransomware Ransomware mitigation strategies
Ransomware mitigation strategies Ransomware playbook flowchart
Ransomware playbook flowchart Axa ransomware
Axa ransomware Waikato dhb ransomware
Waikato dhb ransomware Ransomware hrvatska
Ransomware hrvatska Sakura 32 ransomware
Sakura 32 ransomware Apt lateral movement
Apt lateral movement Signal phrases
Signal phrases