Protocols for the Wireless Paranoid Nitin Vaidya University













- Slides: 30

Protocols for the Wireless Paranoid Nitin Vaidya University of Illinois http: //www. crhc. uiuc. edu/wireless Slightly revised version of slides used for a 2005 INFOCOM (Miami) panel on Paranoid Protocol Design for Wireless Networks March 16, 2005 Other panelists: Jean-Pierre Hubaux (Moderator), Bill Arbaugh, Ed Knightly, Adrian Perrig 1

Disclaimer If you review my research proposals, ignore everything I say here 2

Panel’s Premise g Wireless networks need more paranoid protocols than wired networks 3

Wireless Networks g Greater paranoia may be desirable in wireless networks i. Easier to “tap” into i. Limited g resources Incentive to cheat Programmable devices provide means to cheat But … 4

What are Paranoid Protocols Anyway? 5

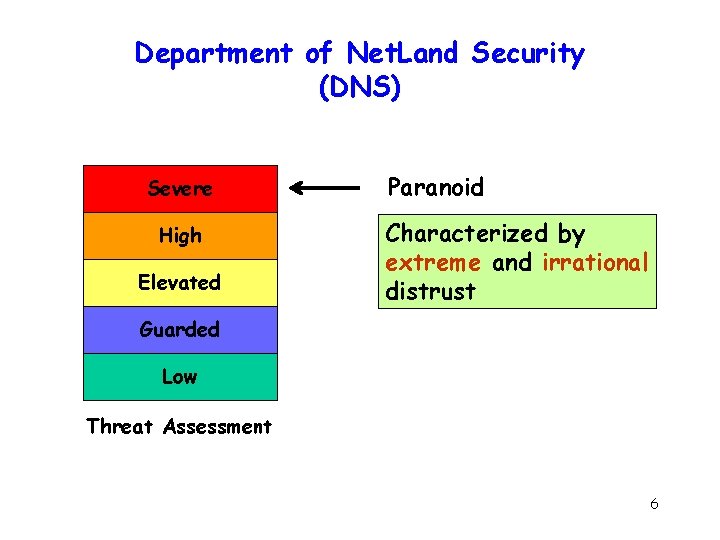
Department of Net. Land Security (DNS) Severe High Elevated Paranoid Characterized by extreme and irrational distrust Guarded Low Threat Assessment 6

Paranoid Design Principles g Everything that can go wrong, will - Murphy’s Law g Protect against everything 7

Research Community’s Response g Enumerate all possible ways things can go wrong g Separate solution for each of the ills Not quite the right approach è Proof by Example 3 Mistakes often made 8

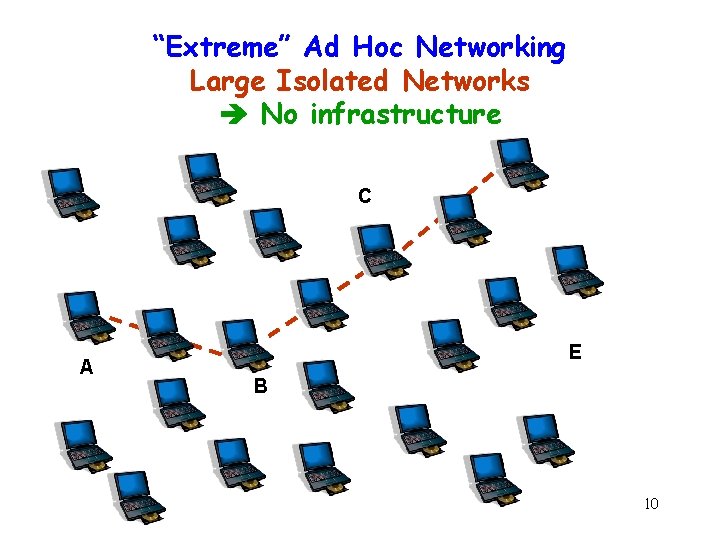
Mistake 1: Assuming Extreme Scenario as the Common Case Ad hoc network are coming ! Ad hoc networks are coming !! 9

“Extreme” Ad Hoc Networking Large Isolated Networks No infrastructure C A E B 10

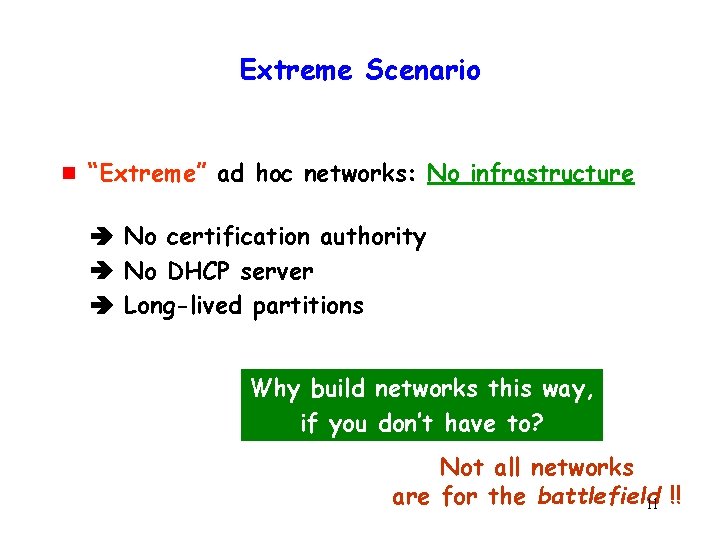
Extreme Scenario g “Extreme” ad hoc networks: No infrastructure No certification authority No DHCP server Long-lived partitions Why build networks this way, if you don’t have to? Not all networks are for the battlefield 11 !!

Extreme Ad Hoc Networks g g Model acceptable when exploring design space for MAC and routing Assuming same model for “security” can lead to unnecessary complexity 12

More Likely Ad Hoc Networks Access to Infrastructure or Small internet C A E B 13

More Likely Ad Hoc Networks Access to Infrastructure or Small 14

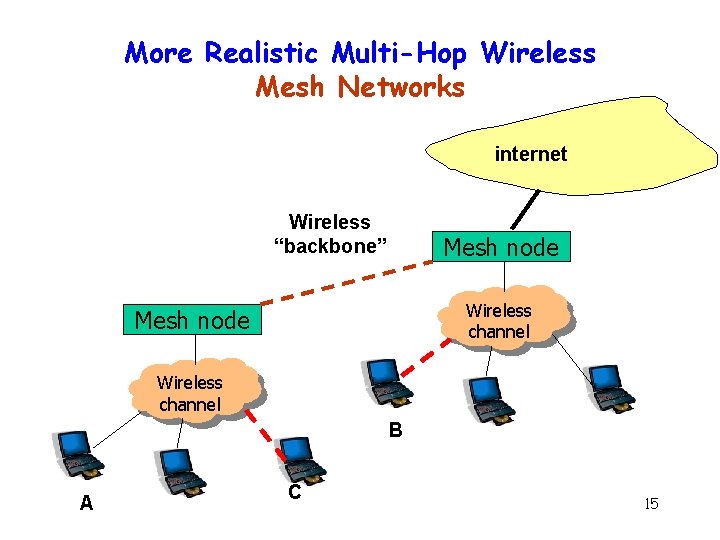
More Realistic Multi-Hop Wireless Mesh Networks internet Wireless “backbone” Mesh node Wireless channel B A C 15

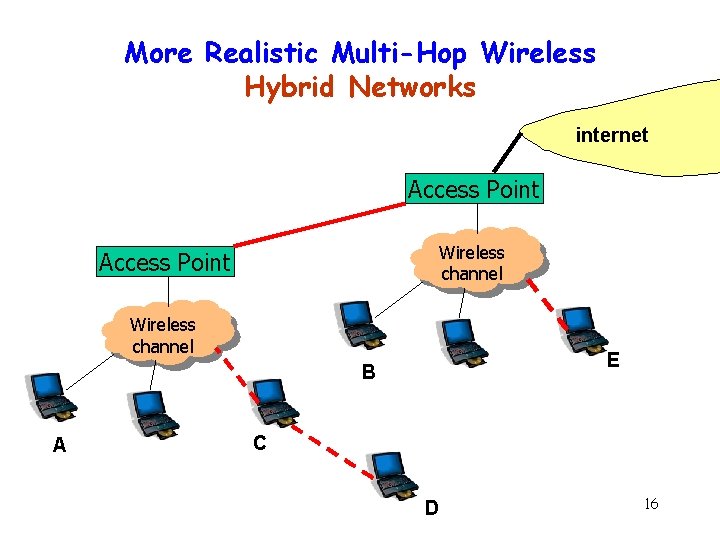
More Realistic Multi-Hop Wireless Hybrid Networks internet Access Point Wireless channel E B A C D 16

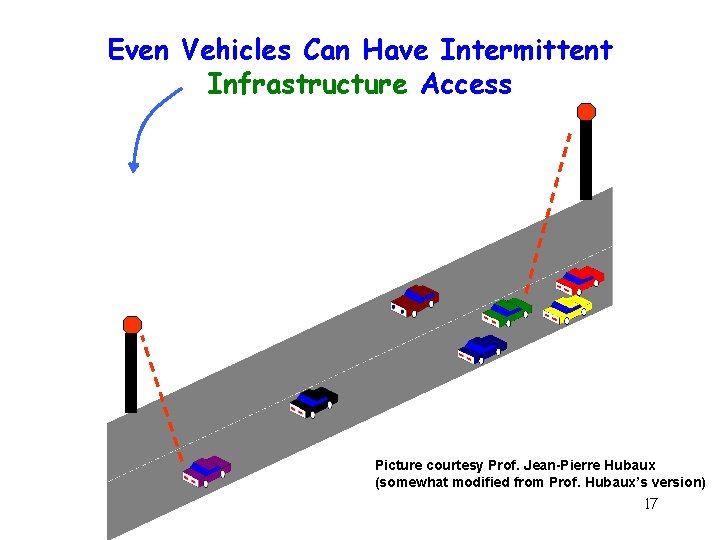
Even Vehicles Can Have Intermittent Infrastructure Access Picture courtesy Prof. Jean-Pierre Hubaux (somewhat modified from Prof. Hubaux’s version) 17

Multi-Hop Wireless is Here (Summary) g Multi-hop wireless, but “infrastructure” can be accessed selectively g Not all enumerable scenarios are relevant Design protocols for the likely scenarios 18

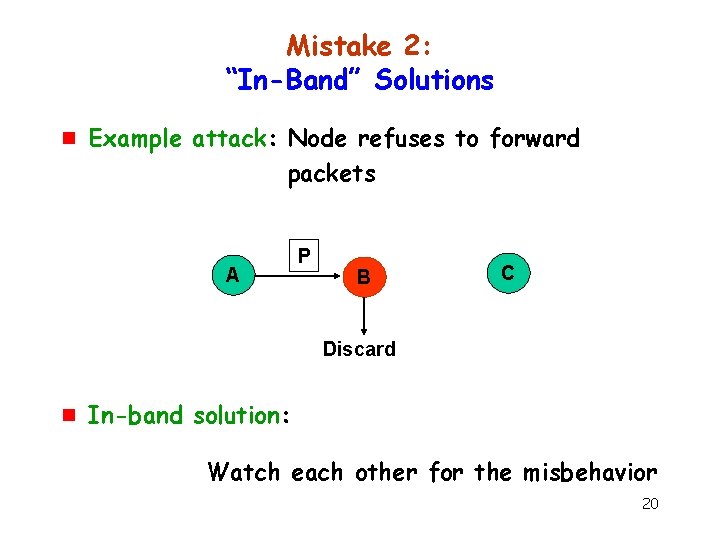
Mistake 2: “In-Band” Solutions g “In-band” solutions Solution tied closely to attack 19

Mistake 2: “In-Band” Solutions g Example attack: Node refuses to forward packets A P B C Discard g In-band solution: Watch each other for the misbehavior 20

Out-of-Band Solutions Often More Practical 1. 2. Disincentives for not forwarding packets Misbehavior translates to poor performance Re-route around “bad” parts of the network Single out-of-band solution can help with many attacks 21

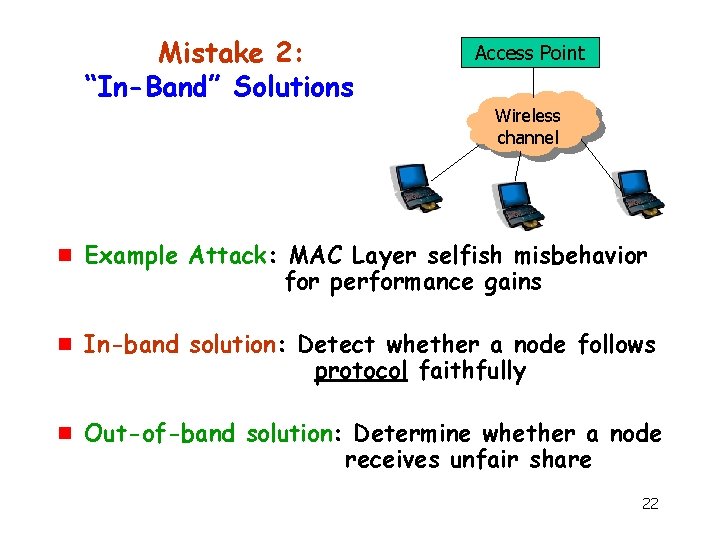
Mistake 2: “In-Band” Solutions Access Point Wireless channel g g g Example Attack: MAC Layer selfish misbehavior for performance gains In-band solution: Detect whether a node follows protocol faithfully Out-of-band solution: Determine whether a node receives unfair share 22

Out-of-Band Solutions (Summary) g Out-of-band solutions often superior, and easier to implement 23

Mistake 3 Wireless = Wired Equivalent g Many protocols work correctly only when nodes see identical wireless channel status 24

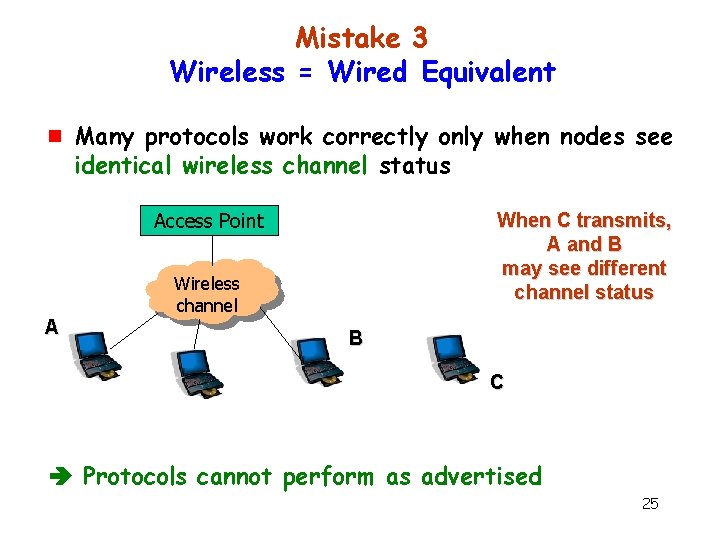
Mistake 3 Wireless = Wired Equivalent g Many protocols work correctly only when nodes see identical wireless channel status Access Point When C transmits, A and B may see different channel status Wireless channel A B C Protocols cannot perform as advertised 25

Mistake 3 Wireless = Wired Equivalent g g Under realistic channel conditions, some of the attacks also difficult to launch undetected Example: Certain “wormhole” attacks Ignore such attacks? 26

Mistake 3 (Summary) g Pay attention to the physical layer g Wired equivalent for wireless not always reasonable g Use solutions that do not rely on such assumptions Out-of-band solutions, removed from the cause, may be less prone 27

Conclusion Need to protect wireless networks … g g but Not everything that can go wrong is worth the cost of protection Develop small set of solutions for a large problem space g Know the wireless channel 28

Conclusion Wireless networks are complex Focus on the real problems, ignore the imaginary 29

Thanks ! nhv@uiuc. edu 30