Some Issues in Ad Hoc Networks Nitin Vaidya















![Duplicate Address Detection in Ad Hoc Networks g Several proposals g One example [Perkins]: Duplicate Address Detection in Ad Hoc Networks g Several proposals g One example [Perkins]:](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-20.jpg)








![Backoff Example g Choose backoff value B in range [0, CW] g Count down Backoff Example g Choose backoff value B in range [0, CW] g Count down](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-43.jpg)

![Game Theoretic Solutions [Mac. Kenzie] g g Assumes there is some cost for transmitting Game Theoretic Solutions [Mac. Kenzie] g g Assumes there is some cost for transmitting](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-46.jpg)








![Link Reversal Algorithm [Gafni 81] (Routing Protocol) A B F C E G D Link Reversal Algorithm [Gafni 81] (Routing Protocol) A B F C E G D](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-65.jpg)
![Link Reversal Algorithm [Gafni 81] A C B E D F G Links are Link Reversal Algorithm [Gafni 81] A C B E D F G Links are](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-66.jpg)
![Mutual Exclusion in Static Networks [Raymond 89] g g Static topology Spanning tree with Mutual Exclusion in Static Networks [Raymond 89] g g Static topology Spanning tree with](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-74.jpg)









- Slides: 98

Some Issues in Ad Hoc Networks Nitin Vaidya University of Illinois at Urbana-Champaign www. crhc. uiuc. edu/~nhv Keynote talk presented at the International Workshop on Theoretical Aspects of Wireless Ad Hoc, Sensor, and Peer-to-Peer Networks Illinois Institute of Technology, Chicago, June 11, 2004 © 2004 Nitin Vaidya 1

Outline g Preliminaries g Advertising g Preaching 2

Ad Hoc Networks g g Formed by wireless hosts which may be mobile Without necessarily using a pre-existing infrastructure • Hybrid architectures using infrastructure likely in many applications 3

Why Ad Hoc Networks ? g Potential ease of deployment g Decreased dependence on infrastructure 4

Many Potential Applications g Personal area networking g Military environments g Civilian environments g Emergency operations icell phone, laptop, ear phone, wrist watch isoldiers, tanks, planes itaxi cab network imeeting rooms isports stadiums iboats, small aircraft isearch-and-rescue ipolicing and fire fighting 5

Challenges (Opportunities) g g g g Broadcast nature of the wireless medium Limited wireless transmission range – Hidden terminal problem Packet losses due to transmission errors Mobility-induced route changes Mobility-induced packet losses Battery constraints Potentially frequent network partitions Ease of snooping on wireless transmissions (security hazard) 6

State of the Art g Lot of research activity on: i. Routing i. Medium access control i. Quality of service 7

State of the Art g More recently … i. Capacity of wireless networks << Information theory community i. Graph-theoretic problems << Algorithms/theory community – Pure wireless networks – Hybrid networks – Delay-throughput trade-off – – Topology control Dominating sets Connectivity problems Coverage problems in sensor networks 8

State of the Art g Many more (academic) problems … rich area g (Too) Many conferences i. Mobi. Hoc i. Sen. Sys i. MASS i. SECON i… 9

What’s Lacking? g Real applications still lacking (beyond military) i. Hard to evaluate protocols in a vacuum g But there is hope … applications on the horizon i. Community networks starting to use ad hoc routing i. Vehicular networks i. Sensor networks 10

What’s Lacking g Primitives to build distributed applications i. Much work on distributed algorithms on fixed and dynamic networks wherein dynamism comes from “random” link failures i. But little on ad hoc networks, where the dynamism comes from node mobility and channel variations i. Need to revisit distributed computing problems in the new context 11

Outline g Preliminaries g Advertising g Preaching 12

Our Research Themes Exploiting physical layer capabilities g g Protocols for directional antennas Rate adaptation Power control & Power save mechanisms Multi-channel mechanisms 13

Our Research Themes Distributed algorithms for ad hoc networks g g Address assignment Mutual exclusion Leader election Token circulation 14

Our Research Themes Misbehavior in Wireless Networks g Protocol design for misbehavior detection 15

Some of our past research … g g g Weak duplicate address detection Misbehavior detection Mutual exclusion 16

Weak Duplicate Address Detection 17

Address Assignment g g Dynamic auto-configuration important for autonomous operation of an ad hoc network Goal: Assign each node a unique address OR Assign each address to at most one node g Can be viewed as distributed mutual exclusion with an address being a resource 18

Auto-Configuration in Ad Hoc Networks g g Worst case network delays may be unknown, or highly variable, or unbounded Partitions may occur, and merge 19
![Duplicate Address Detection in Ad Hoc Networks g Several proposals g One example Perkins Duplicate Address Detection in Ad Hoc Networks g Several proposals g One example [Perkins]:](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-20.jpg)
Duplicate Address Detection in Ad Hoc Networks g Several proposals g One example [Perkins]: i. Host picks an address randomly i. Host performs route discovery for the chosen address i. If a route reply is received, address duplication is detected 20

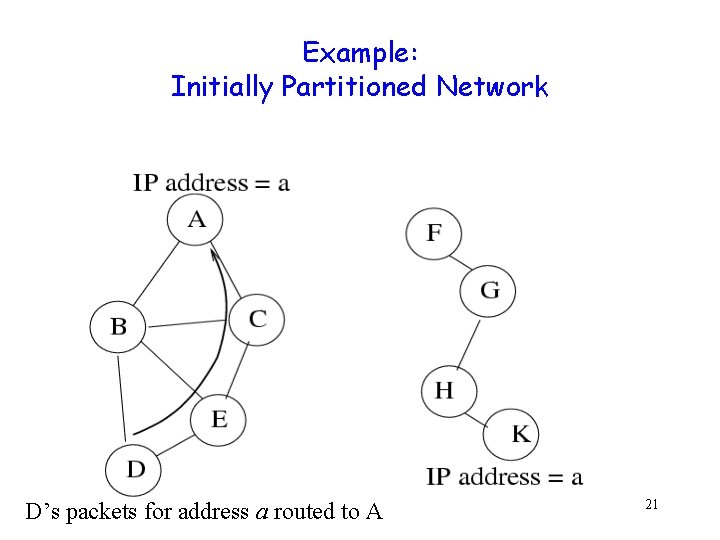
Example: Initially Partitioned Network D’s packets for address a routed to A 21

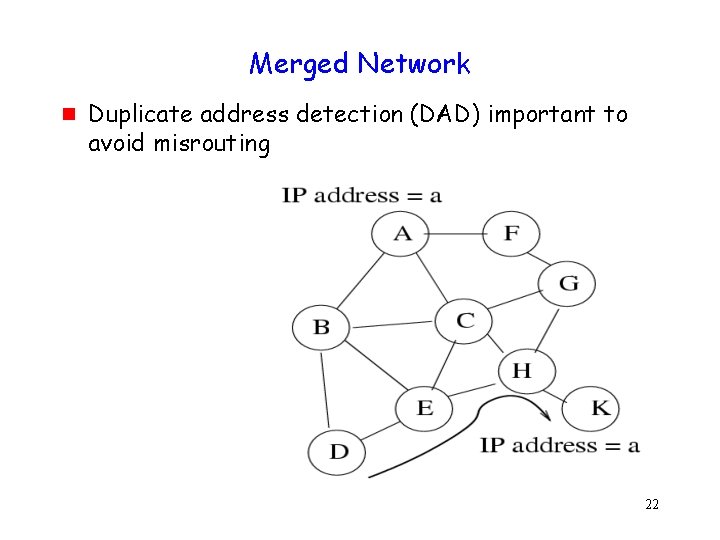
Merged Network g Duplicate address detection (DAD) important to avoid misrouting 22

Strong DAD g g Detect duplicate addresses within t seconds Not possible to guarantee strong DAD in presence of unbounded delays i. May occur due to partitions i. Even when delays are bounded, bound may be difficult to calculate Unknown network size • 23

DAD g Strong DAD impossible with unbounded delay g How to achieve DAD ? 24

Design Principle If you cannot solve a problem Change the problem 25

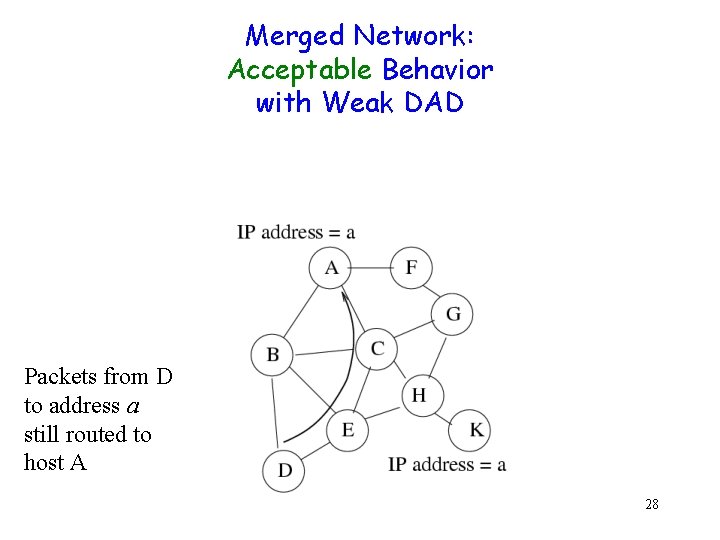
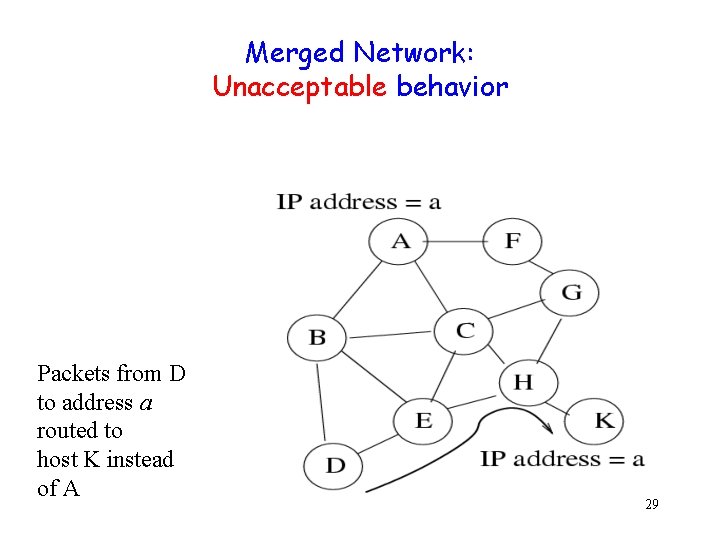
Weak DAD: Requirement Packets from a given host to a given address should be routed to the same destination, despite duplication of the address 26

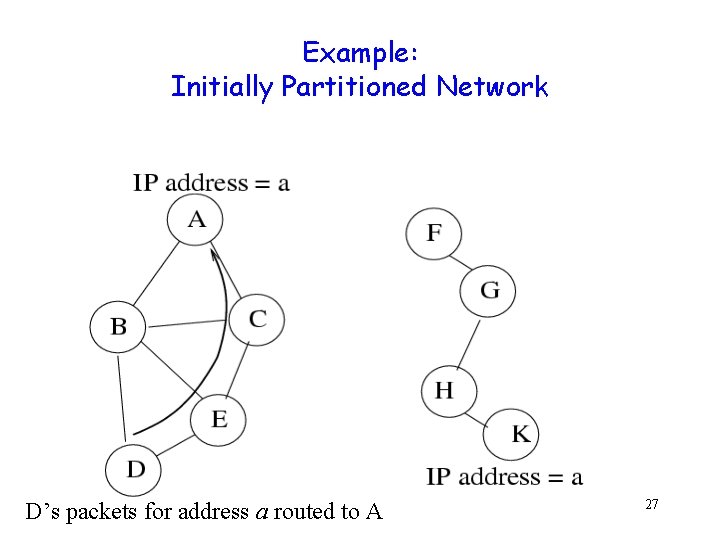
Example: Initially Partitioned Network D’s packets for address a routed to A 27

Merged Network: Acceptable Behavior with Weak DAD Packets from D to address a still routed to host A 28

Merged Network: Unacceptable behavior Packets from D to address a routed to host K instead of A 29

Weak DAD: Implementation g Integrate duplicate address detection with route maintenance 30

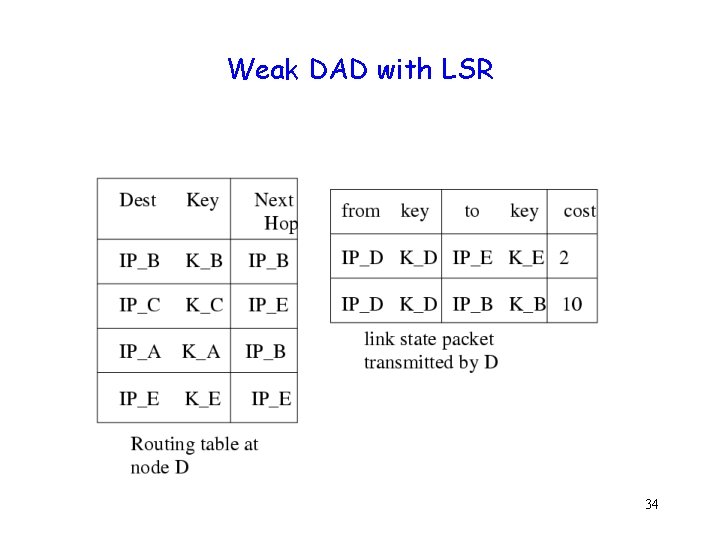
Weak DAD with Link State Routing g g Each host has a unique (with high probability) key i. May include MAC address, serial number, … i. May be large in size In all routing-related packets (link state updates) IP addresses tagged by keys i (IP, key) pair 31

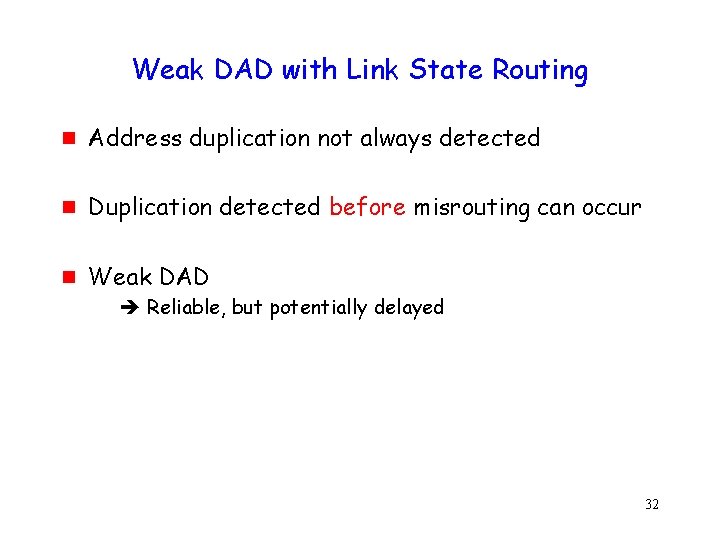
Weak DAD with Link State Routing g Address duplication not always detected g Duplication detected before misrouting can occur g Weak DAD Reliable, but potentially delayed 32

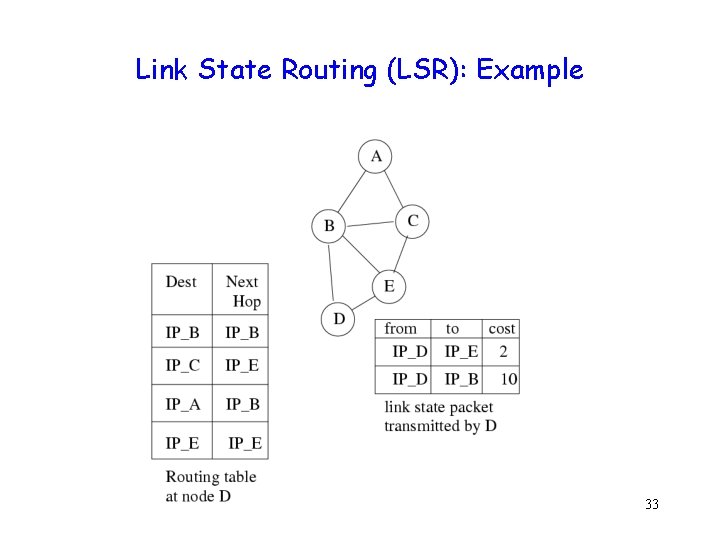
Link State Routing (LSR): Example 33

Weak DAD with LSR 34

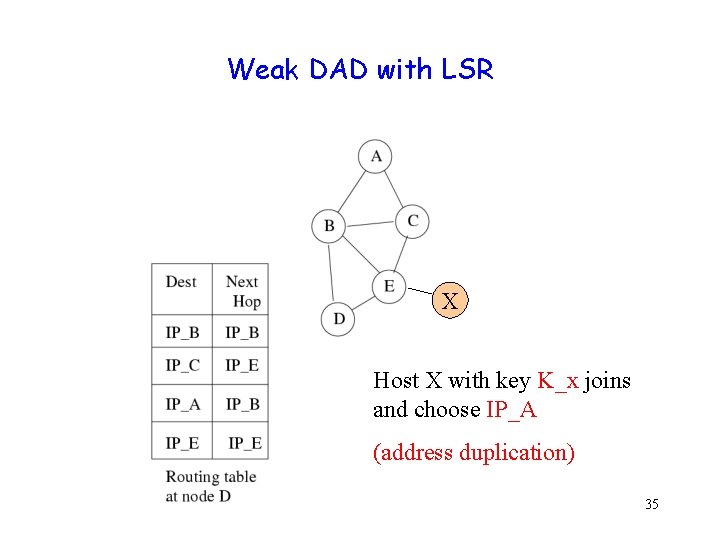
Weak DAD with LSR X Host X with key K_x joins and choose IP_A (address duplication) 35

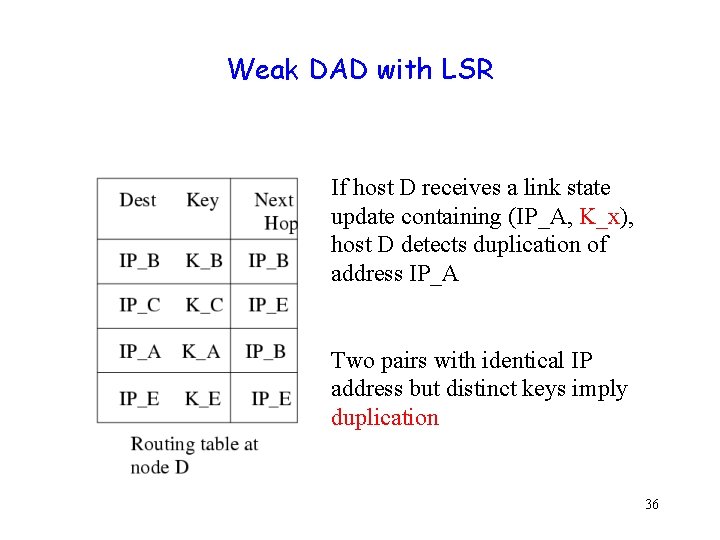
Weak DAD with LSR If host D receives a link state update containing (IP_A, K_x), host D detects duplication of address IP_A Two pairs with identical IP address but distinct keys imply duplication 36

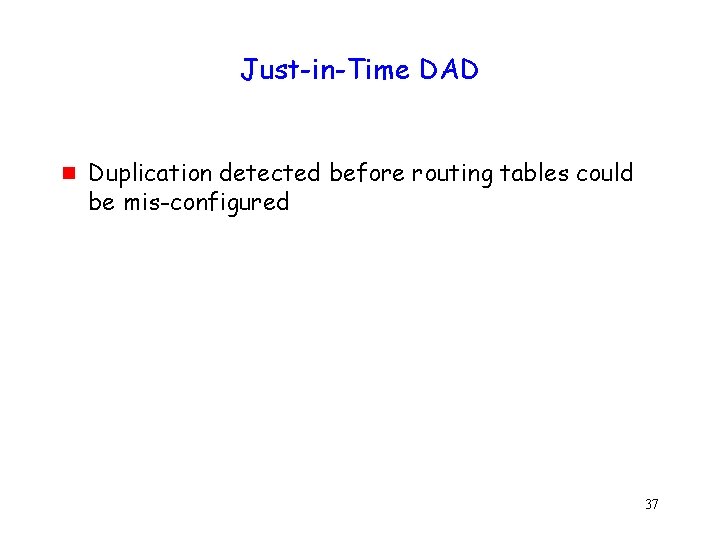
Just-in-Time DAD g Duplication detected before routing tables could be mis-configured 37

Moral of the Story g g Traditionally, address assignment and routing are independent algorithms Duplicate address detection integrated with route maintenance can provide stronger properties 38

Misbehavior Handling Joint work with Pradeep Kyasanur 39

Problem Definition Access Point n Wireless channel A B n A Nodes are required to follow Medium Access Control (MAC) rules Nodes can benefit by misbehaving B 40

IEEE 802. 11 overview g g Distributed Coordination Function (DCF) i. Widely used for channel access DCF is a Carrier Sense Multiple Access/ Collision Avoidance (CSMA/CA) protocol 41

CSMA/CA g g Don’t transmit when channel is busy Defer transmission for a random duration on idle channel 42
![Backoff Example g Choose backoff value B in range 0 CW g Count down Backoff Example g Choose backoff value B in range [0, CW] g Count down](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-43.jpg)
Backoff Example g Choose backoff value B in range [0, CW] g Count down backoff by 1 every idle slot i. CW is the Contention Window B 1=15 S 1 B 1=0 B 1=20 Transmit wait Transmit CW=31 S 2 B 2=25 B 2=10 43

Possible Misbehavior g Backoff from biased distribution i. Example: Always select a small backoff value B 1 = 1 Misbehaving node Transmit Well-behaved node wait B 2 = 20 B 2 = 19 44

Potential Solutions g Prevent misbehavior g Detect misbehavior g Penalize misbehavior 45
![Game Theoretic Solutions Mac Kenzie g g Assumes there is some cost for transmitting Game Theoretic Solutions [Mac. Kenzie] g g Assumes there is some cost for transmitting](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-46.jpg)
Game Theoretic Solutions [Mac. Kenzie] g g Assumes there is some cost for transmitting Nodes independently adjust access probability Under some assumptions, network reaches a fair equilibrium Game theoretic solutions to the misbehavior problem so far assume complete knowledge of the channel (difficult to have in multi-hop networks) i. Not yet clear whether partial information is adequate 46

Charging g Charge for transmitted packets g Transmitting more packets costs more g Disadvantages i. Per-packet charging can still allow misbehavior that decreases the user’s delay i. Need to implement charging mechanism 47

Goals of proposed scheme g Detect misbehavior g Penalize misbehavior 48

Detecting Misbehavior g g g Observe each node If a node does not wait long enough before transmitting, then conclude that it is misbehaving Penalize the misbehaving node 49

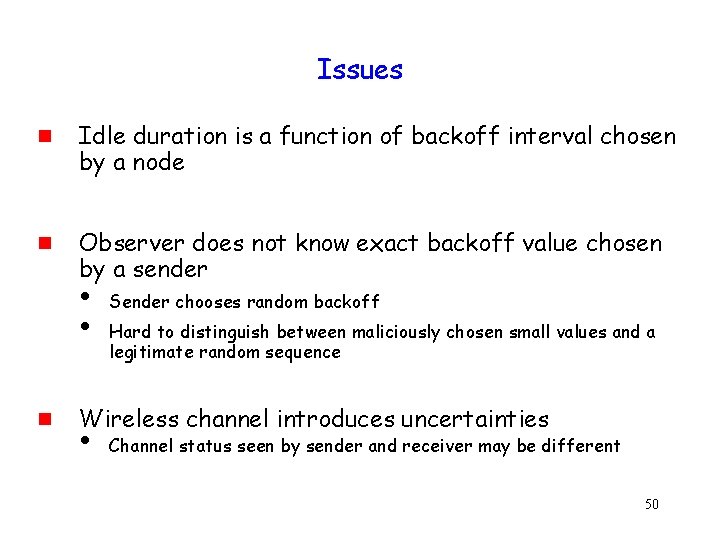
Issues g g Idle duration is a function of backoff interval chosen by a node Observer does not know exact backoff value chosen by a sender i Sender chooses random backoff i Hard to distinguish between maliciously chosen small values and a legitimate random sequence g Wireless channel introduces uncertainties i Channel status seen by sender and receiver may be different 50

Potential Solution: Use long-term statistics g g g Observe backoffs chosen by a sender over multiple packets Backoff values not from expected distribution Misbehavior Longer delay in detection, since the distribution of non-deterministic backoff must be determined 51

A Simpler Approach g Remove the non-determinism 52

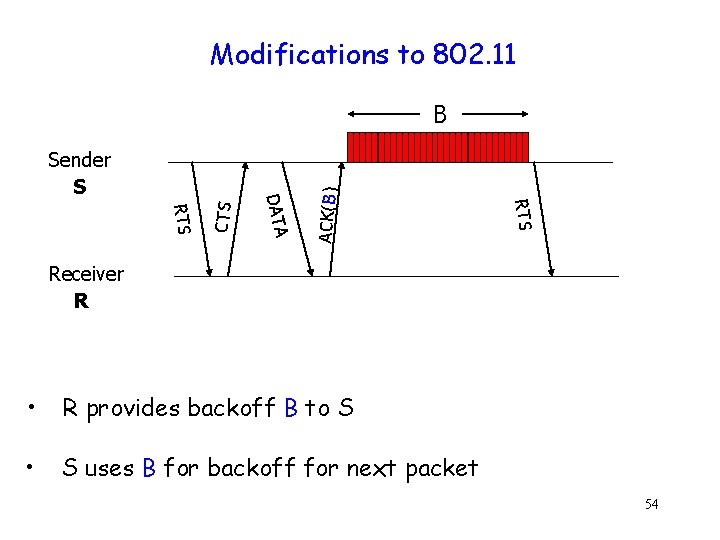
A Simpler Approach g g Receiver provides backoff values to sender Modification does not significantly change 802. 11 behavior 53

Modifications to 802. 11 CTS RTS DATA Sender S ACK(B) B Receiver R • R provides backoff B to S • S uses B for backoff for next packet 54

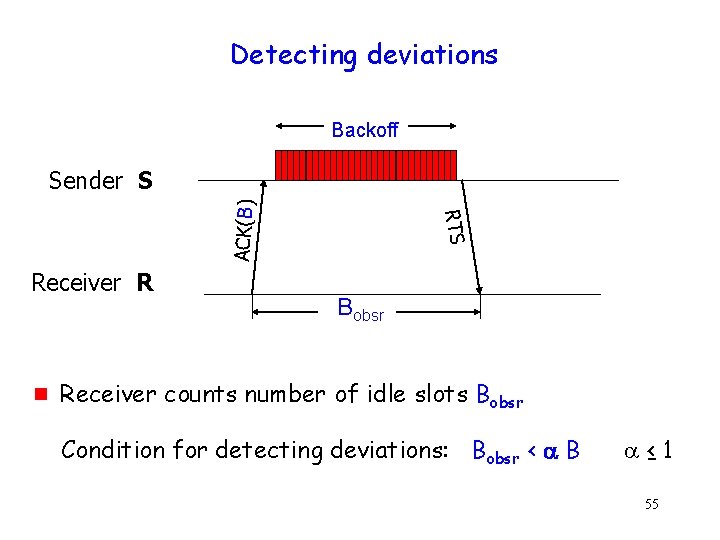
Detecting deviations Backoff Receiver R g RTS ACK(B) Sender S Bobsr Receiver counts number of idle slots Bobsr Condition for detecting deviations: Bobsr < B ≤ 1 55

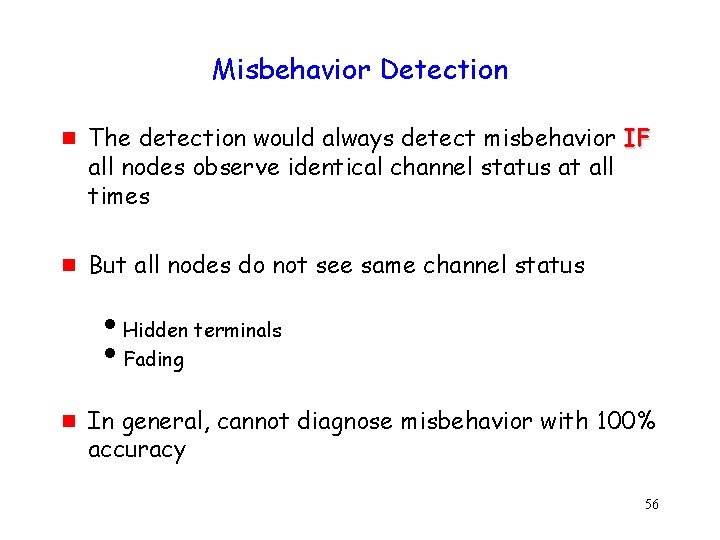
Misbehavior Detection g g The detection would always detect misbehavior IF all nodes observe identical channel status at all times But all nodes do not see same channel status i. Hidden terminals i. Fading g In general, cannot diagnose misbehavior with 100% accuracy 56

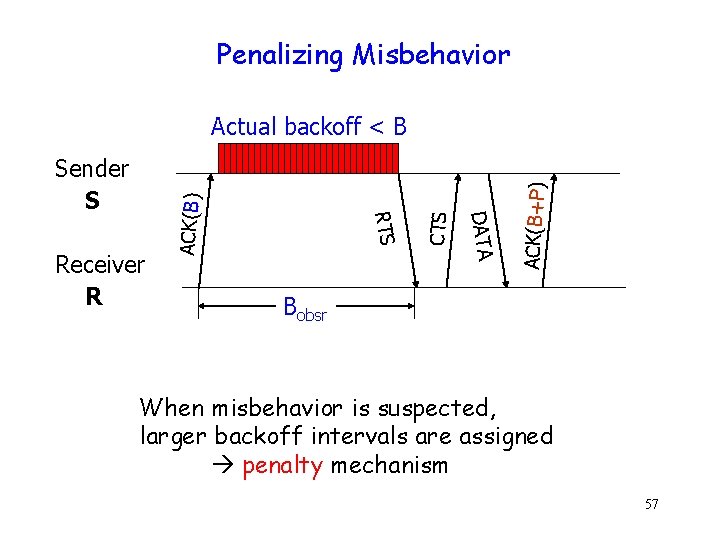
Penalizing Misbehavior ACK(B+P) CTS DATA Receiver R RTS Sender S ACK(B) Actual backoff < B Bobsr When misbehavior is suspected, larger backoff intervals are assigned penalty mechanism 57

Penalty Scheme g g Misbehaving sender has two options i. Ignore assigned penalty Easier to detect i. Follow assigned penalty No throughput gain With penalty, sender has to misbehave more for same throughput gain 58

Diagnosing Misbehavior g g If misbehavior suspected for “long enough” duration, conclude that the misbehavior is intentional Higher layers / administrator can be informed of misbehavior 59

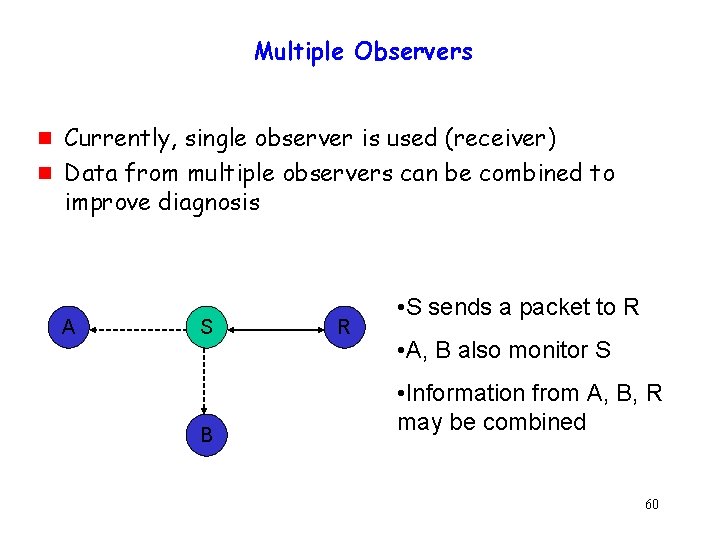
Multiple Observers g g Currently, single observer is used (receiver) Data from multiple observers can be combined to improve diagnosis A S B R • S sends a packet to R • A, B also monitor S • Information from A, B, R may be combined 60

Moral of the Story g g g MAC layer misbehavior can severely affect throughput of well-behaved nodes Improving predictability improves ability to detect misbehavior Open issues: i. Using multiple observers i. Integrating diagnosis with higher layers 61

Distributed Mutual Exclusion Joint work with Jennifer Welch and Jennifer Walter 62

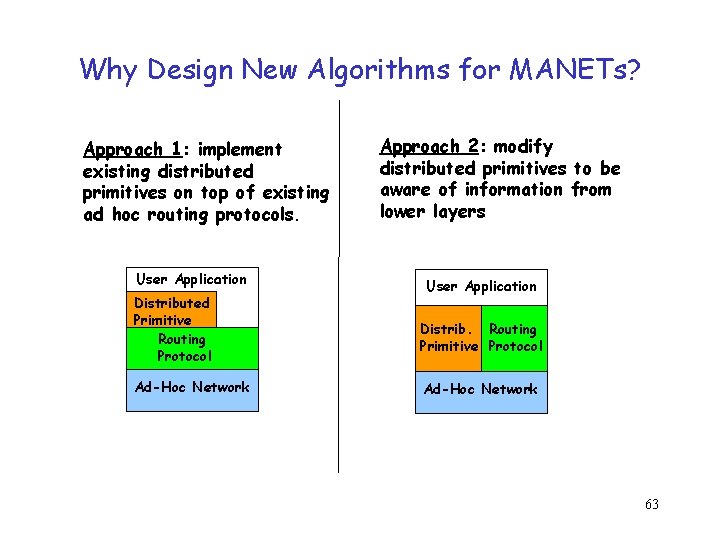
Why Design New Algorithms for MANETs? Approach 1: implement existing distributed primitives on top of existing ad hoc routing protocols. User Application Distributed Primitive Routing Protocol Ad-Hoc Network Approach 2: modify distributed primitives to be aware of information from lower layers User Application Distrib. Routing Primitive Protocol Ad-Hoc Network 63

Distributed Mutual Exclusion g g g Token-based: Only the node possessing the token may enter critical section Nodes must have a way of sending requests to the token holder One solution: Mutual exclusion for fixed topology + Routing on ad hoc networks 64
![Link Reversal Algorithm Gafni 81 Routing Protocol A B F C E G D Link Reversal Algorithm [Gafni 81] (Routing Protocol) A B F C E G D](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-65.jpg)
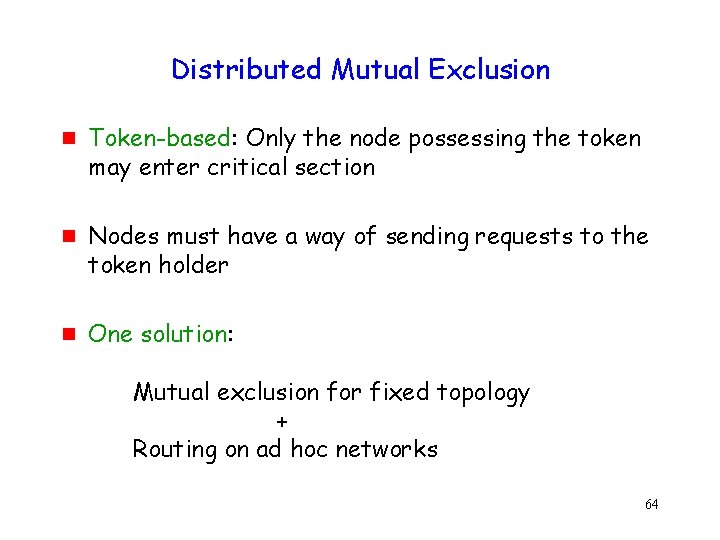
Link Reversal Algorithm [Gafni 81] (Routing Protocol) A B F C E G D 65
![Link Reversal Algorithm Gafni 81 A C B E D F G Links are Link Reversal Algorithm [Gafni 81] A C B E D F G Links are](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-66.jpg)
Link Reversal Algorithm [Gafni 81] A C B E D F G Links are bi-directional But algorithm imposes logical directions on them Maintain a directed acyclic graph (DAG) for each destination, with the destination being the only sink This DAG is for destination node D 66

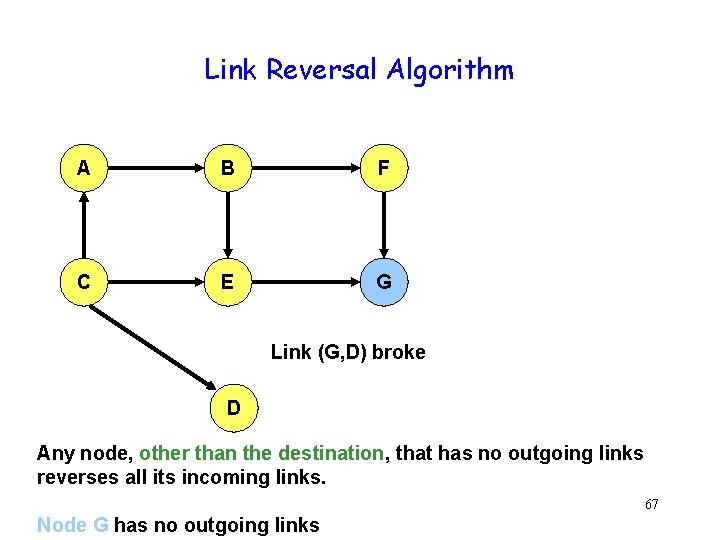
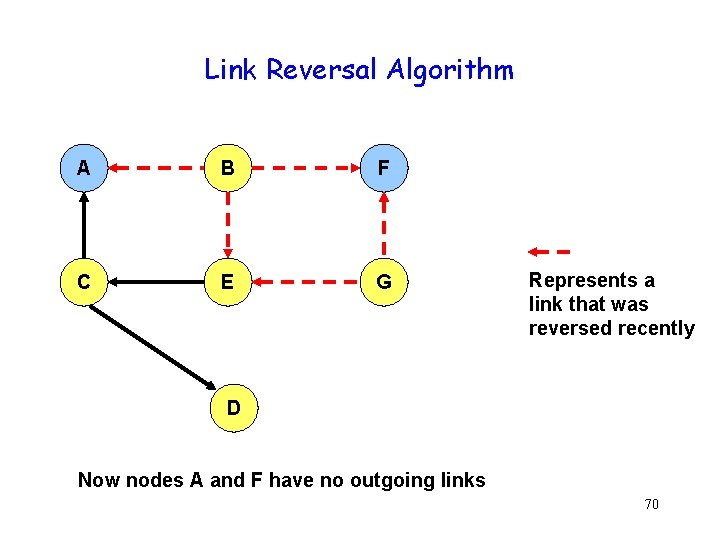
Link Reversal Algorithm A B F C E G Link (G, D) broke D Any node, other than the destination, that has no outgoing links reverses all its incoming links. 67 Node G has no outgoing links

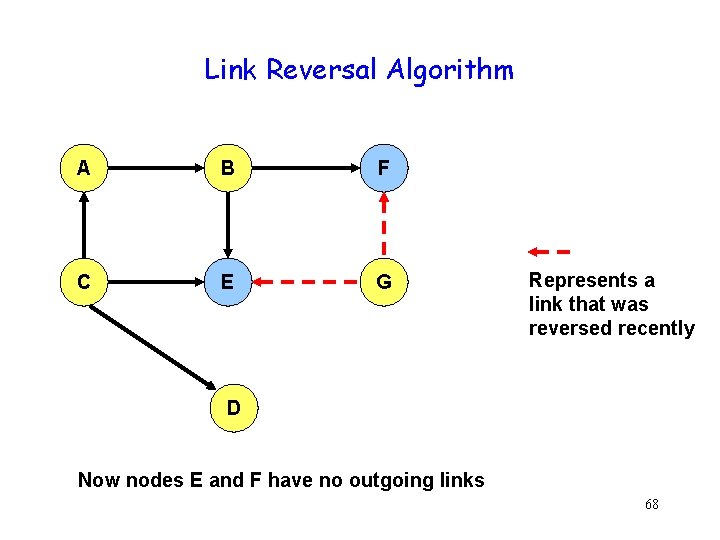
Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now nodes E and F have no outgoing links 68

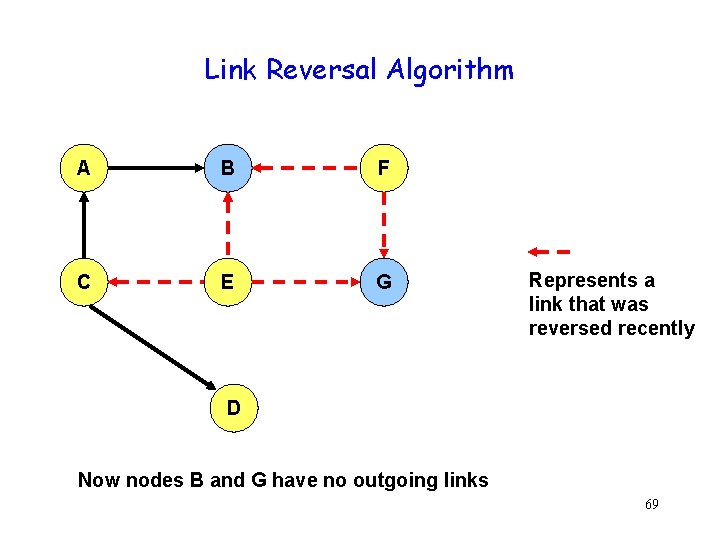
Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now nodes B and G have no outgoing links 69

Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now nodes A and F have no outgoing links 70

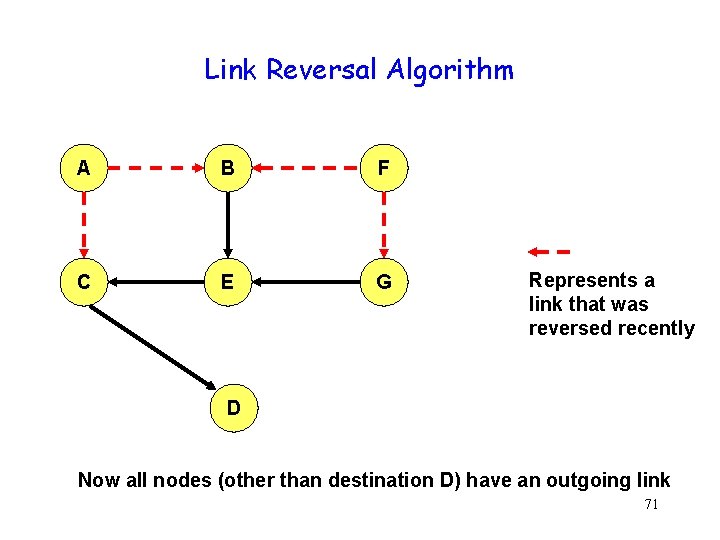
Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now all nodes (other than destination D) have an outgoing link 71

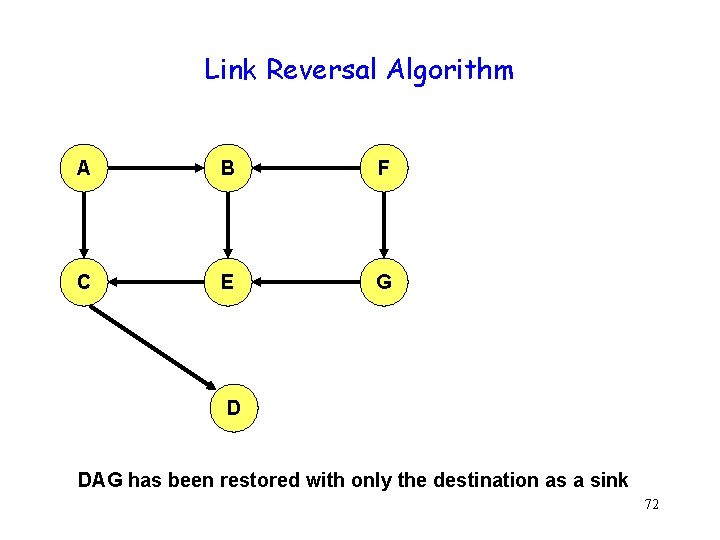
Link Reversal Algorithm A B F C E G D DAG has been restored with only the destination as a sink 72

Link Reversal Algorithm g Goal: Maintain DAG pointing to the “destination” despite topology changes 73
![Mutual Exclusion in Static Networks Raymond 89 g g Static topology Spanning tree with Mutual Exclusion in Static Networks [Raymond 89] g g Static topology Spanning tree with](https://slidetodoc.com/presentation_image/92c851e3d0daf5eb181752aa439675c3/image-74.jpg)
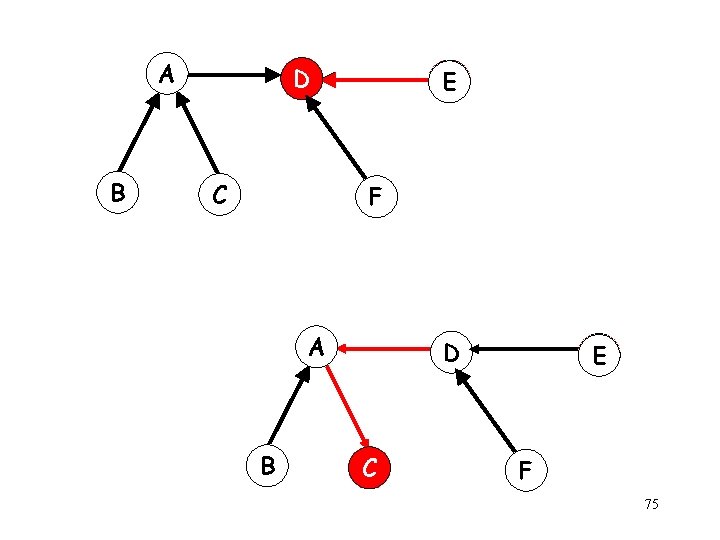
Mutual Exclusion in Static Networks [Raymond 89] g g Static topology Spanning tree with edges directed toward the token holder A B D C E F 74

A B D C E F 75

Raymond’s Algorithm on Ad Hoc Networks g The algorithm can be implemented on top of routing protocol – Routing algorithms provides abstraction of a fully connected network g g Maintain a spanning tree using logical links in the “fully connected” network “Adjacent” nodes in the spanning tree may be far from each other Potentially poor performance 76

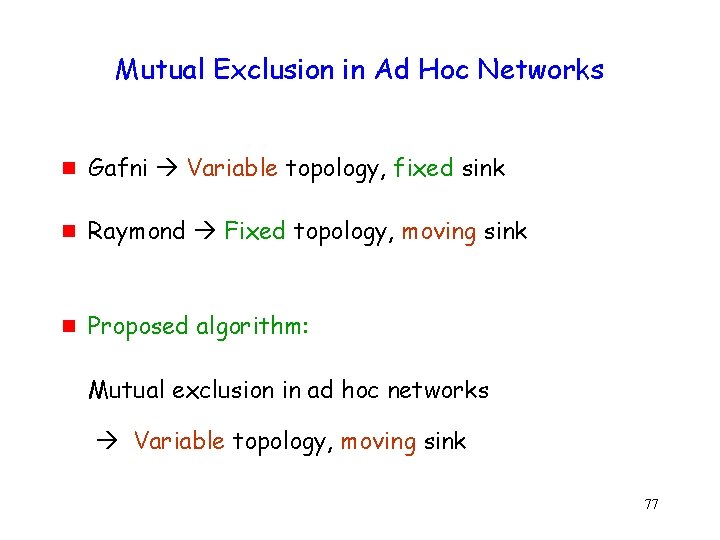
Mutual Exclusion in Ad Hoc Networks g Gafni Variable topology, fixed sink g Raymond Fixed topology, moving sink g Proposed algorithm: Mutual exclusion in ad hoc networks Variable topology, moving sink 77

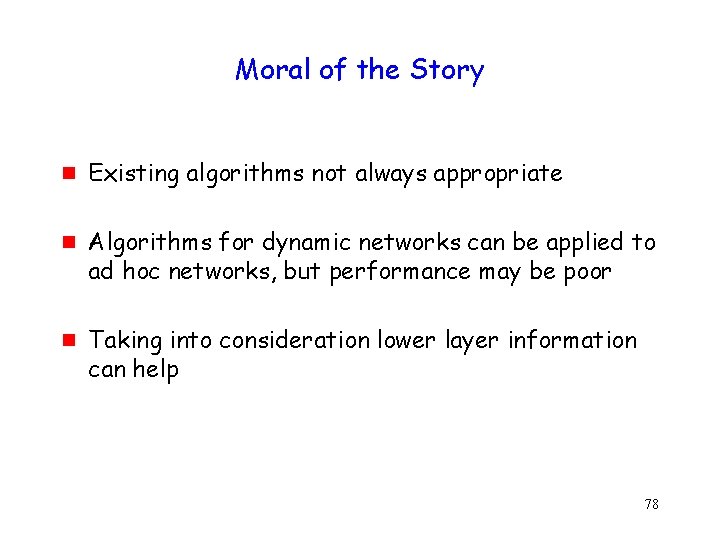
Moral of the Story g g g Existing algorithms not always appropriate Algorithms for dynamic networks can be applied to ad hoc networks, but performance may be poor Taking into consideration lower layer information can help 78

On to the preaching … 79

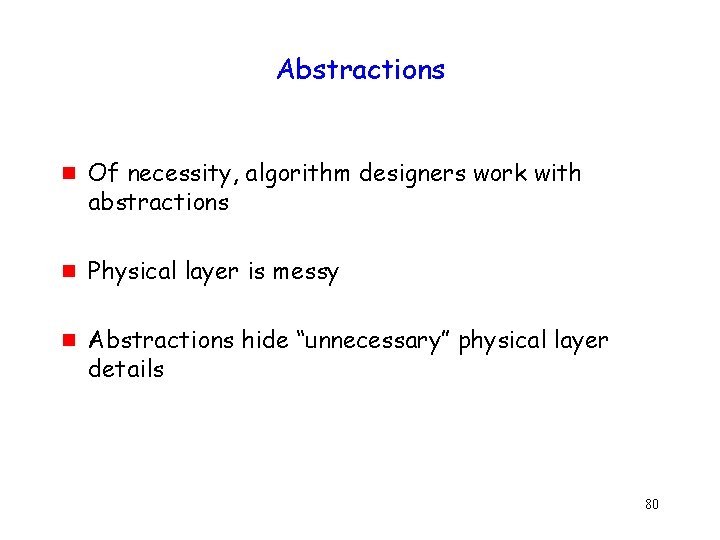
Abstractions g g g Of necessity, algorithm designers work with abstractions Physical layer is messy Abstractions hide “unnecessary” physical layer details 80

Abstractions g But some details are important. Many common mistakes. g I am guilty too … but hopefully learning from the mistakes 81

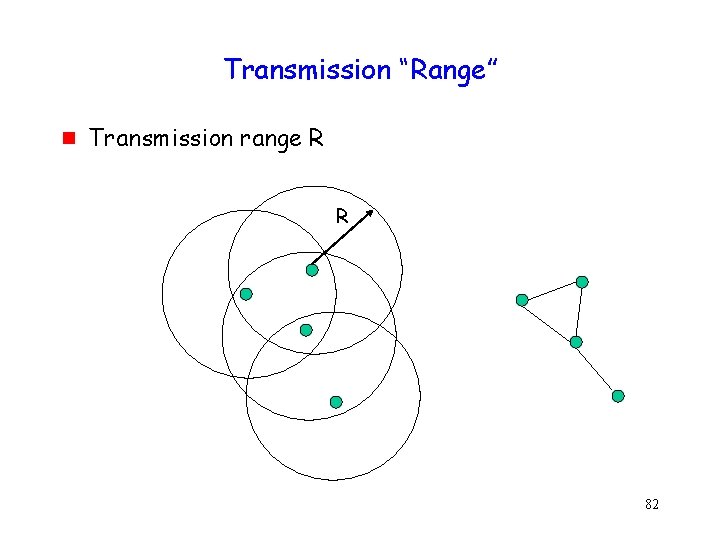
Transmission “Range” g Transmission range R R 82

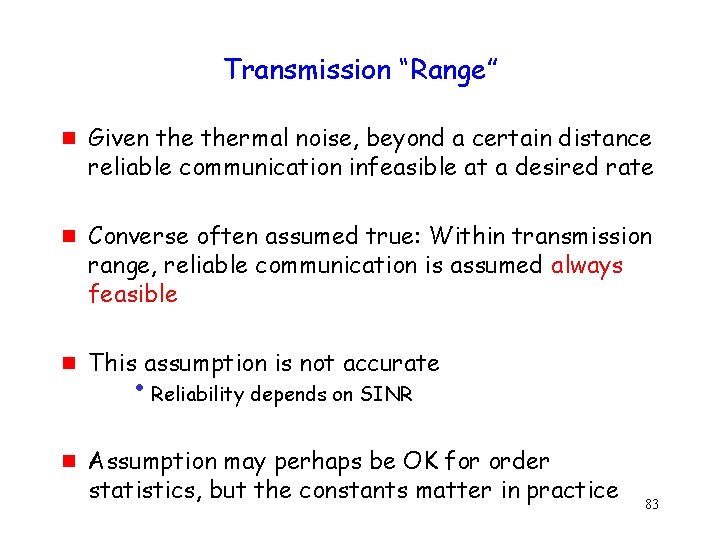
Transmission “Range” g g Given thermal noise, beyond a certain distance reliable communication infeasible at a desired rate Converse often assumed true: Within transmission range, reliable communication is assumed always feasible This assumption is not accurate • Reliability depends on SINR Assumption may perhaps be OK for order statistics, but the constants matter in practice 83

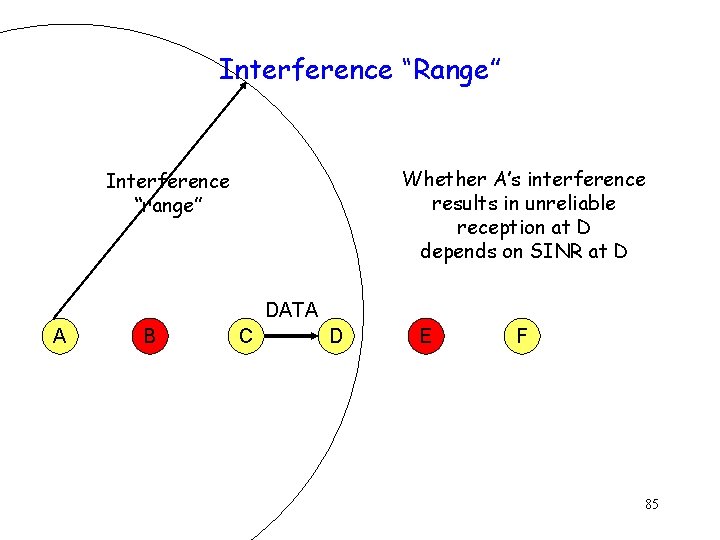
Interference “Range” g g g Interference “range” assumed to be the distance over which a transmission “collides” with another transmission Assumed that if a host transmits, no other transmission within interference range will succeed Not accurate: Reliability depends on SINR 84

Interference “Range” Whether A’s interference results in unreliable reception at D depends on SINR at D Interference “range” DATA A B C D E F 85

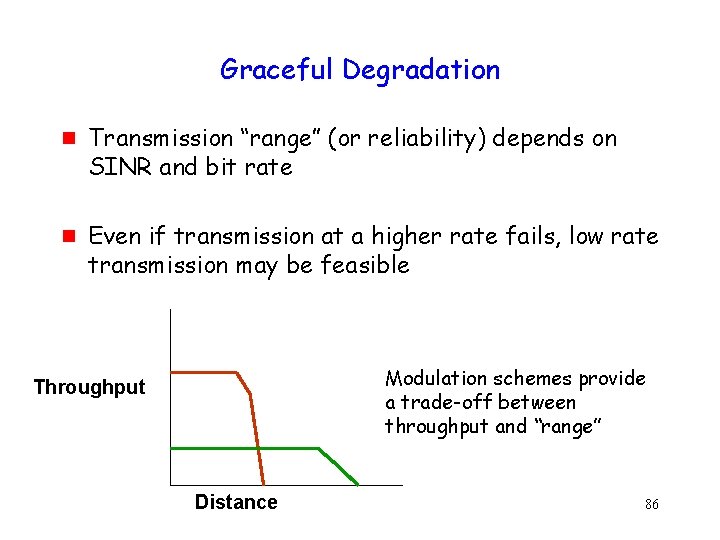
Graceful Degradation g g Transmission “range” (or reliability) depends on SINR and bit rate Even if transmission at a higher rate fails, low rate transmission may be feasible Modulation schemes provide a trade-off between throughput and “range” Throughput Distance 86

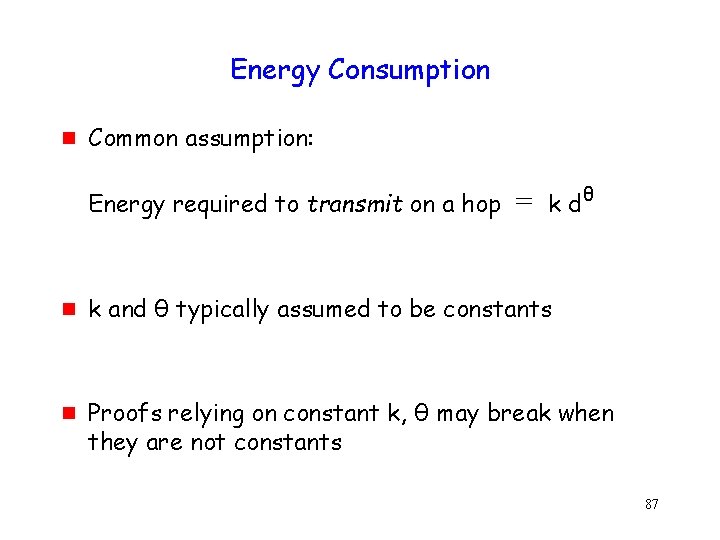
Energy Consumption g Common assumption: Energy required to transmit on a hop g g = k dθ k and θ typically assumed to be constants Proofs relying on constant k, θ may break when they are not constants 87

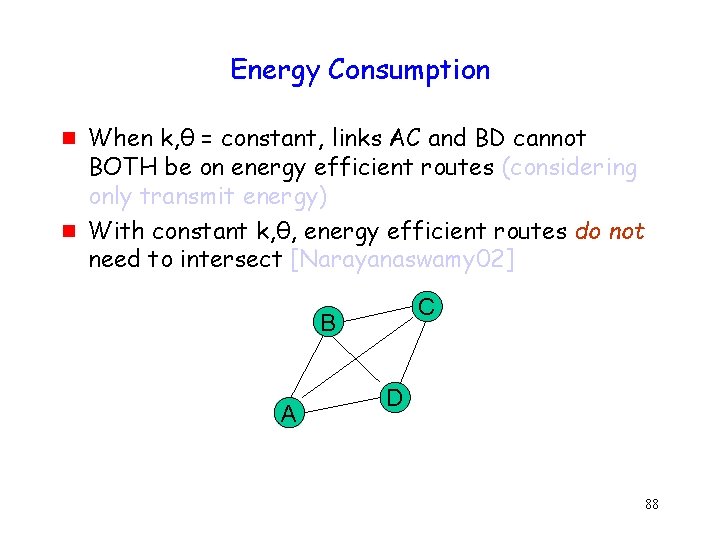
Energy Consumption g g When k, θ = constant, links AC and BD cannot BOTH be on energy efficient routes (considering only transmit energy) With constant k, θ, energy efficient routes do not need to intersect [Narayanaswamy 02] C B A D 88

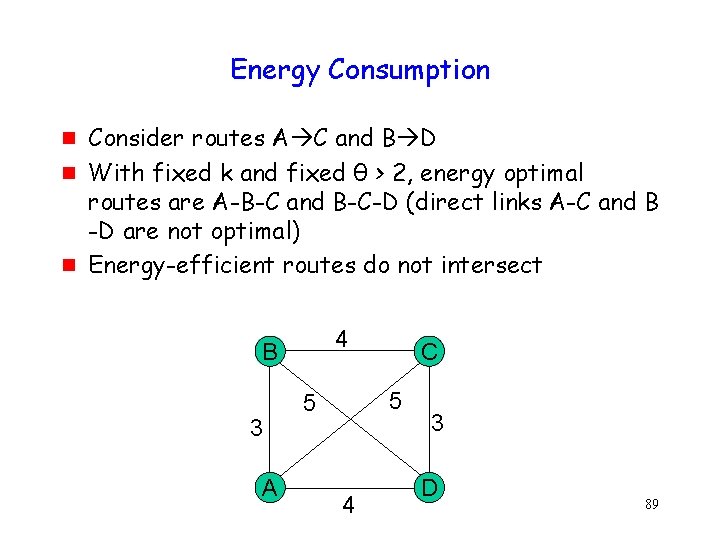
Energy Consumption g g g Consider routes A C and B D With fixed k and fixed θ > 2, energy optimal routes are A-B-C and B-C-D (direct links A-C and B -D are not optimal) Energy-efficient routes do not intersect 4 B 3 A C 5 5 4 3 D 89

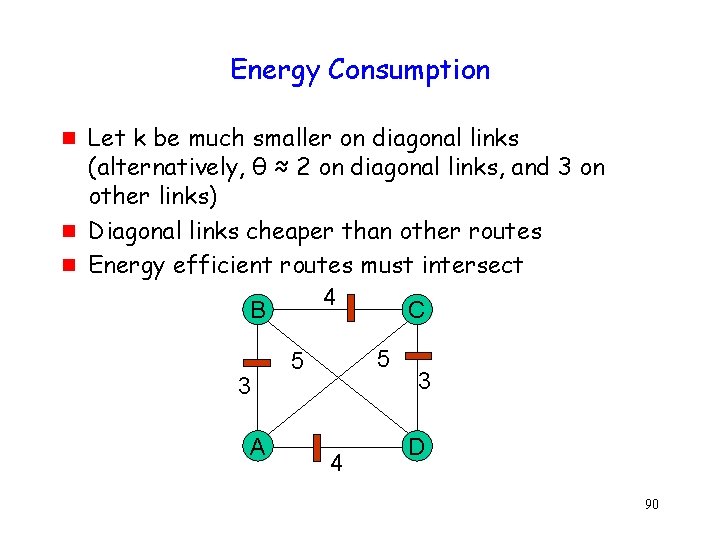
Energy Consumption g g g Let k be much smaller on diagonal links (alternatively, θ ≈ 2 on diagonal links, and 3 on other links) Diagonal links cheaper than other routes Energy efficient routes must intersect 4 B C 3 A 5 5 4 3 D 90

Geographic Location g g g Many algorithms rely on knowledge of physical location Location estimates in practice contain some error The error can affect correctness of geographic routing [Saeda 04] 91

Summary g Physical layer characteristics matter g Can affect algorithm performance and correctness 92

End of preaching … 93

Interesting Open Problems g Protocols that achieve “capacity” g Distributed algorithms for ad hoc networks g Complexity as a function of mobility g Applications for ad hoc networks i. Shared memory i. Message ordering i. Group communication i… 94

Thanks! http: //www. crhc. uiuc. edu/wireless/ 95

Thanks! http: //www. crhc. uiuc. edu/wireless/ 96

Handling other misbehavior g g Receiver may misbehave by assigning large or small backoff values Sender can detect receiver assigning small backoff values i. Backoff assigned by receiver has to follow well-known distribution i. Sender uses larger of assigned backoff and expected backoff 97

Handling other misbehavior g Detecting receiver assigning large backoff values not handled i. Equivalent to receiver not responding at all i. Need higher layer mechanisms g Collusion between sender and receiver i. Harder to detect i. Requires an observer that can monitor both sender and receiver 98