Passwords and Password Policies An Important Part of













- Slides: 21

Passwords and Password Policies An Important Part of IT Control – by Craig Piercy

Why Passwords? Primary means for many systems for implementing authentication and authorization. n Authentication – verifying that you are who you say you are. n Authorization – allowing access to the parts of the system that you need and only those parts.

Could this be you?

Or This?

How well do you follow good Password procedures? Do you use a name for your password? n Do you use a real, “dictionary” word? n Do you use the same password for all or most of your accounts? n Is you password short (< 6 digits)? n Do you still use the default or provided password? n Do you keep your password forever? n Is you password “password, ” “default”, “ 123”? If you answered “yes” to any of the above, then you are failing an important part of good use of passwords. n

Why do you do these things? “weak” password – a password that is fairly easy to guess or “crack. ” “strong” password – a password that is difficult to guess or “crack. ” For most, there is a trade-off between having “strong” passwords and being able to remember them.

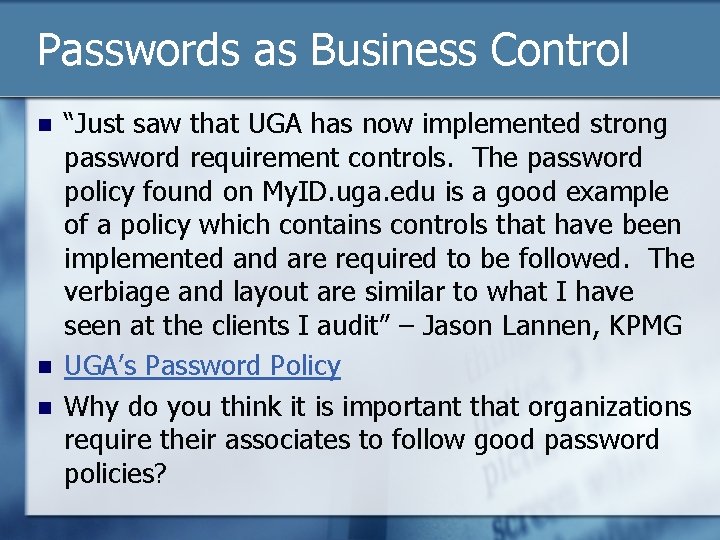
Passwords as Business Control n n n “Just saw that UGA has now implemented strong password requirement controls. The password policy found on My. ID. uga. edu is a good example of a policy which contains controls that have been implemented and are required to be followed. The verbiage and layout are similar to what I have seen at the clients I audit” – Jason Lannen, KPMG UGA’s Password Policy Why do you think it is important that organizations require their associates to follow good password policies?

Characteristics of “strong” passwords n n n DO NOT use a real word or name Long rather than short --- >=8 characters Use a mix of characters – text characters – upper and lower case, numeric digits, punctuation Use different passwords on different accounts Change your password regularly. DO NOT write your passwords down. (see TIES box on page 209 – Chapter 7)

A two step Method for Making Strong Passwords that you can remember. 1. 2. Come up with a “key” that you can remember easily. Come up with as set of simple rules for converting your key into a password

Example - Key 1. Choose a key – my preference is a line of text – favorite song titles are good, could be a proverb, famous quotation, line from a poem, etc. Example – “The leaves have fallen all around…”

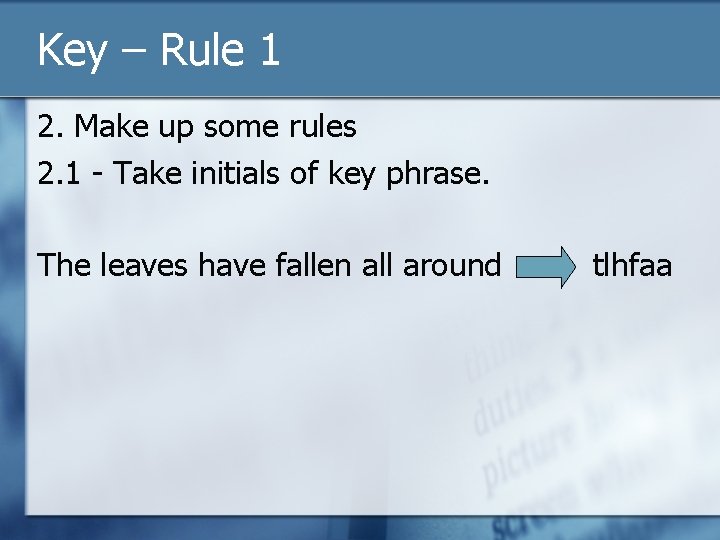
Key – Rule 1 2. Make up some rules 2. 1 - Take initials of key phrase. The leaves have fallen all around tlhfaa

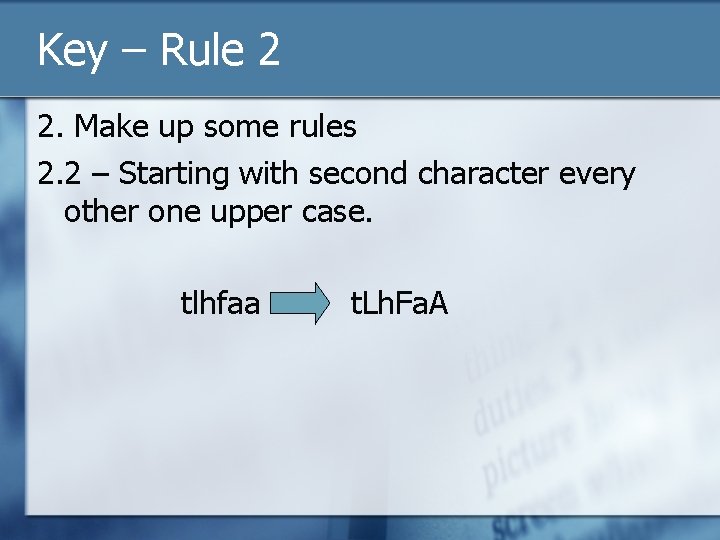
Key – Rule 2 2. Make up some rules 2. 2 – Starting with second character every other one upper case. tlhfaa t. Lh. Fa. A

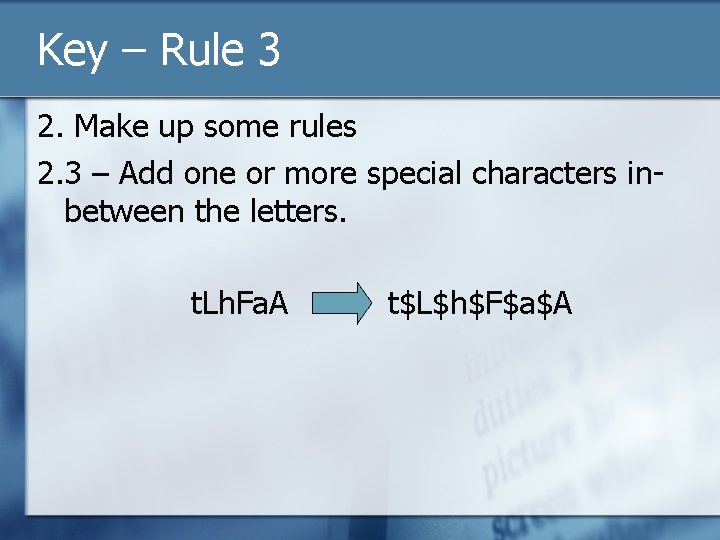
Key – Rule 3 2. Make up some rules 2. 3 – Add one or more special characters inbetween the letters. t. Lh. Fa. A t$L$h$F$a$A

Notes: These are my rules. Make up your own! n Make as many rules in your algorithm that you can remember – rule of thumb 3 to 5 is probably good enough. n Make sure that your key is long enough to generate a long enough password. n Even though you have a stronger password, you still need to be aware of how you use it and when it might be compromised. n n What should you do if you think that your password has been compromised?

What about multiple accounts? Some come up with a code for each account and then concatenate onto their password. n Example: Account Password Code My laptop plap t$L$h$F$a$A_plap UGA account Uga t$L$h$F$a$A_uga Gmail account Gm t$L$h$F$a$A_gm

What about changing regularly? Change the key and apply the rules. Example: n New key: “… Time I was on my way. ” n Apply rules: 1. 2. 3. Take initials of key phrase. Starting with second character every other one upper case. Add one or more special characters in-between the letters. What’s the new password for the uga account? t$I$w$O$m$W_uga

Discussion Are there any problems in my algorithm? n How could I improve it? n Incidentally, I did a slightly dangerous thing in choosing the second key: n 1 st key – 1 st line of Ramble On by Led Zeppelin n 2 nd key – 2 nd line of Ramble On by Led Zeppelin n What would be a safer way of choosing second key? n

How about PIN numbers? Can’t make them as strong. Why? n Should we try to keep our PIN numbers strong? n What characteristics should a strong PIN number have? n

A PIN number example: 1. 2. Pick a key: 1492 (Columbus sailed the ocean blue) Rules: 1. 2. Choose last for digits of credit card For cards: Add key to last for digits of card for PIN. For other accounts find a “look-up-able” related number and add to key. Account Last 4 or related PIN Master. Card 3004 4496 AMEX 1206 2698 OASIS 3452 (last four of student ID) 4944

Discussion What’s good about the example PIN number algorithm? n What’s bad about it? n How would you improve it? n

Call to Action 1. 2. 3. 4. Come up with your key and password algorithm. Use it to come up with your new UGA My. ID. Use it to adjust your other passwords. Start changing your password frequently. About once every 3 months (policies may vary)
 Passwords suck
Passwords suck Myth world passwords
Myth world passwords What are passwords
What are passwords Docs googlw
Docs googlw Hoborules
Hoborules Houstonisdhub
Houstonisdhub Newspaper article format
Newspaper article format From most important to least important in writing
From most important to least important in writing Least important to most important
Least important to most important Security program and policies principles and practices
Security program and policies principles and practices Recruitment and induction process
Recruitment and induction process Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Different parts of body
Different parts of body The mass media play an important part in our lives
The mass media play an important part in our lives Manuel roxas economic advisor
Manuel roxas economic advisor National policy and legislation
National policy and legislation Classroom policies and procedures
Classroom policies and procedures Lending policies and procedures managing credit risk
Lending policies and procedures managing credit risk Antidumping laws
Antidumping laws