Topics Passwords Password policy How to change password









- Slides: 27


Topics • • • Passwords – Password policy, How to change password Connecting to wireless Configure Email on my device Phishing and SPAM emails – how to identify, what to do Mapping network drives Office 365 overview – email, onedrive, webapps, proplus Microsoft work at home program – Windows / Office Dell discounts www. dell. com/mtech 25 Live (Jennifer) Quiz Questions 2

Passwords 1/3 • Minimum password length - 6 characters –password of 6 characters or more. • Maximum password age – 365 days – users would need to change their password every year. • Enforce password history – 2 – users will not be able to re-use their two previous passwords. • Password must meet complexity requirements – – Not contain the user's account name or parts of the user's full name that exceed two consecutive characters – Be at least six characters in length – Contain characters from three of the following four categories: • • English uppercase characters (A through Z) English lowercase characters (a through z) Base 10 digits (0 through 9) Non-alphabetic characters (for example, !, $, #, %) 3

Passwords 2/3 • What you need to know: – After your password is changed, you will want to update any mobile devices you have. You will need to specify your new password to connect to the wireless here on campus. You will also need to update your password so that your device can continue to check your email. • Password best practices: – Do not use your Montana Tech password on third party websites. Try to use a unique password on the third party websites. The reason why you want to avoid doing so - if the third party website is compromised, the person that has the compromised data may try to use your password to authenticate into Montana Tech systems. • Do not write down your password and leave it on your desk. – If you need to write down your password so you can remember it, keep it with you. Write it down and store it in your wallet or purse. Once you have your password memorized get rid of the written password. • Do not share your password with anyone. Montana Tech Network Services will never ask for your password through email, over the phone, 4 or in person.

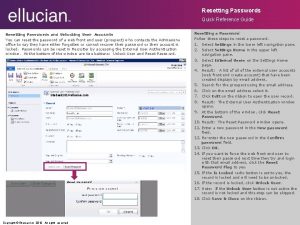
Passwords 3/3 • How to change from a domain PC – CTRL+ALT+DEL after you login • Change Password • Password Reset tool – – Mtech. edu – Tech Support – Authentication – Password Guides – http: //www. mtech. edu/cts/password-reset/ 5

Wireless • MTGuest – for guests only – Users that do not have an @mtech. edu account • Eduroam – use your full email address as your username and your Montana Tech password – Available at many academic affiliate sites – https: //www. eduroam. us/institutions • MTPodium – Specialized wireless network – this connection will be configured by your support specialist. • MTDorms – For use by students in Dorm buildings / Family Housing 6

Wireless • How to connect to eduroam on Android – www. mtech. edu – Tech Support – Wireless-Android – https: //kb. mtech. edu/wireless/Wireless-Android 7

Wireless • How to connect to eduroam on i. OS – www. mtech. edu – Tech Support – Wireless-i. Phone – https: //kb. mtech. edu/wireless/Wireless-i. Phone 8

E-Mail Configuration • Built-in E-Mail app • Outlook Mobile App • Android – https: //kb. mtech. edu/email/Installing-Office-365(Android) • i. OS – https: //kb. mtech. edu/email/Installing-Office-365(i. OS) 9

Phishing • Top 10 tips for spotting a phishing email – – – – – Message contains a mismatched URLs contain a misleading domain name Message contains poor spelling and grammar Message asks for personal information Offer seems too good to be true You didn’t initiate the action (are you expecting the email? ) You’re asked to send money to cover expenses The message makes unrealistic threats Message appears to be from a government agency Something just doesn’t look right (if you are questioning it in the first place, it is probably phishing) 10

What to do with Suspicious Email • Do not forward the suspicious email • Visit https: //kb. mtech. edu – Email – Submitting Scam Messages • Open new email message, drag and drop suspicious email into body of new message, send to junk@office 365. Microsoft. com or phish@office 365. Microsoft. com 11

Email Features • Clutter – Sorts low priority email. Learns based off of your behavior, if you do not read an email, it takes messages you’re most likely to ignore and puts into “Clutter” folder. – Feature can be turned on or off – Clutter is being replaced with Focused Inbox 12

Email Features • Focused Inbox – – Uses same learning algorithm as Clutter, instead of moving to a separate folder you are presented with “Focused” and “Other” views in the inbox. – This view can be seen in Outlook web access – “Focused” and “Other” view is currently not available in Outlook on the desktop. – Focused inbox feature is on by default. – Feature can be turned off. • Outlook OWA – Gear – Mail – Layout – Focused inbox 13

Mapping Network Drives 1/6 • Mapping a network drive is a way of connecting to a shared folder or computer on the network – It is more efficient to map a network drive that is accessed frequently, rather than typing in the path to the shared network folder or referring to a link in an email every time you need to access it – Mapping a network drive assigns a drive letter of your choosing (such as M: ) and makes the network drive appear as a locally attached drive on your computer 14

Mapping Network Drives 2/6 – The syntax used when mapping a network drive is \servernamefoldername • This is referred to as a UNC (universal naming convention) and points to a folder on another computer or server • Example: \mtfiles 01netservices – The UNC path is what your computer coordinator needs when asking them to give you permission to a network drive, not just the letter 15

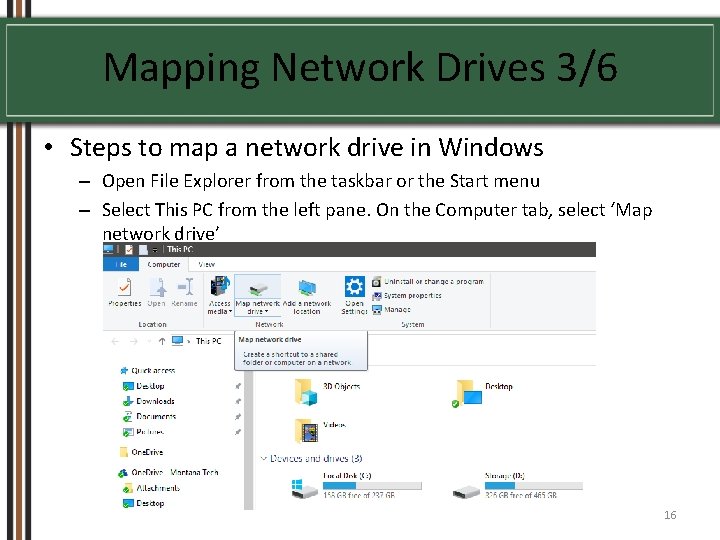
Mapping Network Drives 3/6 • Steps to map a network drive in Windows – Open File Explorer from the taskbar or the Start menu – Select This PC from the left pane. On the Computer tab, select ‘Map network drive’ 16

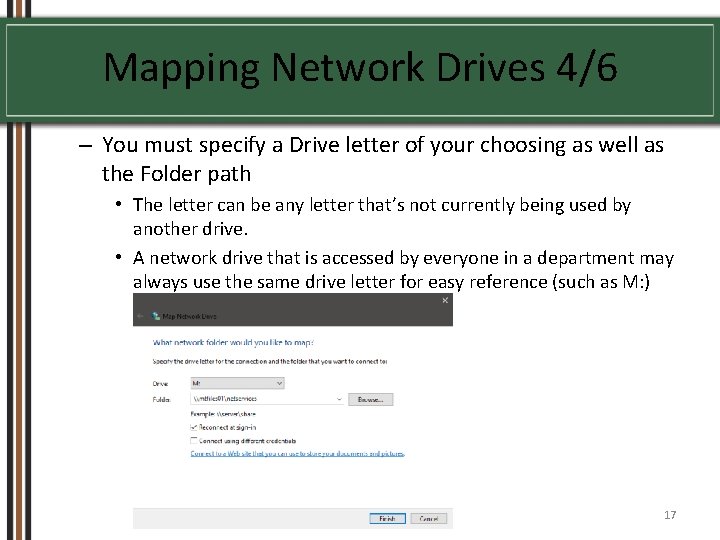
Mapping Network Drives 4/6 – You must specify a Drive letter of your choosing as well as the Folder path • The letter can be any letter that’s not currently being used by another drive. • A network drive that is accessed by everyone in a department may always use the same drive letter for easy reference (such as M: ) 17

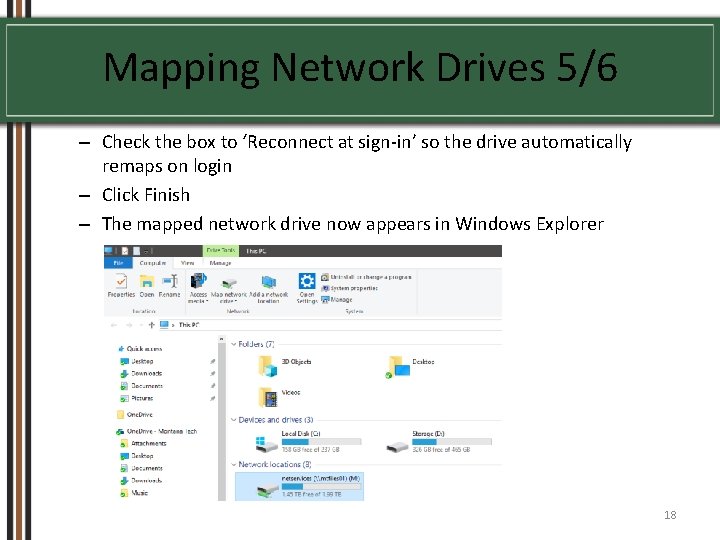
Mapping Network Drives 5/6 – Check the box to ‘Reconnect at sign-in’ so the drive automatically remaps on login – Click Finish – The mapped network drive now appears in Windows Explorer 18

Mapping Network Drives 6/6 • Things to remember: – You must have been given permission to the network drive in order to view or modify its contents – The letter used to map the network drive is of your choosing – When asking your computer coordinator for permission to a network drive, refer to the UNC path and not the letter 19

Office 365 • • Logging into Outlook Web Access Webapps One. Drive Obtaining Pro. Plus – Login to Outlook Web Access, Click Gear, Your app settings – Office 365, Settings – Software “Install Software” – https: //kb. mtech. edu/email/Installing-Office-(PCand-Mac) 20

Microsoft Work from Home Program • https: //kb. mtech. edu/ • Faculty / Staff receive discounted Microsoft products for use on their personal device(s) 21

Dell discounts • • For Personal Purchases only www. dell. com/mtech Standard configurations Deals, Laptops, Desktops, Electronics 22

Quiz • Which password can I use for the user WTQuinn – mtech 1 – Wtquinn 1 – password – MTech 1! – MTech 2 23

Quiz • What should you do if you get a suspicious email? 24

Quiz • True or False – When asking for permission to a network drive, tell your computer coordinator “I need access to the M drive. ” – When asking for permission to a network drive, give your computer coordinator the UNC path (\servernamefoldername). 25

25 Live 26

Questions? 27
 Passwords suck
Passwords suck Myth world passwords
Myth world passwords What are passwords
What are passwords Googlw tricks
Googlw tricks Hashcat $1$
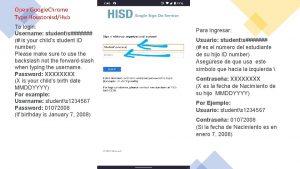
Hashcat $1$ Houstonisdhub
Houstonisdhub Tech mahindra password policy
Tech mahindra password policy Mit change password
Mit change password Reset my adp password
Reset my adp password Onyen password change
Onyen password change Uel outlook
Uel outlook Ui online detma
Ui online detma Temple university change password
Temple university change password Group policy change management
Group policy change management Change management levers
Change management levers Examples for physical change
Examples for physical change Physical and chemical change examples
Physical and chemical change examples Absolute change and relative change formula
Absolute change and relative change formula Intergers
Intergers Difference between physical change and chemical change
Difference between physical change and chemical change Input and output market
Input and output market Supply and demand curve shifts
Supply and demand curve shifts Enagic compensation plan
Enagic compensation plan Proactive vs reactive change
Proactive vs reactive change What is example of physical change
What is example of physical change Spare change physical versus chemical change
Spare change physical versus chemical change Rocks change due to temperature and pressure change
Rocks change due to temperature and pressure change Whats the difference between physical and chemical changes
Whats the difference between physical and chemical changes