PANA in DSL networks draftmorandpanaoverdsl01 txt Lionel Morand





- Slides: 13

PANA in DSL networks draft-morand-panaoverdsl-01. txt Lionel Morand France Telecom Alper Yegin Samsung Yoshihiro Ohba Toshiba John Kaippallimalil Huawei IETF-71, Philadelphia

Draft History • IETF 66: – PANA use case for DSL removed from PANA Framework • IETF 67: – First presentation of the "PANA over DSL" draft (v 00) • IETF 67 and IETF 71: – Draft frozen during finalization of PANA protocol – DSL Liaison on access authentication requirements • IETF 71: – Update version of the "PANA over DSL" draft (v 01) • Based on final version of the PANA base protocol and comments received and outputs of DSLF liaison discussions IETF-71, Philadelphia

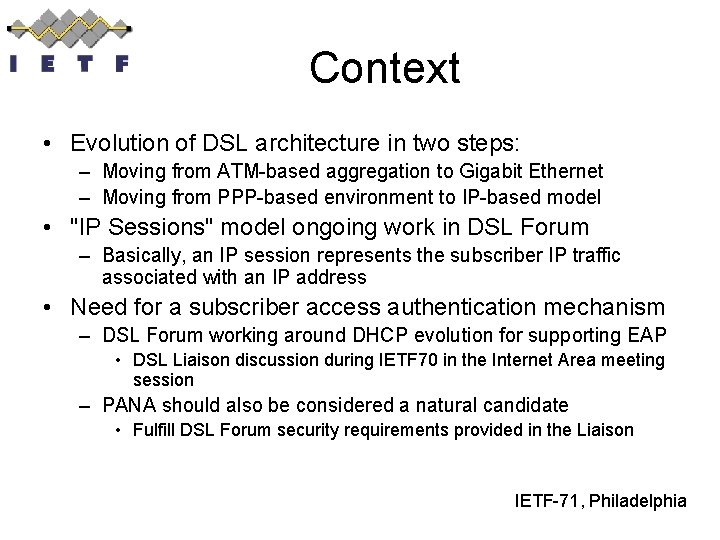
Context • Evolution of DSL architecture in two steps: – Moving from ATM-based aggregation to Gigabit Ethernet – Moving from PPP-based environment to IP-based model • "IP Sessions" model ongoing work in DSL Forum – Basically, an IP session represents the subscriber IP traffic associated with an IP address • Need for a subscriber access authentication mechanism – DSL Forum working around DHCP evolution for supporting EAP • DSL Liaison discussion during IETF 70 in the Internet Area meeting session – PANA should also be considered a natural candidate • Fulfill DSL Forum security requirements provided in the Liaison IETF-71, Philadelphia

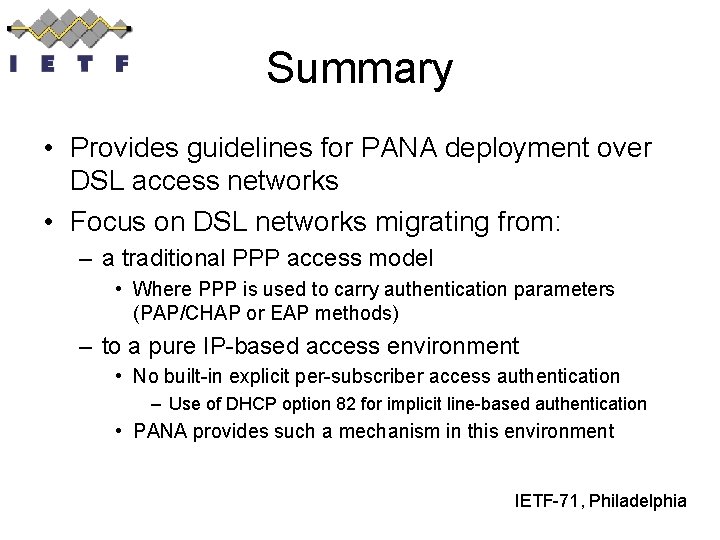
Summary • Provides guidelines for PANA deployment over DSL access networks • Focus on DSL networks migrating from: – a traditional PPP access model • Where PPP is used to carry authentication parameters (PAP/CHAP or EAP methods) – to a pure IP-based access environment • No built-in explicit per-subscriber access authentication – Use of DHCP option 82 for implicit line-based authentication • PANA provides such a mechanism in this environment IETF-71, Philadelphia

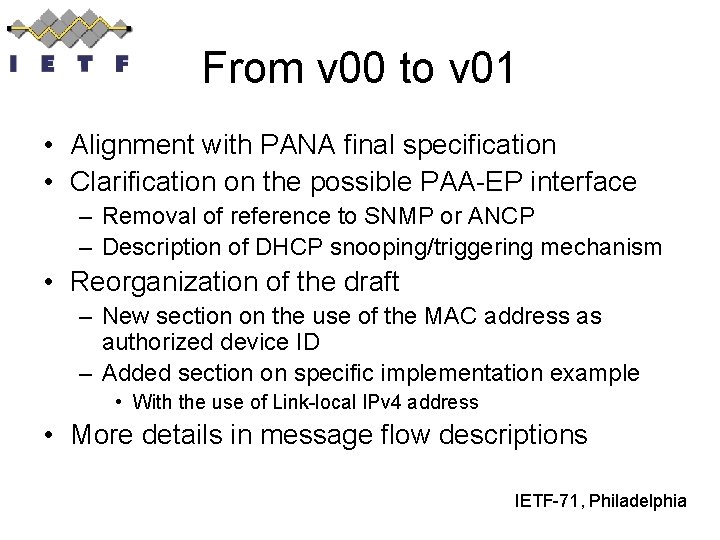
From v 00 to v 01 • Alignment with PANA final specification • Clarification on the possible PAA-EP interface – Removal of reference to SNMP or ANCP – Description of DHCP snooping/triggering mechanism • Reorganization of the draft – New section on the use of the MAC address as authorized device ID – Added section on specific implementation example • With the use of Link-local IPv 4 address • More details in message flow descriptions IETF-71, Philadelphia

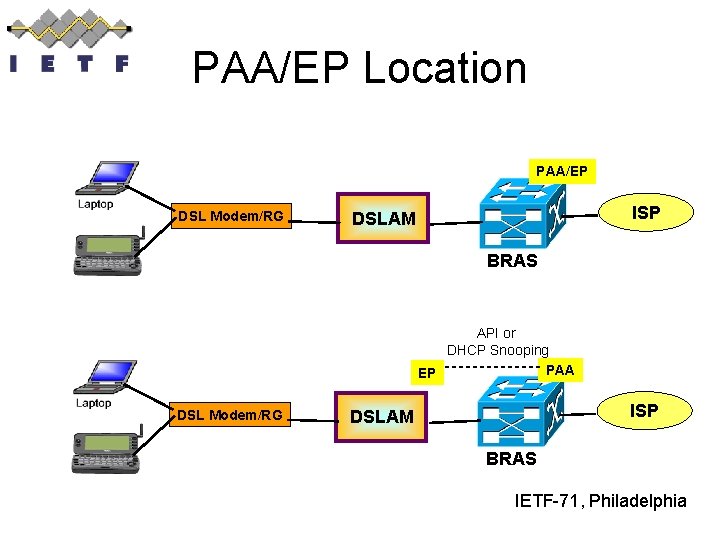
PAA/EP Location PAA/EP DSL Modem/RG ISP DSLAM BRAS API or DHCP Snooping PAA EP DSL Modem/RG ISP DSLAM BRAS IETF-71, Philadelphia

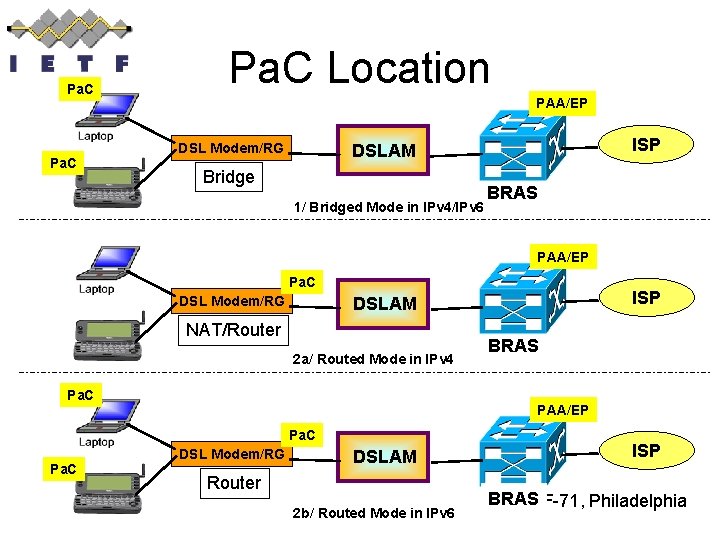
Pa. C Location PAA/EP DSL Modem/RG ISP DSLAM Bridge 1/ Bridged Mode in IPv 4/IPv 6 BRAS PAA/EP Pa. C DSL Modem/RG NAT/Router 2 a/ Routed Mode in IPv 4 Pa. C BRAS PAA/EP Pa. C ISP DSLAM DSL Modem/RG DSLAM Router 2 b/ Routed Mode in IPv 6 ISP BRAS IETF-71, Philadelphia

Use of PRPA/POPA • Mainly useful in IPv 4 context – to prevent waste of scarce IP resources • In IPv 4 context, PRPA may be: – Link-local IP address – Private IP address – Temporary allocated IP address • with short-lease and/or limited use • After a successful authentication, POPA is configured using DHCP IETF-71, Philadelphia

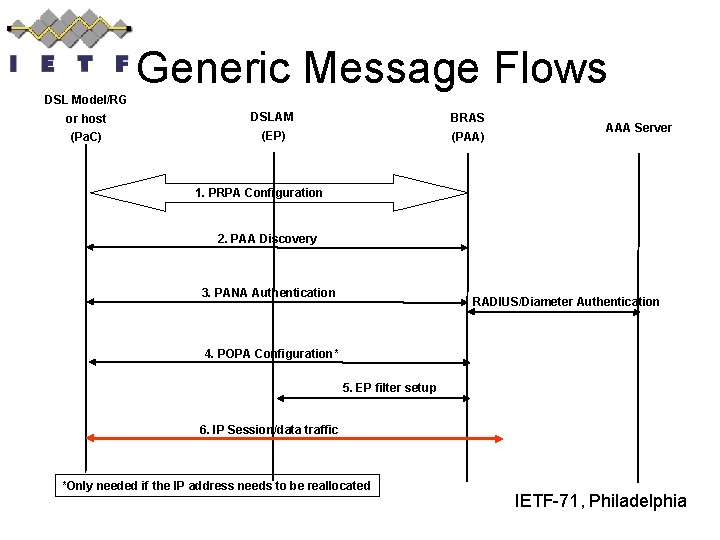
Generic Message Flows DSL Model/RG or host DSLAM BRAS (Pa. C) (EP) (PAA) AAA Server 1. PRPA Configuration 2. PAA Discovery 3. PANA Authentication RADIUS/Diameter Authentication 4. POPA Configuration* 5. EP filter setup 6. IP Session/data traffic *Only needed if the IP address needs to be reallocated IETF-71, Philadelphia

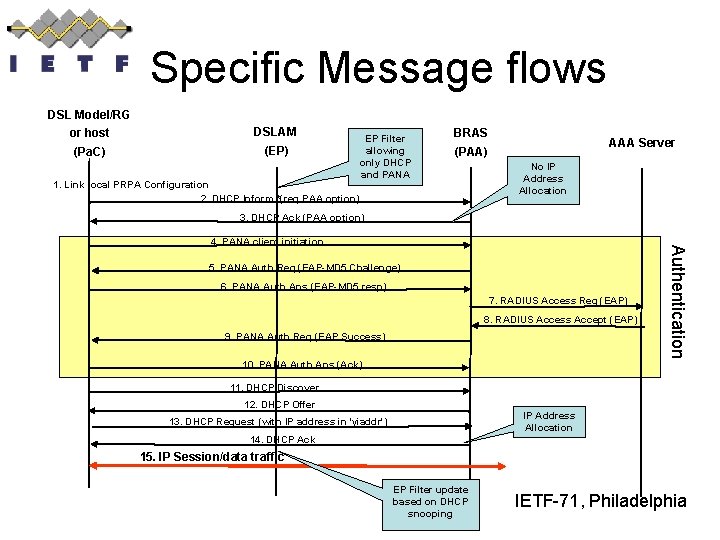
Specific example • Deployment scenario in which: – DSL Network configuration with: • Pa. C in the DSL modem/RG • BRAS hosting PAA, DHCP Server/Relay, and AAA client • DSLAM acting as EP – – – Link-local IPv 4 address as PRPA DHCP-based PAA discovery EAP-MD 5 Authentication method POPA configured using DHCPv 4 EP is triggered by DHCPACK whose 'yiaddr' field is filled IETF-71, Philadelphia

Specific Message flows DSL Model/RG or host DSLAM (Pa. C) (EP) EP Filter allowing only DHCP and PANA BRAS AAA Server (PAA) 1. Link local PRPA Configuration 2. DHCP Inform *(req PAA option) No IP Address Allocation 3. DHCP Ack (PAA option) 5. PANA Auth Req (EAP-MD 5 Challenge) 6. PANA Auth Ans (EAP-MD 5 resp) 7. RADIUS Access Req (EAP) 8. RADIUS Access Accept (EAP) 9. PANA Auth Req (EAP Success) 10. PANA Auth Ans (Ack) Authentication 4. PANA client initiation 11. DHCP Discover 12. DHCP Offer IP Address Allocation 13. DHCP Request (with IP address in 'yiaddr') 14. DHCP Ack 15. IP Session/data traffic EP Filter update based on DHCP snooping IETF-71, Philadelphia

Next Step • Provide more details on: – The use of link-local IP@ • Mechanism to avoid/resolve possible address conflict/collision – PANA impacts on DSL network: • Host, DSL Modem, DSLAM, BRAS, DHCP server – DSLAM acting as EP • And the use of DHCP as EP triggering mechanism – IP@/Identity binding management • Tight/loose coupling between DHCP/PANA/AAA • Investigate/clarify the case of hosts behind a NAT/Router in IPv 4 – Does PANA support NAT traversal? • Consider Unspecified IP address? – As an alternative to link-local IP address as PRPA IETF-71, Philadelphia

Thank You IETF-71, Philadelphia
 Lionel morand
Lionel morand Dsl 1 dsl 2
Dsl 1 dsl 2 Backbone networks in computer networks
Backbone networks in computer networks Virtual circuit switching example
Virtual circuit switching example Modlitwa na wakacje
Modlitwa na wakacje Katecheza pana jezusa i apostołów
Katecheza pana jezusa i apostołów Smaki farb pana kleksa
Smaki farb pana kleksa Tabel cuburi perfecte
Tabel cuburi perfecte Dr jekyll and mr hyde rozbor
Dr jekyll and mr hyde rozbor Litania dominikańska na chwałę pana
Litania dominikańska na chwałę pana Gienek washable wniebowstąpienie
Gienek washable wniebowstąpienie Modlitwa przed katechezą
Modlitwa przed katechezą Listy dzieci do pana boga
Listy dzieci do pana boga Przymioty boga w biblii
Przymioty boga w biblii