Network Architecture R 02 L 1 Jon Crowcroft











- Slides: 20

Network Architecture (R 02) - L 1 Jon Crowcroft, http: //www. cl. cam. ac. uk/~jac 22 http: //www. cl. cam. ac. uk/teaching/1010/R 02/

Course Structure 16 Lectures several guest slots - n n n Andrew Moore - router h/w algorithmics Cecilia Mascolo - sensor/mobile net arch Dirk Trossen - pub/sub in the net Hamed Haddadi - topology over time Participation by you n n n Reading & Critique-ing papers See “How to read a paper” by Keshav http: //www. sigcomm. org/ccr/drupal/files/p 83 -keshav. A. pdf

Course Assessment n Your involvement each week n n 3 essays - compare/contrast n n n Alternate me present & you all contribute Due dates oct 29, nov 26, start of next term An annotated bibligraphy n At start of next term, but update each week

Workload n Read 1 -2 papers per week n n Plus scan related material Keep notes Feel free to ask me more Essays can be n n n 2 -4 pages Note form is fine References/citing source material essential

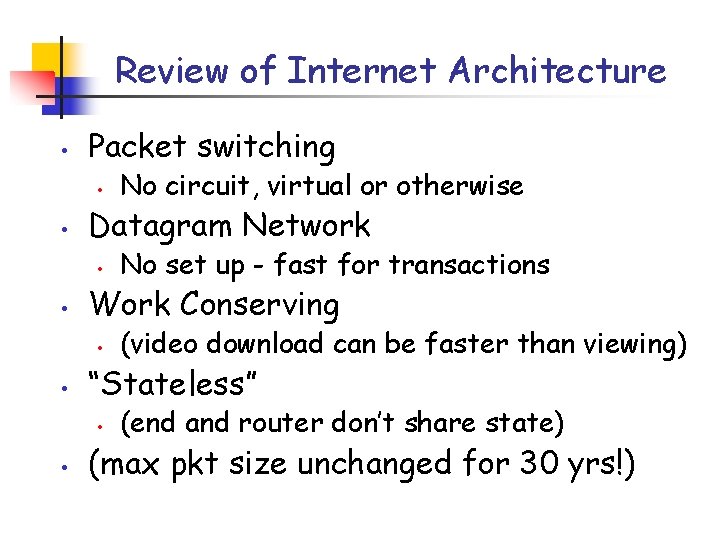
Review of Internet Architecture • Packet switching • • Datagram Network • • (video download can be faster than viewing) “Stateless” • • No set up - fast for transactions Work Conserving • • No circuit, virtual or otherwise (end and router don’t share state) (max pkt size unchanged for 30 yrs!)

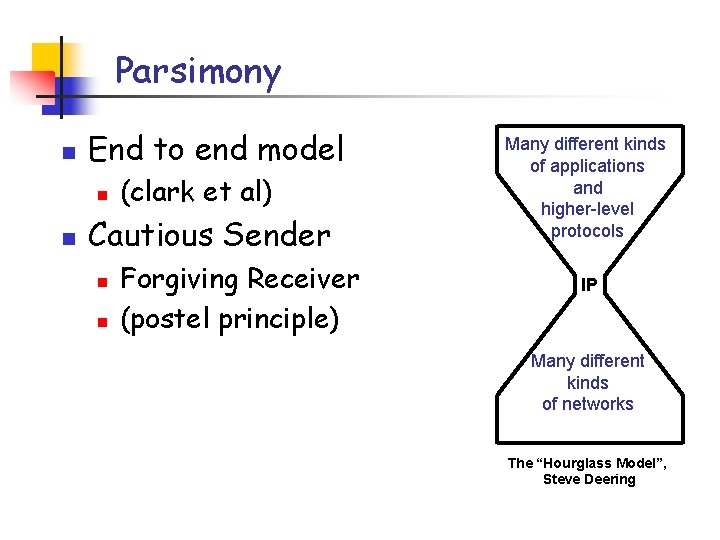
Parsimony n End to end model n n (clark et al) Cautious Sender n n Forgiving Receiver (postel principle) Many different kinds of applications and higher-level protocols IP Many different kinds of networks The “Hourglass Model”, Steve Deering

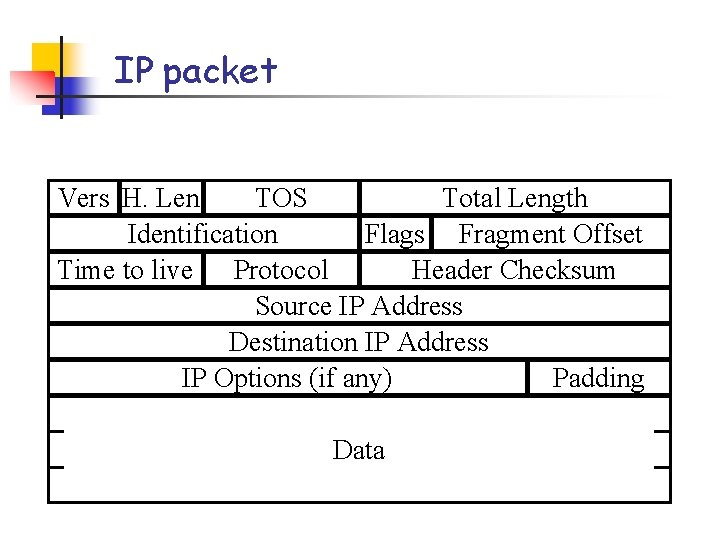
IP packet Vers H. Len TOS Total Length Identification Flags Fragment Offset Time to live Protocol Header Checksum Source IP Address Destination IP Address IP Options (if any) Padding Data

IP Address & Forwarding n Based on destination address (32 bits!) n n Forwarding is “hop by hop” n n an interface of a host (can have lots) Route is “how to get there” n n May change (or fail) somewhere along path Address is “where” something is n n Not source (why is it there? ) Computed seperately, continuously and asynchronously Names (see later) are “what” something is

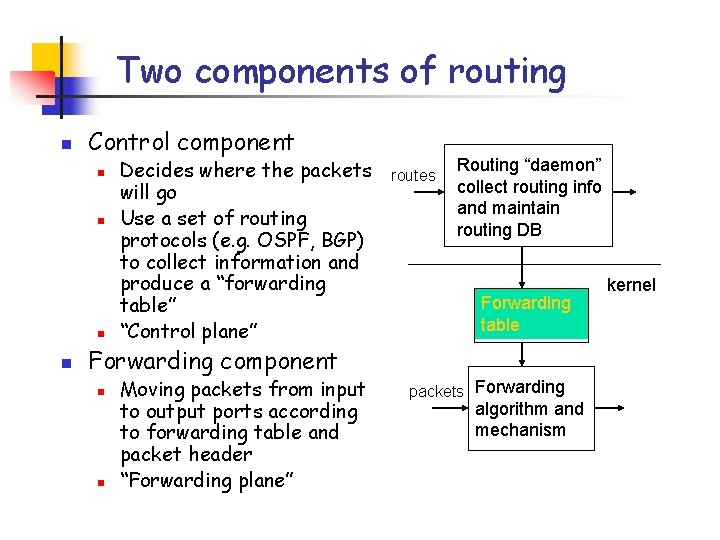
Two components of routing n Control component n n Decides where the packets will go Use a set of routing protocols (e. g. OSPF, BGP) to collect information and produce a “forwarding table” “Control plane” routes Routing “daemon” collect routing info and maintain routing DB Forwarding table Forwarding component n n Moving packets from input to output ports according to forwarding table and packet header “Forwarding plane” packets Forwarding algorithm and mechanism kernel

Address Matching n Packet forwarding requires n Address matching Followed by table lookup of output port n Moving the packet through the router (from input port to output port) This involves scheduling, queueing, design of switch fabric etc, conventional aspects of switch design n Address matching n Exact matching e. g. bridge forwarding, DECnet, OSI/CLNP… n Longest prefix match – “best matching” IP networks

Exact match n n Easier Software approach: n n n Binary search Hash function Hardware: Content Addressable Memory (CAM)

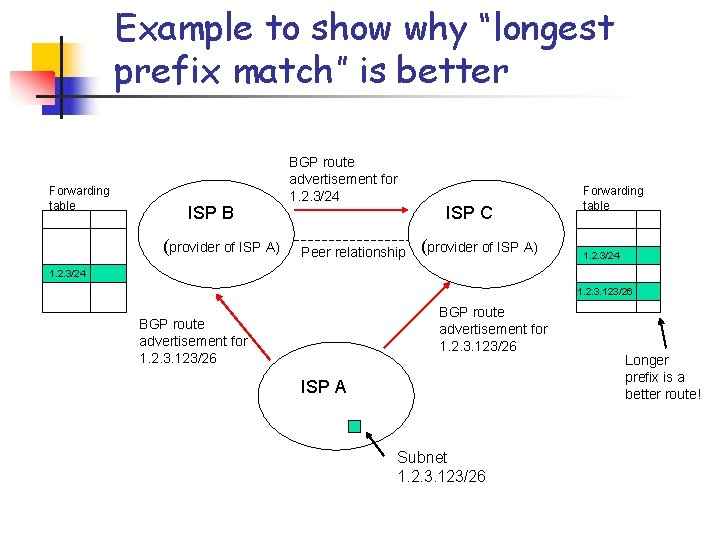
Longest prefix match n n IP addresses are assigned in a manner that reflect network topology Address aggregation: group destinations with the same prefix together if they exit the same output port Therefore, longer prefixes tend to be announced by customers ISPs who are closer to the destination, whereas provider ISPs tend to announce aggregated addresses Hence a route to the longest prefix match is preferred

Example to show why “longest prefix match” is better Forwarding table ISP B (provider of ISP A) BGP route advertisement for 1. 2. 3/24 Peer relationship ISP C (provider of ISP A) Forwarding table 1. 2. 3/24 1. 2. 3. 123/26 BGP route advertisement for 1. 2. 3. 123/26 ISP A Subnet 1. 2. 3. 123/26 Longer prefix is a better route!

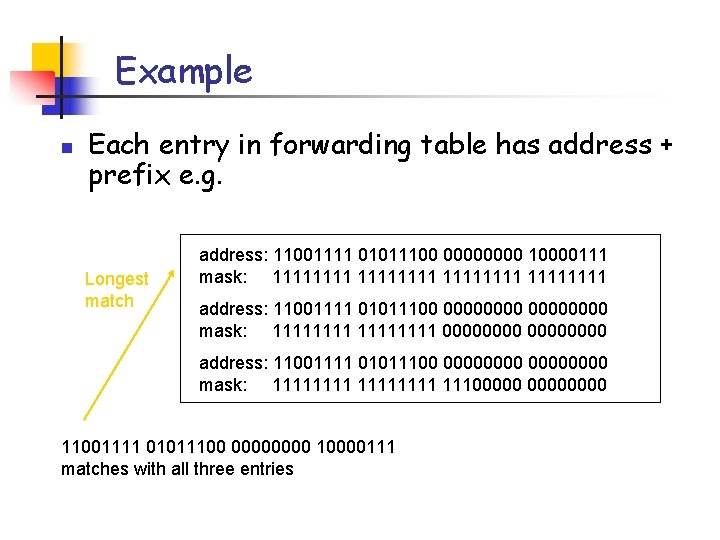
Example n Each entry in forwarding table has address + prefix e. g. Longest match address: 11001111 01011100 0000 10000111 mask: 11111111 address: 11001111 01011100 00000000 mask: 11111111 00000000 address: 11001111 01011100 00000000 mask: 11111111 11100000 11001111 01011100 0000 10000111 matches with all three entries

How to do Longest Prefix Match n n Not as easy as exact match Approaches: n n n Create a data structure for doing LPM Convert the problem into a form so that we can do binary search Reduce the problem to a sequence of exact match problems which we can apply hashing Optimization based on distribution of prefix lengths Combine software and hardware techniques

Algorithms There is an entire industry of algorithms: n Binary search among all prefixes in forwarding table Perlman’s book, 13. 4 Lampson et al “IP Lookups using Multiway and Multicolumn Search”, IEEE Infocom 1998 n Trie: bit-by-bit match Perlman’s book, 13. 3 n Binary search based on prefix length Perlman’s book, 13. 3. 3 Waldvogel et al “Scalable High Speed IP Routing Lookups”, Sigcomm 1997

But this is all going wrong! Why? n Not enough bits -> NATs… n n n Three M’s (historical order) n n Multicast Mobility Multihoming Security and Social Scale n n n NAT Traversal, Stateful browser/server end is URL + Persistent HTTP state + cookie! Unsolicited traffic Byzantine (v. selfish or rational or altruistic) Despite original ARPANET packet radio n And multicast since 1988,

So Ipng effort started in 1992 n See course web site for papers! n n n Specification of desiderata Led to a set of competing efforts Look at SIP & PIP n n n Represent extremes of CS (SIP) & Telco (PIP) SIP from PARC looks XNS n n Just ip with more address bits PIP looks VC/ATM ish… n Qo. S, fancy routing options

Eventually, converged on IPv 6 n n n Committee design Overtaken by reality ? Three M’s (current order) n n n New requirements Receiver control of input n n n Multihoming - killing aggregation Mobility (smart phones roaming and receiving IP) Multicast - sidelined? New kinds of bad guys Authentic addresses (HIP) New content type (video “interest”)

For next week (Tuesday 12 th oct) n n I want each of you to read the papers And come up with n n n 1 good feature of IPv 6 1 bad feature of IPv 6 And email me 1 slide with that on! Which YOU will present! And we will discuss how the desiderata (requirements) changed!