Mondrix Memory Isolation for Linux using Mondriaan Memory



- Slides: 23

Mondrix: Memory Isolation for Linux using Mondriaan Memory Protection Emmett Witchel Junghwan Rhee Krste Asanovic Sreeram Ramalingam 10/26/2005 CS 5204 Fall 2005 1 Oct. 26, 2005

Roadmap n Introduction n Mondria(a)n Memory Protection – Overview n Kernel Partitioning n MMP Structure and Features n Memory Supervisor n Experimental Evaluation n Conclusion and Comments CS 5204 Fall 2005 2 Oct. 26, 2005

Introduction n Motivation n Memory Protection l prevents one process from corrupting the memory of another process l Involves hardware and software l Methods: − − − Segmentation Paging Protection Keys n Fine-grained vs. Coarse-grained CS 5204 Fall 2005 3 Oct. 26, 2005

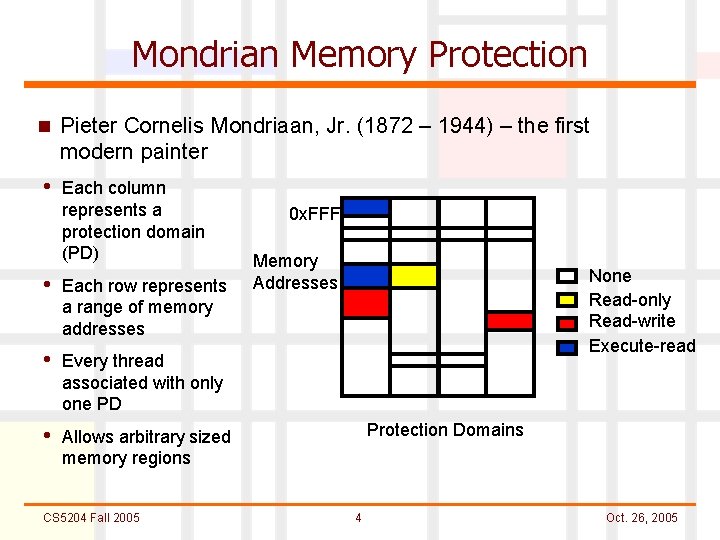
Mondrian Memory Protection n Pieter Cornelis Mondriaan, Jr. (1872 – 1944) – the first modern painter • Each column represents a protection domain (PD) • Each row represents a range of memory addresses • Every thread associated with only one PD • Allows arbitrary sized memory regions CS 5204 Fall 2005 0 x. FFF Memory Addresses None Read-only Read-write Execute-read Protection Domains 4 Oct. 26, 2005

Linux Kernel Partitioning n Mondrix isolates each kernel module in its own domain n Each module in Disk and Network Device drivers has its own domain n Basic Domains in Mondrix PD 0 – Memory Supervisor (Bottom) l PD 1 – Memory Supervisor (Top) l PD 2 – Kernel l PD 3 – String Functions l n Domain creation occurs when modules are loaded in the kernel CS 5204 Fall 2005 5 Oct. 26, 2005

Module Loading / Domain Creation n insmod program is called by user to load a new kernel module n Kernel then calls memory supervisor to set memory permissions Length of program sections l Start address of every function l Address of the return instruction l CS 5204 Fall 2005 6 Oct. 26, 2005

Domain Creation PD 1 owns the rest of the address space PD 1 owns entire address space PD 2 owns its static code and data CS 5204 Fall 2005 7 Oct. 26, 2005

Device Drivers Partitioning n Disk Driver l Device dependent bottom half l Device independent top half l Mondrix detects improper programming of device registers n Network Driver l Chip-specific portion (coordinates reception and transmission) l Board-specific portion (moves data on and off n/w card) CS 5204 Fall 2005 8 Oct. 26, 2005

Other Domain Partitions n Device Interrupts l Jumps to interrupt stubs marked executable in the global group protection domain n Inlined Functions l Export permissions on data l Uninline the function n Slab Allocator CS 5204 Fall 2005 9 Oct. 26, 2005

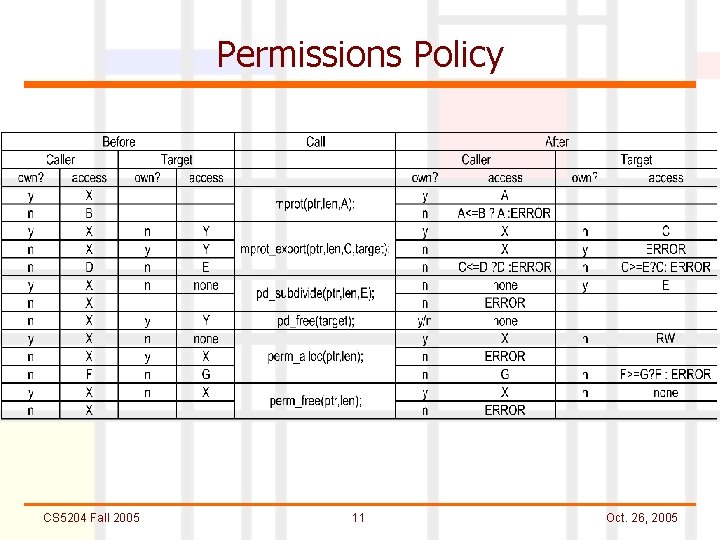
Memory Supervisor n Split into two layers – ‘top’ and ‘bottom’ n Bottom layer’s functionality is to just write the permissions table in memory n Top layer functionalities Permissions and Memory allocation (uses API calls perm_alloc and perm_free) l Thread-local stack permissions l Permissions policy l Group Protection domains l − Used in management of inodes CS 5204 Fall 2005 10 Oct. 26, 2005

Permissions Policy CS 5204 Fall 2005 11 Oct. 26, 2005

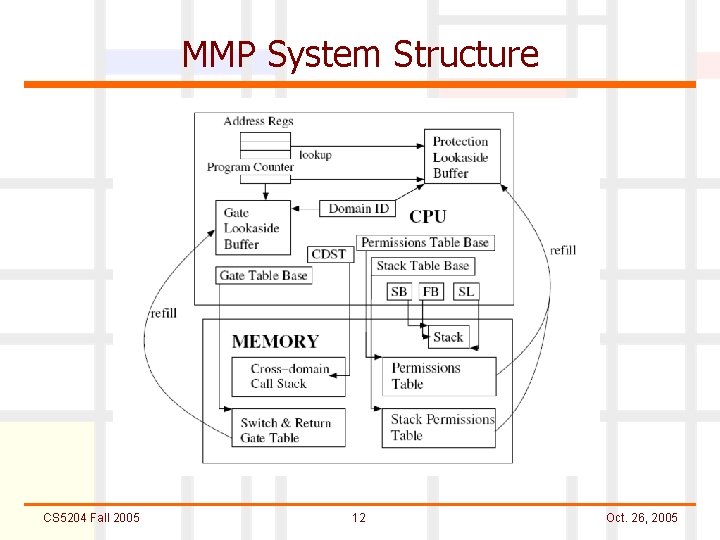
MMP System Structure CS 5204 Fall 2005 12 Oct. 26, 2005

MMP Features in Mondrix(1) n Memory Protection l Address space is the kernel virtual address space l Permissions information stored in permissions table in main memory l Protection Lookaside Buffer (PLB) is used as a cache by the MMP hardware and is similar to the TLB l Preserves the user/kernel mode distinction (uses high bit of PD-ID register) CS 5204 Fall 2005 13 Oct. 26, 2005

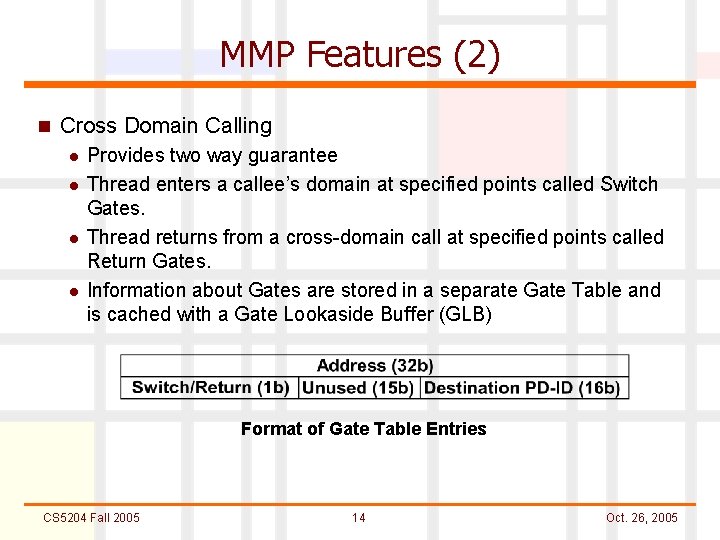
MMP Features (2) n Cross Domain Calling l l Provides two way guarantee Thread enters a callee’s domain at specified points called Switch Gates. Thread returns from a cross-domain call at specified points called Return Gates. Information about Gates are stored in a separate Gate Table and is cached with a Gate Lookaside Buffer (GLB) Format of Gate Table Entries CS 5204 Fall 2005 14 Oct. 26, 2005

Experimental Evaluations n Functional Evaluation l Expose a Linux Error! l Fault Injection experiments (used in Nooks) n Performance Evaluation l Used Sim. ICS and Bochs system emulators l CPU and Memory overheads were less than 15% l Four benchmarks were chosen − − config-xemacs thttpd find My. SQL CS 5204 Fall 2005 15 Oct. 26, 2005

Linux Error! n free_task_struct() used to free the task structure if the task structure reference count is zero n Proc_pid_lookup() and proc_pid_delete_inode() call free_task_struct() n During kernel initialization task structure count is zero causing kernel stack memory to be freed CS 5204 Fall 2005 16 Oct. 26, 2005

Fault Injection Experiments n Fault Types l Bit flips l Low-level software faults l High-level software faults n Corruption Detection l Indirect Corruption l Direct Corruption − − − Checksum mem. Test File copies Source: The Rio File Cache: Surviving Operating System Crashes CS 5204 Fall 2005 17 Oct. 26, 2005

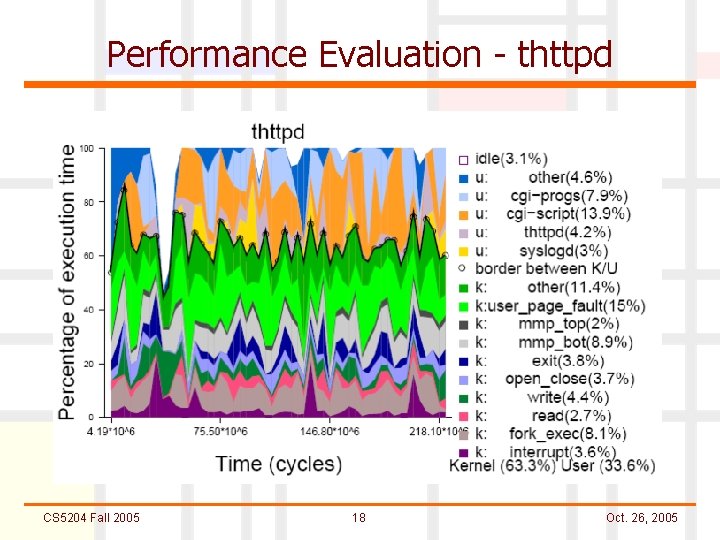
Performance Evaluation - thttpd CS 5204 Fall 2005 18 Oct. 26, 2005

Performance Evaluation n Cross Domain Calling l Cross domain calls accounted for less than 1% of total execution time l Cross domain call stack never grew deeper than 64 entries n Memory Use l Sum of Active and Inactive memory in kernel was within 1% for Mondrix and Linux n PLB Refill Traffic l Less than 4% execution time spent in PLB refilling CS 5204 Fall 2005 19 Oct. 26, 2005

Related Work n Nooks uses conventional hardware to isolate modules in different addressing contexts. n Language-based protection l Use safe languages for OS implementation n Hardware-based protection l Use of NX bit n OS structure-based CS 5204 Fall 2005 20 Oct. 26, 2005

Conclusion n Provides Fine-grained memory protection n Backward compatibility for operating systems, ISAs and programming models n Additional hardware not on processor’s critical path n Fits naturally with how modern software is designed and written CS 5204 Fall 2005 21 Oct. 26, 2005

Questions/Comments? CS 5204 Fall 2005 22 Oct. 26, 2005

MMP Features (3) n Stack Permissions l Registers designate stack frames in the current domain as readable or writable l Earlier frames are designated as read only l Stack write permissions table is used to decide whether a given stack address is writable by the thread (This is also cached in the PLB) CS 5204 Fall 2005 23 Oct. 26, 2005