Modeling Secure Connectivity of SelfOrganized Wireless Ad Hoc







- Slides: 17

Modeling Secure Connectivity of Self-Organized Wireless Ad Hoc Networks Chi Zhang, Yang Song and Yuguang Fang IEEE INFOCOM 2008 Computer Architecture Lab. Hanbit Kim 2008. 12. 4

Contents Introduction Problem & Answer Network Model Problem Formulation Properties of Secure Graph Conclusion Discussion 2/17

Introduction Wireless Ad Hoc Networks (WANET) Wireless networks without the support of centralized network management 3/17

Introduction Security architecture with selforganization Users prefer to join and leave the network at random. Without the trusted third party How to exploit primary security associations (SA) for secure connectivity 4/17

Question & Answer Question What is the minimum fraction of primary SAs for securing all the links? Answer When the average number of authenticated neighbors of each node is Θ(1) 5/17

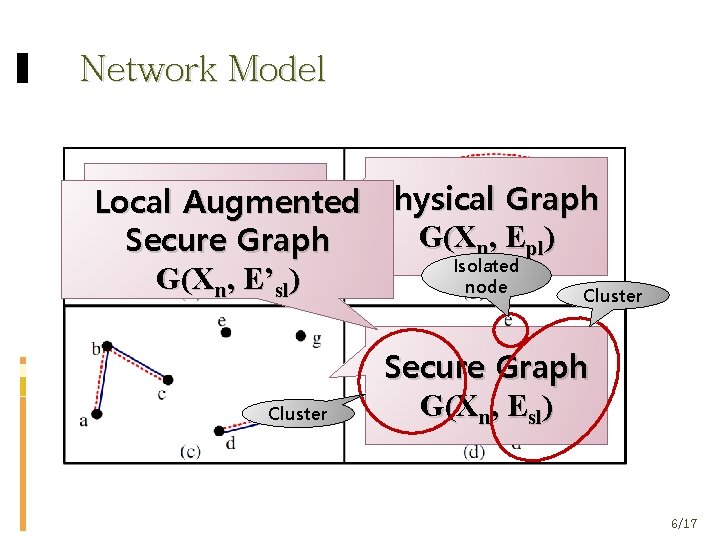
Network Model Physical Graph Local Trust. Augmented Graph G( Χ , Ε ) Secure G(Χn, ΕGraph ) n pl SA Isolated G(Χn, Ε’sl) node Cluster Secure Graph G(Χn, Εsl) 6/17

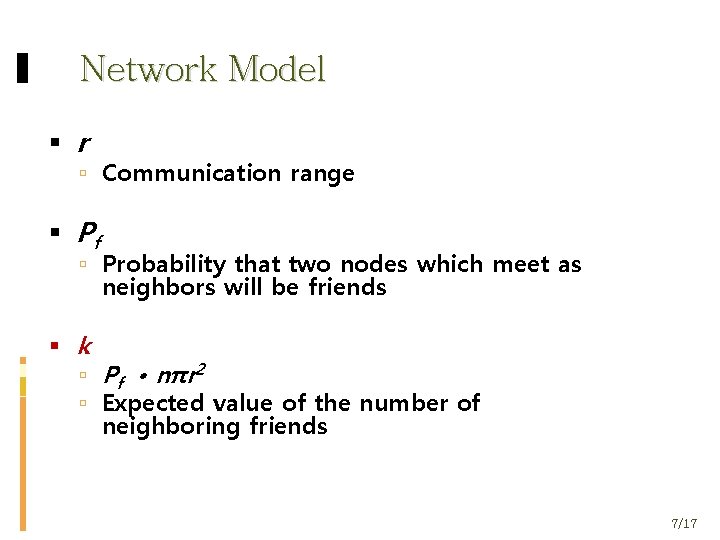
Network Model r Communication range Pf Probability that two nodes which meet as neighbors will be friends k Pf • nπr 2 Expected value of the number of neighboring friends 7/17

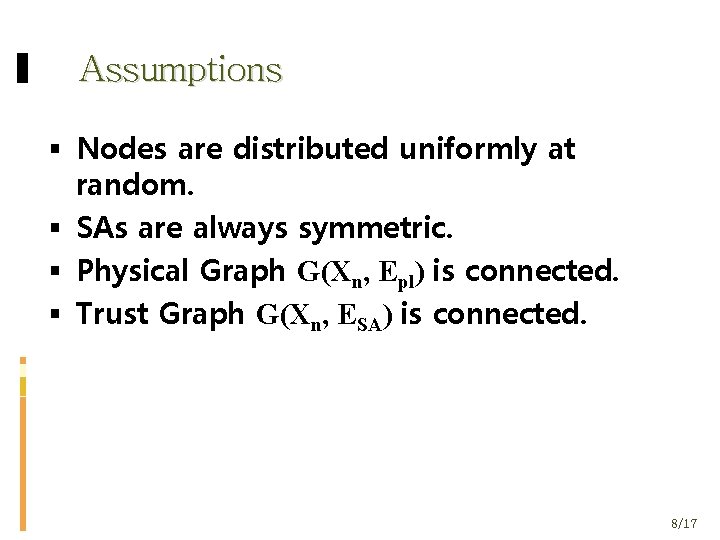
Assumptions Nodes are distributed uniformly at random. SAs are always symmetric. Physical Graph G(Χn, Εpl) is connected. Trust Graph G(Χn, ΕSA) is connected. 8/17

Problem Formulation Constructing a secure path between an arbitrary pair of nodes What should k be? We must avoid routing-security dependency loop. 9/17

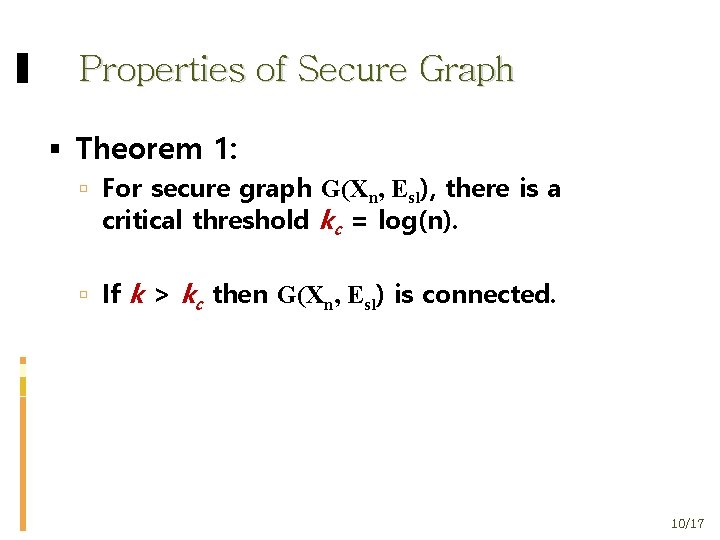
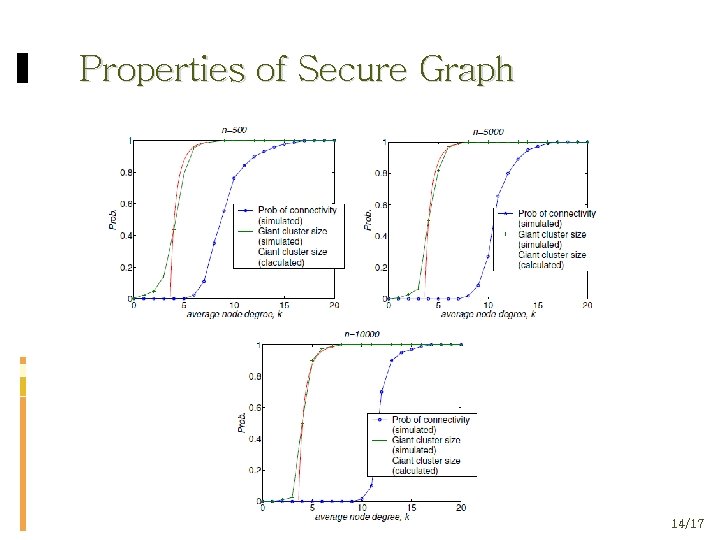
Properties of Secure Graph Theorem 1: For secure graph G(Χn, Εsl), there is a critical threshold kc = log(n). If k > kc then G(Χn, Εsl) is connected. 10/17

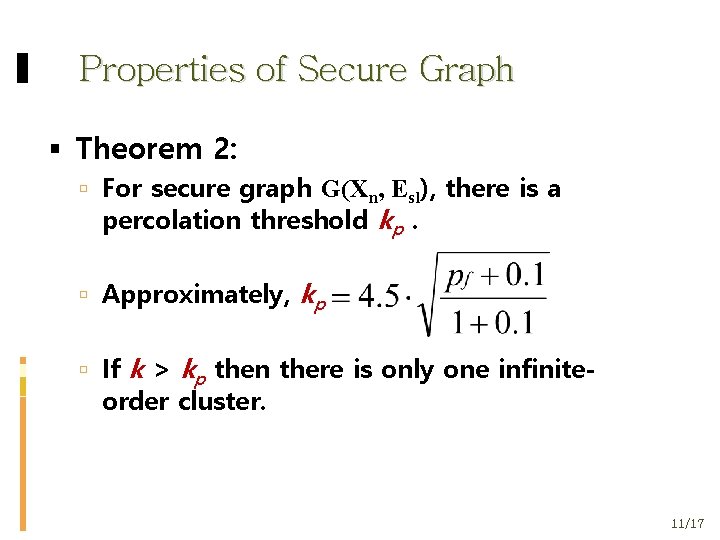
Properties of Secure Graph Theorem 2: For secure graph G(Χn, Εsl), there is a percolation threshold kp. Approximately, kp If k > kp then there is only one infinite- order cluster. 11/17

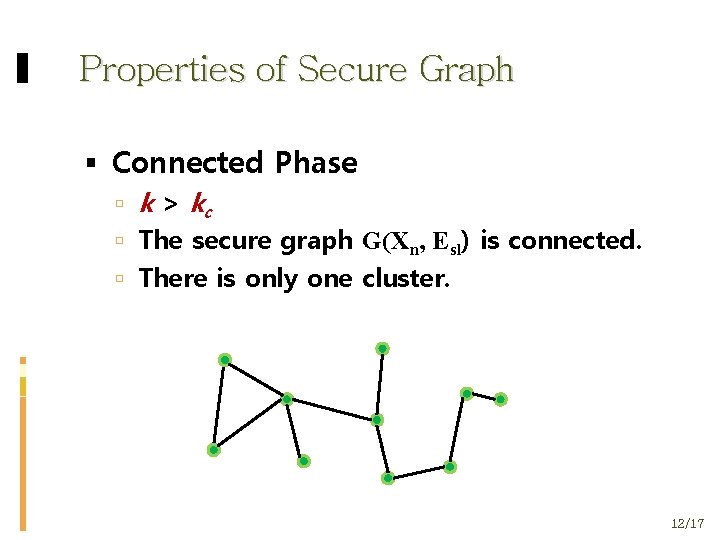
Properties of Secure Graph Connected Phase k > kc The secure graph G(Χn, Εsl) is connected. There is only one cluster. 12/17

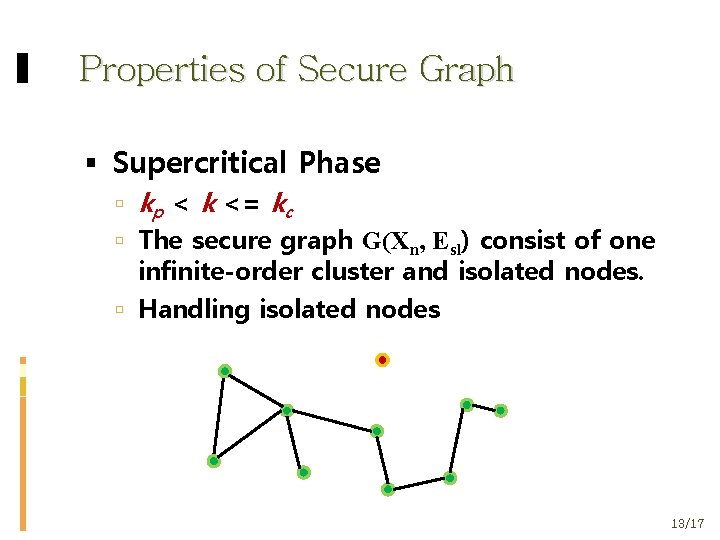
Properties of Secure Graph Supercritical Phase kp < k <= kc The secure graph G(Χn, Εsl) consist of one infinite-order cluster and isolated nodes. Handling isolated nodes 13/17

Properties of Secure Graph 14/17

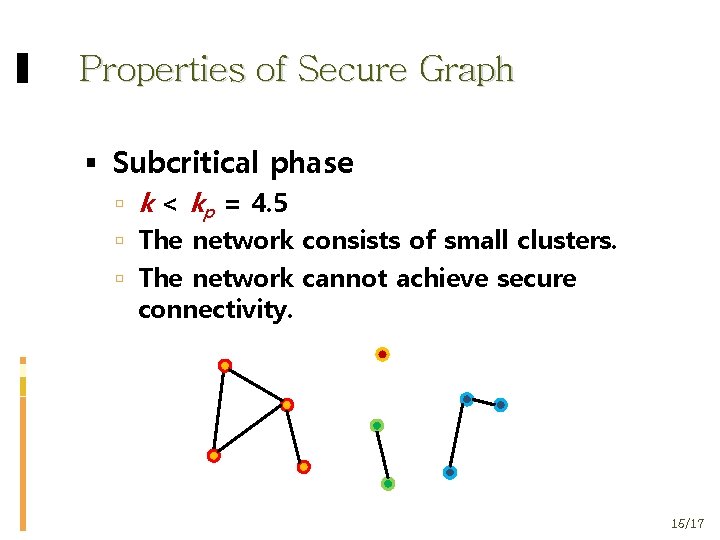
Properties of Secure Graph Subcritical phase k < kp = 4. 5 The network consists of small clusters. The network cannot achieve secure connectivity. 15/17

Conclusion The secure graph is at least in the supercritical phase. Achieve secure connectivity when the average number of authenticated neighbors is at least Ω(1). 16/17

Discussion Not uniform distribution Not connected trust graph 17/17
 Hic haec hoc latin chart
Hic haec hoc latin chart What is false analogy
What is false analogy Post hoc test
Post hoc test Strawman arguement
Strawman arguement Post hoc ergo procter hoc
Post hoc ergo procter hoc Affirming the consequent fallacy
Affirming the consequent fallacy Gmat
Gmat Post hoc ergo proctor hoc
Post hoc ergo proctor hoc Telecommunications the internet and wireless technology
Telecommunications the internet and wireless technology Modeling role modeling theory
Modeling role modeling theory Dimensional modeling vs relational modeling
Dimensional modeling vs relational modeling Global connectivity solutions
Global connectivity solutions Teoa tools
Teoa tools Connectivity package bmw
Connectivity package bmw Edge connectivity
Edge connectivity Java data base
Java data base Data base 1
Data base 1 Interactive connectivity establishment
Interactive connectivity establishment