MGMT Managing Information Chapter 17 Importance of Information






- Slides: 13

MGMT Managing Information Chapter 17

Importance of Information can be used: First-Mover Advantage Strategic advantage companies earn being first to use information technology to substantially lower costs or differentiate a product. Usually have higher market shares & profits Sustaining a Competitive Advantage 2

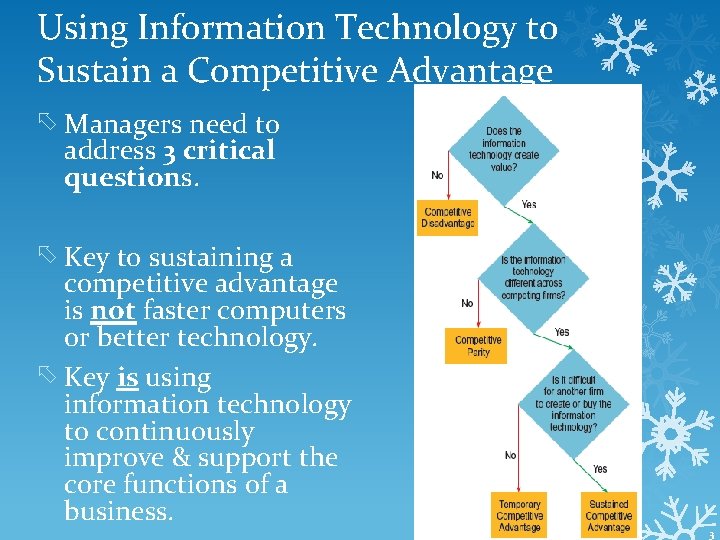
Using Information Technology to Sustain a Competitive Advantage Managers need to address 3 critical questions. Key to sustaining a competitive advantage is not faster computers or better technology. Key is using information technology to continuously improve & support the core functions of a business. 3

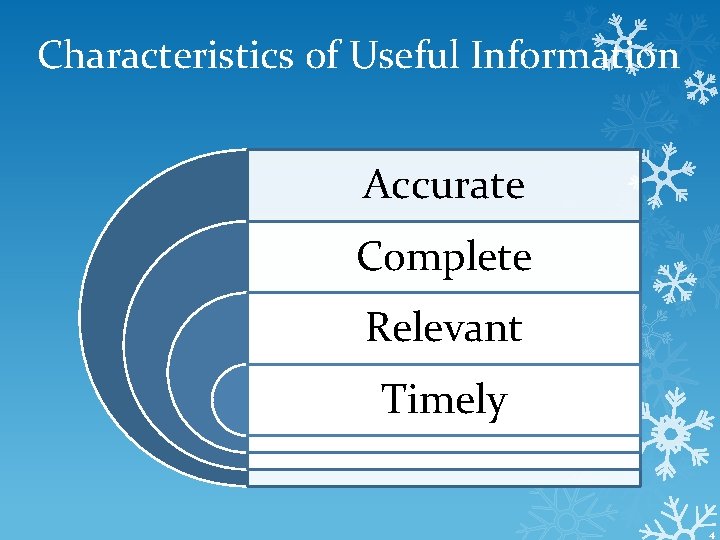
Characteristics of Useful Information Accurate Complete Relevant Timely 4

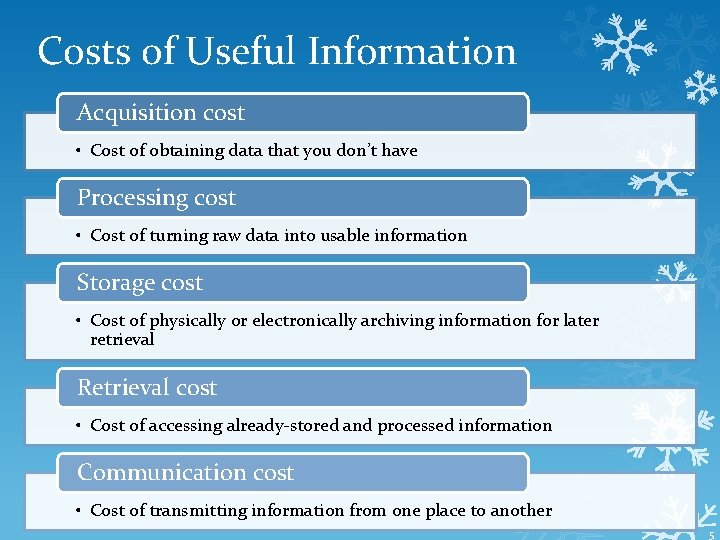
Costs of Useful Information Acquisition cost • Cost of obtaining data that you don’t have Processing cost • Cost of turning raw data into usable information Storage cost • Cost of physically or electronically archiving information for later retrieval Retrieval cost • Cost of accessing already-stored and processed information Communication cost • Cost of transmitting information from one place to another 5

Methods of Capturing Information Manual - slow, costly, labor-intensive Electronically Bar codes – requires direct line of sight Radio frequency identification (RFID) tags Electronic scanners Optical character recognition 6

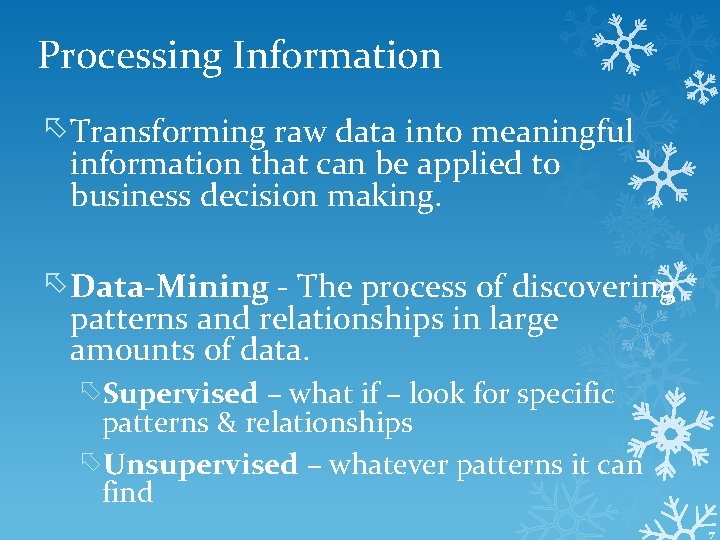
Processing Information Transforming raw data into meaningful information that can be applied to business decision making. Data-Mining - The process of discovering patterns and relationships in large amounts of data. Supervised – what if – look for specific patterns & relationships Unsupervised – whatever patterns it can find 7

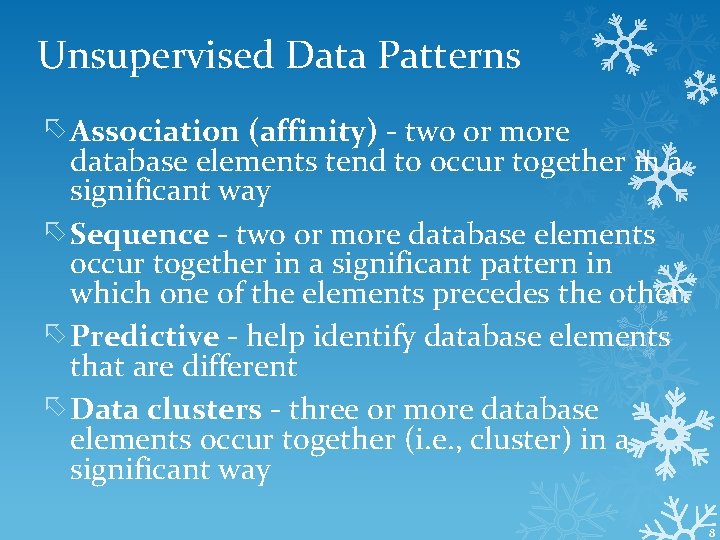
Unsupervised Data Patterns Association (affinity) - two or more database elements tend to occur together in a significant way Sequence - two or more database elements occur together in a significant pattern in which one of the elements precedes the other. Predictive - help identify database elements that are different Data clusters - three or more database elements occur together (i. e. , cluster) in a significant way 8

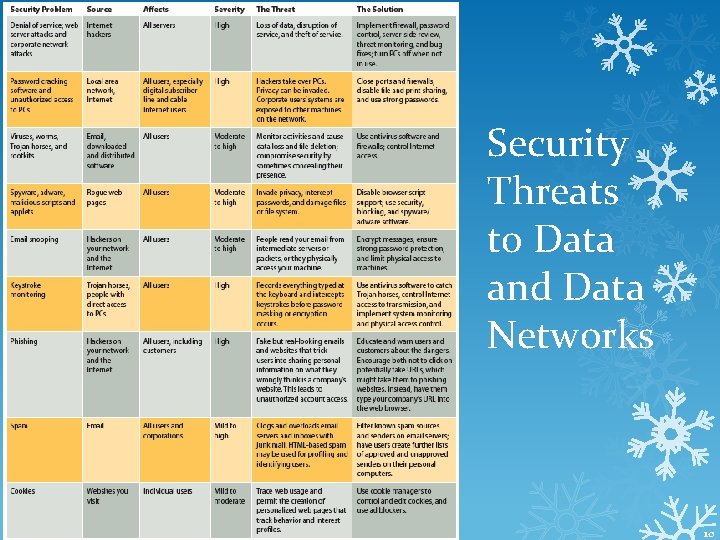
Protecting Information Process of ensuring that data are reliably and consistently retrievable in a usable format for authorized users but no one else. Authentication Authorization Two-factor authentication Biometrics Firewalls Data encryption Virtual private networks Secure sockets layer encryption Hiring white hat hackers 9

Security Threats to Data and Data Networks 10

Summary First-mover advantage is the strategic advantage that companies earn by being the first in an industry to use new information technology Information technology that companies use include bar codes, RFID tags, and electronic scanners Companies use IT to improve internal and external access and sharing of information and sharing of knowledge and expertise 11

Key Terms Moore’s law Processing information Raw data Data mining Information Data warehouse First-mover advantage Supervised data mining Acquisition cost Unsupervised data mining Processing cost Association or affinity patterns Storage cost Sequence patterns Retrieval cost Predictive patterns Communication cost Data clusters Bar code Protecting information Radio frequency identification (RFID) tags Authentication Electronic scanner Optical character recognition Authorization 12

Key Terms Two-factor authentication Intranets Firewall Corporate portal Virus Electronic data interchange (EDI) Data encryption Virtual private network (VPN) Secure sockets layer (SSL) encryption Executive information system (EIS) Web services Extranets Knowledge Decision support system (DSS) Expert system 13