MANAGEMENT of INFORMATION SECURITY Fifth Edition CERTIFICATION AND









- Slides: 11

MANAGEMENT of INFORMATION SECURITY, Fifth Edition

CERTIFICATION AND ACCREDITATION Management of Information Security, 5 th Edition, © Cengage Learning 2

Trends in Certification and Accreditation • In security management, accreditation is the authorization of an IT system to process, store, or transmit information • It is issued by a management official and serves as a means of assuring that systems are of adequate quality • It also challenges managers and technical staff to find the best methods to assure security, given technical constraints, operational constraints, and mission requirements Management of Information Security, 5 th Edition, © Cengage Learning 3

Trends in Certification and Accreditation • Certification is “A comprehensive assessment of a system’s technical and nontechnical protection strategies, as specified by a particular set of requirements” • Organizations pursue accreditation or certification to gain a competitive advantage, or to provide assurance or confidence to customers Management of Information Security, 5 th Edition, © Cengage Learning 4

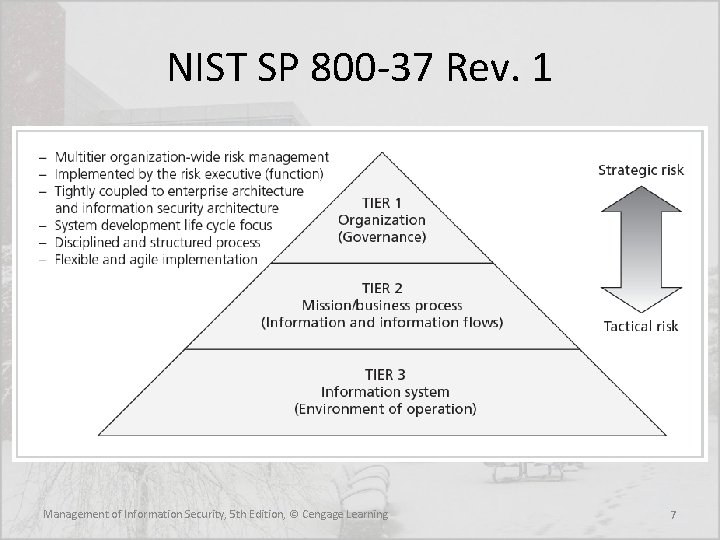
Trends in Certification and Accreditation • In 2009, the U. S. government, through NIST, changed the fundamental approach to the C&A of federal information systems, bringing the government into alignment with industry • The focus moved from formal C&A activities to a riskmanagement life cycle approach • With the publication of “NIST SP 800 -37, Rev. 1: Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach, ” the approach shifted to a process of risk management-based assessment and authorization, much of which was driven by the Federal Information Security Management Act of 2002 (FISMA) Management of Information Security, 5 th Edition, © Cengage Learning 5

NIST SP 800 -37 Rev. 1 • With the publication of NIST SP 800 -37, Rev. 1, a common approach to a Risk Management Framework (RMF) for Info. Sec practice became the standard for the U. S. government • The revised process emphasizes: (i) building Info. Sec capabilities into federal information systems through the application of state-of-the-practice management, operational, and technical security controls (ii) maintaining awareness of the security state of information systems on an ongoing basis though enhanced monitoring processes (iii) providing essential information to senior leaders to facilitate decisions regarding the acceptance of risk to organizational operations and assets, individuals, other organizations, and the Nation arising from the operation and use of information systems Management of Information Security, 5 th Edition, © Cengage Learning 6

NIST SP 800 -37 Rev. 1 Management of Information Security, 5 th Edition, © Cengage Learning 7

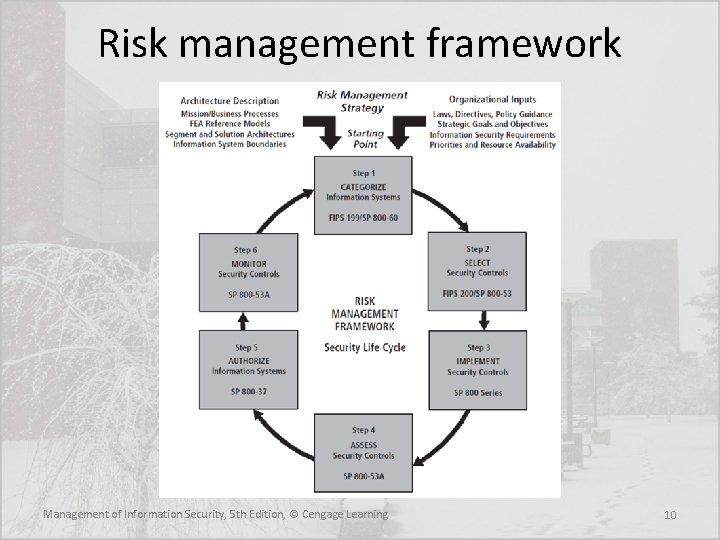
NIST SP 800 -37 Rev. 1 • The RMF steps include: – Categorize the information system and the information processed, stored, and transmitted by that system based on an impact analysis – Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on an organizational assessment of risk and local conditions – Implement the security controls and describe how the controls are employed within the information system and its environment of operation Management of Information Security, 5 th Edition, © Cengage Learning 8

NIST SP 800 -37 Rev. 1 (cont. ) – Assess the security controls using appropriate assessment procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system – Authorize information system operation based on a determination of the risk to organizational operations and assets, individuals, other organizations, and the Nation resulting from the operation of the information system and the decision that this risk is acceptable – Monitor the security controls in the information system on an ongoing basis including assessing control effectiveness, documenting changes to the system or its environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to designated organizational officials Management of Information Security, 5 th Edition, © Cengage Learning 9

Risk management framework Management of Information Security, 5 th Edition, © Cengage Learning 10

NIST SP 800 -37 Rev. 1 • Accreditation and certification are not permanent. • Just as standards of due diligence and due care require an ongoing maintenance effort, most accreditation and certification processes require reaccreditation or recertification every few years (typically every three to five years) • Approaches such as the RMF are designed to follow a continuous-improvement method, ensuring that the organization does not ramp up for a C&A cycle, then relax in the years following, potentially resulting in lapses in security, only to ramp up again prior to the next C&A cycle Management of Information Security, 5 th Edition, © Cengage Learning 11
 Management of information security 5th edition
Management of information security 5th edition Principles of marketing fifth european edition
Principles of marketing fifth european edition Psychology ciccarelli 5th edition
Psychology ciccarelli 5th edition Fundamentals of corporate finance fifth edition
Fundamentals of corporate finance fifth edition Democritus atomic model diagram
Democritus atomic model diagram Segregat
Segregat Molecular biology
Molecular biology Human anatomy fifth edition
Human anatomy fifth edition Human anatomy fifth edition
Human anatomy fifth edition Principles of information security 5th edition pdf
Principles of information security 5th edition pdf Information management principles
Information management principles Information asset classification worksheet
Information asset classification worksheet