Malware Overview Computer Security I CS 461ECE 422
































- Slides: 41

Malware Overview Computer Security I CS 461/ECE 422 Spring 2012

Reading Material • Chapter 6 of text • Ken Thompson and Trojans – http: //cm. bell-labs. com/who/ken/trust. html • Worm Anatomy and Model http: //portal. acm. org/citation. cfm? id=948196

Outline • Malware – Trojans, rootkits – Virus – Structure – Prevention – Worm – Structure – Prevention

Zero Day Exploit • An exploit that has no patch available • Time between exploit discovery and wide activation shrinking • Malware developer has trade-off – Big splash but faster discovery – Reduced attack rate but longer undiscovered

Windows Meta File Exploit • Exploit flaws in the Windows rendering engine enable remote code execution – Memory corruptions – Visiting web site with “bad image” causes attack – Drive-by download – Attack sold for $4, 000 – http: //www. eweek. com/article 2/0, 1895, 1918198, 00. asp • Bugtraq post in December 2005 – Probably lingering earlier – 0 day exploit • Microsoft’s response in early January 2006 – http: //www. microsoft. com/technet/security/bulletin/ms 06001. mspx

Malicious Code • Set of instructions that cause a site’s security policy to be violated • Often leveraging an inadvertent flaw (design or implementation) – To propagate/install on target – To cause harm on target

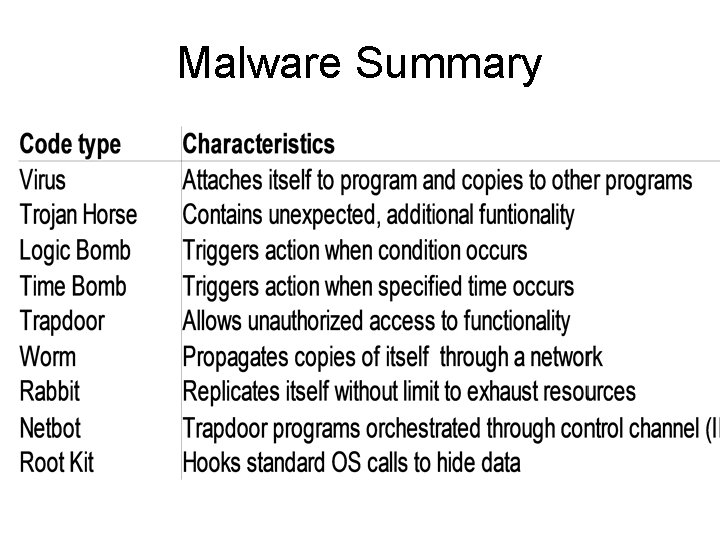
Malware Summary

Trojan Horses • Seemingly useful program that contains code that does harmful things – Perform both overt and covert actions • Frequently embedded in applets or games, email attachments (mafia wars? ) • Trojan horse logins, spoof authentication or webpage forms

Thompson's Trojan Compiler • Infect it in compiling “login” program – Add “bug” to accept fixed password • Problem: – Easily seen in code review • Solution: – Add second bug activated when compiling compiler itself – Then remove bugs from source • http: //cm. bell-labs. com/who/ken/trust. html

Rootkits • Replace function table entries. • New version performs extra checks to hide information before performing original call. • Can replace Windows API pointers (user mode) • Can also replace syscall table pointers • Both require privilege, but most Windows installs require privilege anyway • Techniques apply equally well to Linux and Mac

Rootkit Infiltration

Rootkit Countermeasures • Hard to defend/detect • User mode - Look for discrepancies • Between results of different APIs • Between API results and direct access to storage • E. g. , Rootkit revealer from Sysinternals (now MS)

Sony Player DRM and Rootkits • Bad press for Sony 2005 – Mark Russinovich's original observations http: //blogs. technet. com/markrussinovich/archive/2005/10/31/son y-rootkits-and-digital-rights-management-gone-toofar. aspx#comments – A timeline – http: //www. boing. net/2005/11/14/sony_anticustomer_te. html • To ensure that copy protection is not evaded install rootkit to hide the protection code – – Available for other attackers to use Un-installable Uses CPU and memory Not adequately noted in EULA

Virus Parts • Infection mechanism • How the virus moves from victim to victim • Trigger • The condition that causes the payload to activate or be delivered • Payload • The activity of the virus beyond the spreading • E. g. , installing software, harvesting information

Virus Operation • Virus Phases: – Dormant: Waiting on trigger event – Propagation: Replicating to programs/disks – Triggering: By event to execute payload – Execution: Executing payload • Details usually Machine/OS specific – Exploits different features or weaknesses

Virus Pseudocode • beginvirus: • If spread-condition then begin – For some set of target files do begin • If target is not infected then begin – Determine where to place virus instructions – Copy instructions from beginvirus to endvirus into target – Alter target to execute new instructions • If trigger pulled • Perform some actions • Goto beginning of infected program • endvirus:

Virus Attachment • A Virus can attach itself to a program or to data by – Appending itself to either the beginning or end of either source code or assembly, so it is activated when the program is run – Integrate itself into the program, spread out code – Compress original program so addition of virus does not change file system – Integrate into data: executable text macro, scripting – Macros and email attachments • An activated virus may: – Cause direct or immediate harm – Run as a memory resident program (TSR, daemon, or service) – Replace or relocate boot sector programs, start at system startup

Macros Viruses • Macro code attached to some data file – Interpreted rather than compiled – Platform independent – Mobile code • Interpreted by program using the file – E. g. , Word/Excel macros – Esp. using auto command macros – Often automatically invoked • Blurs distinction between data and program files making task of detection much harder • Classic trade-off: ”ease of use” vs ”security”

Email Viruses • Spread using email with attachment containing a macro virus – Melissa, Love. Bug • Triggered when user opens or executes attachment – Also when mail viewed by using scripting features in mail agent – Usually targeted at Microsoft Outlook mail agent and Word/Excel documents, Microsoft IIS

Basic Precautions • Don’t import untrusted programs – Who can you trust? – Viruses have been found in commercial shrink -wrap software – Standard download sites have been corrupted • Check MD 5 hashes • Scan for viruses, install anti-virus software • Update anti-virus software regularly

Signature Scanning • Early viruses had characteristic code patterns known as signatures • Create a database of patterns, search files for patterns (Mc. Affee) • Use data-mining, learning, feature extraction etc. to look for disguised or obfuscated patterns • Can only scan for known signatures • Text calls this “first generation” scanner

Signature Avoiding Viruses • Polymorphic Virus produces varying but operationally equivalent copies of itself – Use alternative but equivalent instructions – Gets around signature scanners. Whale virus, 32 variants • Stealth Virus actively tries to hide all signs of its presence – A virus can intercept calls to read a file and return correct values about file sizes etc. Brain Virus

Another Signature Avoiding Virus • Encrypted Virus stores bulk of self encrypted – Small decrypt routine in clear – Key stored in clear – Metamorphic virus: mutates with every infection – Similar to polymorphic – But this is a complete rewrite

Other Virus Scanners • Second generation • Use heuristics rather than direct signatures • Look for code fragments like encrypt/decrypt loops • Use integrity checks to track changes • Third generation • Track virus by actions rather than code • Identify/notify/prevent anomalous behaviour • E. g. , installing device driver after visiting a web site • E. g, Cisco Security Agent. Host based intrusion detection. Behaviour blocking software discussed in text.

Other Virus Scanners • Fourth Generation • Use multiple techniques • Scanning • Access control • Behavioural analysis

Virus Scanners v. Malware What percentage of new viruses does a virus scanner detect?

Worms • Propagate from one computer to another – Self-directed propagation • Viruses use email/infected media to propagate to so differentiation is fuzzy

The Morris Worm Incident • How 99 lines of code brought down the Internet (ARPANET actually) in November 1988. • Robert Morris Jr. Ph. D student, Cornell, wrote a program that could: – Connect to another computer, and find and use one of several vulnerabilities (buffer overflow in fingerd, password cracking, backdoor in mail program) to copy itself to that second computer. – Begin to run the copy of itself at the new location. – Both the original code and the copy would then repeat these actions in an infinite loop to other computers on the ARPANET (mistake!) • Morris was sentenced to three years of probation, 400 hours of community service, and a fine of $10, 050. (He is now a Professor at MIT. ) • Worms have gotten bigger and more aggressive

Worm Phases • Dormant • Propagation – Search for other systems to infect – Establish connection to target remote system – Replicate self onto remote system • Triggering • Execution

Who to target? • Scanning – Currently generally used – Select random addresses • Mix of addresses in current network (local computers probably have similar vulnerabilities) and remote networks – No longer feasible in IPv 6 • 32 bit vs 128 bit address space

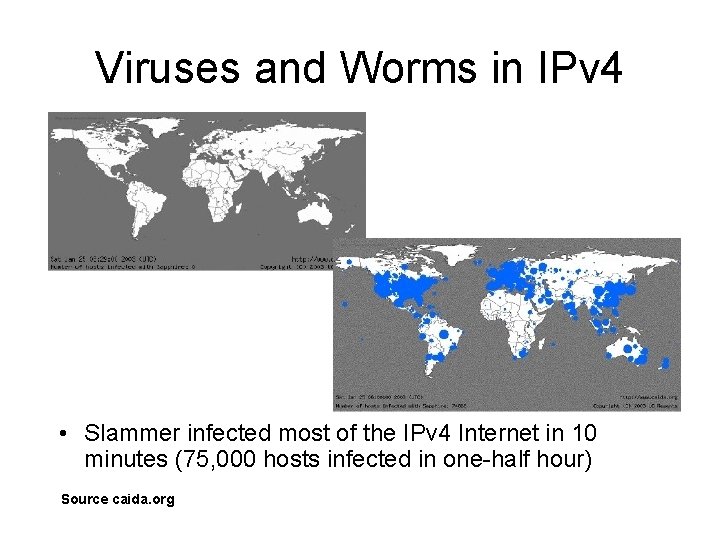
Viruses and Worms in IPv 4 • Slammer infected most of the IPv 4 Internet in 10 minutes (75, 000 hosts infected in one-half hour) Source caida. org

Worms in IPv 6 • Address space is 2^128 instead of 2^32 – Random address selection will not work • Say ¼ of address in IP 4 network run Windows (2^30) – 1 in 4 chance of finding a target with each probe • Spread that among 2^128 addresses – 1 in 2^98 chances of finding a viable target

Viruses and Worms in IPv 6 • Pure Viruses don’t change in IPv 6 but hybrid and pure worms do. – Hybrids and pure worms today rely in Internet scanning to infect other hosts, this isn’t feasible as shown earlier in this presentation. – At 1 million packets per second on a IPv 6 subnet with 10, 000 hosts it would take over 28 years to find the first host to infect – Let’s take a look at the same animation this time simulating how slammer might fare in an all IPv 6 Internet: 28 Years Later • Worm developers will adapt to IPv 6 but pure random scanning worms will be much more problematic for the attacker. Best practices around worm detection and mitigation from IPv 4 remain.

Other Techniques to Find Targets • Interesting Papers – How to 0 wn the Internet… http: //www. icir. org/vern/papers/cdcusenix-sec 02/ – Top speed of flash worms http: //www. caida. org/publications/papers/2004/topspeedworms/t opspeed-worm 04. pdf • Hitlist Scanning – Stealthy scans (randomized, over months), distributed scanning, • DNS searches, Spiders (Code red, crawls for high connectivity), listening on P 2 P networks, public lists • Permutation scanning (divide up IP address space) • Warhol worm- Hit list + permutation

Network Propagation • Send small number of packets to reduce detection • UDP packets – No ACK needed, so can spoof source address • Connect to vulnerable network services – Generally exercise buffer overflow – Launch shell • Running at high privilege (ideal) • Or use as foothold to mount other attacks to gain privilege • Or use as attack launch point

Worm Examples • Morris Worm • Code Red – – Exploited bug in MS IIS to penetrate and spread Probes random IPs for systems running IIS Had trigger time for denial-of-service attack 2 nd wave infected 360000 servers in 14 hours • Code Red 2 - trapdoor, for remote control • Nimda - used multiple infection mechanisms, email, file-sharing, web-client, IIS, Code Red 2 backdoor

More Worm Examples • SQL Slammer • Buffer overflow in MS SQL Server • Infected 90% of vulnerable hosts in 10 minutes • Conficker • Attacks windows systems to install botnet software • Password attacks and MS network vulnerabilities

Botnets • Install on compromised machines • Master sends commands to bots – Originally communicate through IRC – DDo. S, large distributed computing, spam – Now user more sophisticated P 2 P control nets – Changing domain names • Stable framework to create your own botnets – http: //www. egghelp. org/ – http: //www. energymech. net/

Drive-by Infections • Much malware installation (e. g. netbots) in caused by user-instigated drive-by download • Visit infected web site and accidently download software (like the windows meta file exploit) • Click link to view cute “Dancing bunny” e-card your friend sent you • Less is caused by direct worm-style network propagation • Improved network controls

Worm Controls • Signature based scanning • Filter-based worm containment • Payload-classification • Packet analysis. More than just scanning • Threshold random walk • Look for randomness in communication patterns • Rate limiting • Limit the amount of scan-like traffic per host • Rate halting • Stop host after limit is reached

Key points • Malware is real – Propagation – Attack – Control – Malware evolves – Technology – Motivations