Lecture5 Implementation of Information System Part II Thepul
























- Slides: 26

Lecture-5 Implementation of Information System Part - II Thepul Ginige

Major Topics • • • Security Privacy Guidelines Organizational metaphors Evaluation IS outsourcing Strategies 2

Security • Security considerations must be included when implementing a system • These include – Physical security – Logical security – Behavioral security 3

Physical Security • Physical security is controlling access to physical computer resources • Logical security is controlling software access • Behavioral security is building procedures to prevent persons from misusing computer hardware and software 4

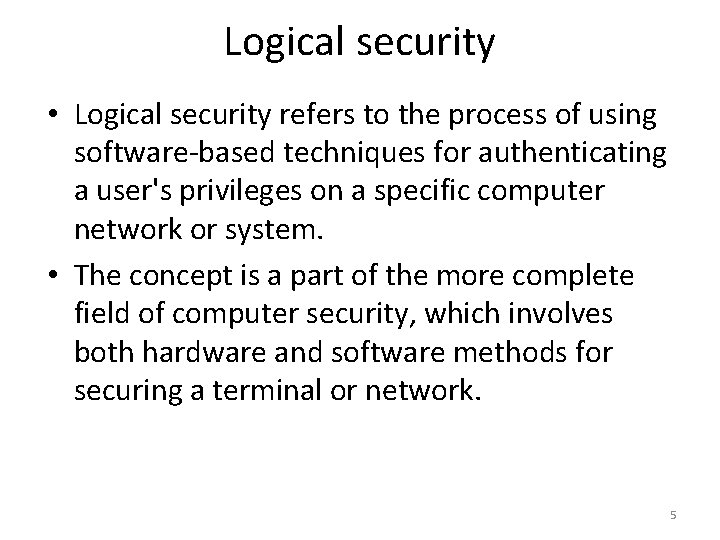
Logical security • Logical security refers to the process of using software-based techniques for authenticating a user's privileges on a specific computer network or system. • The concept is a part of the more complete field of computer security, which involves both hardware and software methods for securing a terminal or network. 5

• When discussing logical security, one should consider the different techniques used, which include : – Usernames and Passwords – Token security – Two-way Authentication on a system. 6

Behavioral security • The underlying principle of behavioral security is that all operationally relevant threats and attacks can be discerned through visibility into network traffic behavior. • Infiltrated networks exhibit host-connection patterns that deviate from historical, or normal, connection patterns. 7

Web Security • Precautions used to protect the computer network from both internal and external Web security threats include – Virus protection software – Email filtering products – URL filtering products – Firewalls, gateways, and virtual private networks 8

Web Security • Precautions, continued – Intrusion detection products – Vulnerability management products – Security technologies such as secure socket layering for authentication – Encryption technologies – Public key infrastructure use and obtaining a digital certificate 9

Ecommerce Privacy Guidelines • Privacy is essential to ecommerce • Some privacy policy guidelines are – Start with a corporate policy on privacy – Only ask for information required to complete the transaction – Make it optional for customers to fill out personal information on the Web site • Further privacy policy guidelines are – Use sources that allow you to obtain anonymous information about classes of customers – Be ethical in data gathering 10

Evaluation Approaches • Several evaluation approaches can be used: – Cost-benefit analysis – Revised decision evaluation approach – User involvement evaluations – The information system utility approach 11

Information System Utility Evaluation • The information system utility framework is a way to evaluate a new system based on utilities of – Possession – Form – Place – Time – Actualization – Goal 12

Information System Utility Evaluation • Possession utility answers the question of who should receive output • Goal utility answers the why of information systems by asking whether the output has value in helping the organization achieve its objectives • Place utility answers the question of where information is distributed 13

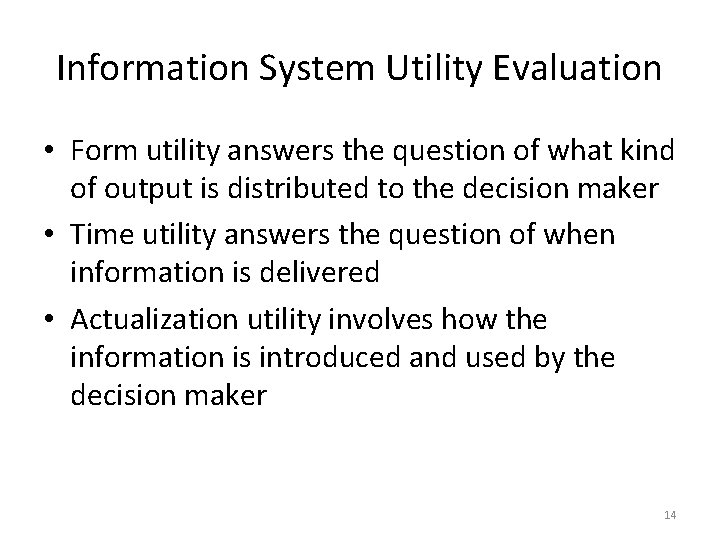
Information System Utility Evaluation • Form utility answers the question of what kind of output is distributed to the decision maker • Time utility answers the question of when information is delivered • Actualization utility involves how the information is introduced and used by the decision maker 14

Web Site Evaluation • Corporate Web sites should be evaluated • The following is a list of key things to learn about the Web site visitors: – Know how often the Web site is visited – Learn details about specific pages on the site – Find out demographic and other information about Web site visitors 15

Web Site Evaluation • Web site evaluation, continued – Discover if visitors can properly fill out the Web forms – Find out who is referring Web site visitors to the client’s Web site – Determine what browsers visitors are using – Find out if the client’s Web site visitors are interested in advertising the Web site 16

Organizational Metaphors • Organizational metaphors may be used to assist in a successful implementation of a new system 17

Organizational Metaphors (and associated concepts) • • Machines Organisms Brains Cultures Political Systems Psychic Prisons Flux and Transformation Instruments of Domination 18

Interpreting Organizational Metaphors • Machines • Efficiency, waste, maintenance, order, clockwork, cogs in a wheel, programmes, inputs and outputs, standardisation, production, measurement and control, design • Organisms • Living systems, environmental conditions, adaptation, life cycles, recycling, needs, homeostasis, evolution, survival of the fittest, health, illness 19

Interpreting Organizational Metaphors • Brains • Learning, parallel information processing, distributed control, mindsets, intelligence, feedback, requisite variety, knowledge, networks • Cultures • Society, values, beliefs, laws, ideology, rituals, diversity, traditions, history, service, shared vision and mission, understanding, qualities, families 20

Interpreting Organizational Metaphors • Political Systems • Interests and rights, power, hidden agendas and back room deals, authority, alliances, party-line, censorship, gatekeepers, leaders, conflict management • Psychic Prisons • Conscious & unconscious processes, repression & regression, ego, denial, projection, coping & defence mechanisms, pain & pleasure principle, dysfunction, workaholis 21

Interpreting Organizational Metaphors • Flux and Transformation • Constant change, dynamic equilibrium, flow, self-organisation, systemic wisdom, attractors, chaos, complexity, butterfly effect, emergent properties, dialectics, paradox • Instruments of Domination • Alienation, repression, imposing values, compliance, charisma, maintenance of power, force, exploitation, divide and rule, discrimination, corporate interest 22

IS outsourcing • Outsourcing is an arrangement in which one company provides services for another company that could also be or usually have been provided in-house. Outsourcing is a trend that is becoming more common in information technology and other industries for services that have usually been regarded as intrinsic to managing a business. 23

• In some cases, the entire information management of a company is outsourced, including planning and business analysis as well as the installation, management, and servicing of the network and workstations. 24

IS outsourcing strategies • The key to a successful outsourcing strategy is to look both outside the organization – carefully considering the vendor you will partner with – as well as the dynamics inside your own organization, and how your outsourcing strategy impacts your own people. Human capital goals must be aligned with outsourcing goals. 25

• A careful planning and consideration will help ensure your outsourcing strategy is successful. – Manage internal engagement, morale, and motivation – Maintain or enhance the company culture – Manage the community response and reaction 26