IT777 Malware Analysis Static Analysis Dr Alex V













- Slides: 24

IT-777 Malware Analysis Static Analysis Dr Alex V Mbaziira

Agenda • Anti-virus scanning • Hashing malware files • Finding Strings • Packed and Obfuscated Malware • Portable Executable File (PE) Format • Linked Libraries and Functions • Analyzing malware in VMs

Antivirus scanning • Scanning malware in multiple antivirus programs is a good first step to get a sense of what you are dealing with • How anti-virus scanners detect malware: • Some anti-virus rely on a database of known suspicious code (file signatures) • Other antivirus uses behavioral and pattern-matching analysis (heuristics) • Virus. Total (http: //www. virustotal. com/) is a web application with multiple antivirus engines for testing malware

Antivirus scanning • Antivirus is not perfect because malware authors: • modify their code hence creating new signatures that can evade virus scanners • Test new malware with anti-virus software to ensure that it evades virus scanners

Hashing malware files • Hashing a technique for generating unique signatures for files • Some popular hashing algorithms: • Message-Digest Algorithm 5 (MD 5) • Secure Hash Algorithm 1 (SHA-1) • Some hashing tools • md 5 deep • Win. MD 5

Finding Strings • A string is a sequence of characters within a program/software • Software contains strings if • it prints a message • connects to a URL • copies a file to a specific location • You can use strings software to search for strings in software • https: //docs. microsoft. com/en-us/sysinternals/downloads/strings • Strings in software executable files are stored either in ASCII or Unicode standards

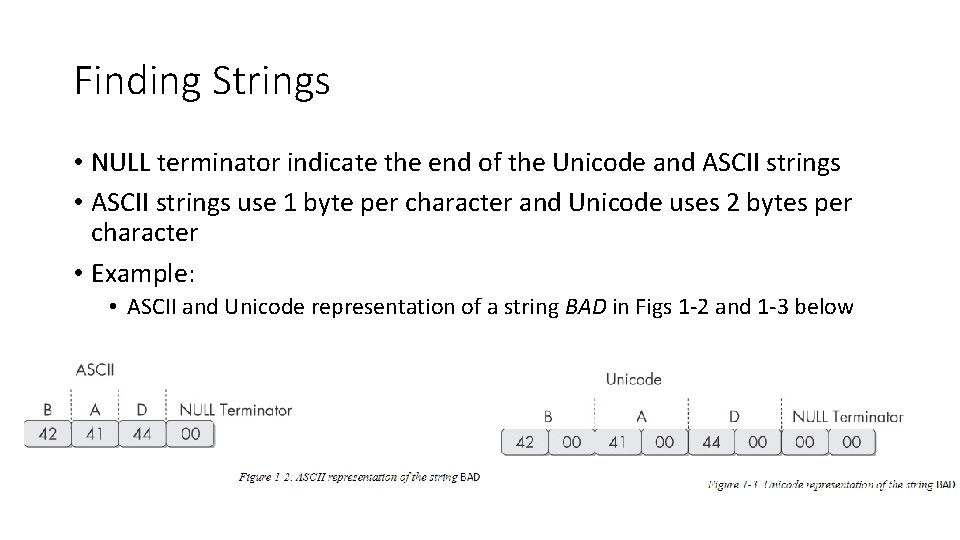
Finding Strings • NULL terminator indicate the end of the Unicode and ASCII strings • ASCII strings use 1 byte per character and Unicode uses 2 bytes per character • Example: • ASCII and Unicode representation of a string BAD in Figs 1 -2 and 1 -3 below

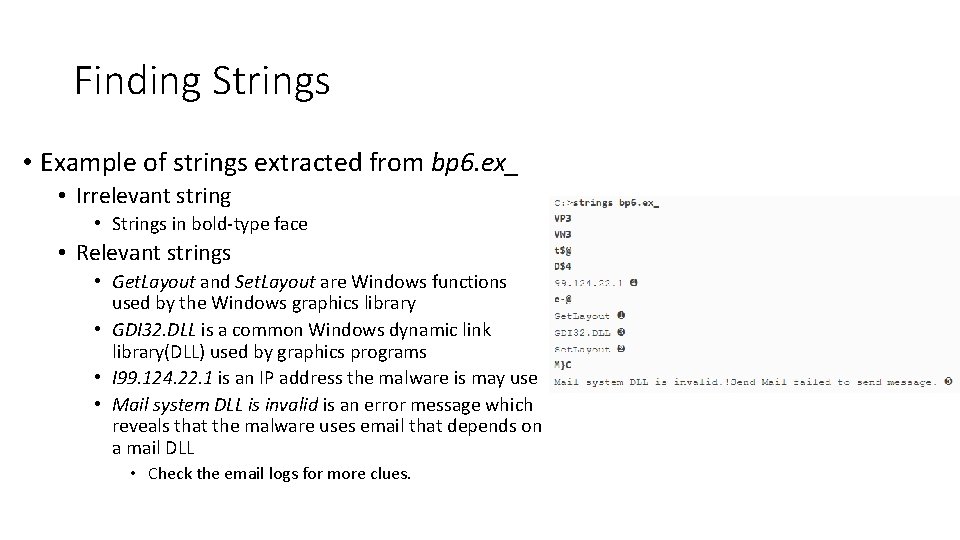
Finding Strings • Example of strings extracted from bp 6. ex_ • Irrelevant string • Strings in bold-type face • Relevant strings • Get. Layout and Set. Layout are Windows functions used by the Windows graphics library • GDI 32. DLL is a common Windows dynamic link library(DLL) used by graphics programs • I 99. 124. 22. 1 is an IP address the malware is may use • Mail system DLL is invalid is an error message which reveals that the malware uses email that depends on a mail DLL • Check the email logs for more clues.

Packed and Obfuscated Malware • Malware authors use packing and obfuscation to make it difficult to statically analyze malware • Obfuscated programs • Malware authors attempt to hide execution of malware • Packed programs • compressed programs that cannot be analyzed • Benign software normally has many strings, but obfuscated and packed software has very few strings

Portable Executable File (PE) Format • PE format is a data structure: • that contains the information required by Windows OS loader to manage wrapped executable code • used by Windows executables, object code, and DLLs • Windows files with executable code are loaded by Windows in the PE file format • PE files start with headers which contain: • information about the code • the type of application required library functions • space requirements

Linked Libraries and Functions • Programmers link imports to programs re-use functionality in multiple programs e. g. code libraries • Code libraries can be linked statically, at runtime, or dynamically. • Information in the PE header depends on how the code library is linked • This can provide better understanding of malware

Linked Libraries and Functions • Static Linking • Least common method for linking code libraries to executable code • all code from a library is copied into the executable • can’t differentiate between statically linked code and the executable’s own code • PE file header has no info to indicate that the file contains linked code

Linked Libraries and Functions • Runtime Linking • A popular method for code libraries in packed and obfuscated malware • Used in executable programs to connect libraries only when a specific function is needed • Most commonly libraries used are Load. Library and Get. Proc. Address, Ldr. Get. Proc. Address and Ldr. Load. Dll • Load. Library and Get. Proc. Address allow a program to access any function in any library on the system

Linked Libraries and Functions • Dynamic Linking • The host OS looks for the necessary libraries when the program is loaded • The function executes within the library when the program calls the linked function • The PE file header stores information on all libraries that will be loaded and every function that the program will use • This is also the most interesting linked library method for malware analysts • The Dependency Walker program (http: //www. dependencywalker. com/) can be used to show dynamically linked libraries in executable programs

PE File Header and Sections • . text • This section contains the instructions executed by the CPU • It is also the section that includes code • . rdata • This section contains the import and export information and other read-only data used by programs • Export and import information can also be viewed using tools like Dependency Walker and PEview

PE File Header and Sections • . data • This section contains the program’s global data, accessible from anywhere in the program • . rsrc • This section includes the resources used by the executable which are not considered part of the executable e. g • icons, images, menus, and strings

Analyzing malware in VMs • Malware should be analyzed from a safe contained environment to prevent it from quickly spreading to other machines on the network. • You can setup malware analysis environment using dedicated physical or virtual machines. • Dedicated physical machines can setup into an airgapped network • The main disadvantage to using physical machines is that some malware can be notoriously difficult to remove • Virtual machines are popular and are of 2 types: • Type 1 hypervisor • Type 2 hypervisor

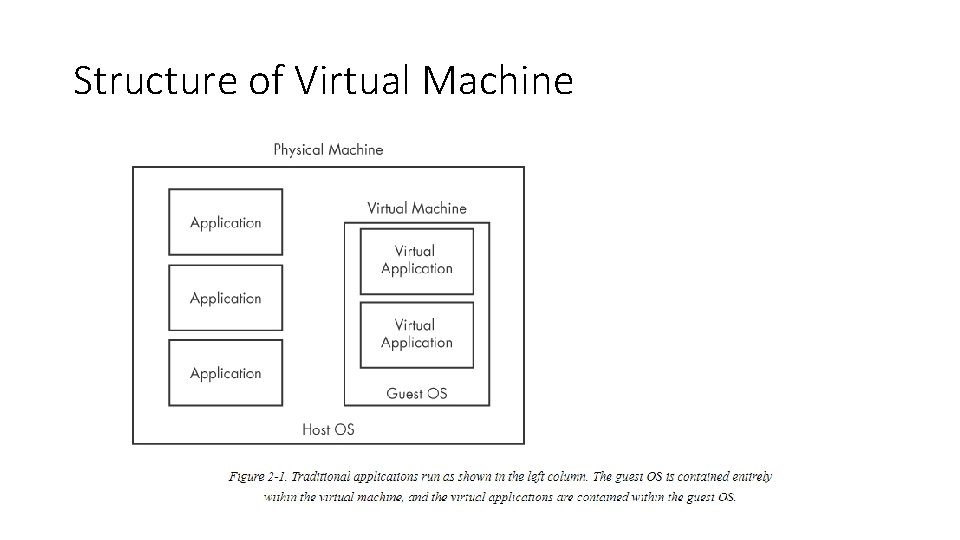
Structure of Virtual Machine

Setting up Virtual Machines • Some popular products for setting up virtual machines: • • Virtual. Box (opensource) VMWare (proprietary) Microsoft Hyper-V etc

Setting up Virtual Machines • Some popular products for setting up virtual machines: • • Virtual. Box (opensource) VMWare (proprietary) Microsoft Hyper-V Etc • Virtual machines can be configured and setup into either a host-only environment or networked with other virtual machines

Setting up Virtual Machines • Snapshots is are unique to virtual machines • A snapshot enables one to save a computer’s current state and return to that point later • Why is this a big deal in malware analysis?

Group Activity • Identify any 4 common dynamic linked libraries (DLLs) in Windows OS? What functionality is in the DLLs that you have selected? • What measures would you take to harden your virtual machine to safeguard it from malware infection? • Attempt Lab 1 -4 in the malware analysis text book • Questions 1 -4 • Keep your responses concise and precise.

References Page • Chapters 1 & 2 - Sikorski, M. , & Honig, A. (2012). Practical malware analysis: the hands-on guide to dissecting malicious software. no starch press.

Q&A