ISOIEC JTC 1SC 27 IT Security Techniques Dr






- Slides: 13

ISO/IEC JTC 1/SC 27 IT Security Techniques Dr. Walter Fumy Chairman ISO/IEC JTC 1/SC 27 Chief Scientist, Bundesdruckerei Gmb. H, Germany

SC 27 – IT Security Techniques Scope The development of standards for the protection of information and ICT. This includes generic methods, techniques and guidelines to address both security and privacy aspects, such as § Security requirements capture methodology; § Management of information and ICT security; in particular information security management systems (ISMS), security processes, security controls and services; § Cryptographic and other security mechanisms, including but not limited to mechanisms for protecting the accountability, availability, integrity and confidentiality of information; § Security management support documentation including terminology, guidelines as well as procedures for the registration of security components; § Security aspects of identity management, biometrics and privacy; § Conformance assessment, accreditation and auditing requirements in the area of information security; § Security evaluation criteria and methodology. 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 2

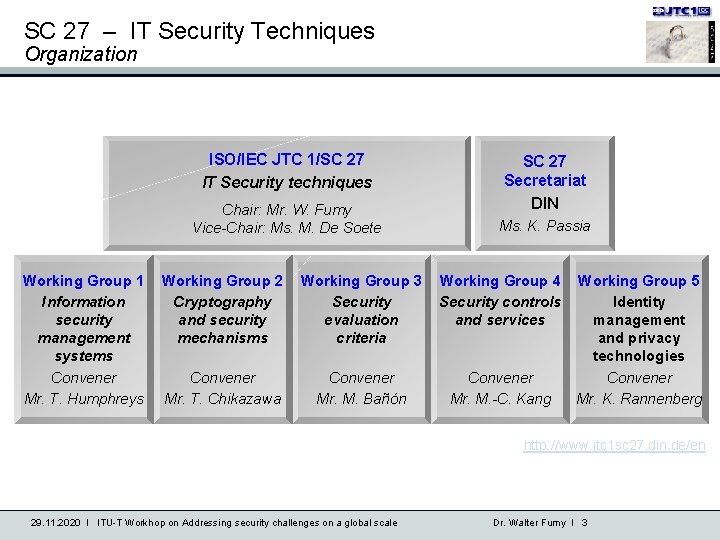
SC 27 – IT Security Techniques Organization ISO/IEC JTC 1/SC 27 IT Security techniques Chair: Mr. W. Fumy Vice-Chair: Ms. M. De Soete Working Group 1 Information security management systems Convener Mr. T. Humphreys SC 27 Secretariat DIN Ms. K. Passia Working Group 2 Cryptography and security mechanisms Working Group 3 Security evaluation criteria Working Group 4 Security controls and services Convener Mr. T. Chikazawa Convener Mr. M. Bañón Convener Mr. M. -C. Kang Working Group 5 Identity management and privacy technologies Convener Mr. K. Rannenberg http: //www. jtc 1 sc 27. din. de/en 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 3

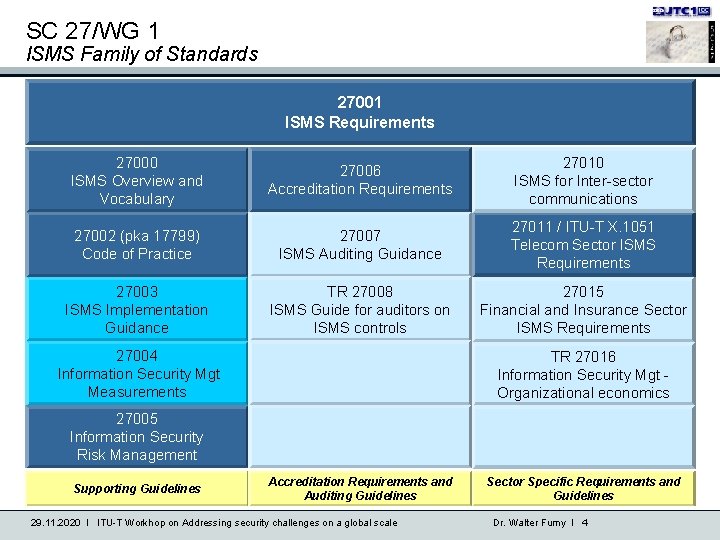
SC 27/WG 1 ISMS Family of Standards 27001 ISMS Requirements 27000 ISMS Overview and Vocabulary 27006 Accreditation Requirements 27010 ISMS for Inter-sector communications 27002 (pka 17799) Code of Practice 27007 ISMS Auditing Guidance 27011 / ITU-T X. 1051 Telecom Sector ISMS Requirements 27003 ISMS Implementation Guidance TR 27008 ISMS Guide for auditors on ISMS controls 27015 Financial and Insurance Sector ISMS Requirements 27004 Information Security Mgt Measurements TR 27016 Information Security Mgt Organizational economics 27005 Information Security Risk Management Supporting Guidelines Accreditation Requirements and Auditing Guidelines 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Sector Specific Requirements and Guidelines Dr. Walter Fumy I 4

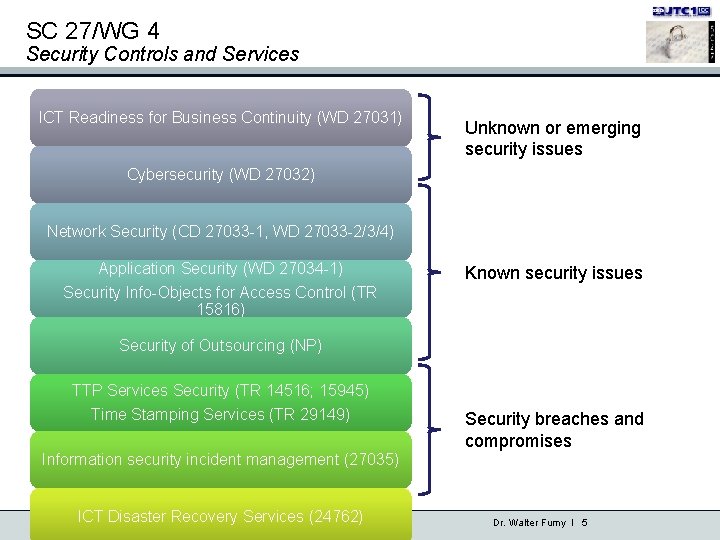
SC 27/WG 4 Security Controls and Services ICT Readiness for Business Continuity (WD 27031) Unknown or emerging security issues Cybersecurity (WD 27032) Network Security (CD 27033 -1, WD 27033 -2/3/4) Application Security (WD 27034 -1) Security Info-Objects for Access Control (TR 15816) Known security issues Security of Outsourcing (NP) TTP Services Security (TR 14516; 15945) Time Stamping Services (TR 29149) Information security incident management (27035) ICT Disaster Recovery Services (24762) 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Security breaches and compromises Dr. Walter Fumy I 5

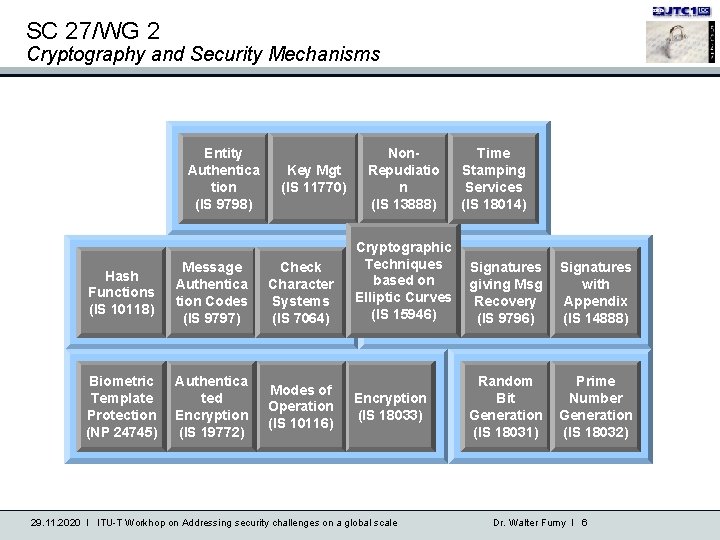
SC 27/WG 2 Cryptography and Security Mechanisms Entity Non. Time Authentica Key Mgt Repudiatio Stamping Cryptographic Protocols tion (IS 11770) n Services (IS 9798) (IS 13888) (IS 18014) Message Check Hash Authentica Character Functions Messagetion Authentication Codes Systems (IS 10118) (IS 9797) (IS 7064) Biometric Template Protection (NP 24745) Cryptographic Techniques Signatures based on giving Msg with Digital. Recovery Signatures Elliptic Curves Appendix (IS 15946) (IS 9796) (IS 14888) Authentica Modes of Encryption & ted Encryption Operation Encryption (IS 18033) Modes of Operation (IS 10116) (IS 19772) 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Random Prime Parameter Bit Number Generation (IS 18031) (IS 18032) Dr. Walter Fumy I 6

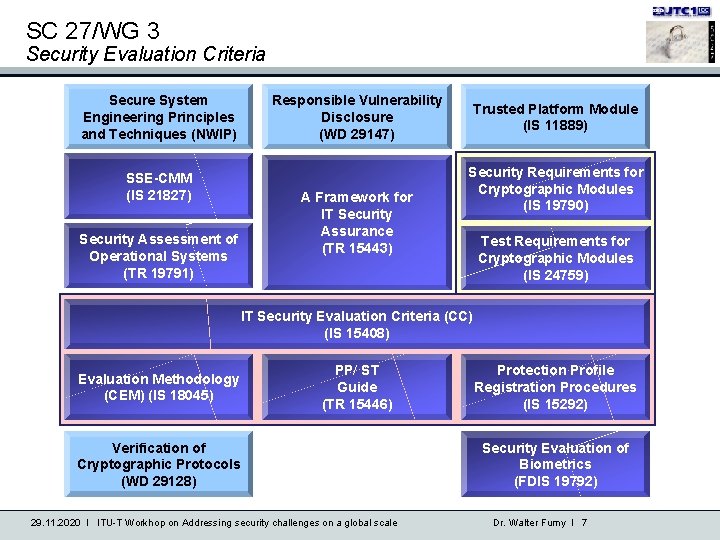
SC 27/WG 3 Security Evaluation Criteria Secure System Engineering Principles and Techniques (NWIP) SSE-CMM (IS 21827) Security Assessment of Operational Systems (TR 19791) Responsible Vulnerability Disclosure (WD 29147) A Framework for IT Security Assurance (TR 15443) Trusted Platform Module (IS 11889) Security Requirements for Cryptographic Modules (IS 19790) Test Requirements for Cryptographic Modules (IS 24759) IT Security Evaluation Criteria (CC) (IS 15408) Evaluation Methodology (CEM) (IS 18045) PP/ ST Guide (TR 15446) Verification of Cryptographic Protocols (WD 29128) 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Protection Profile Registration Procedures (IS 15292) Security Evaluation of Biometrics (FDIS 19792) Dr. Walter Fumy I 7

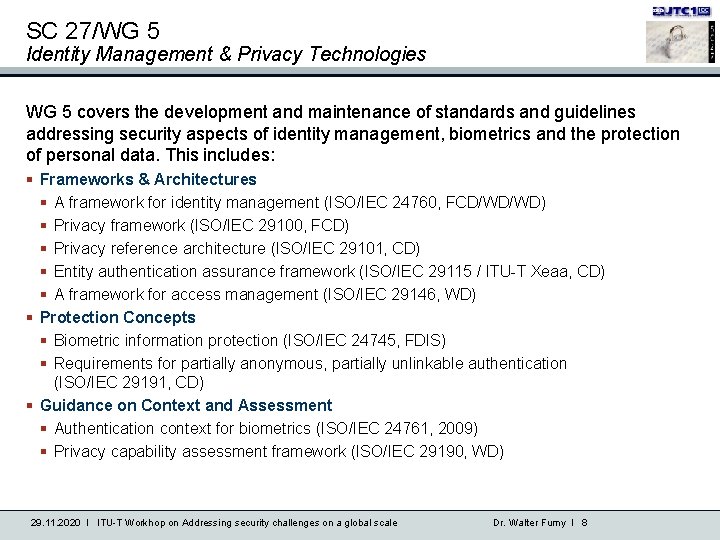
SC 27/WG 5 Identity Management & Privacy Technologies WG 5 covers the development and maintenance of standards and guidelines addressing security aspects of identity management, biometrics and the protection of personal data. This includes: § Frameworks & Architectures § A framework for identity management (ISO/IEC 24760, FCD/WD/WD) § Privacy framework (ISO/IEC 29100, FCD) § Privacy reference architecture (ISO/IEC 29101, CD) § Entity authentication assurance framework (ISO/IEC 29115 / ITU-T Xeaa, CD) § A framework for access management (ISO/IEC 29146, WD) § Protection Concepts § Biometric information protection (ISO/IEC 24745, FDIS) § Requirements for partially anonymous, partially unlinkable authentication (ISO/IEC 29191, CD) § Guidance on Context and Assessment § Authentication context for biometrics (ISO/IEC 24761, 2009) § Privacy capability assessment framework (ISO/IEC 29190, WD) 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 8

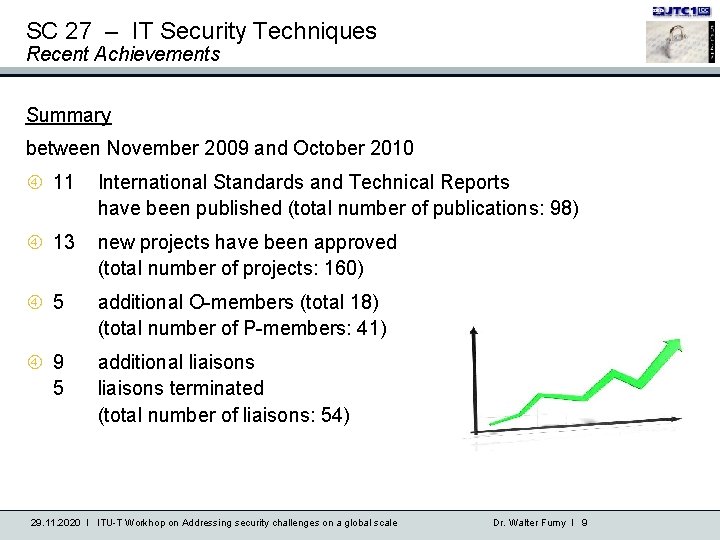
SC 27 – IT Security Techniques Recent Achievements Summary between November 2009 and October 2010 11 International Standards and Technical Reports have been published (total number of publications: 98) 13 new projects have been approved (total number of projects: 160) 5 additional O-members (total 18) (total number of P-members: 41) 9 5 additional liaisons terminated (total number of liaisons: 54) 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 9

20 Years of SC 27 Information Security Standardisation Platinum Book available from http: //www. jtc 1 sc 27. din. de/sbe/sc 27 berlin Next SC 27 meetings § Apr 11 -19, 2011 (WGs and Plenary) § Oct 10 -14, 2011 (WGs) § May 7 -15, 2012 (WGs and Plenary) Singapore Nairobi, Kenya Sweden 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 10

Thank You! Walter. Fumy@bdr. de

Areas of Collaboration include ISO/IEC 15816: Security information objects for access control (= ITU-T X. 841) ISO/IEC 14516: Guidelines on the use and management of TTP services (= ITU-T X. 842) ISO/IEC 15945: Specification of TTP services to support the application of digital signatures (= ITU-T X. 843) ISO/IEC 18028: IT network security ISO/IEC 27011: Information security management guidelines for telecommunications (= ITU-T X. 1051) ISO/IEC 27010: Information security management for inter-sector communications ISO/IEC 27014: Information security governance framework ISO/IEC 27032: Guidelines for cybersecurity ISO/IEC 24760: A framework for identity management ISO/IEC 29115: Entity authentication assurance (= ITU-T X. eaa) 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 12

Approved New Projects ISO/IEC 20004 – Software development and evaluation under ISO/IEC 15408 ISO/IEC 20008 – Anonymous digital signatures (2 Parts) ISO/IEC 20009 – Anonymous entity authentication (2 Parts) ISO/IEC TR 27016 – Information security management – Organizational economics ISO/IEC 27038 – Specification for digital redaction ISO/IEC 30104 – Physical security attacks, mitigation techniques and security requirements 29. 11. 2020 I ITU-T Workhop on Addressing security challenges on a global scale Dr. Walter Fumy I 13