Intrusion Detection Systems Dj Gerena What is an






- Slides: 10

Intrusion Detection Systems Dj Gerena

What is an Intrusion Detection System • Hardware and/or software • Attempts to detect Intrusions • Heuristics /Statistics • Signatures • Gathers and reports incidents • Sent to console • Trigger a response

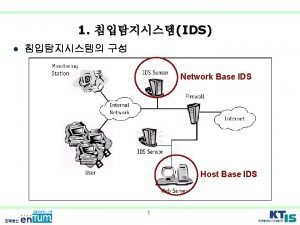
Composition of an IDS • Components are added into an existing network • Sensor • Copy a record of all network activity and sends it to the Collector • Determines if an attack is taking place • IDS Manager • Laptop/Desktop with IDS software • Check for alerts • Change settings • Database • Houses network baseline data or attack signatures


Anomaly Based vs. Signature Based IDS • Anomaly Based • Monitors network traffic • Keeps track of patterns of traffic and information to obtain baseline • If deviation in network behavior is detected, IDS will assume an attack • Higher risk of false positive • Signature Based • Attack Signature database is maintained • Compare traffic to the database • If match is found, alert is sent • Requires constant updates

Network-Based vs. Host-Based IDS • Network-Based • Monitors all traffic on the network • Useful for monitoring non critical systems. • Host-Based • IDS customized to a specific server • Being closer to host allows for greater chance of detection • Prevents threats such as Trojans and backdoors from being installed form within the network

Passive vs. Reactive • Passive • When an attack is detected an alarm or alter will be triggered • No further action is performed by the IDS • Reactive • Collector will send an alert • Send instruction to firewall and router to block activity from occurring on the network • Response should be managed and assessed, regardless of system being used.

Response to Attacks • If an automatic response was not enacted • Verify that an attack occurred • Shutdown any necessary ports or processes • Do a quick damage assessment • Once response has been applied • Patch/block vulnerabilities • Verify if attack has ended • Determine whether to lift blocks

Benefits of IDS • Eliminate the need to shut down a network when an attack occurs • Allows user to observe the type of attack and methods used by the attack to prevent future attacks • The security baseline defines the criteria such as used bandwidth, protocols, ports, and the types of devices that can be connected to each-other.

Sources • http: //www. firewalls. com/blog/intrusion_detection/ • https: //www. sans. org/readingroom/whitepapers/detection/understanding-intrusiondetection-systems-337 • https: //www. sans. org/readingroom/whitepapers/detection/intrusion-detection-systemsdefinition-challenges-343 • http: //www. youtube. com/watch? v=O 2 Gz-v 8 Wsw. Q