Introduction to Security in Computing 01204427 Computer and








- Slides: 17

Introduction to Security in Computing 01204427 Computer and Network Security Semester 1, 2011 Lecture #01

What’s about Security � Why to secure something? � Valuable � How assets to protect to secure? � Place in a safe place � Guarding � How strong of protection? � May implement several layers � May be complex locks system � May need multiple parties to grant access

Principle of Adequate Protection Computer items must be protected to a degree consistent with their value

Security in Computing System � Computing � Collection � HW � Storage � Data � People System of

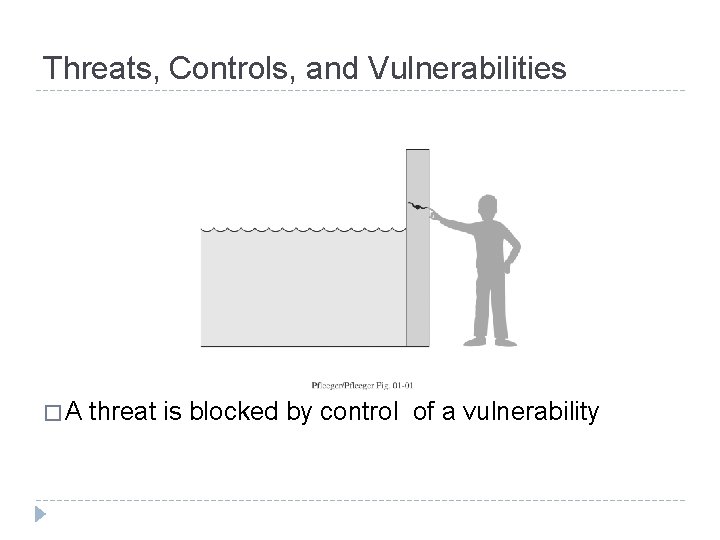
Threats, Controls, and Vulnerabilities �A threat is blocked by control of a vulnerability

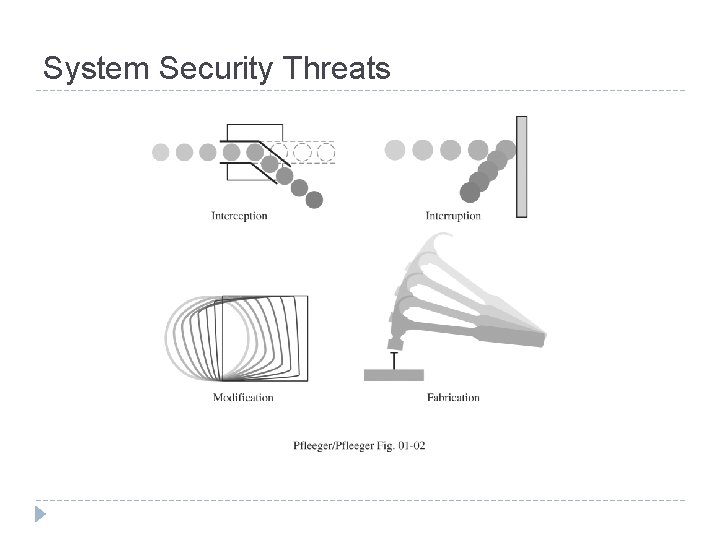
System Security Threats

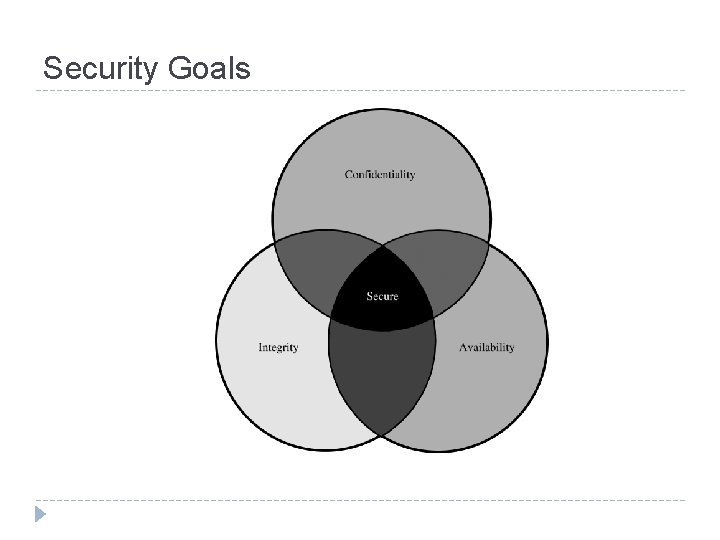
Security Goals

Security Goal: Confidentiality � Only authorized people or system can access protected data � Ensuring � More the confidentiality can be difficult! to concern � Access : a single bit or the whole collection? � Disclose to other parties prohibit?

Security Goal: Integrity � Several meanings � Precise � Accurate � Unmodified � Modified in acceptable way � Consistent � May cover two or more of above properties

Security Goal: Availability � Several properties Present in a usable form � Enough capacity to meet the service’s needs � Bounded waiting time � Completed services in an acceptable period of time � � System is well available if : - Timely response to a request � Generalized fairly allocate resources � Fault tolerance (graceful cessation instead of crash or abrupt) � Easily to be used � Concurrency is controlled (simultaneous, deadlock management, exclusive access) �

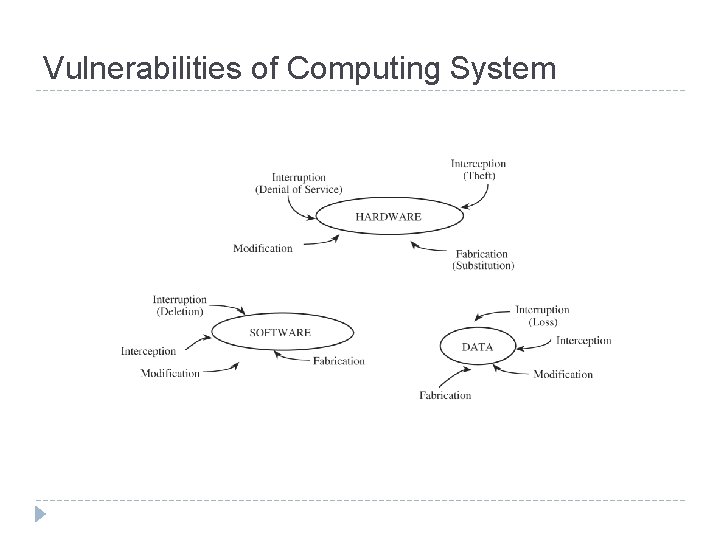
Vulnerabilities of Computing System

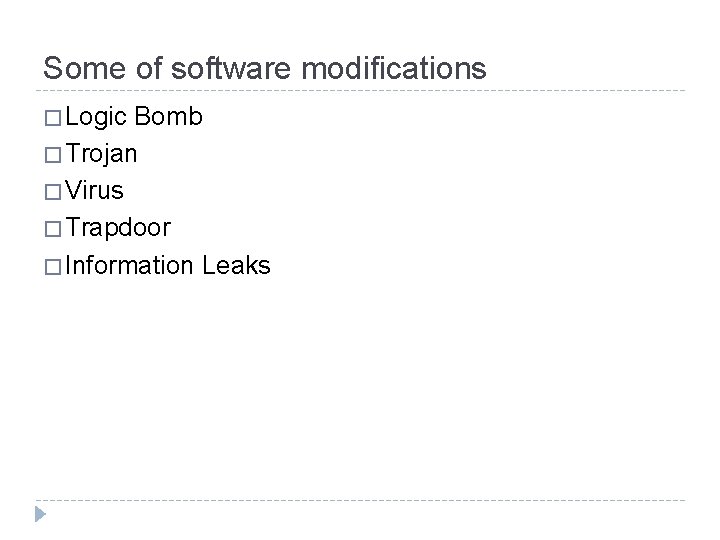
Some of software modifications � Logic Bomb � Trojan � Virus � Trapdoor � Information Leaks

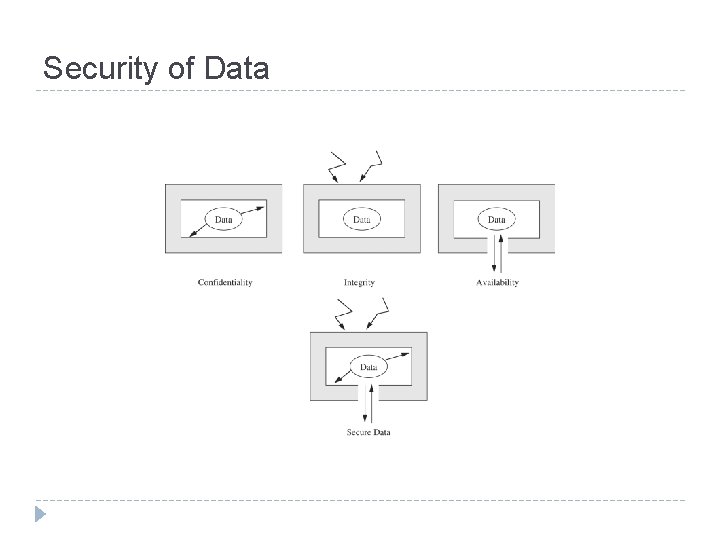
Security of Data

Computer Criminal � Armatures � Crackers � Career Criminals � Terrorists

Method of Defense � Prevent � Blocking the attack � Closing the vulnerability � Deter � Making the attack harder � Deflect � Making another target more attractive � Detect � Discover real-time or off-line � Recover � From its effects

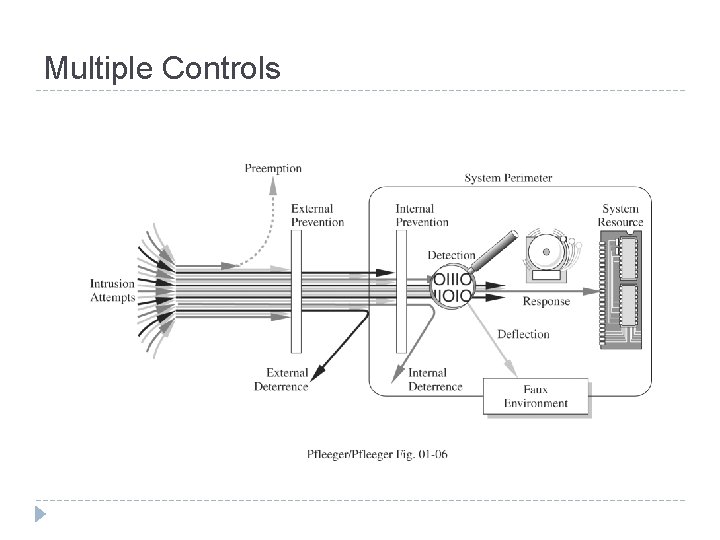
Multiple Controls

Q&A