Implementation of SHA1 and ECDSA for Vehicular Ad





- Slides: 19

Implementation of SHA-1 and ECDSA for Vehicular Ad. Hoc Network using NS-3 Author: Sinan Nacy, Tae Oh, Jim Leone Publisher: Proceedings of the 2 nd annual conference on Research in information technology (2013) Presenter: 柯懷貿 Date: 2018/12/19 Department of Computer Science and Information Engineering National Cheng Kung University, Taiwan R. O. C.

Introduction l As with any other emerging technology, standards and protocols for VANET have to be created and tested before being adopted. The implementation of such a technology in a real world scenario will increase the safety of drivers. l Any digital security implementation must be sufficiently efficient to allow anticipated (message) traffic to occur without degradation to the network’s realtime capabilities. l The NS-3 network simulator provides a convenient test-bed with which to test an algorithm’s efficiency. National Cheng Kung University CSIE Computer & Internet Architecture Lab 2

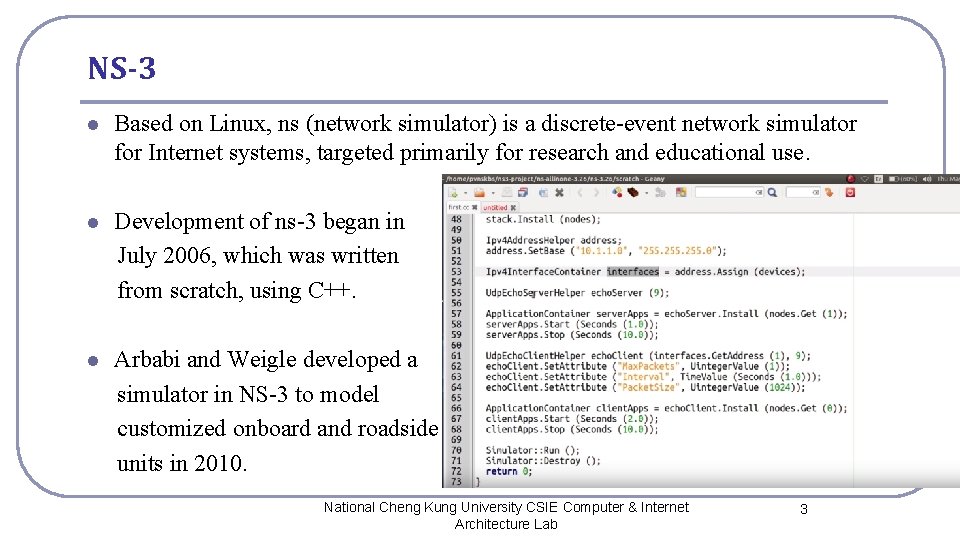
NS-3 l Based on Linux, ns (network simulator) is a discrete-event network simulator for Internet systems, targeted primarily for research and educational use. l Development of ns-3 began in July 2006, which was written from scratch, using C++. l Arbabi and Weigle developed a simulator in NS-3 to model customized onboard and roadside units in 2010. National Cheng Kung University CSIE Computer & Internet Architecture Lab 3

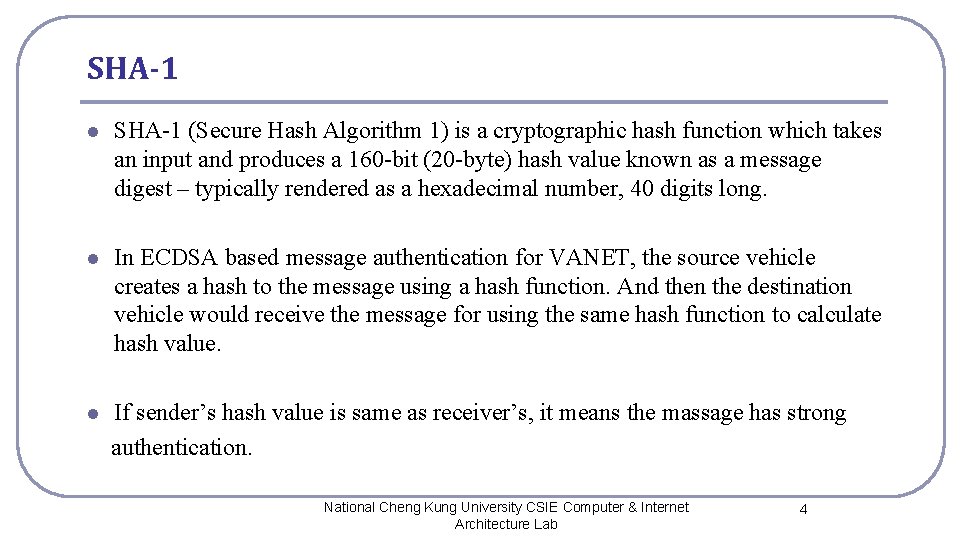
SHA-1 l SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function which takes an input and produces a 160 -bit (20 -byte) hash value known as a message digest – typically rendered as a hexadecimal number, 40 digits long. l In ECDSA based message authentication for VANET, the source vehicle creates a hash to the message using a hash function. And then the destination vehicle would receive the message for using the same hash function to calculate hash value. l If sender’s hash value is same as receiver’s, it means the massage has strong authentication. National Cheng Kung University CSIE Computer & Internet Architecture Lab 4

ECDSA l Entity X should use the key deployment procedure to establish a key pair. Entity Y should be able to obtain X’s public key. l When X wants to send a message M, it should sign the message using its key pairs and generate a signature S. l When Y receives the message, it applies the verifying operation using X’s public key in order to verify the message authenticity. National Cheng Kung University CSIE Computer & Internet Architecture Lab 5

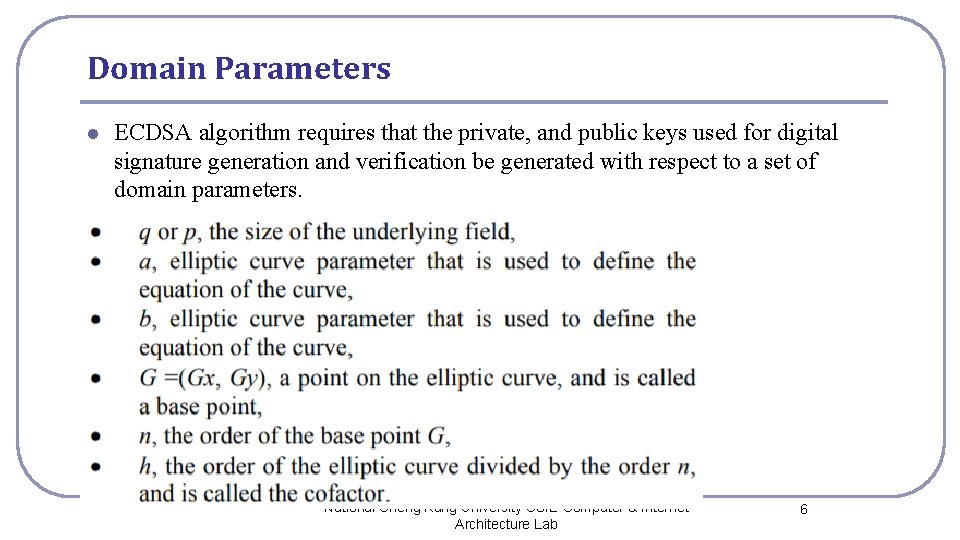
Domain Parameters l ECDSA algorithm requires that the private, and public keys used for digital signature generation and verification be generated with respect to a set of domain parameters. l l l National Cheng Kung University CSIE Computer & Internet Architecture Lab 6

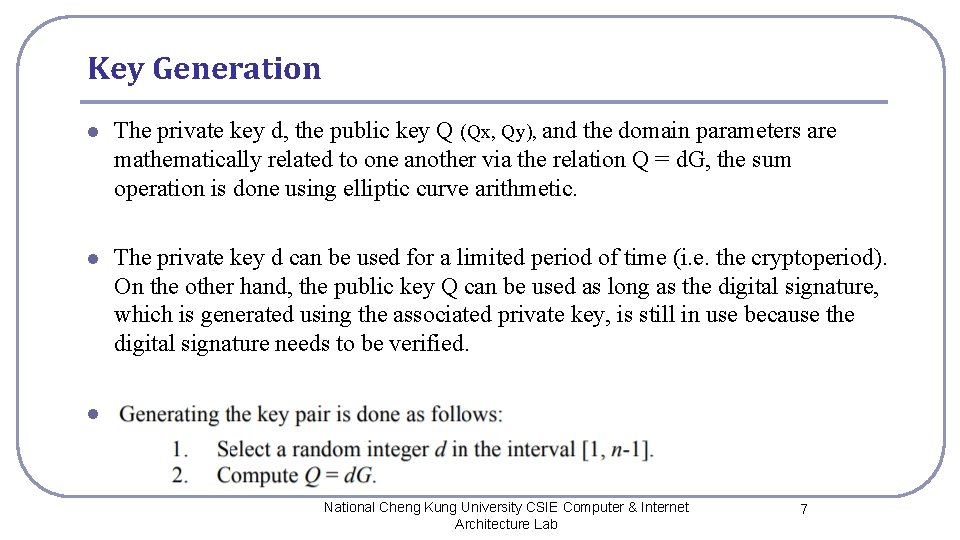
Key Generation l The private key d, the public key Q (Qx, Qy), and the domain parameters are mathematically related to one another via the relation Q = d. G, the sum operation is done using elliptic curve arithmetic. l The private key d can be used for a limited period of time (i. e. the cryptoperiod). On the other hand, the public key Q can be used as long as the digital signature, which is generated using the associated private key, is still in use because the digital signature needs to be verified. l National Cheng Kung University CSIE Computer & Internet Architecture Lab 7

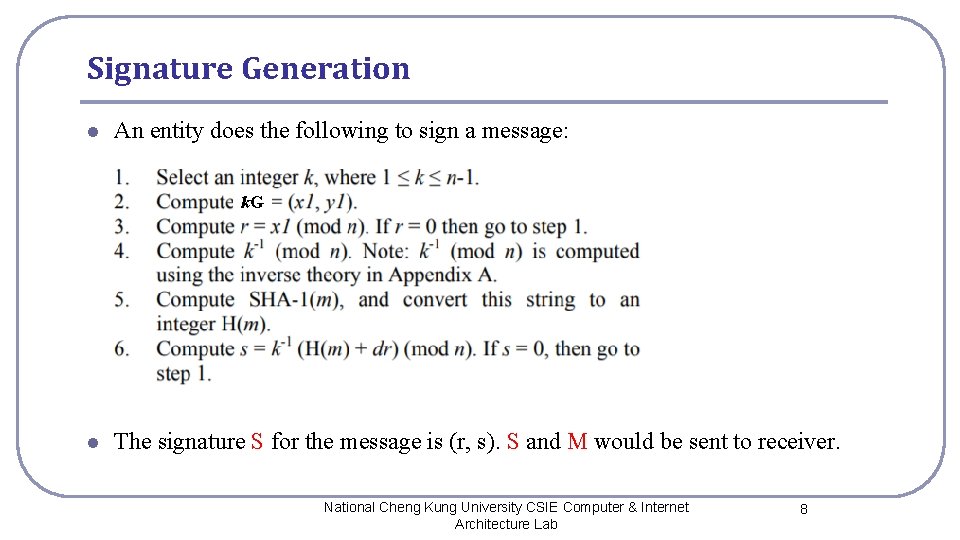
Signature Generation l An entity does the following to sign a message: k. G l The signature S for the message is (r, s). S and M would be sent to receiver. National Cheng Kung University CSIE Computer & Internet Architecture Lab 8

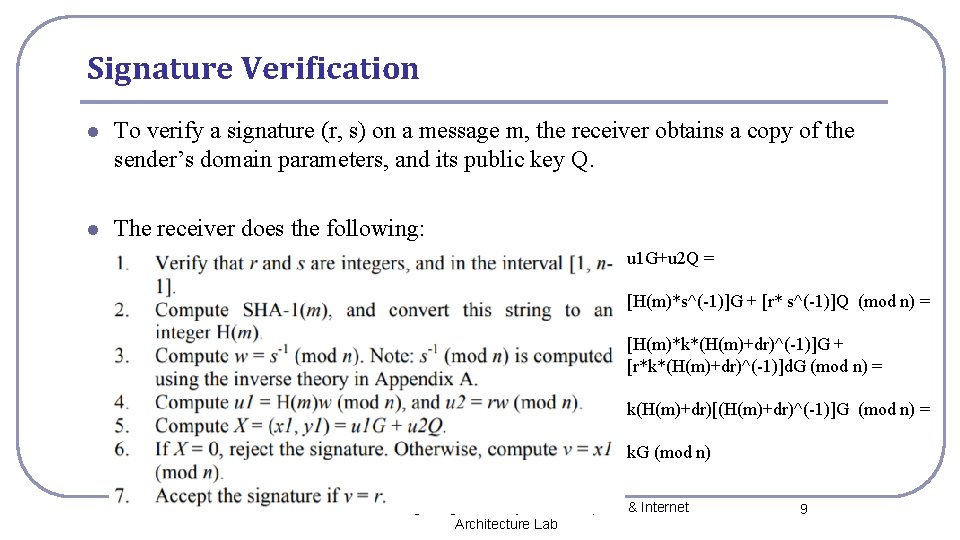
Signature Verification l To verify a signature (r, s) on a message m, the receiver obtains a copy of the sender’s domain parameters, and its public key Q. l The receiver does the following: u 1 G+u 2 Q = [H(m)*s^(-1)]G + [r* s^(-1)]Q (mod n) = [H(m)*k*(H(m)+dr)^(-1)]G + [r*k*(H(m)+dr)^(-1)]d. G (mod n) = k(H(m)+dr)[(H(m)+dr)^(-1)]G (mod n) = k. G (mod n) National Cheng Kung University CSIE Computer & Internet Architecture Lab 9

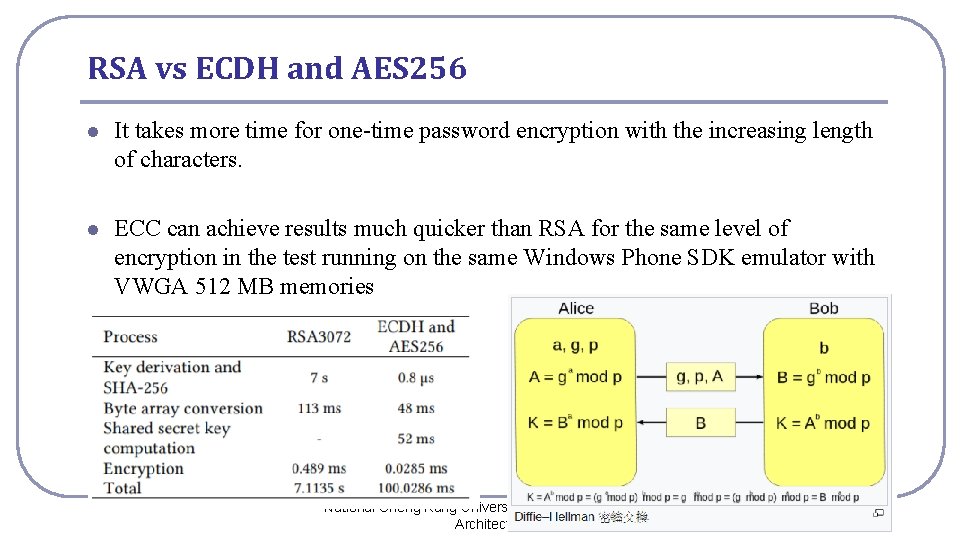
RSA vs ECDH and AES 256 l It takes more time for one-time password encryption with the increasing length of characters. l ECC can achieve results much quicker than RSA for the same level of encryption in the test running on the same Windows Phone SDK emulator with VWGA 512 MB memories National Cheng Kung University CSIE Computer & Internet Architecture Lab 10

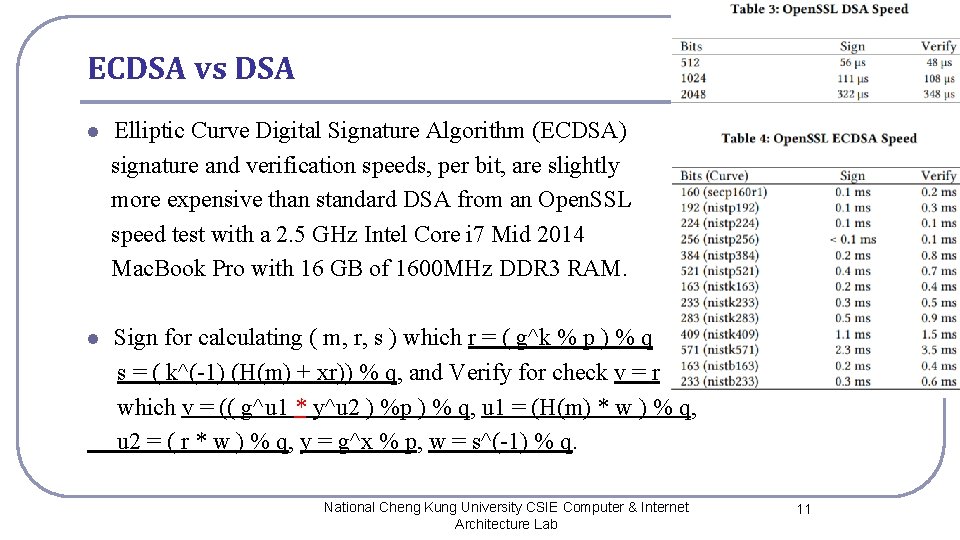
ECDSA vs DSA l Elliptic Curve Digital Signature Algorithm (ECDSA) signature and verification speeds, per bit, are slightly more expensive than standard DSA from an Open. SSL speed test with a 2. 5 GHz Intel Core i 7 Mid 2014 Mac. Book Pro with 16 GB of 1600 MHz DDR 3 RAM. l Sign for calculating ( m, r, s ) which r = ( g^k % p ) % q s = ( k^(-1) (H(m) + xr)) % q, and Verify for check v = r which v = (( g^u 1 * y^u 2 ) %p ) % q, u 1 = (H(m) * w ) % q, u 2 = ( r * w ) % q, y = g^x % p, w = s^(-1) % q. National Cheng Kung University CSIE Computer & Internet Architecture Lab 11

Traditional Applications l Key Exchange: The 69 websites of the top 100 most visited websites utilized some form of ECC for key exchange. l DNSSEC Validation: The domain name system (DNS), the system which translates web queries into IP addresses that the computer understands, can be protected by DNS Security Extensions (DNSSEC) implementing ECC, which is slower at validation but increases security by DNSSEC implementing RSA. l Signature Server: GPUs can be utilized to speed up ECDSA and create a functional universal signature server that is also capable of key agreement and encryption with ECC. They call their server GUESS (GPU-accelerated Universal Elliptic-curve Signature Server). National Cheng Kung University CSIE Computer & Internet Architecture Lab 12

Mobile Applications Authentication l The proposed protocol with ECC uses two-factor authentication was verified with the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool, which is suitable for practical application by making use of light-weight operations. l MANETs are eligible for attack through various means, such as worm hole, black hole, and rushing attacks. To prevent against unauthorized access, Enhanced Adaptive Acknowledgment (EAACK) with Elliptic Curve Algorithm. The protocol uses light weight ECC Digital Signatures to require all acknowledgment packets to be signed before they are sent and verified once accepted. National Cheng Kung University CSIE Computer & Internet Architecture Lab 13

Internet of Tings l Since many Io. T devices are open to security threats, one-time password (OTP) authentication scheme for Io. T devices using ECC is introducted for its lightweight avoiding some Io. T devices may not have enough computing power. l Algorithm for Io. T devices based on ECDH has the advantage of ECC’s smaller -key-size-for-equal-security and quick computations to reduce power consumption, which is superior to the other tested algorithms, like DH and RSA, in terms of power and area. National Cheng Kung University CSIE Computer & Internet Architecture Lab 14

Smart Grid l The smart grid aids electrical power transmission by including status information along with the power being transmitted. This greatly improves the efficiency of the grid. l To ensure the security of communication, anonymous key distribution (AKD) scheme using identity-based ECC provides smart meter anonymity and mutual authentication without needing a trusted party. The new scheme has greater performance than other AKD schemes. National Cheng Kung University CSIE Computer & Internet Architecture Lab 15

Vehicular Communication l Large key size has made secure communication difficult to implement. By using ECC the team was able to develop a method that is able to use smaller key sizes which could grant equal or greater security vehicle communication. l Man-in-the-middle attacks and brute force attacks are not possible in polynomial time due to the elliptic curve discrete logarithm problem, making the system a secure method of communication which can save lives. National Cheng Kung University CSIE Computer & Internet Architecture Lab 16

RFID l Radio Frequency Identification (RFID) is a technology used for automatic identification via radio waves and is used in a large variety of applications. l M. Benssalah et al. used an FPGA to validate RFID messages for authentication using ECC. This time, the ECC implementation is used for actual encryption by means of ECC-El. Gamal. Specifically, the team showed the effectiveness of the implementation with car key systems. National Cheng Kung University CSIE Computer & Internet Architecture Lab 17

Iris Pattern Recognition l For iris pattern recognition, S. V. Vishnubhatla developed a hashing algorithm based off of ECC. l The hashing was done on grayscale images using Python with the Open. CV library. After results were collected, analysis showed that the elliptic curve hashing algorithm outperformed the standard MD 5 and SHA-1 hashing algorithms and is accurate at a rate of 99. 5%. National Cheng Kung University CSIE Computer & Internet Architecture Lab 18

E-Health Applications l G. Sahebi et al. have designed a framework utilizing ECC for its fast speed, smaller keys, and greater security for E-health applications such as sensors and wearables. l Secure and Efficient Elliptic Curve Cryptosystem (SEECC) is their proposition developed to select secure, efficient curves from all available curves. By choosing these safer curves, security is enhanced. l The method also increases the efficiency of ECC by means of a parallel genetic algorithm. National Cheng Kung University CSIE Computer & Internet Architecture Lab 19
 Sha1
Sha1 Sha1
Sha1 Hash 111
Hash 111 Rsa
Rsa Callmanager-ecdsa
Callmanager-ecdsa Law of conservation of momentum
Law of conservation of momentum Extricacion 1
Extricacion 1 Vehicular cloud
Vehicular cloud Fspos vägledning för kontinuitetshantering
Fspos vägledning för kontinuitetshantering Typiska drag för en novell
Typiska drag för en novell Tack för att ni lyssnade bild
Tack för att ni lyssnade bild Returpilarna
Returpilarna Varför kallas perioden 1918-1939 för mellankrigstiden
Varför kallas perioden 1918-1939 för mellankrigstiden En lathund för arbete med kontinuitetshantering
En lathund för arbete med kontinuitetshantering Särskild löneskatt för pensionskostnader
Särskild löneskatt för pensionskostnader Tidbok yrkesförare
Tidbok yrkesförare Anatomi organ reproduksi
Anatomi organ reproduksi Förklara densitet för barn
Förklara densitet för barn Datorkunskap för nybörjare
Datorkunskap för nybörjare Stig kerman
Stig kerman