Identity Theft Information is Power Copyright 2019 Curt










- Slides: 12

Identity Theft Information is Power Copyright © 2019 Curt Hill

Introduction • Identity theft is using stolen credentials to make money • What is the goal? • Two possibilities: – Using your credentials to steal your finances – Using your credentials to steal from your organization Copyright © 2019 Curt Hill

Credit Card Theft • Obtain the physical card or intercept its usage to capture the card number • As simple as a waiter copying the number and using later • As complicated as intercepting credit card information in a business computer system or over internet Copyright © 2019 Curt Hill

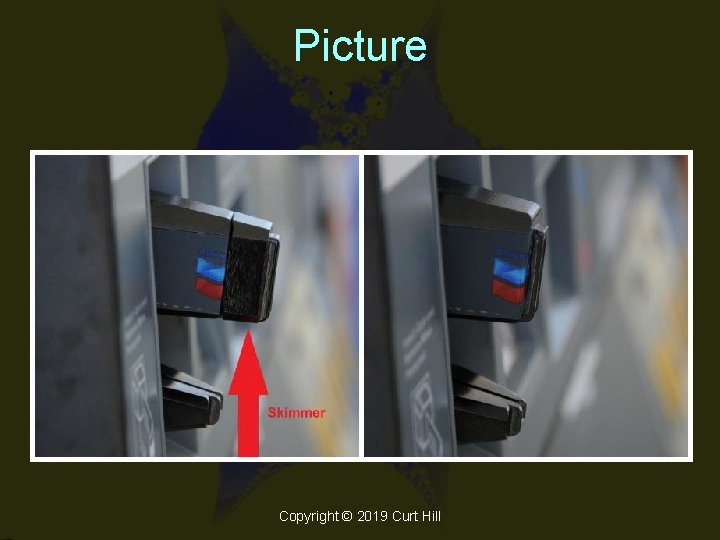
Skimmers • A device that scans the card as it is inserted to a card reader – Often a gas pump or other unattended card reader • The data is sent twice – To the scammer and the owner of the device to which it is attached Copyright © 2019 Curt Hill

Picture Copyright © 2019 Curt Hill

Interception • The goal here is to obtain a credit card or other credential in transit • Two approaches – Infiltrate a business system with whom you do business – Gain access to a router that passes a packet with your information Copyright © 2019 Curt Hill

Phishing • A social engineering technique where a user gives scammer a credential under a false assumption • Typically using email from a spoofed account – One that is supposed to be trustworthy • It typically asks the victim to reply with some information or go to a bogus website • 90% of corporate breaches start with a phishing attack Copyright © 2019 Curt Hill

Spear Phishing • Phishing relies on mass mailings – Few respond but those that do create profit • Spear Phishing targets a particular individual – Requires some knowledge of the organizational environment – Usually involves several exchanges between mark and scammer – Often the result of previous phishing success Copyright © 2019 Curt Hill

More is better? • Regardless of technique, the more information the attacker gets the more damage they can perpetrate • The Social Security Number is the gold standard of Identity Theft • This will generally allow the attacker to open accounts in the victim’s name • Victim is saddled with paying for the attack in a variety of ways – False purchases and cleanup of damage Copyright © 2019 Curt Hill

Protection • Unlike the investment scams the victim is not motivated by greed • They are usually just doing what they think they should • They are always ignorant that something is not right • Thus education to dispel this ignorance is the solution Copyright © 2019 Curt Hill

Actions • Do not provide personal information – Shred documents with personal information – No legitimate organization will ask for most of these • Keep the OS, antivirus and antimalware programs updated • Check credit card bills for invalid entries Copyright © 2019 Curt Hill

Summary • The goal of identity theft is get information from the victim that can be monetized • This could be: – Credit/Debit card numbers – Driver’s license – SSN – Among others • Winning this conflict requires people who know too much to become a victim Copyright © 2019 Curt Hill