Identity Theft 101 Road Map n What identity
























- Slides: 27

Identity Theft “ 101”

Road Map n What identity theft is n Credit and how it is affected n Road to recovery n The law n A few tools and tricks of the trade

What is identity theft? n n Identity theft or identity fraud (true name fraud) is the taking of the victim’s identity to obtain credit, steal money from accounts, rent an apartment, file bankruptcy, obtain a job, or commit a crime using a victim’s name There are countless numbers of ways to have your information stolen and used against you

Identity theft is the fastest growing crime in the united states n n statistics now show that one in four U. S. households has been a victim of identity theft in the past five years The time, money, and resources lost to businesses and individuals on the account of identity theft produces stagering statistics

A Summary of the Identity Theft Statistics in 2003: n Average loss to businesses per victim: $4, 800 n Loss to businesses: $47. 6 billion n Average out-of-pocket loss for victims: $500 n n n Number of victims: 9. 9 million Total loss to victims: $5 billion Hours spent per victim resolving the problem: 30 n Hours spent resolving problem: 297 million (Source: Federal Trade Commission identity theft survey report www. FTC. gov)

Credit • What is it? • How it is affected?

Credit Today, there are three major credit bureaus -Trans. Union -Experian -Equifax. n

n n These bureaus collect and report consumer credit information. Lenders, landlords, insurers, utility companies, and other credit grantors use the information provided to make fast and fair financial and credit decisions.

n n Our financial and economic standing, or credit score, plays a huge role in our modern economic structure Unfortunately, this world of electronic transactions and print outs is not secure, and anyone with malicious intent whom acquires the right information can easily exploit your financial and credit standings.

How Your Credit Is Affected n n The thief may be able to add lines of credit, bounce checks, drain accounts, and run up credit cards These blemishes will then be recorded by the three major credit bureaus onto YOUR financial report u Review of your credit report is an essential tool to help keep your identity secure

Identity Theft and The Law n Federal law n State law n The uphill battle

Federal Regulations n n A wide range of federal laws relate to identity theft. These laws can be grouped into four main categories: u Identity theft specific laws u false identification laws u privacy and personal data laws u credit law

Federal Enforcement n n n The Federal Bureau of Investigation The United States Secret Service The United States Postal Inspection service

State Law n State laws expand upon federal laws all the way down through misdemeanors. Each state is responsible for setting its own laws and penalties

Pennsy lvania 18 Pa. C. S. A. § 4120 Identity theft If the total value involved is less than $2, 000, the offense is a misdemeanor of the first degree. If the total value involved is $2, 000 or more, the offense is a felony of the third degree. Regardless of the total value involved, if the offense is committed in furtherance of a criminal conspiracy, as defined in section 903, the offense is a felony of the third degree. Regardless of the total value involved, if the offense is a third or subsequent offense, the offense is a felony of the second degree

n Often times if you did not suffer the greatest financial loss, the judicial discretion to pursue a case is left up to the corporation, business, or the biggest loser involved. n On the bright side though, there many laws, lawyers, and agencies dedicated to helping identity theft victims

The Road to Recovery How to get started

How To Stop The Fraud n n First knowledge of fraud u A creditor will contact you u Mysterious credit denial u Fraudulent transactions Contact the bureaus u This will not stop the fraud immediately, but it gets you started

Ways To Combat the Fraud n n As stated earlier, many people aid in the battle against identity theft Law firms and companies compile detailed packets of information walking you step-bystep through the process to fix your financial identity

Social Enginering n The backbone of identity theft

n n n Social Engineering is the practice of obtaining confidential information by manipulation. A Social Engineer will commonly use the telephone or Internet to trick people into revealing sensitive information or getting them to do something that is against typical policies. Social Engineering techniques are based on flaws in human logic

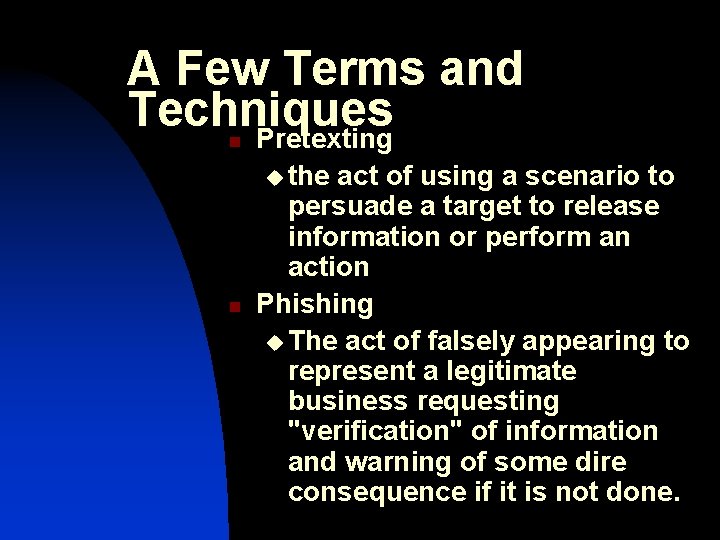
A Few Terms and Techniques Pretexting n u the n act of using a scenario to persuade a target to release information or perform an action Phishing u The act of falsely appearing to represent a legitimate business requesting "verification" of information and warning of some dire consequence if it is not done.

n n Gimmes u take advantage of curiosity or greed to deliver malware u Also known as Trojan Horses Road Apple u A Trojan Horse on a cd-rom or flash drive left in a place that is sure to be found u It may have a legitimate looking label that sparks curiosity, such as "Executive Salary Summary Q 1 2007"

Common Situations in which your identity may be stolen n n n Dug out of trash cans and dumpsters Memorized or copied by sales clerks Removed from your u mailbox u employer's files u hospital records u financial lender's files u landlord's files Purchased or found in online or offline databases Collected from "cloned" Web sites Stolen from a merchant database through hacking u Restaurants ranked highest in most likely places to have your identity stolen. The lack of security on their systems makes an easy target for Hackers Basically, anywhere that you have provided information can be a target.

n skimmers can be put on credit card or ATM machines that will record credit card information for later use. These devices also come in handy, portable, key chain sized models These devices are equipped to store the information of thousands of magnetic strips, and also have panic buttons to completely erase and overwrite their memory

n A great number of high and low tech devices are readily available online to assist in the exploitation of others.

In Conclusion Identity theft is on the rise, and the best way to avoid having your information compromised it is to be prepared.