Identity theft 1 Outline Identity theft Relevant theory

















- Slides: 20

網路心理與行為 Identity theft 1

Outline Identity theft Relevant theory Study 1 Study 2 2

Identity theft (身份竊用) Identity a multi-faceted concept that is best understood by a division into three categories: personal, social and legal. Personal identity: a sense of continuity an ability to know that we are different now than we were then and that life processes. 3

Social identity: identity viewed by others in society, or how others see us. Legal identity: the way that pieces of information can distinguish one person from another 4

Identity theft, the legal aspect is the most important factor of an individual's identity Identity theft: the misuse of an individual's personal information (mainly legal identity such as date of birth, name, address) to commit fraud The Internet plays a major role in distributing information about identity theft. 5

Identity Theft introduction https: //www. youtube. com/watch? v=lp_8 cv. Nm_v. E 6

Relevant theory Victims of online identity theft Mendelsohn's research(1963): certain individuals who suffered damage and loss due to a crime might share some degree of responsibility with the offenders. Victims had an unconscious aptitude for being victimized. 7

Information Online Availability of identifiable information online The Internet provides numerous opportunities for identity theft to occur. Most majority of social networking websites share common or core features such as a main profile, social networks, mail and comments. 8

Vulnerabilities 弱點 Users also provide considerable amounts of information when shopping online. Online shoppers are vulnerable to identify theft for 3 reasons 1. the data on any computer can be compromised 2. the data transfer to an online business can be compromised 3. the data stored by businesses may be compromised 9

Anxiety online Anxiety is a psychological and physiological state that is characterized by cognitive, emotional, behavioral and somatic components. These components combine to create unpleasant feelings such as uneasiness, fear or worry. Individuals who are most worried anxious about crime take more precautions to make themselves feel less at risk and safer. Users tend to engage in bad password-management behaviors because of the convenience-security tradeoff. 10

Study 1 H 1: the victims of online identity theft experiences higher levels of anxiety than non-victims when shopping/banking online. H 2: the victims of online identity theft take stronger precautions/measures when shopping/banking online. H 3: there is a difference between the amount of information provided by victims and non-victims online. 11

Study 1 focus on two groups of individuals - online identity theft victims and non-victims - and the anxiety that both groups experience online. A content analysis of profiles on the social networking website "Facebook" was conducted Participants 60 participants (30 males and 30 females) took part in Study 1. 12

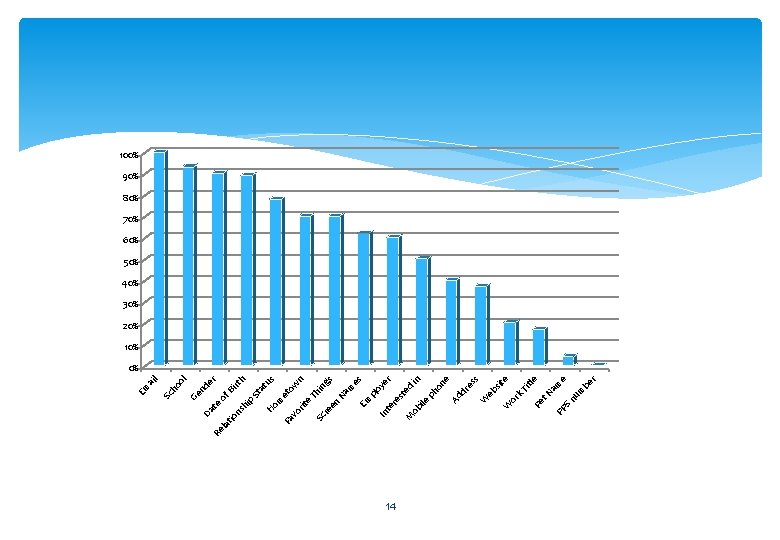
Procedures A list of sixteen codes for the content analysis of the Facebook profiles was devised. The coding scheme was developed from creating a new Facebook profile and determine the information that was required and the information that was optional. The codes used were: gender, hometown, date of birth, social security number, email address, mobile/home phone number, address, website, relationship status, school, employer, work title, screen name, favorite things, pet name, former address. 13

14 S PP e itl be r nu m am e t. N Pe s sit e k. T or W r in dr es eb W d ye on e ph Ad ile ob M te re s pl o es Na m n Th in gs Em en te re In Sc at us et ow m rit e vo Fa Ho h er Bi rt nd ol ho St of p hi ns tio la Re te Da Ge Sc ail Em 100% 90% 80% 70% 60% 50% 40% 30% 20% 10% 0%

Study 2 Purpose: an online survey to gauge participants’ knowledge of online identity theft and the difference in precautions and anxiety levels of victims and non-victims. Participants 85 participants completed study 2. All were over 18 and were required to currently shop or bank online. Materials Beck’s Anxiety Inventory (貝克焦慮量表) 15

Knowledge and experience of identity theft 1. The majority (88%) of participants reported that they understood what the term “identity theft” meant, and 12% revealed that they somewhat understood the term “identity theft”. 2. Participants who had previously experienced one or more incidents of identity theft had higher anxiety scores than those participants who had never experienced any form of identity theft (t=4. 9, df=83, p<0. 001) 16

Internet usage and victimization 1. 68 participants (87 %) indicated that they shopped online using credit cards, and 40 participants (51%) shopped online using debit cards. 52 (43. 6%) provided information on social networking websites. 2. A chi-square test of independence revealed that participants who had experienced personal identity information theft, were less likely to use credit cards to shop. 17

Precautions and measures online 1. 71 percent reported that they had not ordered a copy of their credit report in the last year. 2. 43% had used personal information such as mother’s maiden name or date of birth when creating online passwords. Victims were less likely to use this personal information when creating passwords than non-victims were. 18

Discussions There was a significant difference between victim’s and non-victims’ level of anxiety when shopping and banking online. There was no significant difference found in victim’s and non-victim’s precautions when shopping and banking online. However, there was a significant difference between victims’ and non-victims’ usage of personal information when creating online passwords. There was no significant difference in the amount of information that victims and non-victims provided on social networking Websites. 19
