HIPAA and the Non Clinical employee Iowa State





































- Slides: 38

HIPAA and the Non. Clinical employee Iowa State Association of Counties June 27, 2017

Sorry, I have to do this! � The contents of this presentation are provided for the purpose of information and education only and do not constitute legal advice. You are encouraged to consult competent legal counsel of your choice for all legal issues.

“ I work in the auditors office, I never see PHI” � Auditor’s office – supporting documentation for accounts payable � Shared office space with a department that does access PHI � Shared copiers/printers � Common unsecured mailboxes in the courthouse breakroom � Misdirected interoffice mail

� Janitorial staff � Paper PHI in transit � Misdirected faxes � Shared storage facilities � Phishing e-mails � The reality is, PHI could float through just about every department

�A county may be a designated hybrid entity… • One big happy family • Actions of one can impact everyone • Rural counties probably have the most exposure

Why should counties even care about HIPAA? � Presence Health • Missing operating room schedules • 836 individuals impacted • Failed to notify those individuals within 60 days as required by HIPAA • $475, 000 fine

� MAPFRE • Failed to safeguard portable devices and poor risk assessment/risk management • Inadequate security awareness training • Stolen unsecured flash drive – 2, 209 individuals impacted • Did not start securing portable devices until 3 years later • $2. 2 million fine

� Children’s Medical Center of Dallas • 2011 stolen blackberry – 3, 800 people impacted • 2013 stolen laptop – 2, 463 people impacted • Aware of the risks in 2011 but didn’t secure and safeguard workstations and portable devices until 2013 • $3. 2 million fine

� Memorial Healthcare System • 115, 413 people impacted • Failed to terminate former employee’s access credentials for over a year • Company failed to review activity within the system, or conduct risk assessment • $5. 5 million settlement

Privacy matters!

Who should receive HIPAA training? � The easier question is who shouldn’t receive HIPAA training! � Those employees who have absolutely no possibility of coming into contact with protected health information � Secondary roads, conservation, economic development, etc. BUT only if the have separate offices

Training must be relevant � Essential to connect with non-clinical staff on why HIPAA is important to them � Identity theft is a HUGE issue for all of us � Invasion of privacy � The cost of fines and settlements is skyrocketing

� Quinzella Romer – former health insurance company employee � During a traffic stop, officers discovered an outstanding warrant � During pat down found a driver’s license from another person and a cell phone � Obtained a search warrant for the phone

� Found over 20 screen shots on the phone that contained PHI of over 50 people. � 12 had already been victims of taxrelated identity theft where the IRS paid out refunds � Sentenced to 32 months in prison and restitution of $16, 264

Catholic Health Care Services � Employee’s i. Phone was stolen � Contained PHI of 412 people � i. Phone was not encrypted or even password protected � CHCS had no policies or procedures addressing mobile devices or what to do in a security incident � Settlement payment of $650, 000

What do they need to know? � What is PHI � How to handle PHI � Minimum Necessary Doctrine � Danger of phishing attacks and ransomware � Importance of not sharing any information with those who do not need to know it

What is PHI � Protected Health Information (PHI) is individually identifiable health information that is: Created or received by a health care provider, health plan, employer, or health care clearinghouse that � Relates to the past, present, or future physical or mental health or condition of an individual; � Relates to the provision of health care to an individual � The past, present or future payment for the provision of health care to an individual.

� PHI is so much more than just the medical record. � PHI includes information by which the identity of a person can be determined with reasonable accuracy and speed either directly or by reference to other publicly available information.

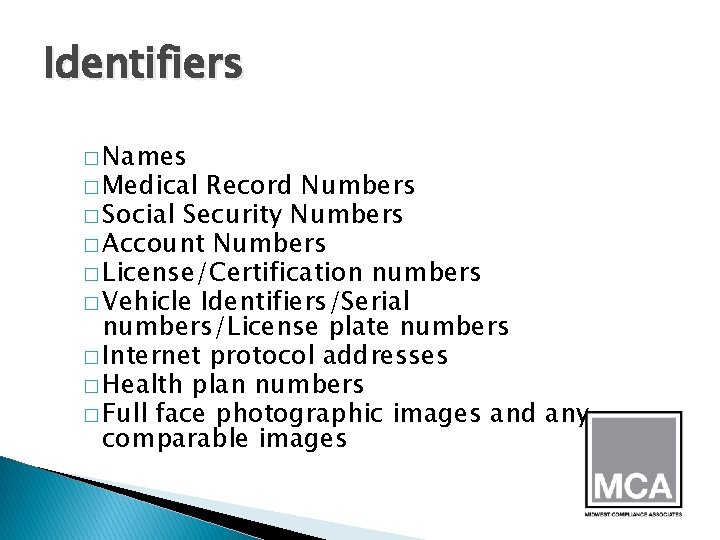
Identifiers � Names � Medical Record Numbers � Social Security Numbers � Account Numbers � License/Certification numbers � Vehicle Identifiers/Serial numbers/License plate numbers � Internet protocol addresses � Health plan numbers � Full face photographic images and any comparable images

� Web universal resource locaters (URLs) � Any dates related to any individual (date of birth) � Telephone numbers � Fax numbers � Email addresses � Biometric identifiers including finger and voice prints � Any other unique identifying number, characteristic or code � PHI is more than name, date of birth and SSN!

How to handle PHI � First and foremost, protect it! � Ensure it remains private � Ensure it is secure when in electronic format – encryption, firewalls, etc. � Access must be authorized � Do not discuss PHI in public areas such as cafeterias, breakrooms, etc. � Dispose of it properly

Cornell Prescription Pharmacy � Small single location pharmacy � OCR received notification from local TV station that unsecured paper medical records were disposed in an unlocked open container on the premises � No policies or procedures for destruction of documents � Paid $125, 000 settlement

Minimum Necessary Standard � The Minimum Necessary Doctrine seems to trip up a lot of organizations both in terms of over disclosing and in “handcuffing” � Use or disclose/release only the minimum necessary to accomplish intended purposes of the use, disclosure, or request.

� The Minimum Necessary Standard applies to business practices and all members of the workforce � The Office for Civil Rights considers the standard to be a key protection under HIPAA � “If I promise to tell you a secret do you promise not to tell? ”

Dangers of Phishing and Ransomware � Phishing is a particularly dangerous form of spam that seeks to trick users into revealing sensitive information, such as passwords � Over 75% of breaches are because someone let the bad guys in � The best protection is to always be skeptical about e-mails – “when in doubt, throw it out!”

Why is Phishing so dangerous? � E-mails appear to come from a legitimate company and can look very official � Easy to be fooled into providing personal information in hopes of rectifying some nonexistent problem with your account � Sense of urgency created tricks people into acting without thinking

Examples � “There has been a security breach and your immediate attention is required. If you don’t update and confirm your password within 48 hours all data will be lost. ” � Provides a link to access the log-in page which actually takes the person directly to the bad guys

Red Flags �A financial institution will NEVER ask you to reset your account information online � The e-mail claims there will be dire consequences unless you log in immediately � There is a link within the e-mail that takes you to the “log-in” page � Fear is attacker’s best weapon

� The best way to train employees on the dangers of Phishing attempts is to show them what “bad” e-mails tend to look like � All it takes is for one employee to take the bait � Spear Phishing – highly personalized emails that go to a person higher up in the organization = more damage

� Ransomware – a type of malicious software that blocks access to the victim’s data or threatens to publish or delete until a ransom is paid � May 12, 2017 the Wanna. Cry virus and infected 200, 000 in the first few hours

� In most cases the malware makes it seem like the message is from the government or official organization � The virus can install embarrassing pornography on the screen and demands a ransom to remove the image

� The risks from ransomware, both in terms of data loss and reputation damage are potentially huge � Key is to stay away from risky web sites, recognize Phishing attacks and never give out log in credentials

Know when not to share PHI � If someone doesn’t need to know PHI to do their job, NEVER share PHI, regardless of how “juicy” it may be � Confirm there is a proper authorization in place BEFORE sharing PHI � Just working for the county does not constitute an “all access pass” to all county information

Do’s and Don’ts � Do keep computer sign-on codes and passwords secret and use locked screensavers � Do Not allow unauthorized persons to access your computer � Do keep notes, files, USB drives and mobile devices in a secure place and not out in the open

� Do Not place PHI on a mobile device that isn’t encrypted and password protected � Do hold discussions of PHI in private areas and for job-related purposes only � Do be aware of other people listening in on your conversation

� Do make sure all envelops used to mail or transport PHI are sealed and closed securely � Do follow proper procedures for proper disposal of sensitive information i. e. secure shredding � Do Not include PHI in e-mails unless the e-mail is encrypted

Bottom Line � Nearly every county employee, even non-clinical employees should have annual HIPAA based training � The bad guys are continually coming up with new ways to access sensitive information � The cost of enforcement is greater than ever

Questions? Gary N. Jones J. D. CHC, CHPC gary. jones@mwcompliance. com Midwest Compliance Associates, LLC 721 W. 1 st Street Cedar Falls, Iowa 50613
 Employee attitudes and employee performance
Employee attitudes and employee performance Bufkit weather
Bufkit weather Iowa state sona
Iowa state sona Iowa state tree
Iowa state tree Iowa state intramurals
Iowa state intramurals Iowa state snowmobile association
Iowa state snowmobile association Isu mesonet
Isu mesonet Iowa state geology
Iowa state geology Student success center iowa state
Student success center iowa state Alissa stoehr iowa state
Alissa stoehr iowa state Iowa state university intramurals
Iowa state university intramurals Iowa state pearson books
Iowa state pearson books Isu accounts receivable
Isu accounts receivable Koak weather
Koak weather Iowa state patrol districts
Iowa state patrol districts Ee 201
Ee 201 Cpre 288 iowa state
Cpre 288 iowa state Iowa state vet school supplemental application
Iowa state vet school supplemental application Isu dining schedule source
Isu dining schedule source Iowa state math department
Iowa state math department Ubill iowa state
Ubill iowa state Iem mesonet
Iem mesonet Iowa staewide assessment of student progress
Iowa staewide assessment of student progress R. ganesh rajagopalan
R. ganesh rajagopalan Iowa state association of counties
Iowa state association of counties Blackboard qu
Blackboard qu Iowa state outlook
Iowa state outlook Texas state afrotc
Texas state afrotc Debout jeunesse lève toi
Debout jeunesse lève toi Indiana state employee benefits
Indiana state employee benefits Colorado state university employee benefits
Colorado state university employee benefits Employee assistance program washington
Employee assistance program washington Arotc oregonstate
Arotc oregonstate Geisingerconnect
Geisingerconnect Cvs privacy awareness training answers
Cvs privacy awareness training answers Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Jcaho standards
Jcaho standards Penn state clinical psychology
Penn state clinical psychology Hipaa training georgia
Hipaa training georgia