Herding Cats and Security Tools Harold Toomey Product












- Slides: 29

Herding Cats and Security Tools Harold Toomey Product and Application Security Mc. Afee LLC 10 Nov 2017 NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5

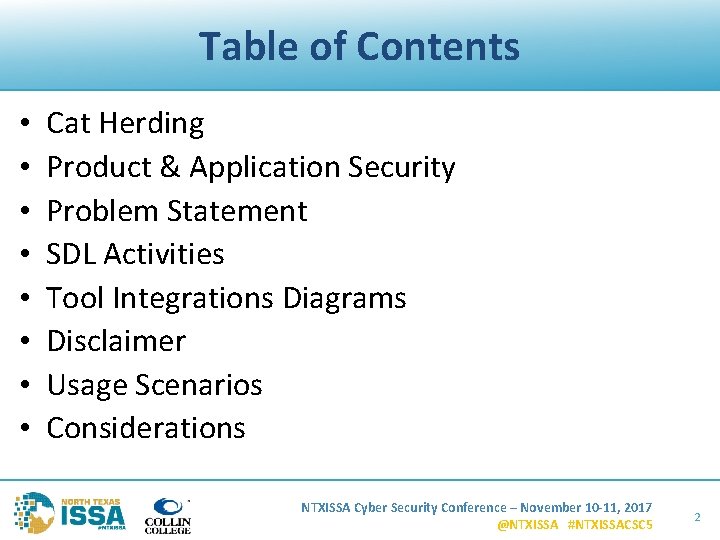
Table of Contents • • Cat Herding Product & Application Security Problem Statement SDL Activities Tool Integrations Diagrams Disclaimer Usage Scenarios Considerations NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 2

Cat Herding NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 3

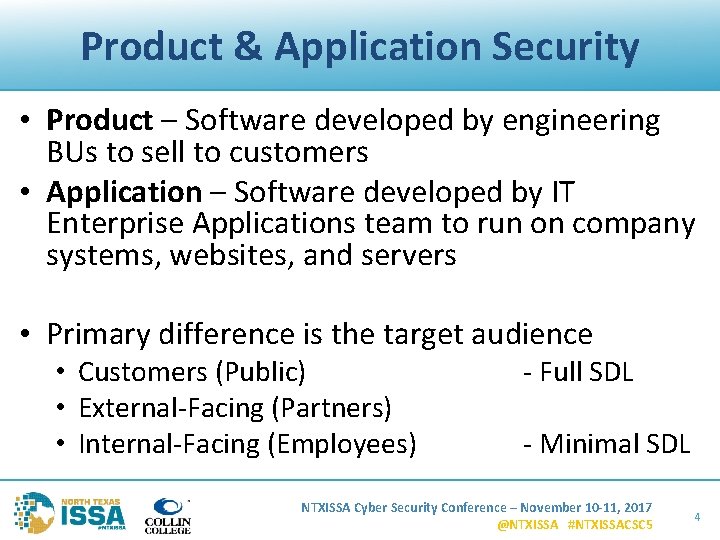
Product & Application Security • Product – Software developed by engineering BUs to sell to customers • Application – Software developed by IT Enterprise Applications team to run on company systems, websites, and servers • Primary difference is the target audience • Customers (Public) • External-Facing (Partners) • Internal-Facing (Employees) - Full SDL - Minimal SDL NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 4

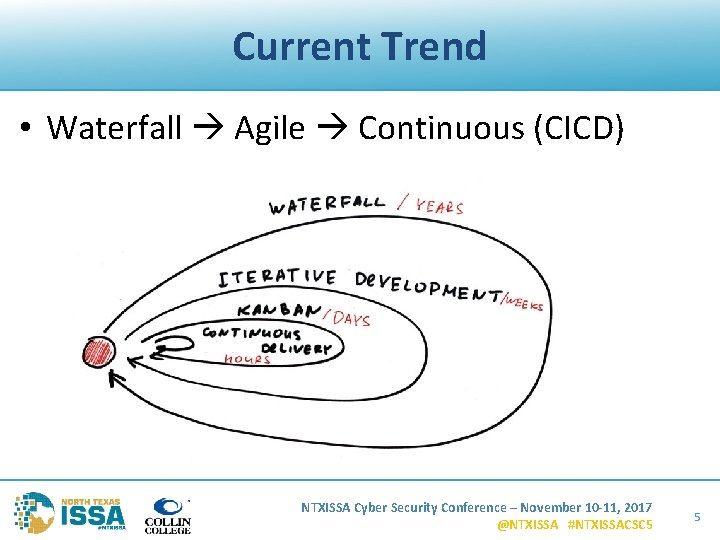
Current Trend • Waterfall Agile Continuous (CICD) NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 5

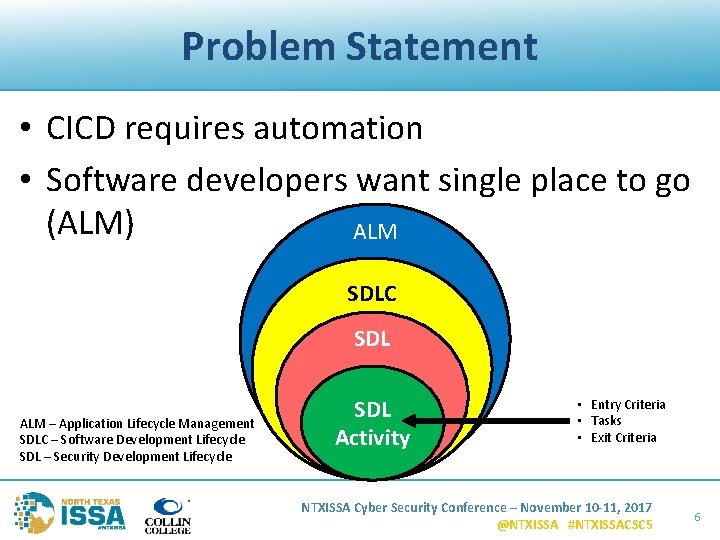
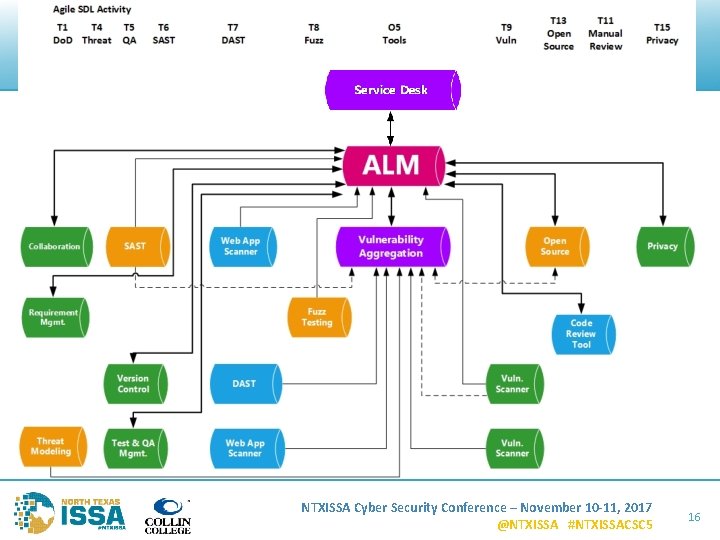
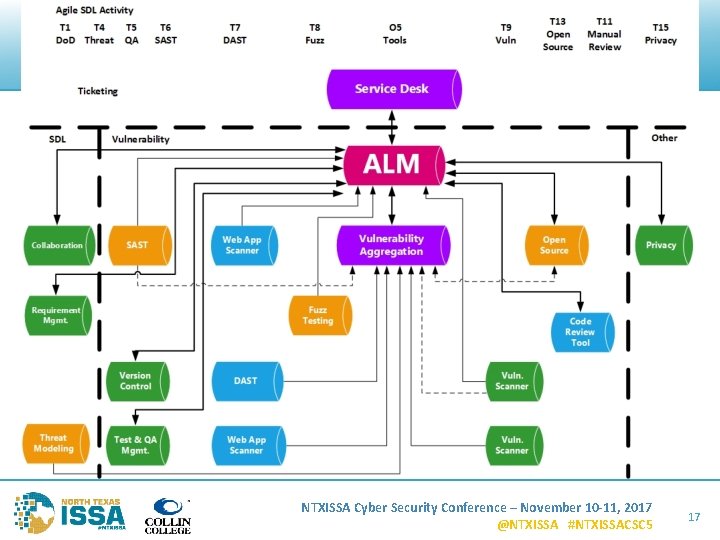
Problem Statement • CICD requires automation • Software developers want single place to go (ALM) ALM SDLC SDL ALM – Application Lifecycle Management SDLC – Software Development Lifecycle SDL – Security Development Lifecycle SDL Activity • Entry Criteria • Tasks • Exit Criteria NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 6

SDL – Operational Activities 1. 2. 3. 4. 5. 6. 7. 8. 9. Program SDL PSIRT People & Resources Tools & Services Policy, Compliance, & Certifications Training Metrics Maturity Models NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 7

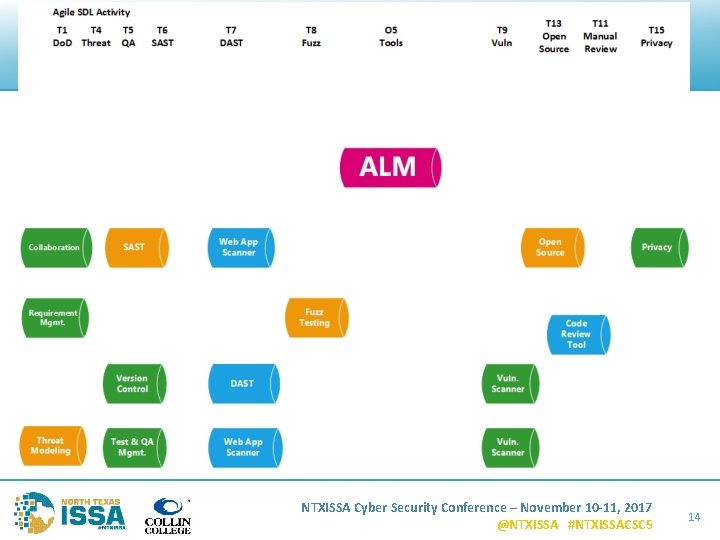
SDL – Technical Activities 1. Security Definition of Done (Do. D) 2. Security Architecture Review 3. Security Design Review 4. Threat Modeling 5. Security Testing & Validation 6. Static Analysis (SAST) • Interactive Analysis (IAST) 7. Dynamic Analysis (DAST) 8. 9. 10. 11. 12. 13. Fuzz Testing Vulnerability Scan Penetration Testing Manual Code Review Secure Coding Standards Open Source & 3 rd Party Libraries 14. Vendor Management 15. Privacy 16. Operating Environment NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 8

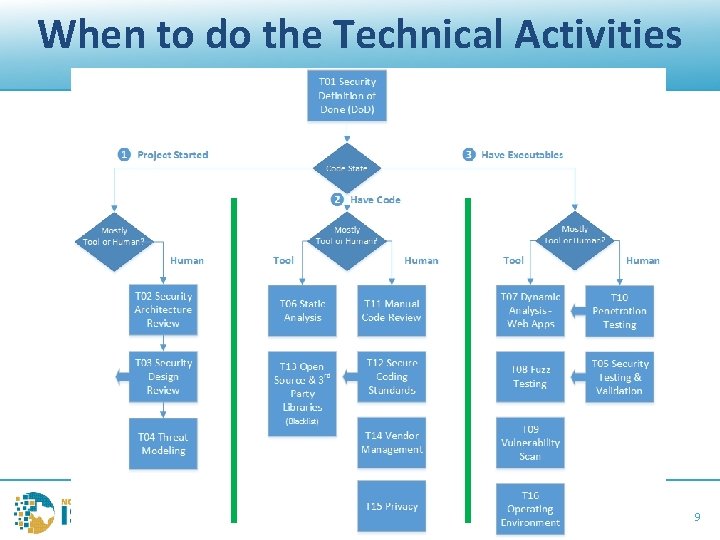
When to do the Technical Activities NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 9

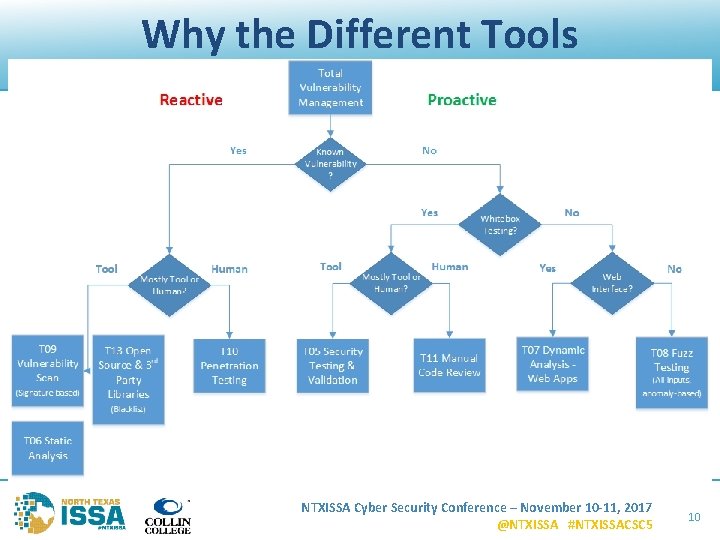
Why the Different Tools NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 10

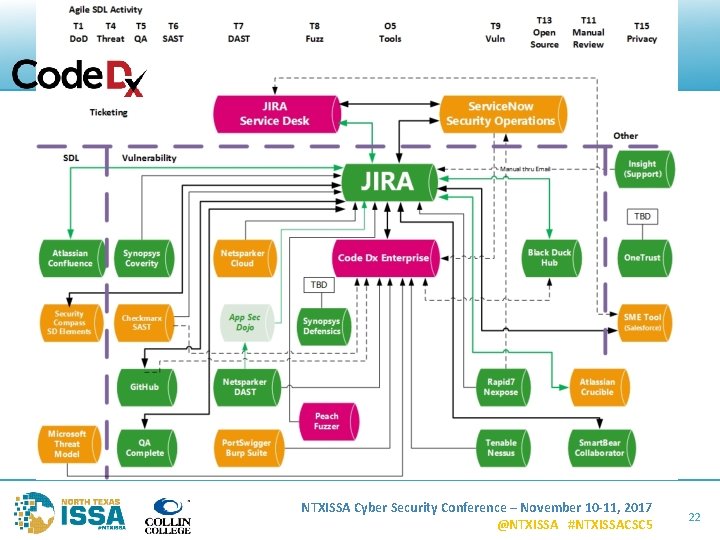
Tools Integration – Generic Flow Diagram Example NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 11

Herding Cats (Tools) NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 12

NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 13

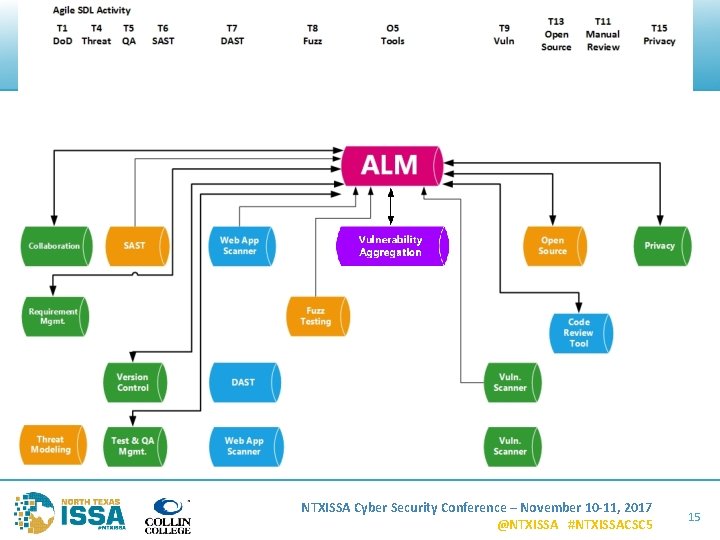
NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 14

NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 15

NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 16

Solution NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 17

Disclaimer • Mention of vendor names and tools does not imply endorsement • Vendor list is intentionally incomplete • Based on my limited research • Best integration for me may not be best for you NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 18

ALMs NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 19

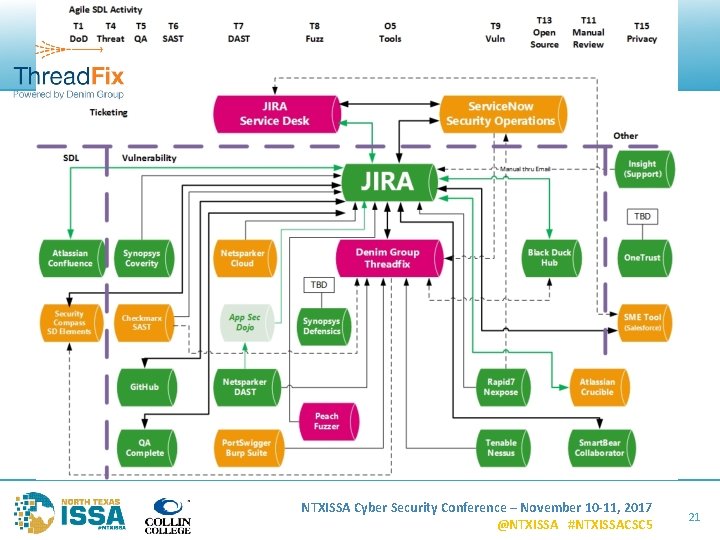
Tools Integration – Real Tools Flow Diagram Examples NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 20

NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 21

NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 22

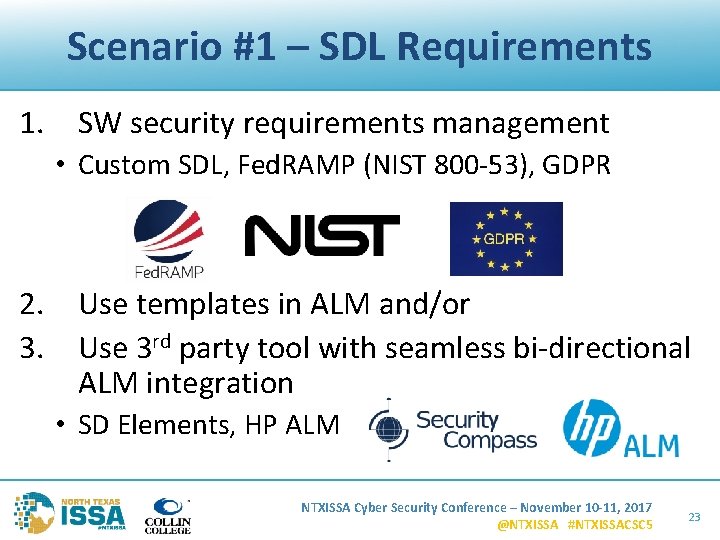
Scenario #1 – SDL Requirements 1. SW security requirements management • Custom SDL, Fed. RAMP (NIST 800 -53), GDPR 2. Use templates in ALM and/or 3. Use 3 rd party tool with seamless bi-directional ALM integration • SD Elements, HP ALM NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 23

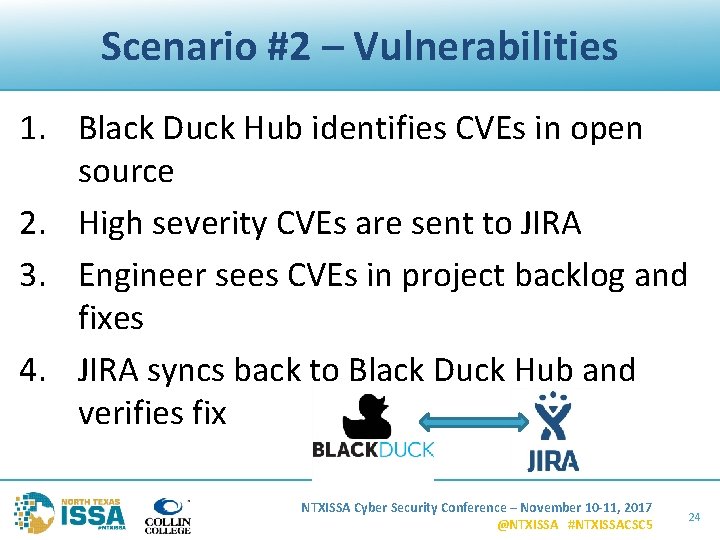
Scenario #2 – Vulnerabilities 1. Black Duck Hub identifies CVEs in open source 2. High severity CVEs are sent to JIRA 3. Engineer sees CVEs in project backlog and fixes 4. JIRA syncs back to Black Duck Hub and verifies fix NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 24

Considerations • Tool integration considerations 1. 2. 3. 4. 5. 6. 7. Availability (Y/N)? When? Push, pull, both (bidirectional), or none? Native or through a 3 rd party connector? Tight or loose integration? Server-side or client plugin? Ability to throttle? (high severity only) Cost? NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 25

Considerations • Business considerations 1. 2. 3. 4. 5. 6. 7. 8. Due diligence researched (all options) Integration with existing systems? Buy, build or use existing? When? This Fiscal Year, next FY? Who will use? Which BUs will purchase? (other benefactors) Who will install, host, and maintain? Who will configure and customize? NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 26

Considerations • Engineer considerations 1. Does ALM contain all user stories? • Insight manual integration (email) 2. Ticketing system adds advanced workflow and SLA reminders • Does it need to be engineer friendly or just tightly integrated with ALM? 3. Data overload - throttle settings • Issue severity: Critical, High, Medium, Low • Business Impact vs. Risk score vs. CVSS v 3 score NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 27

Questions? Harold Toomey Sr. Software Security Architect Product & App. Security Group Mc. Afee LLC Harold_Toomey@Mc. Afee. com W: (972) 963 -7754 M: (801) 830 -9987 NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 28

Thank you NTXISSA Cyber Security Conference – November 10 -11, 2017 @NTXISSA #NTXISSACSC 5 29
 Project management herding cats
Project management herding cats Stella ting toomey
Stella ting toomey Advantages and disadvantages of nomadic farming
Advantages and disadvantages of nomadic farming Nomadic herding definition ap human geography
Nomadic herding definition ap human geography Staff of herding
Staff of herding Security private
Security private Social exchange theory thibaut and kelley
Social exchange theory thibaut and kelley Edwin binney and harold smith
Edwin binney and harold smith Harold and the purple crayon summary
Harold and the purple crayon summary Example of figure of speech personification
Example of figure of speech personification Journal of a lumpy kid by ken jiffy
Journal of a lumpy kid by ken jiffy The day they parachuted cats into borneo correct order
The day they parachuted cats into borneo correct order Cats of borneo timeline
Cats of borneo timeline Epaxial muscle injection dog
Epaxial muscle injection dog What is hyperbole in figure of speech
What is hyperbole in figure of speech Learner response system
Learner response system Acronym for reactivity series
Acronym for reactivity series Identification of scanning and analysis tools
Identification of scanning and analysis tools Wireless security in cryptography and network security
Wireless security in cryptography and network security Electronic commerce security
Electronic commerce security Harold hütt herrera
Harold hütt herrera Harold cohen aaron
Harold cohen aaron Cara british mendapatkan tanda tangan sultan
Cara british mendapatkan tanda tangan sultan Klasifikasi negara menurut h.n sinha
Klasifikasi negara menurut h.n sinha Godfrey harold hardy
Godfrey harold hardy Minecraft harold brian
Minecraft harold brian Harold pincus
Harold pincus Why did harold macmillan resign
Why did harold macmillan resign Harold castilla cruz
Harold castilla cruz El reloj de acaz
El reloj de acaz