Securing Your Microsoft Windows SOHO Network Harold Toomey






































- Slides: 75

Securing Your Microsoft Windows SOHO Network Harold Toomey, Product Manager Symantec Corporation htoomey@symantec. com 8 January 2002 1

Agenda § The Threat • Hackers • Attacks § Security Best Practices • The 80 -20 Rule • Patches • Password strength § The Tools • Norton Internet Security 2002 • Enterprise-Class tools § Typical SOHO Network • Network layout • Vulnerable segments • Security tips 2 Symantec Confidential

The Threat § Whether your Internet connection is always on or you only dial in occasionally, your computer is vulnerable every minute it's online § Hackers have the tools and knowledge to compromise your system § Security experts are calling 2001 the worst year for computer viruses • December is the worst month • Experts predict 2002 will be even worse • Predict “viruses and their cousins, the self-propagating worms, will find new and even more nasty ways to attack computer systems, possibly even hitting mobile devices, pocket PCs and smart phones in the coming year. ” (Source: Reuters 12 -26 -2001 & USA Today 12 -27 -2001) 3 Symantec Confidential r

Why Hackers Attack § Professionals • Military tool / Cyber warfare • Industrial espionage • Hacktivism § Hackers • Money $$ (credit cards, extortion) • Power (DDo. S zombies) • Fame (want a “name”) • Fun (adventure game) • Socialize (hacker clubs) • Revenge (www. grc. com) • Cheap (can’t afford own hard drive space) • Because they can 4 Symantec Confidential r

Why Hackers Attack § Script Kiddies • Only use tools others have created • Usually just kids (10 -17) § White Hat Hackers • Good intent • Test for security vulnerabilities before attackers can abuse them § Black Hat Hackers • Evil intent 5 Symantec Confidential r

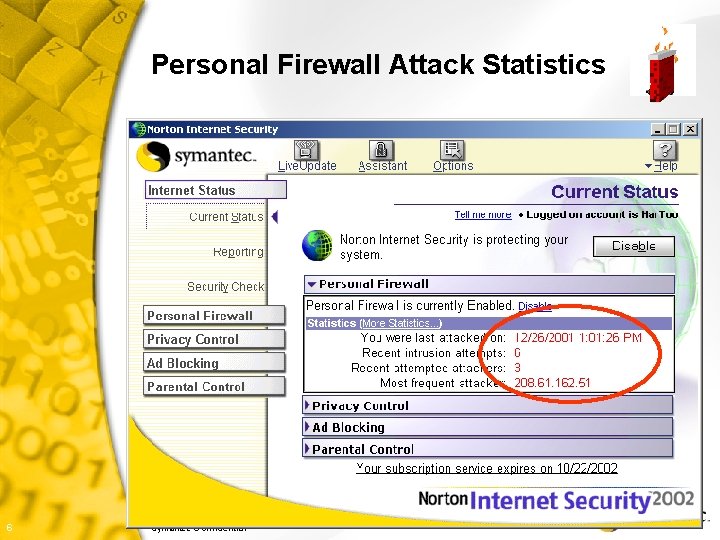
Personal Firewall Attack Statistics 6 Symantec Confidential

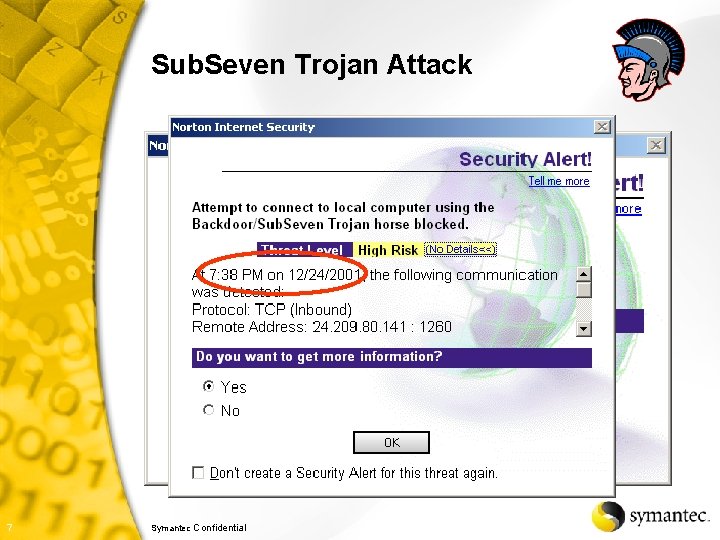
Sub. Seven Trojan Attack 7 Symantec Confidential

Trojan Horses and Backdoors § Trojan Horses • Replace known programs • A login Trojan works like normal login, but captures user passwords or gives privileged access on demand • Will have the same behavior as the programs they are replacing and are difficult to find • Usually contain backdoors • Mask the existence of backdoors § Backdoors • May replace known programs • Backdoors give attackers direct access (often root level) to the system, foregoing normal authentication • May replace login command to allow quick root level access • May listen on certain ports for further direct access 8 Symantec Confidential k

Sub. Seven Trojan § What it does • Allows remote control of Windows: – File – Monitoring – Network § Protection from it • Keep your systems updated • Eliminate all unneeded programs • Periodically scan network for common backdoor services • Check critical files for tampering (MD 5 signature) • Use intrusion detection (IDS) 9 Symantec Confidential

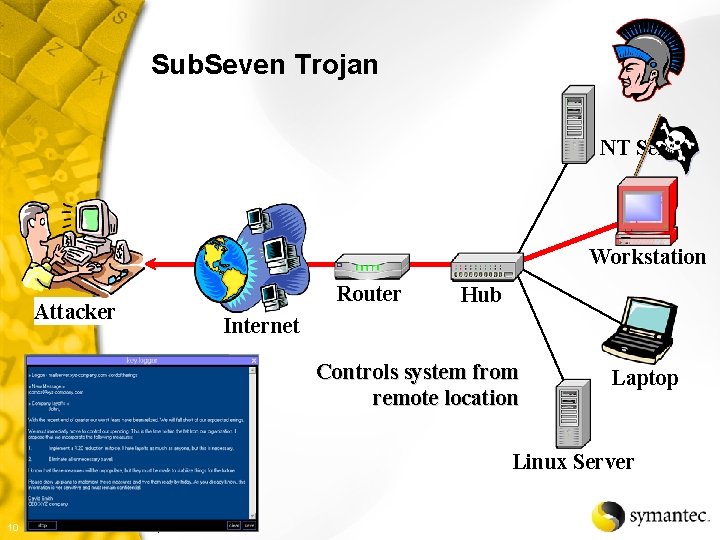
Sub. Seven Trojan NT Server Workstation Attacker Router Hub Internet Controls system from remote location Laptop Linux Server 10 Symantec Confidential

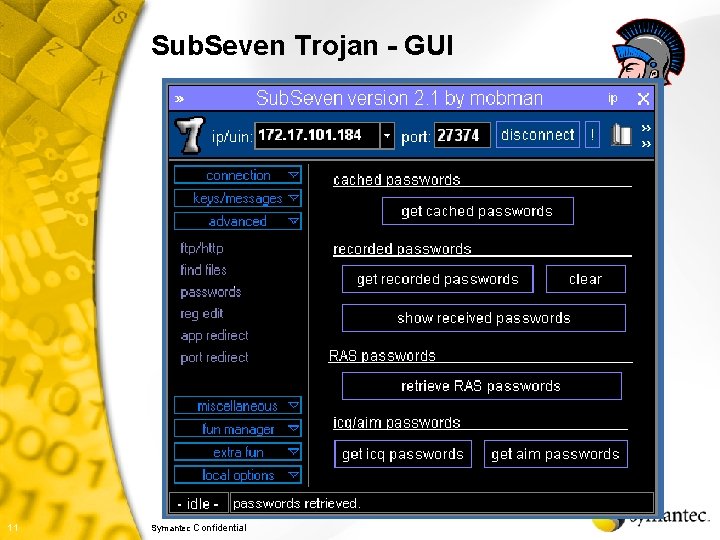
Sub. Seven Trojan - GUI Connect to remote system 11 Symantec Confidential

Sub. Seven Trojan - GUI we have captured a very > New Message < confidential email Jcombs@xyz-company. com message! Company layoffs < Select Key logger John, to capture what is With the recent end of quarter our worst fears have been realized. We will fall short of our expected earnings. typed on the We must immediately move to control our spending. This is the time to trim the fat from our keyboard of the organization. I propose that we incorporate the following measures: remote system 1. Implement a 20% reduction in work force, I hate layoffs as much as anyone, but this is >Logon – mailserver. xyz-company. com <lordoftherings> 12 2. necessary. Eliminate all unnecessary travel. 3. I know that these measures will be unpopular, but they must be made to stabilize things. 4. 5. Please draw up plans to implement these measures and have them ready by Friday. As you already know, this Information is very sensitive and must remain confidential. 6. 7. David Smith CEO XYZ Company Symantec Confidential

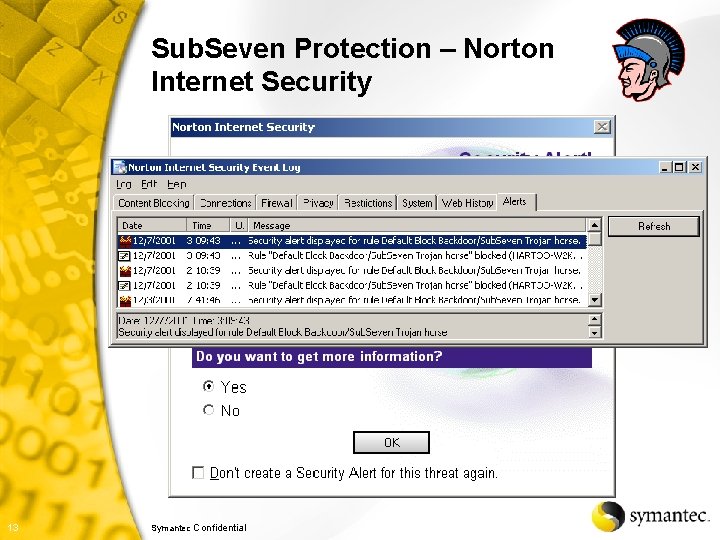
Sub. Seven Protection – Norton Internet Security 13 Symantec Confidential

Sub. Seven Protection – Anti. Virus 14 Symantec Confidential

Sub. Seven Detection - Net. Recon 15 Symantec Confidential

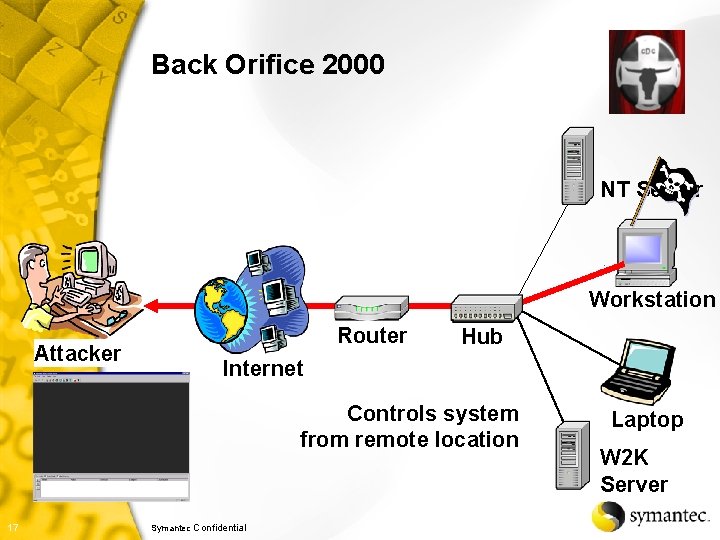
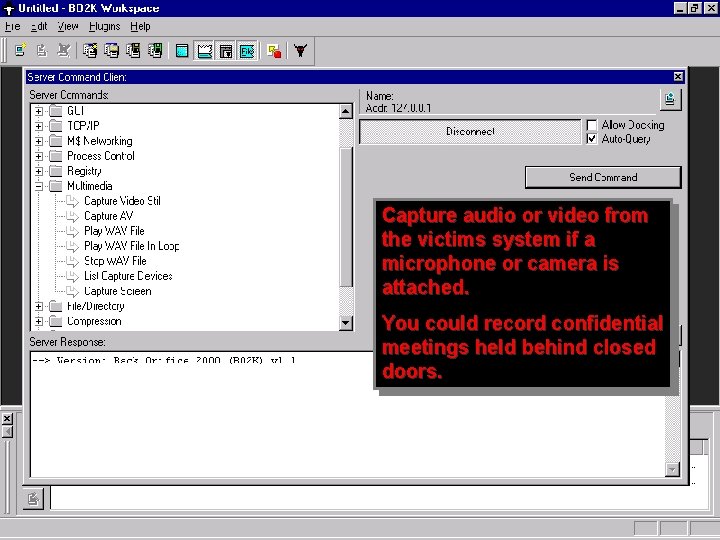
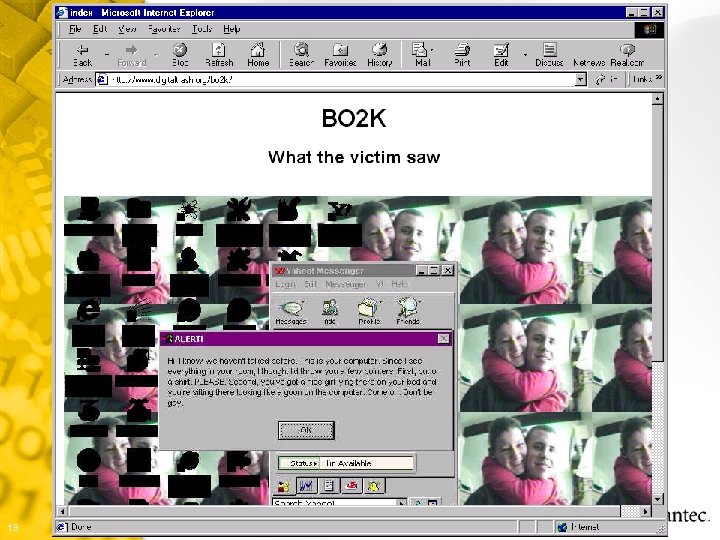
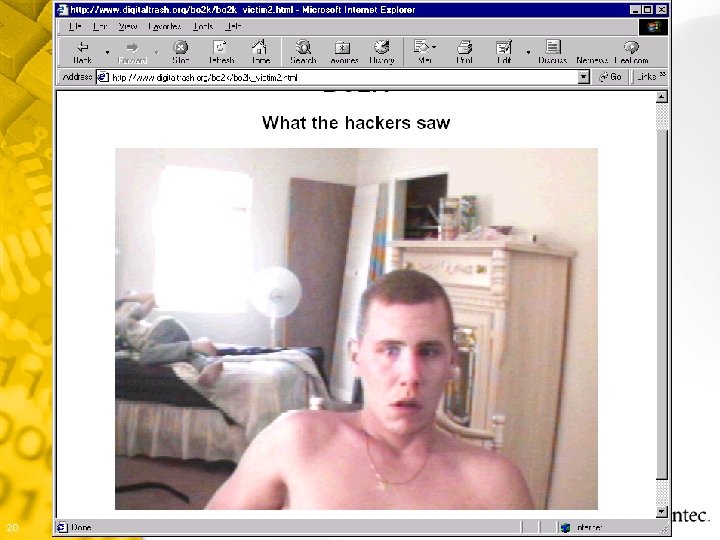
Backdoor - Back Orifice 2000 § From “cult of the dead cow” § Allows remote control of Windows: • File system • Passwords • Network • Registry • Processes • System • Extensive multi-media controls • Capture images from server screen • Record confidential conversations § NT registry passwords and Win 9 x screen saver password dumping § Most virus detection software will identify the binary version § Completely open-source (anyone can change it) 16 Symantec Confidential

Back Orifice 2000 NT Server Workstation Attacker Router Hub Internet Controls system from remote location 17 Symantec Confidential Laptop W 2 K Server

Capture audio or video from the victims system if a microphone or camera is attached. You could record confidential meetings held behind closed doors. 18 Symantec Confidential

19 Symantec Confidential

20 Symantec Confidential

The system power turns off! 21 Symantec Confidential

22 Symantec Confidential

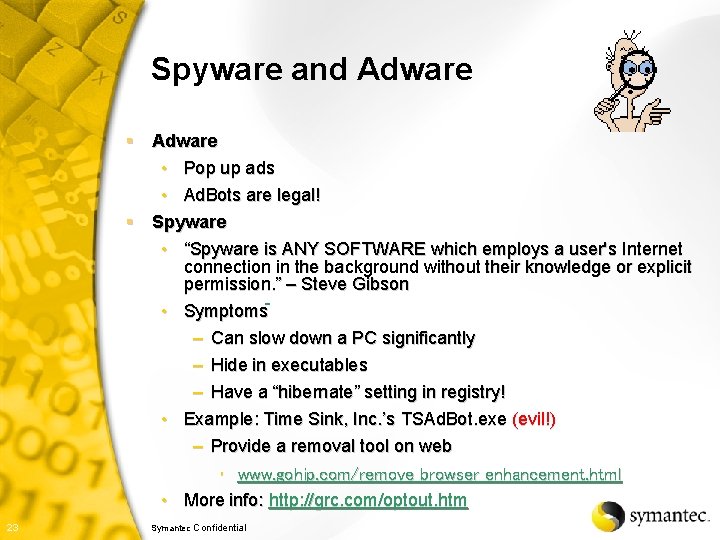
Spyware and Adware § Adware • Pop up ads • Ad. Bots are legal! § Spyware • “Spyware is ANY SOFTWARE which employs a user's Internet connection in the background without their knowledge or explicit permission. ” – Steve Gibson • Symptoms – Can slow down a PC significantly – Hide in executables – Have a “hibernate” setting in registry! • Example: Time Sink, Inc. ’s TSAd. Bot. exe (evil!) – Provide a removal tool on web • www. gohip. com/remove_browser_enhancement. html • More info: http: //grc. com/optout. htm 23 Symantec Confidential

Viruses & Worms § A few viruses that received media attention • Naked Wife • Anna Kournikova • ILOVEYOU • Melissa § A few worms that received media attention • Code. Red II • Nimda • Sir. Cam § http: //securityresponse. symantec. com/ 24 Symantec Confidential

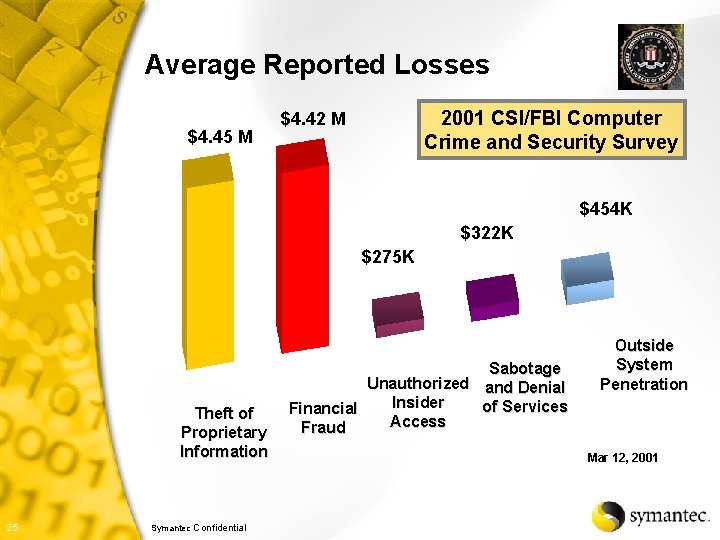
Average Reported Losses $4. 45 M 2001 CSI/FBI Computer Crime and Security Survey $4. 42 M $454 K $322 K $275 K Theft of Proprietary Information 25 Symantec Confidential Sabotage Unauthorized and Denial Insider of Services Financial Access Fraud Outside System Penetration Mar 12, 2001

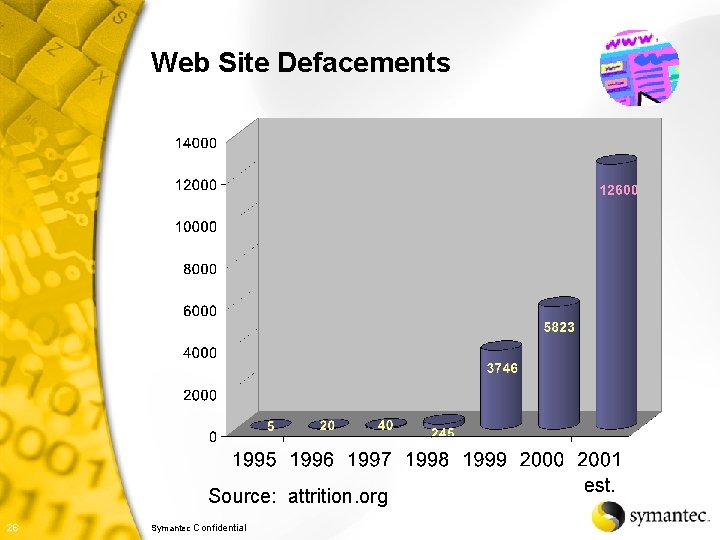
Web Site Defacements Source: attrition. org 26 Symantec Confidential

Security Best Practices § No need to start from scratch • Rather than analyzing every risk, look at what others are doing • Meet standards of due care • Use existing standards and industry “best practices” • Pay attention to regulations and requirements – Government – Industry – Partners 27 Symantec Confidential

Security Best Practices § Best Practices that Block Most Attacks • Employ a layer 7, full inspection firewall • Use automatically updated anti-virus at gateway, server, and client • Ensure security patches are up to date • Ensure passwords are strong • Turn off unnecessary network services 28 Symantec Confidential

Security Best Practices § The 80 -20 rule of security 1) Security patches 2) Password strength 3) Unnecessary services § The 80 -20 rule means do 20% of the work to gain 80% of the results 29 Symantec Confidential

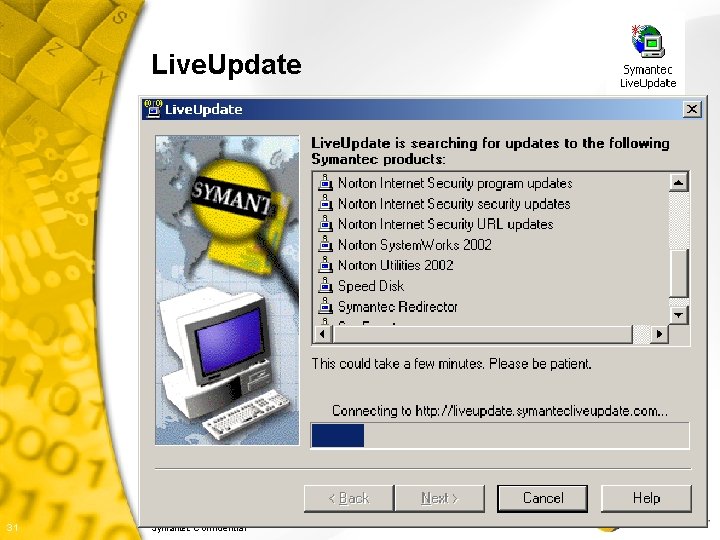
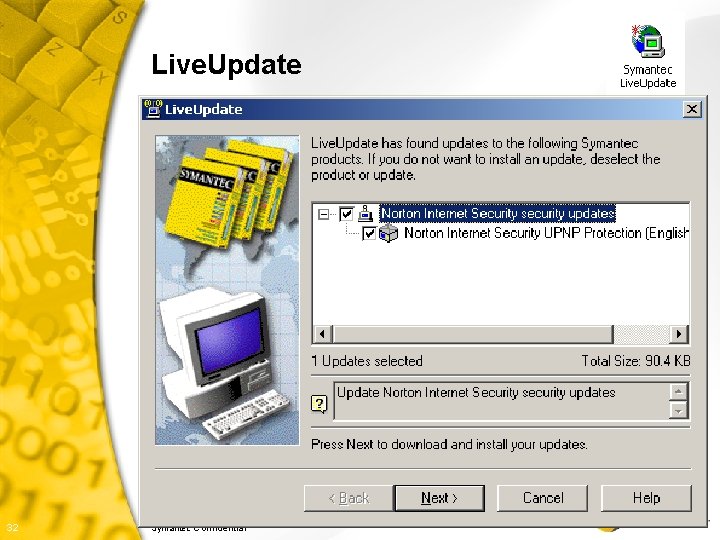
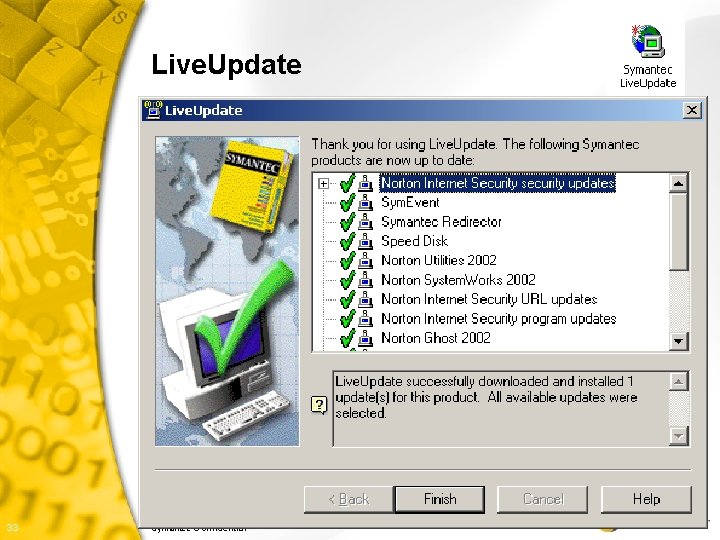
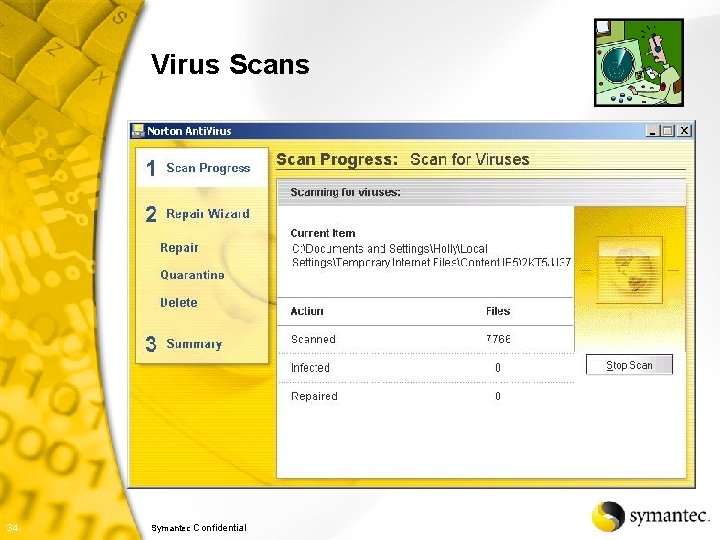
Security Patches § Norton Anti. Virus Live. Update • Schedule to check for updates regularly • Updates virus signatures • Updates content to entire Norton Internet Security 2002 suite § Virus Scans • Scan for viruses 3 x weekly § Enable Personal Firewall • Be sure it is “Enabled” 30 Symantec Confidential k

Live. Update 31 Symantec Confidential

Live. Update 32 Symantec Confidential

Live. Update 33 Symantec Confidential

Virus Scans 34 Symantec Confidential

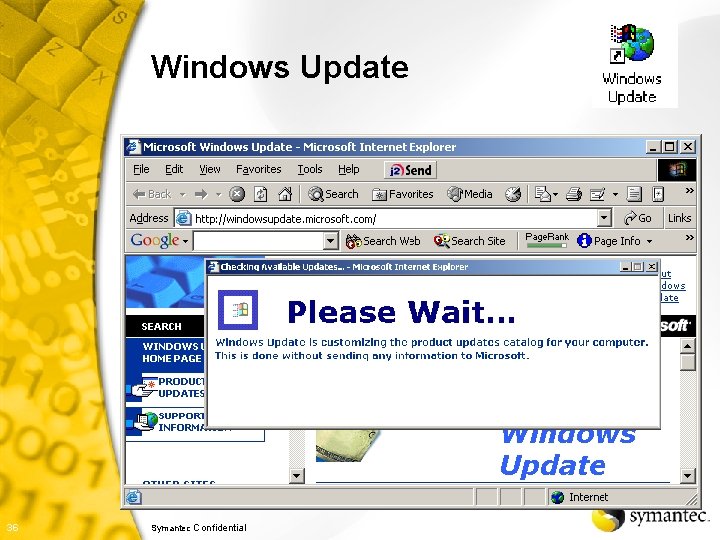
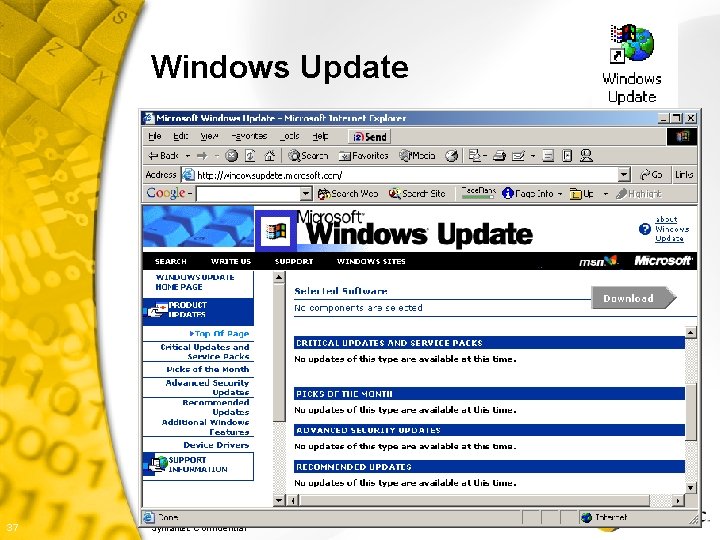
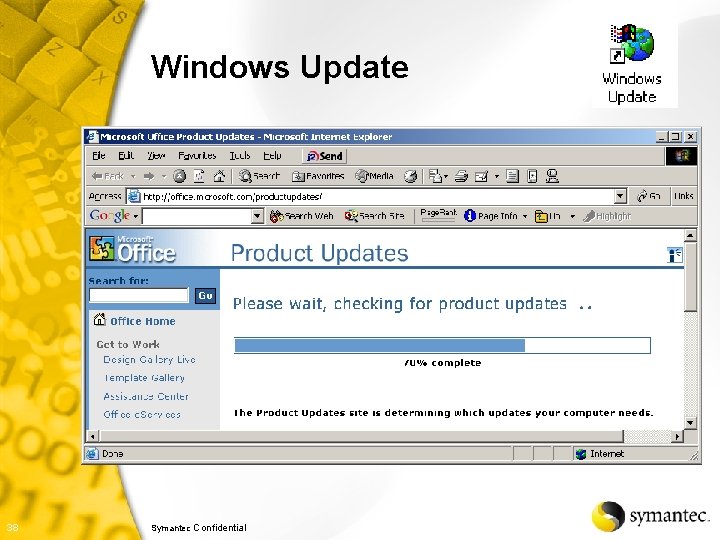
Security Patches § MS Windows Update • Download critical updates at a minimum • %System. Root%system 32wupdmgr. exe • http: //windowsupdate. microsoft. com/ Product Updates § MS Office Product Updates • http: //windowsupdate. microsoft. com/ Microsoft Office Product Updates § Other software products 35 Symantec Confidential k

Windows Update 36 Symantec Confidential k

Windows Update 37 Symantec Confidential k

Windows Update 38 Symantec Confidential k

Password Strength § Password stealing • CGI script exploits, password cracking, social engineering, shoulder surfing, … • Network sniffing – Reading the password directly from network traffic § Password guessing • Predictable passwords – blank, “guest”, user name, family name, birthdays, license plates, pets, etc. • Dictionary attack – “earth 1” is an example of a password that is susceptible to dictionary attack • Brute force 39 Symantec Confidential k

Password Strength § Password cracking tools • Use available tools to regularly check for bad passwords • Commercial tools – Symantec Enterprise Security Manager – Symantec Net. Recon • Hacker tools – LØpht. Crack (www. atstake. com/research/lc 3/) – John the Ripper (www. openwall. com/john/) – Caution: Use of such tools may be grounds for dismissal and/or legal action 40 Symantec Confidential r

Password Strength § Don’t send passwords over the network in clear text § Consider two-factor authentication • A password + something else – For example, encryption key pair, smart card, … § Enforce strict password policies • E. g. minimum 8 characters § Keep your systems and applications patched and updated 41 Symantec Confidential r

Password Strength § Do’s • Use mixed-case letters – Use uppercase letters throughout the password • Use alphanumeric characters and include punctuation • Use mixed-case letters – Do not just capitalize the first letter, but add uppercase letters throughout the password • Use at least six characters, eight characters for Windows NT – Password rules apply to the first N characters of the password • Use a seemingly random selection of letters and numbers • Change passwords regularly 42 Symantec Confidential r

Password Strength § Do’s • Use password expiration settings – No old (recycled) passwords – Can't use passwords less than N days old – Old and new passwords must differ by at least N characters • Watch for – Maximum number of character pairs • E. g. “Hiiiiii. Mom” – Minimum inside digits • E. g. “Hi 123456 Mom” • Test your passwords – http: //www. securitystats. com/tools/password. asp 43 Symantec Confidential r

Password Strength § Do Not’s • Use a network login ID in any form (reversed, capitalized, or doubled as a password) • Use your first, middle or last name or anyone else’s in any form – Do not use your initials or any nicknames you may have or anyone else’s • Use a word contained in English or foreign dictionaries, spelling lists, or other word lists and abbreviations • Use a password that can be typed quickly, without having to look at the keyboard ("shoulder surfing") 44 Symantec Confidential r

Password Strength § Do Not’s • Use other information easily obtained about you – This includes pet names, license plate numbers, telephone numbers, identification numbers, the brand of your automobile, the name of the street you live on, and so on • Use a password of all numbers, or a password composed of alphabet characters – Mix numbers and letters • Use dates e. g. , September, SEPT 1999 or any combination thereof • Use keyboard sequences, e. g. , qwerty. • Use a sample password, no matter how good, that you’ve gotten from a book that discusses information and computer security 45 Symantec Confidential r

Password Strength § Do Not’s • Use any of the above things spelled backwards, or in caps, or otherwise disguised • Write a password on sticky notes, desk blotters, calendars, or store it online where it can be accessed by others. • Use shared accounts – Accountability for group access is extremely difficult • Reveal a password to anyone 46 Symantec Confidential r

Unnecessary Services § Turn off non-essential services • Every service is a potential hole into your network • Allow connections only from trusted systems • Do not share unnecessary resources § Turn off File Sharing • At least password protect if used § Example: Disable web server services if not used • Ports 80 & 8080 47 Symantec Confidential r

Unnecessary Services Hacker Exploitation of File Sharing 1) Find open file shares - Use Legion v 2. 1 from www. rhino 9. com 2) Crack passwords - Copy SAM files from Windows systems - Use LØphtcrack. exe to crack passwords - www. lØpht. com - Can also obtain backup of SAM files. Must rename first. NOTE: To get SAM files, - Run rdisk. exe to create an emergency repair disk - Look in Win. NTsystem 32 for SAM files 48 Symantec Confidential

Unnecessary Services Hacker Exploitation of File Sharing 3) Login 4) Install BØ 2 K - Run BØpeep - Can wrap Elf Bowling game with BØ 2 K using Suranwrapper - BØ 2 K executable is only 110 KB 5) Use a packet sniffer - Snort (www. whitehat. com for signatures) - e. Eye Iris 2. 0 Traffic Analyzer (www. eeye. com) 6) Keep Under FBI Limit - FBI Cyber Crime Unit - CIA Cyber Crime Unit - Won't prosecute unless > $10, 000 or child porn Source: 23. org, 5 -17 -2000 49 Symantec Confidential

The Tools 50 Symantec Confidential

Virus and Hostile Applet Protection § Use anti-viral and content scanning software • Desktops • Servers • Firewall § Apply latest patches • E-mail (IE – MS Outlook) • Browser • Operating System (XP) § Don’t double-click blindly on attachments • Beware of. EXE, . VBS, and. SCR § Use higher levels of browser security 51 Symantec Confidential

Firewalls § Protect your perimeter with a firewall • Monitor both in-coming and out-going traffic • Use a highly configurable, proxy-based firewall • Make sure it is ICSA and Checkmark certified § Personal Firewalls • Norton Personal Firewall 2002 § Enterprise-Class Firewalls • Symantec Firewall Appliance • Raptor Firewall 52 Symantec Confidential r

Symantec Tools § Norton Internet Security 2002 • Personal Firewall • Privacy Control • Intrusion Protection • Anti-Virus • Ad Blocking • Parental Control • Configure Internet Access for each user v 2002 Shipped 30 Aug 2001 53 Symantec Confidential

Personal Firewall § Defend your PC against hackers • Norton™ Personal Firewall starts protecting your PC by "hiding" it from hackers. • Exclusive Symantec technology automatically configures firewall rules for the most common Internet applications. • Monitors both inbound and outbound traffic. • The Internet Access Control feature prevents the applications on your PC from secretly making connections to Internet sites and sending information to them. 54 Symantec Confidential

Privacy Control § Keep your personal information private • Will alert you if you accidentally try sending credit-card numbers over an unsecure web connection. • Protect your bank-account information, creditcard numbers, and other confidential data online. • Prevent web sites from retrieving your email address without your knowledge, and to control which sites are allowed to track your online activities with "cookies. “ • Lets you block Java™ applets, Active. X® controls, and cookies on a site-by-site basis. 55 Symantec Confidential

Intrusion Protection § Norton Internet Security 2002 • Intrusion Protection with Auto. Block automatically stops systems from trying to probe your PC's ports. • It safeguards your PC and your personal information by blocking unauthorized connections and alerting you to attempted intrusions. 56 Symantec Confidential

Anti-Virus § Stop viruses and other malicious code automatically • Norton Anti. Virus™ provides maximum protection against viruses-including those included in email messages. • The world's leading anti-virus software works in the background to defend your computer 24 hours a day. • New and exclusive Script Blocking technology proactively protects against known and unknown threats, such as the renowned "I Love You" and "Anna Kournikova" viruses - without the need for virus definitions. 57 Symantec Confidential

Ad Blocking e 18 Must b r… or olde § Block unwanted ads • Banner ads and pop-up windows can clutter your screen and lengthen web page download times. • They can also expose children to inappropriate advertising. • Norton Internet Security 2002 lets you filter them out for a faster, more enjoyable web experience. 58 Symantec Confidential

Parental Control § Keep your children safe on the Internet • Norton Parental Control software blocks access to objectionable sites based on a comprehensive, customizable list. • Make sure that your children have a safe, enjoyable experience every time they log on to the Internet. • It also lets you set up different Internet access privileges for each person in your household, so you can quickly and easily provide full access for adults and age-appropriate access for each child. • Tools are only 80% to 90% effective. “Teach them correct principles …” 59 Symantec Confidential

Updates with Live. Update § Get regular protection updates • Symantec's Internet security experts update Norton Internet Security 2002 continuously to deal with new viruses and other Internet threats. • Norton Anti. Virus even keeps itself updated, using Symantec's exclusive Live. Update™ technology to check for new virus definitions when you're online and download them automatically. • As a registered user, you'll get free anti-virus and firewall updates for one year. After that, you can subscribe to future updates $3. 95 annual fee. § More info: • http: //securityresponse. symantec. com 60 Symantec Confidential

Norton Internet Security 2002 System Requirements Windows XP Home Edition/Professional - Intel Pentium II 300 MHz or higher processor - 128 MB of RAM Windows NT/2000 Professional - Windows NT 4. 0 Workstation with service pack 6 a or higher - Intel Pentium 150 MHz or higher processor - 64 MB of RAM Windows Me/98 - Intel Pentium 150 MHz or higher processor - 32 MB of RAM (48 MB recommended) REQUIRED FOR ALL INSTALLATIONS - 60 MB of available hard disk space (without Parental Control feature installed) - 90 MB of available hard disk space (for complete installation) - CD-ROM or DVD-ROM drive - Microsoft ® Internet Explorer 4. 01 with MSIE Service Pack 1 or later - Microsoft Windows Internet support 61 Symantec Confidential

Norton Internet Security 2002 System Requirements Email scanning supported for any standard POP 3 compatible email client, including - Microsoft Outlook Express 4. 0/5. x - Microsoft Outlook XP/2000/98/97 - Netscape Messenger 4. X - Netscape Mail 6. 0 - Eudora Light 3. 0, Eudora Pro 4. 0, Eudora 5. 0 Supported instant messaging clients for Confidential Information filtering - MSN Messenger 3. 6 - AOL Instant Messenger 4. 3 - Windows Messenger 4 62 Symantec Confidential

Symantec Firewall/VPN Small Office Appliance § § § § Firewall VPN IP Sharing/DHCP Server 10/100 Auto-sense switch Automatic dial-up backup* Load balancing built-in (model 200) Remote management *with external analog modem 63 Symantec Confidential

Network Vulnerability Scanners § Symantec Net. Recon 1. Discovers systems 2. Discovers services 3. Finds vulnerabilities than can be exploited 4. Cracks passwords 5. Logs in 6. Reports § ISS Internet Scanner • Strong market share • Will execute denial-of-service (Do. S) attacks § Nessus Scanner • Is free 64 Symantec Confidential r

Intrusion Detection § Stop scans at the perimeter • Use a highly configurable firewall (proxy-based is best) • Only allow necessary ports to be accessible from the outside • Use a DMZ for other services § Use both Host-based and Network-based intrusion detection • Security administrator can be alerted when an attack is in progress • Symantec Intruder Alert (host-based) • Net. Prowler (network-based) 65 Symantec Confidential r

Other Symantec Products § Anti. Virus • Norton Anti. Virus • NAV for Palm Pilots • NAV for Gateways § Firewall • Symantec Enterprise Firewall (Raptor) • Symantec Firewall Appliance • Norton Personal Firewall § Security Assessment • Enterprise Security Manager • Symantec Net. Recon • ESM for Databases, Web Servers and Firewalls 66 Symantec Confidential § Intrusion Detection • Intruder Alert • Prowler. IDS § Content Filtering § I-Gear § Mail Gear § Privacy § Norton Internet Security § Administration / Utilities § pc. Anywhere § Norton Ghost § Norton Utilities § Norton Clean. Sweep § VPN § Raptor. Mobile

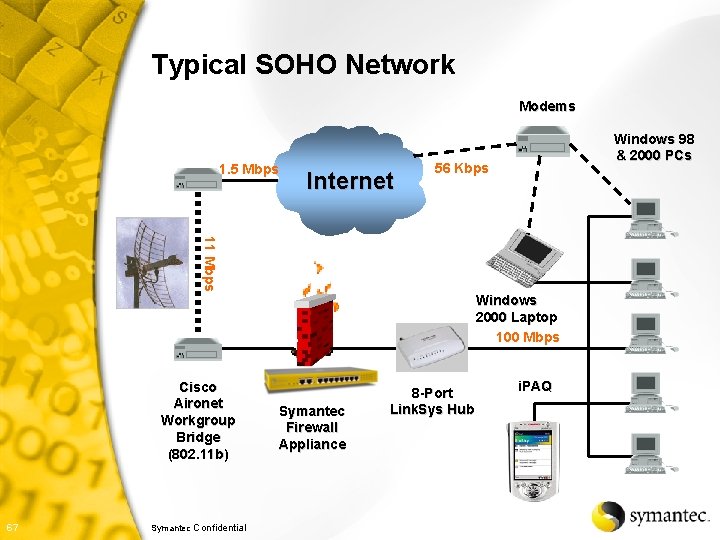
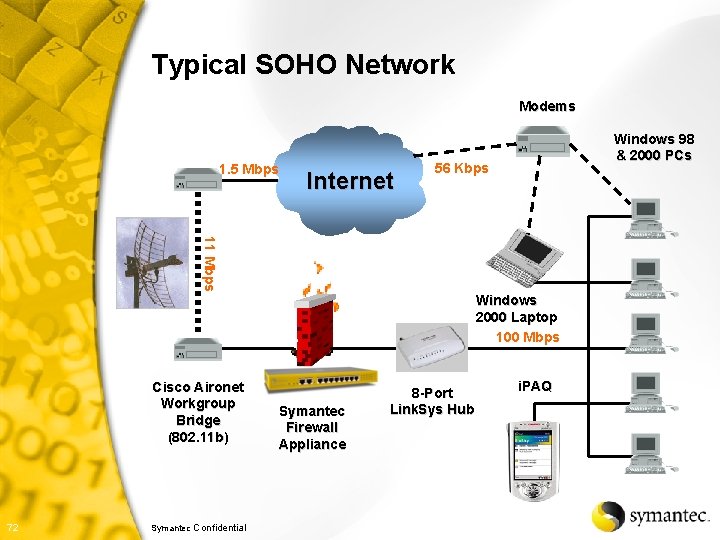
Typical SOHO Network Modems 1. 5 Mbps Internet Windows 98 & 2000 PCs 56 Kbps 11 Mbps Windows 2000 Laptop 100 Mbps Cisco Aironet Workgroup Bridge (802. 11 b) 67 Symantec Confidential Symantec Firewall Appliance 8 -Port Link. Sys Hub i. PAQ

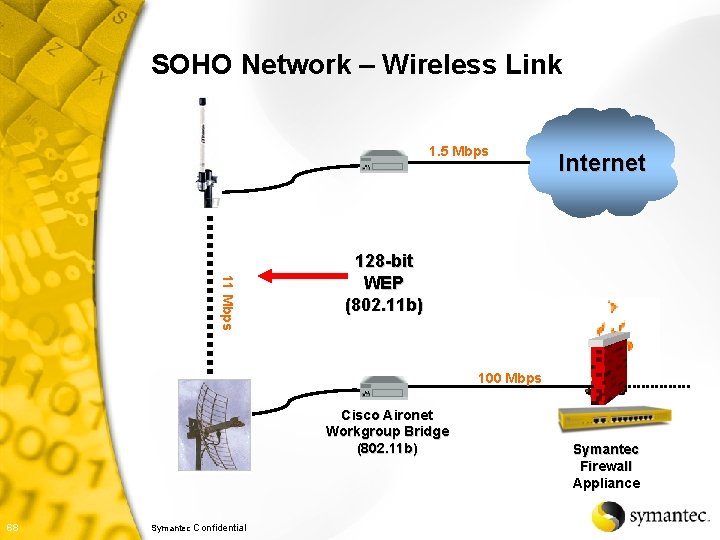
SOHO Network – Wireless Link 1. 5 Mbps Internet 11 Mbps 128 -bit WEP (802. 11 b) 100 Mbps Cisco Aironet Workgroup Bridge (802. 11 b) 68 Symantec Confidential Symantec Firewall Appliance

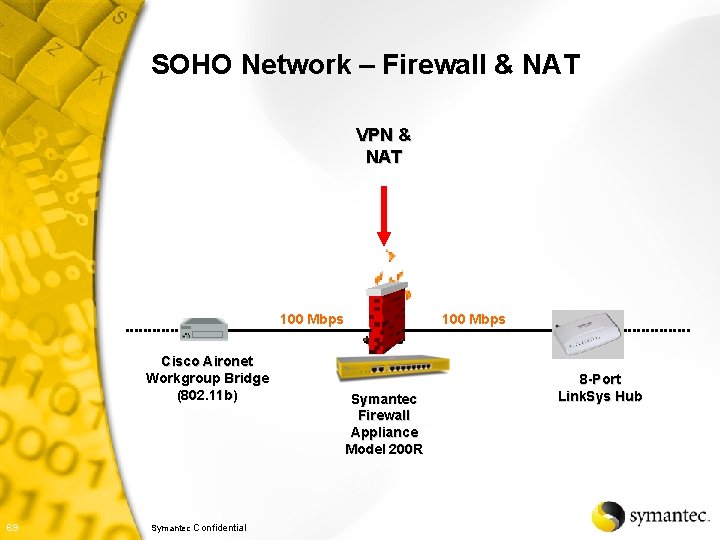
SOHO Network – Firewall & NAT VPN & NAT 100 Mbps Cisco Aironet Workgroup Bridge (802. 11 b) 69 Symantec Confidential 100 Mbps Symantec Firewall Appliance Model 200 R 8 -Port Link. Sys Hub

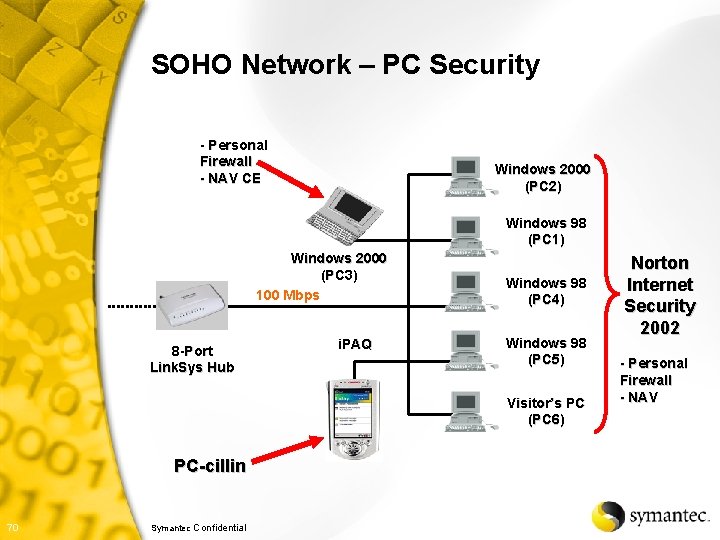
SOHO Network – PC Security - Personal Firewall - NAV CE Windows 2000 (PC 2) Windows 98 (PC 1) Windows 2000 (PC 3) 100 Mbps 8 -Port Link. Sys Hub i. PAQ Windows 98 (PC 4) Windows 98 (PC 5) Visitor’s PC (PC 6) PC-cillin 70 Symantec Confidential Norton Internet Security 2002 - Personal Firewall - NAV

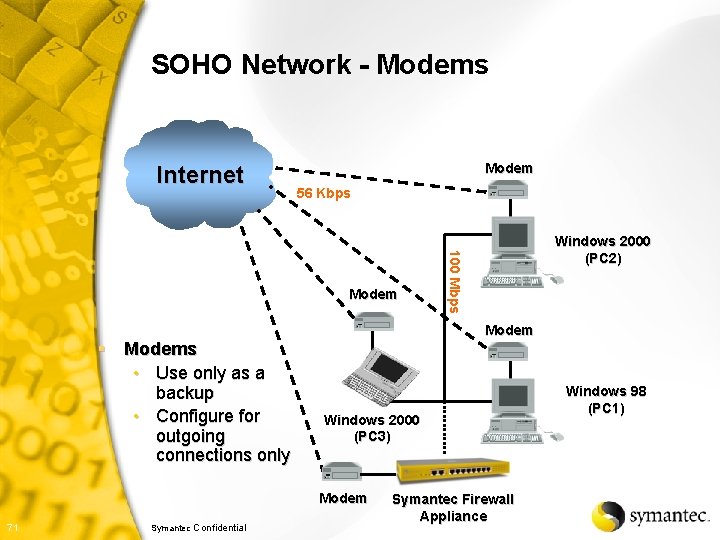
SOHO Network - Modems Internet Modem 56 Kbps 100 Mbps Modem Windows 2000 (PC 2) Modem § Modems • Use only as a backup • Configure for outgoing connections only Windows 2000 (PC 3) Modem 71 Symantec Confidential Symantec Firewall Appliance Windows 98 (PC 1)

Typical SOHO Network Modems 1. 5 Mbps Internet Windows 98 & 2000 PCs 56 Kbps 11 Mbps Windows 2000 Laptop 100 Mbps Cisco Aironet Workgroup Bridge (802. 11 b) 72 Symantec Confidential Symantec Firewall Appliance 8 -Port Link. Sys Hub i. PAQ

Where to Look for More Information § Symantec Corporation • http: //www. symantec. com • http: //securityresponse. symantec. com § SANS Top 20 List • http: //www. sans. org § CERT Advisories • http: //www. cert. org § CVE (Common Vulnerabilities and Exposures) • http: //cve. mitre. org § Security Focus (Home of BUGTRAQ) • http: //www. securityfocus. com § Packet Storm • http: //packetstorm. securify. com 73 Symantec Confidential

Conclusion § Hackers will attack your SOHO network • They have access to powerful tools and lots of information • Looking for DDo. S Zombies • Want free hard disk space to store porn, etc. § Form a habit of following the 80 -20 rule of security • Check for OS, application and security patches weekly • Use strong passwords • Turn off unnecessary services § Firewalls and anti-virus software must be used • Design security into your network § Use Symantec software! • Largest security company in the world • 100% focused on security 74 Symantec Confidential r

75 Symantec Confidential