Hacking Exposed 7 Network Security Secrets Solutions Chapter













- Slides: 15

Hacking Exposed 7 Network Security Secrets & Solutions Chapter 11 Mobile Hacking 1

Outline • Hacking Android – Android fundamentals – Hacking your Android – Hacking other’s Android • Hacking i. OS – How secure is i. OS – Hacking your i. OS – Hacking other’s i. OS 2

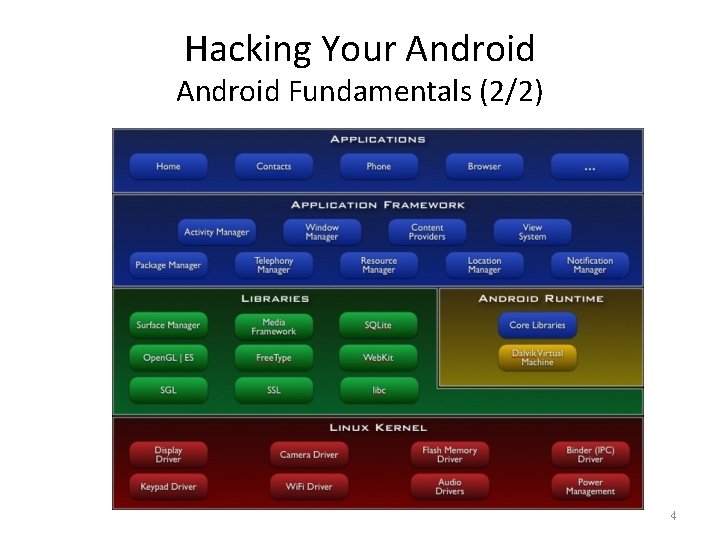
Hacking Android Fundamentals (1/2) • Android architecture – – – ARM cross-compiled Linux kernel Native libraries Android runtime (including Dalvik virtual machine) Application framework Applications • Software Development Kit (SDK) – Android Emulator: prototype, develop, and test Android applications without using a physical device – Android Debug Bridge (ADB): • a command-line tool for communicating with an emulator or a physical device • execution of native apps – Dalvik Debug Monitor Server (DDMS): • obtain log information through logcat • send simulated location data, SMS, and phone calls • provide memory management information 3

Hacking Your Android Fundamentals (2/2) 4

Hacking Your Android • Rooting “your” Android to get administrative privileges – Full control of the device – The device may be “bricked” • Android Rooting Tools: Super. One Click, Z 4 Root, Ginger. Break • Steps for rooting a Kindle Fire – – – Enable installation of applications from unknown sources Install the Android SDK Add commends in adb_usb. in android_winusb. inf Connect Kindle Fire with PC through ADB Download rooting files and execute them 5

Hacking Your Android Apps for Rooted Android Devices • Superuser: control which applications can execute with root privileges • ROM Manager: install a custom ROM • Market Enabler: spoof your location and carrier network to the Android market • Connect. Bot: execute shell commands remotely • Screenshot: obtain device screenshots • ES File Manager: copy, paste, cut, create, delete, and rename system files • Set. CPU: set the CPU clock • Juice Defender: save power and extend battery life by managing hardware components 6

Hacking Your Android Native Apps on Android • Busy. Box: a set of UNIX tools that allows you to execute useful commands • Tcpdump: capture and display packets that are transmitted over a network • Nmap: discover hardware and software on a network to identify specific details of the host operating system, open ports, DNS names, and MAC addresses, • Ncat: read and write data across networks from the command line for making various remote network connections 7

Hacking Your Android Trojan Apps • A malicious program that disguises legitimate apps by using the same icon or name • Reengineer Android applications – Manifest. xml: an encoded XML file that defines essential information about the application to the Android – Classes. dex: the Dalvik executable where the compiled code resides • Tools for Modify an app – apktool: unzip and repack the Android application (apk) file – Sign. Apk: verify the repacked file – Steps • • • Use apktool to unzip an apk file Modify the application name in Mainifest. xml via any editor tool (e. g. notepad) Change icons in the unzipped folder/subfolder User apktool to repack the apk file Sign the verification via Sign. Apk 8

Hacking Other’s Android Vulnerabilities in Android (1/2) • Remote Shell via Web. Kit – Get the latest version of Android – Install antivirus software • Root an Android remotely: Rage. Against. The. Cage – Get the latest version of Android – Install antivirus software • Data Stealing through a PHP file – – – Get the latest version of Android Install antivirus software Temporarily disable Java. Script Use another third-party browser Unmount the “/sdcard” partition to protect the data stored there • Remote Shell with Zero Permissions – Check the ratings and user reviews to try to identify suspicious applications 9

Hacking Other’s Android Vulnerabilities in Android (2/2) • Exploiting Capability Leaks – Check the ratings and user reviews to try to identify suspicious applications • URL-sourced Malware (Side-load Applications) – Unselect “Unknown Sources” in Settings->Applications • Skype Data Exposure – Keep applications updated • Carrier IQ – Use Lookout’s Carrier IQ Detector • HTC Logger – Get the patch from HTC • Cracking the Google Wallet PIN – – Don’t leave the phone unattended. Use the traditional Android screen lock Do not root the device Install antivirus software 10

Hacking i. OS How Secure Is i. OS? • Third-party apps are disallowed except under a less privileged user account • Apps have to be signed by Apple to execute • Code signature verification is at both load time and runtime • i. OS has made great gains in terms of its security model 11

Hacking Your i. OS Jailbreaking • Jailbreak: The process of taking full control of an i. OS-based device – Allow for using third-party apps – Expose yourself to a variety of attack vectors • Boot-based Jailbreak – Obtain the firmware image (IPSW) – Switch the device to Device Firmware Update (DFU) mode – Install the IPSW file image to the device • Remote Jailbreak – Load a specially crafted PDF into the web browser, Safari, to take the control of the browser, and then the operating system 12

Hacking Other’s i. OS Vulnerabilities in i. OS • Malware infection: Jailbreak. Me 3. 0 – Keep your operating system and software updated with the latest patches • SSH attack: i. Kee Attacks! – Don’t jailbreak your i. Phone – Change the default credentials for a jailbroken device • The FOCUS 11 Man-in-the-Middle Attack – Update your device and to keep it up to date – Configure the i. OS device to “Ask to Join Networks” • App store malware: Handy Light, Insta. Stock – Apps should be installed only when absolutely necessary and only from trustworthy vendors • Vulnerable apps: bundled and third-party (not on the app store) – Keep your device updated with the latest version of i. OS, and keep apps updated to their latest versions • Physical Access – Ensure that all sensitive data on the device has been encrypted 13

Summary • Adapt the behavior and configuration of the device to your purpose/data after evaluation • Enable device lock • Keep physical control of the device • Enable wipe functionality as appropriate using local or remote features • Install security software • Leave the device home when traveling 14

Homework Ch 11 Due: in printed hardcopy (format: problem, solution with explanation, screen dumps) 1. 2. 3. 4. 5. 6. (60 points) Android Debug Tool 1) 2) 3) Install Android SDK. Connect an Android device or emulator to the host which runs DDMS in the SDK. Dump and explain contents output by logcat in DDMS. (40 points) Select an Android device or emulator (e. g. the one in Android SDK, Bluestacks, and so on), root it. It is recommended to root on an Android emulator to avoid turning your phones "bricked". (20 points) Use document management app (e. g. Root Explorer) to add/remove apk files to/from the folder “/system/app/” in a rooted Android device or emulator, and observe what happens. (20 points) Install the app, Ad. Block, in an rooted Android device or emulator and explain how it blocks Ads. (20 points) Install a root-dependent app (except Ad. Block) to a rooted Android device or emulator and explain why it needs a root system. (20 points) Select one version of i. OS, survey how to jailbreak it, and list the steps. 15