FORTHs Honeypots CIPSEC workshop Frankfurt 16102018 Manos Athanatos



- Slides: 16

FORTH’s Honeypots CIPSEC workshop Frankfurt 16/10/2018 Manos Athanatos, FORTH Co-funded by the Horizon 2020 Framework Programme of the European Union 1

Honeypot - What is it? ■ A non production computer resource whose task is to be probed, attacked, compromised or accessed in any other unauthorized way. ■ It could be: ■ A piece of information/data ■ A service ■ An application ■ An entire system ■ It has: ■ No ordinary users ■ No regular services ■ Like an “undercover” computer which is built to be an “easy” target for the attacker and waits to be compromised! ■ A trap for attackers

Honeypot - How it works? ■ Honeypots are deployed in the network ■ Mimic the behavior of a server ■ Listen to an unused IP range ■ A possible attacker probes the unused IPs for services ■ Honeypots reply and interact with the entity ■ Entities attempting to communicate with honeypots, are by default suspicious ■ Activity between entities and honeypots is monitored: ■ Commands executed ■ Files downloaded ■ Links visited ■ Attacker IP is blacklisted to prevent potential attacks ■ Firewalls can be updated to block traffic from this IP address

Honeypots Classification Type of attacked resources Indicates whether the honeypot’s resources are exploited in server or client mode: ■ Server Side Honeypots ■ Act like a real server ■ Mimic network services ■ Listen on their standard ports ■ Monitor any connections initiated by remote clients ■ Detect scanning worms or manual attack attempts ■ Client Side Honeypots ■ Employ a set of client applications (e. g. web browser) ■ Connect to remote services ■ Monitor the activity and the remote content ■ Detect malicious behavior and content online

Honeypots Classification Level of interaction Indicates whether the honeypot’s resource is a real one, an emulated one or of a mixed type: ■ Low Interaction Honeypots ■ Resources are emulated ■ Services (for server side honeypots) ■ Applications (for client side honeypots) ■ High Interaction Honeypots ■ Provide real OS, services and applications ■ Hybrid Honeypots ■ Combine both low and high interaction honeypots

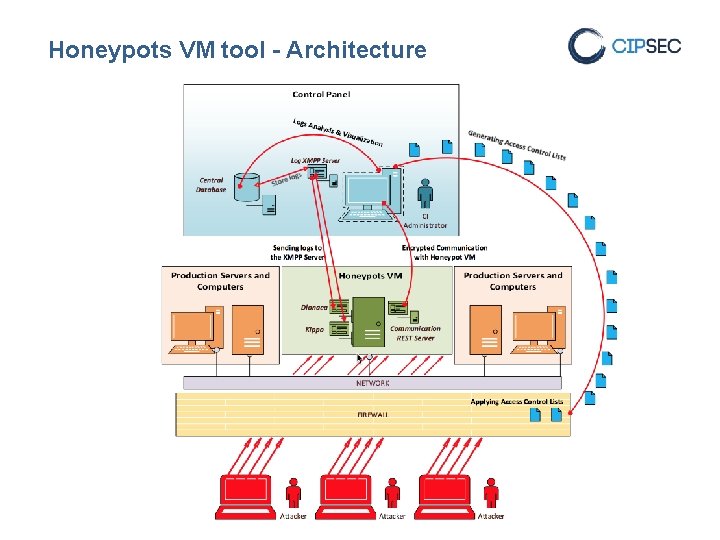
Honeypots VM tool - Components ■ Ubuntu VMs with pre-installed software ■ Dionaea Honeypot ■ DDOS tool ■ ICS/SCADA honeypot ■ Kippo SSH Honeypot ■ REST API server for remote access ■ Communication with the control panel over SSL ■ Logs aggregator XMPP server ■ Central Postgre. SQL database ■ Incidents stored in a unified format ■ Web based control panel ■ Remote administration of VMs ■ Visualization of attacks ■ Monitoring of honeypots’ VM performance ■ Extra features include: ■ LDAP authentication for users ■ Delivery of personalized alerts via email in PDF format

Dionaea Honeypot ■ Dionaea is a low interaction honeypot ■ Uses Python to emulate well known services ■ HTTP, HTTPs, FTP, TFTP, SMB, MSSQL, My. SQL ■ Accurate implementation of the Server Message Block (SMB) protocol ■ Providing share access to printers and files (port 445) ■ Popular target for worms and bots to spread ■ Modular architecture ■ New protocols can be emulated and added ■ Supports IPv 6 ■ Good performance and stability ■ Can monitor many IP addresses simultaneously

Kippo Honeypot ■ Kippo emulates the SSH service ■ Provides high level accuracy ■ Implemented in Python ■ Emulates a Debian filesystem ■ Provides content for some files (e. g. /etc/password) ■ Stores all files that are downloaded ■ Simulates wget and curl commands ■ Stores all commands executed ■ Enables the analyst to replay the commands ■ Good performance and stability ■ Can monitor many IP addresses simultaneously

ICS/SCADA Honeypot ■ CONPOT emulates SCADA Services ■ Supports 12 known protocols including modbus, http, bacnet, ftp, enip, ipmi, s 7 comm and more ■ Basic emulation capabilities ■ Implemented in Python ■ Modified for CIPSEC to provide logging via syslog ■ Easy to configure/use ■ Low logging capabilities

FORTH’s DDo. S Tool ■ Detects Do. S amplification attack attempts ■ Able to monitor attacks targeting multiple protocols such as: DNS, Net. BIOS, NTP, SNMP and more ■ Provides syslog output to the ATOS XL-SIEM ■ Visualisation of the detected events to the unified CIPSEC dashboard

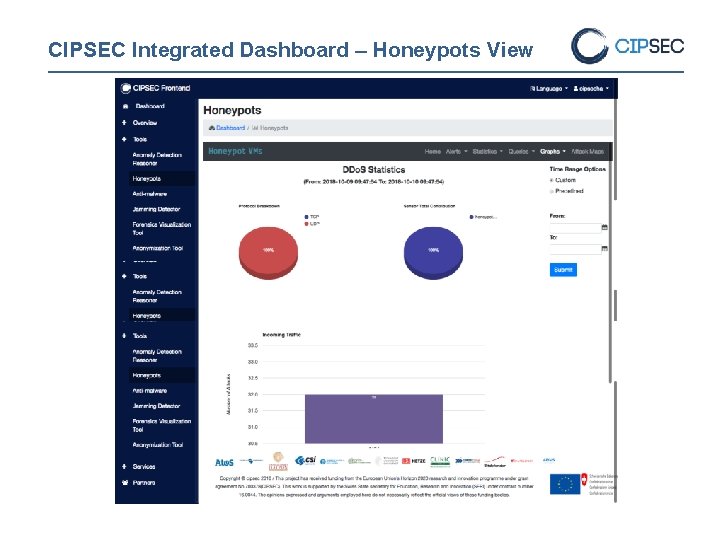
Honeypots’ VM tool - Workflow ■ Security Administrator Initialize the Honeypots’ VM in the network that needs to be protected. ■ It can choose which honeypots to enable( Dionaea Honeypot, DDOS tool, ICS/SCADA honeypot, Kippo SSH Honeypot ) ■ Through the Control panel initializes the Honeypots’ VM ■ Applies a unique ID to the sensor ■ Configures the monitoring IP Dark Space ■ Starts all services ■ Automated updated and patching mechanism ■ Honeypots monitor the network for attacks ■ Attackers discover services and try to compromise them ■ Honeypots track their activity ■ Honeypots logs are sent to ATOS XL-SIEM and stored to a database ■ CIPSEC Integrated Dashboard visualizes the attacks

Honeypots VM tool - Architecture

CIPSEC Integrated Dashboard – Honeypots View

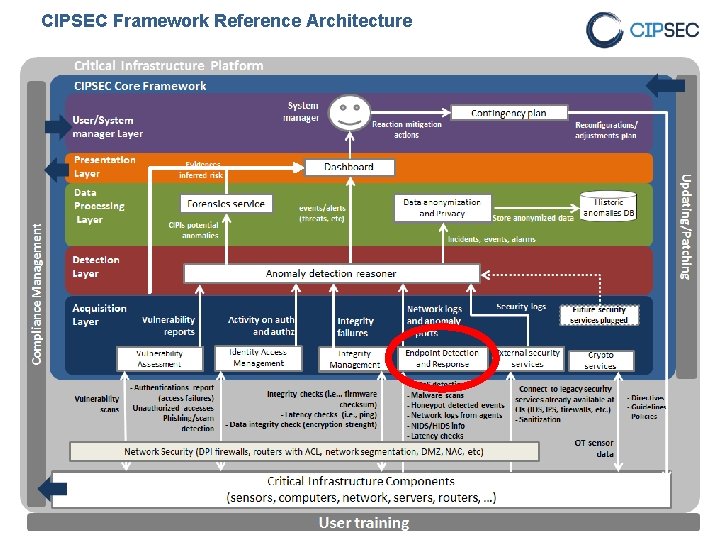
CIPSEC Framework Reference Architecture

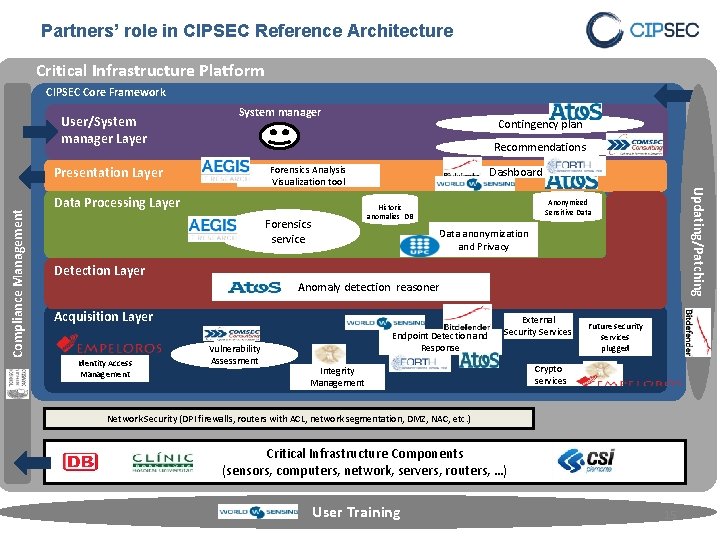
Partners’ role in CIPSEC Reference Architecture Critical Infrastructure Platform CIPSEC Core Framework User/System manager Layer System manager Recommendations Forensics Analysis Visualization tool Presentation Layer Data Processing Layer Dashboard Anonymized Sensitive Data Historic anomalies DB Forensics service Updating/Patching Compliance Management Contingency plan Data anonymization and Privacy Detection Layer Anomaly detection reasoner Acquisition Layer Identity Access Management Vulnerability Assessment Endpoint Detection and Response External Security Services Integrity Management Future security services plugged Crypto services Network Security (DPI firewalls, routers with ACL, network segmentation, DMZ, NAC, etc. ) Critical Infrastructure Components (sensors, computers, network, servers, routers, …) User Training 15

Thanks for your attention! Questions? Contact: Project Coordinator Antonio Álvarez ATOS antonio. alvarez@atos. net Technical Coordinator Sotiris Ioannidis FORTH sotiris@ics. forth. gr www. cipsec. eu @CIPSECproject https: //www. linkedin. com/in/cipsec-project/ https: //www. youtube. com/channel/UCekxic. SFAw. Zd. IPAV 3 i. LHtt g CIPSEC Technical Review Meeting Barcelona 22/11/2017 16
 Honeypots and honeynets
Honeypots and honeynets Frankfurt horizontal düzlemi
Frankfurt horizontal düzlemi Frankfurt parliament
Frankfurt parliament Walter benjamin escuela de frankfurt
Walter benjamin escuela de frankfurt Reunidos na escola de frankfurt filosofos alemaes
Reunidos na escola de frankfurt filosofos alemaes Plano de frankfurt medicina
Plano de frankfurt medicina Housing first frankfurt
Housing first frankfurt [email protected]
[email protected] Escuela de frankfurt en la actualidad
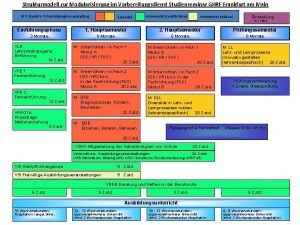
Escuela de frankfurt en la actualidad Studienseminar frankfurt ghrf
Studienseminar frankfurt ghrf Ofd hcc wiesbaden
Ofd hcc wiesbaden Harnsteinmetaphylaxe
Harnsteinmetaphylaxe Hersch beker
Hersch beker Studienseminar frankfurt grundschule
Studienseminar frankfurt grundschule Freiherr-vom-stein-gymnasium
Freiherr-vom-stein-gymnasium Frankfurt bip
Frankfurt bip Write a note on frankfurt parliament
Write a note on frankfurt parliament