Ethics Privacy Safety Source Ethics in Computing How













- Slides: 16

Ethics, Privacy, & Safety

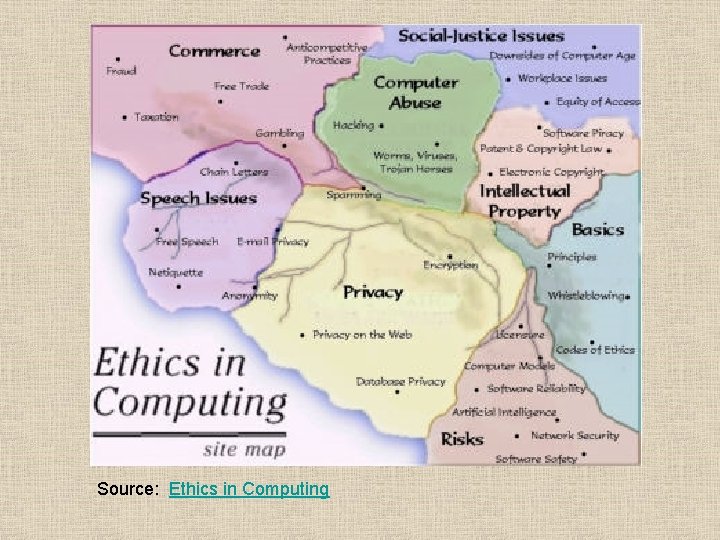
Source: Ethics in Computing

How do People Learn to Engage in Ethical Behavior? • A recognition that an action has caused harm • Social disapproval • Punishment by authority Source: Computer Ethics, Etiquette & Safety

Information and communication technologies affect ethical behavior • Technology does not provide tangible feedback • Technology allows us to become invisible Source: Computer Ethics, Etiquette & Safety

Eight Ethical Decision-Making Strategies • Golden Rule Test • Trusted Adult Test • Is There a Rule? Test • Front Page Test • If Everybody Did It Test • Real World Test • Gandhi Test • Check Inside Test Source: Computer Ethics, Etiquette & Safety

Universal Rationalizations • • The finger of blame (“She started it…”) Follow the crowd (“Everyone does it…”) If I only had a brain (“He told me to…”) No harm no foul (“Nobody got hurt”) It’s only a little bit wrong… Good intentions (“It’s for a good cause…”) “No one ever gets caught…” “Things have changed…” Source: Computer Ethics, Etiquette & Safety

What Can You Do? • • • Play by the Rules Keep It Private Look Your Best Don’t Pollute Remain Cool Under Fire • Read with Your Eyes Open • Credit the Source • Respect the Creator • Watch Where You are Looking • Don’t Take Candy from Strangers • Don’t Go Where You Don’t Belong Source: Computer Ethics, Etiquette & Safety

Web Resources • Cyber. Ethics – Cyber. Smart Curriculum – Copyright – Computer Virus Myths, Hoaxes, Urban Legends, Hysteria • Cyberethics, Cybersecurity and Cybersafety

The Ten Commandments of Computer Ethics 1. Thou shalt not use a computer to harm other people. 2. Thou shalt not interfere with other people's computer work. 3. Thou shalt not snoop around in other people's computer files. 4. Thou shalt not use a computer to steal. 5. Thou shalt not use a computer to bear false witness. 6. Thou shalt not copy or use proprietary software for which you have not paid. 7. Thou shalt not use other people's computer resources without authorization or proper compensation. 8. Thou shalt not appropriate other people's intellectual output. 9. Thou shalt think about the social consequences of the program you are writing or the system you are designing. 10. Thou shalt always use a computer in ways that ensure consideration and respect for your fellow humans. Computer Ethics Institute A project of the Brookings Institution http: //www. brook. edu/its/cei_hp. htm

What About Privacy? • • Computer Safety Secure e-mail Identity Theft Credit Reports Spam Filters Anti-Virus Spyware Removal • • Privacy Software Ad Blockers Firewalls Encryption Parental Control Key Loggers Privacy Fence

Web Resources • Protecting your Privacy on the Internet • Internet Privacy Resources

Let’s Stop and Play… • Privacy Playground • Cybersense and Nonsense • Jo Cool or Jo Fool

Cyberbullies • March 08, 2005 – USA Today • "Cyberbullies, mostly ages 9 to 14, are using the anonymity of the Web to mete out pain without witnessing the consequences, " reports USA Today. • Half of 3, 000 U. S. children surveyed the past six months said they or someone they know have been victims or guilty of cyberbullying, Wired Safety says. • Bullying isn't just for large males. Now anyone, male or female, with minimal technical skills can get into the act. But victims still tend to be kids seen as "different. "

Let’s explore… • Quiz • Think about this… • Suggestions

Safety • • Playing It Safe Keeping Children Safer Surf Swell Island Cyber. Netiquette Comix Get. Net. Wise Safe. Kids and Safe. Teens Netsmartzkids. org

“Integrity is doing the right thing, even if nobody is watching. ” Anonymous