ICT ETHICS 1 Privacy ICT privacy generally means





















































































- Slides: 91







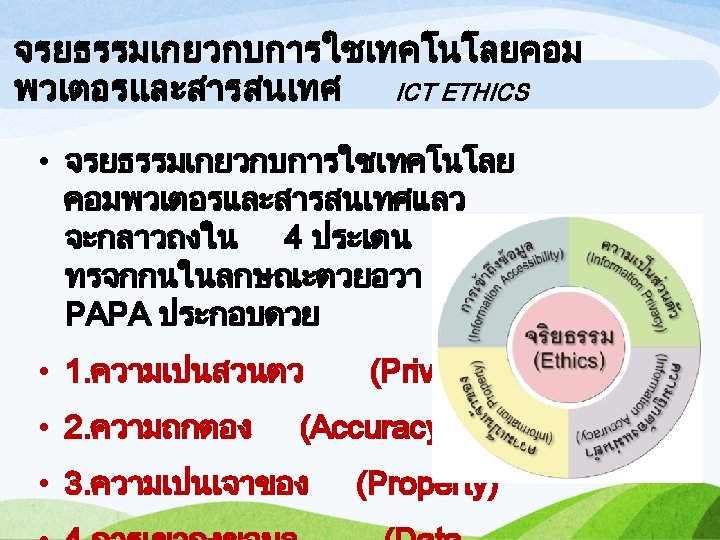
จรยธรรมเกยวกบการใชเทคโนโลยคอม พวเตอรและสารสนเทศ ICT ETHICS • 1. Privacy: ICT privacy, generally means; rights of being isolated or the ownership of individual to control their data accessibility to other, this rights includes the ownership of individual, group of people, and organizations. For instance, the e-mails and user’s profile for accessing a website. 7


จรยธรรมเกยวกบการใชเทคโนโลยคอม พวเตอรและสารสนเทศ ICT ETHICS Obvious privacy intrusions are; • 1. 1 Email accessibility and file-saving on a computer along with stored and exchanged profiles of users on the internet services. • 1. 2 Using technologies to trail or closely observe a person’s behavior such as; a company uses computers to monitor and watch the employees’ operation till it immorally intrudes their privacy. • 1. 3 Using customers’ information from many sources for commercial and marketing benefits. • 91. 4 Collecting customers’ contacts and details to create customer’s database and sell it to others companies.




จรยธรรมเกยวกบการใชเทคโนโลยคอม พวเตอรและสารสนเทศ ICT ETHICS 2. Information Accuracy To manage information to be accurate and reliable, the administrators need to check and verify the information before uploaded to the server and need to frequently update to make the information to be as up-to-date as possible. Besides, admin should provide users authority to check and correct their profiles such as; 13





ความลบทางการคา Secrets) (Trade . 1 Trade Secrets means all the intellectual properties such as chemical formula, production plans, product design, tools which are not publicized to keep them secret. The owners can patent for the copyright which the regulations can be vary by the places or states of registration. Example: - patent of carbonate drinks formula - patent of chili paste ingredients A part of details is informed to the customers but all details will not be publicized.


ลขสทธ (Copyright). 2 Copyright is the ownership of creations such as; literatures, music, arts which are not allowed to copy by others except formal permission from authorities even if the creations are exhibit over the internet. According to the law, the copyright will exist for 50 years after the creation’s first


งานสรางสรรคทมลขสทธ Copyright Creations • Literatures such as; books, booklets, writings, publications, computer programs. • Dramatic works such as; choreography, dancing, acting. • Artistic works such as; painting, sculptures, printings, architectural designs, and photos. • Musical works are including with the lyrics and melodies along with music compositions and rearrangement. • Audiovisual works such as; videotapes, laser discs, etc. • Motion pictures.


สทธบตร (Patent) • . 3 Patent means the official letter issued by the government to the person for the protection of the innovative creations. Patent will last 20 years from the registration date. • Unlike trade secrets, patents and copyright aim to protect the products which are manufactured for customers and the information which are publicized.




• Distributing copied software among friends is caution because the programs might be copyright and should acknowledge the user’s authority, for example; • Copyright or Software license - the license is included with the product payment and authority is under conditions. • Shareware – you can try the software before you buy.


จรยธรรมเกยวกบการใชเทคโนโลย คอมพวเตอรและสารสนเทศ 4. Data Accessibility The right to access the programs or computer systems is usually controlled by the rank of users to protect the system and other users’ profile. Therefore, the development of computer systems concerns the security and It has been designed to secure user accessibility. The access from unauthorized user is considered a violation as well as personal 30


อาชญากรรมคอมพวเตอร crimes Computer Using computers as a tool for crime. 1. to steal credit card numbers. 2. To impersonate other people, act as one another by using his/her identities such as ID number. 3. The computer scam is done by deceiving others through computers such as, text messaging or fault ads.


ลกษณะของอาชญากรรม คอมพวเตอร Computer Crimes Samples of 3 computer crimes; 1. Accessing and using one’s computer without permission. 2. Harassment or data deletion. 3. Identity and computer hardware theft.



. 1ไวรสคอมพวเตอร Virus( (Computer Is a program written for making some modifications to other programs. The number of infected programs will increase rapidly. They can be embedded in files or storage devices such as hard disks. For the damage will be divided into two types. 1. Virus which shows messages or slow down your computer. But it doesn’t destroy the data. 2. Damages from virus which causes the system destruction includes with files deletion or the computer shutdown.


. 1ไวรสคอมพวเตอร Virus( (Computer viruses are divided into 3 types: 1. Boot sector viruses (system virus) will run when the computer starts. 2. File or program Viruses. The viruses are embedded in the various files, mostly with the extension “. exe” and “. com” The files are usually infected by downloading from the Internet or opening email attachments. 3. Macro viruses work on programs that use macros such as word processor and spreadsheet.


. 2เวรมหรอหนอนอนเทอรเนต (Worm( • A computer program that can spread itself like a virus but a bit different that viruses need the command to trigger while worms are able to spread from computer to computer via email and the Internet. • The uniqueness of worms is they can duplicate itself immensely in just a few minutes. • The samples of well-known worms are "Nimda", "W 32. Sobig", "W 32. bugbear", "W 32. blaster" and "Love Bug" etc.



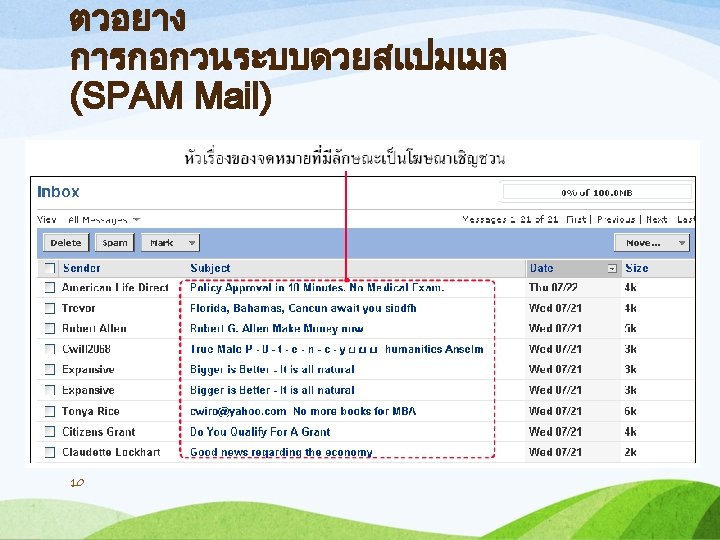
. 4ขาวหลอกลวง (Hoax) Send a message to each other like a chain letter, to misunderstand others by using psychological techniques such as; • "Virtual Card for You" • "Life is Beautiful“ • "FAMILY PICTURES“ • Please do not drink. . . • Beverage brands. . . • Please do not use mobile brand. . .



ขอสงเกตเพอการตรวจสอบวาเครองคอมพวเตอร ไดรบไวรส เวรม และมาโทรจน หรอไม Observations to check whether your computer is infected by viruses, worms or Trojan horses or not. 1. unknown text or images are shown on the screen. 2. Unusual noise or music are sometimes played. 3. Computer memory is lower than it should be. 4. Programs or files are missing even you did not delete them. 5. There is unknown program. 6. Unusually large file size. 7. Files or programs are malfunctioned.


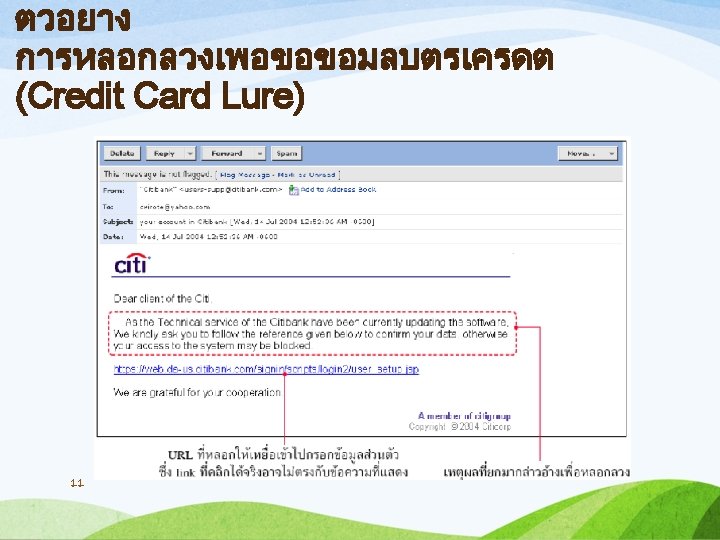
การขโมยขอมลและอปก รณคอมพวเตอร Identity theft, and computer equipment • Such as; unauthorized access to data or computer, stealing credit card numbers from the accounting database. • May be accessed externally or internally. • Protective devices and security should be installed and check the entry of visitors who access the system by


วธการปองกนการเขาถงขอมลแ ละคอมพวเตอร How to prevent access to information and computers. 1. The username, user ID, and password should not be simple and can be easily guess like birthday. 2. Using any other items to access like using ATM card to do banking transactions, this card is typically encrypted by a unique set of 4 -digit numbers as the password. The owner should realize of its importance and use more complicate numbers than date of birth or do not write the numbers onto the card.


ควรสราง password ทยากตอการคาดเดา และไมควรใหเครองจำ password You should create a password that is difficult to predict and avoid using password recognizing program. • Do not use any word in the dictionary. • Do not use any word related to us, such as telephone number, birthday, pet name, nickname, etc. • Do not write your password anywhere. • Do not tell your password to others for any reason. • Randomly use letters, numbers and special characters together. • Do not let your computer remember the


วธการปองกนการเขาถงขอมลและ อมพวเตอร Accessibility Protection 3. Using biometric devices to check the personal characteristics, to allow applications such as audio identification, fingerprint or palm-scan, signature, iris and face scan so the device will convert the personal biometrics into digital data for further biometric access comparison. If the information does not match, the computer will reject the login. ค


วธการปองกนการเขาถงขอมลและ วธการปองกนการเขาถงขอมลแ อมพวเตอร ละคอมพวเตอร Accessibility Protection ค 4. Callback system is a system which the user needs to identify the name and password to get access to the system. If the information is correct, it will automatically grant the user to access. Operating in this way will be more effective if the applicant uses computer or devices from the unchanged location (same phone number).


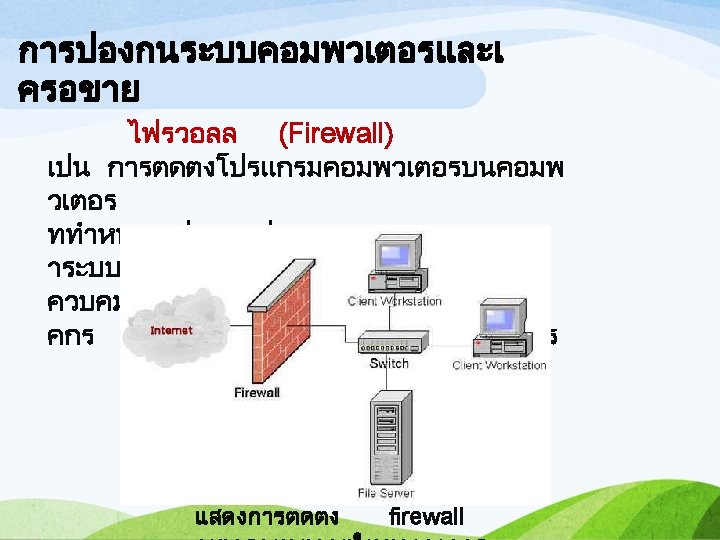
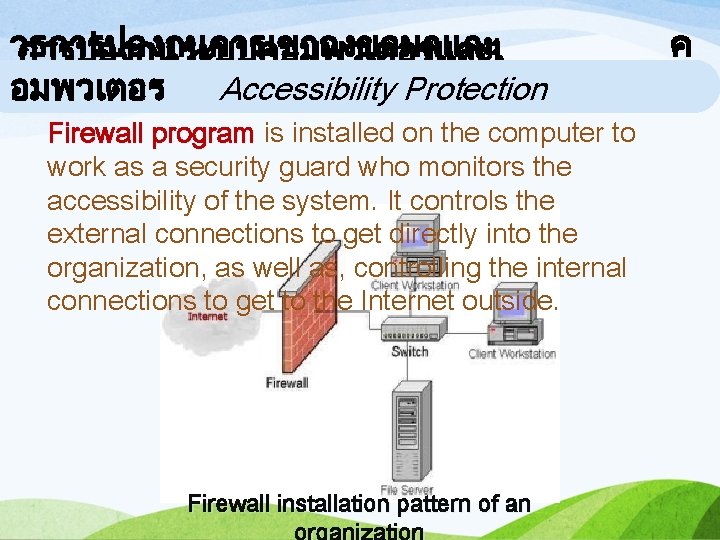
วธการปองกนการเขาถงขอมลและ การปองกนระบบคอมพวเตอรและเ อมพวเตอร Accessibility Protection ครอขาย Firewall program is installed on the computer to work as a security guard who monitors the accessibility of the system. It controls the external connections to get directly into the organization, as well as, controlling the internal connections to get to the Internet outside. Firewall installation pattern of an ค



การปองกนไวรสคอมพวเตอร Virus Protection 1. Never open stranger’s email, because of the high risk of being a virus or a spam. 2. Keep observing the topic of the email. Especially the attractive English subject. 3. Install antivirus software such as; Norton Antivirus, PC -cillin, and regularly update the virus database. 4. Follow and pay attention to the news about the virus. 5. Learn to be careful. Do not open email without a second thought, since the survey found that 70 to 80 percent of all email is spam and email viruses. 6. Follow the news about the prevention of harassment and destruction from Thai Computer Emergency


จรรยาบรรณในการใชงานคอมพวเตอร Ethics in computer professions Ethics means the Codes of Behavior that is established in each field of vocation to guarantee and promote the reputation and fame of members such as; the ethics of medical staffs, ethics teachers, ethics of journalists, etc. Each professionals associated with computer should respect and adopt the ethics to their occupation, such as; the ethics of systems analysts that the analyst should always keep the company's data low-profile – that the information is confidential, programmers should not write code or virus attached to the application that


จรรยาบรรณในการใชงานคอมพวเตอร อร Ethics in computer usages จรรยาบรรณในการใชคอมพวเตอร computer usages are as follows; ม ดงน Ethics in the 1. Must not use the computer to commit a crime or violate the rights of others. 2. Must not use the computer to harass others. 3. Must not spy or modify the documents or files of others without prior permission. 4. Must not use the computer to steal information. 5. Must not use the computer to create false evidence. 6. Must not use a computer to copy the copyrighted program. 7. Must not violate or use the unauthorized computer resources. 8. Must not use the computer to steal the work of others to be their own.


กฎหมายเทคโนโลยสารสนเทศ IT Act Why there need to be information technology legislation? 1. The advance of science and technology make people use more IT. 2. Law guarantees the reliability and confidence to do electronic transactions and trade over electronic commerce (E-Commerce E-Business). 3. Every organization is stepping to the Information society with paperless policy, in order to reduce the use of paper by using electronic data instead that make it easy to do the Electronic Data Interchange (EDI). 4. Doing business over the Internet more and more


กฎหมายเทคโนโลยสารสนเทศของไทย Thailand's Information Technology Law Cabinet has approved the information technology Law of Thailand on December 15, 1998, the Ministry of Science and Technology, in hands with the National Electronics and Computer Technology Center to induce 6 drafts of IT Laws include; Act of Electronic Transactions. Act of Electronic Signature. Act of Computer Crimes. Act of Personal Information Privacy. Act of Electronic Funds Transfer. Secondary Legislation Act, Section 78 of the Constitution of Thailand.








ตวอยางคดอาชญากรรมทาง คอมพวเตอร • Theft of money from others’ bank account • Theft of corporate secrets stored in the computer • Virus spread by sending, sharing malicious programs to others • The use of computers in counterfeit documents and sabotage • Stealing the domain name without shapes • Piracy


. 4 กฎหมายคมครองขอมลสวนบ คคล Protection of personal information. The information in digital photo can be published and distributed quickly. Forwarding the broadcast could affect the right of privacy and against the Personal Information Protection Act. - U. S. and European privacy laws prohibit the act of seizing or stealing the data sent over the network unless given government official permission. In the past, Thailand has one of the electronic commerce website which was hacked by a UK




าตรา 78 Secondary legislation Law, in the Section 78, in the section 78 of the Constitution of the Kingdom of Thailand on the state to decentralization and local self-reliance and decision making on their own local affairs, economic, and infrastructure development. Also the information system infrastructure that cover the local area thoroughly and equally.


• Current IT law was enacted, it is the Act of electronic Transaction 2002, 2002 which combined 2 laws of the electronic commerce and the electronic signature, on April 3, 2002 • The law greatly benefits both the electronic customers and the legal officials because the law accepts electronic evidences in the hearing procedure.


• Current problem in Thailand is the law is unable to guarantee adequate electronic protection and it is the main reason making the investors and businessperson to do any transactions over the internet. Because of the inefficiency of the system security and the uncertainty of interlude and intervention from outsiders, including with the fear of intellectual property violations(piracy), A stronger IT law is very necessary for electronic commerce to grow in Thailand.


สรป Conclusion • IT and IT system are important for modern lifestyle, so there must be the protection system to secure the users’ safety which can be done three ways; protect the computers in the organization, secure the safe connection, and protect the privacy. These concerns are similar in the main purpose is to protect from outside intrusions such as; virus, hacking, stealth, which cause a lot of damages to the users and information system.
