DYNAMIC SECURITY EXPANDED UNC CHAPEL HILLS APPROACH TO


















- Slides: 33

DYNAMIC SECURITY EXPANDED UNC CHAPEL HILL'S APPROACH TO ACCESS MANAGEMENT VIA PEOPLESOFT DYNAMIC SECURITY SESSION: 6163 OCT 04, 2016 10: 00 AM

Your Presenter ROGER M. RICE University of North Carolina at Chapel Hill Enterprise Applications Security Team Lead Mathematical Sciences Computer Science, B. S. University of North Carolina at Chapel Hill

University of North Carolina at Chapel Hill Student Population 18, 350 undergraduates 10, 785 grad/professional students Faculty and Staff 3, 696 faculty 8, 267 staff Degree Programs 70+ majors and minors 68 doctoral programs 112 master's programs

University of North Carolina at Chapel Hill Nation’s first public university Ranked as the best value in public higher education Strong, diverse student body Unique academic opportunities Leading research university Carolina Covenant makes college possible for low-income students Annual University budget: $2. 4 billion (operating expenses in fiscal 2013 -14)

University of North Carolina at Chapel Hill In Production: People. Tools 8. 53 PS Interaction Hub 9. 1 PS Campus Solutions 9. 0 PS Financials 9. 1 PS HCM 9. 1

Overview At the University of North Carolina, Dynamic Security has been used to control access within our individual People. Soft applications as well as controlling access between People. Soft Applications. We have used Dynamic Security to leverage access in external systems. Additionally, Dynamic Security has also been used to control security after a system refresh.

Agenda/Contents Dynamic Security Basics Dynamic security to control user access externally between 2 People. Soft applications Dynamic security to control user access externally between a People. Soft application and an external application Dynamic security to control user access after a People. Soft application system refresh

DYNAMIC SECURITY EXPANDED: Dynamic Security Basics

Dynamic Security Basics – People. Soft Role Assignment The Security Administrator manually assigns the role to a user profile. These users are static role members. Role Membership can also be assigned based on role rules. A batch process is run that will assign roles to user profiles that match the criteria for these rules. These users are dynamic role members. Dynamic role assignment greatly reduces security administrative tasks as well as aids in eliminating the security administrator bottleneck.

Dynamic Security Basics – Dynamic Role Assignment Dynamic Role Rules: • • • PS/Query People. Code Directory (e. g. LDAP) The app engine program DYNROLE_PUBL assigns dynamic roles by using the logic in the role rule to obtain a list of operator IDs.

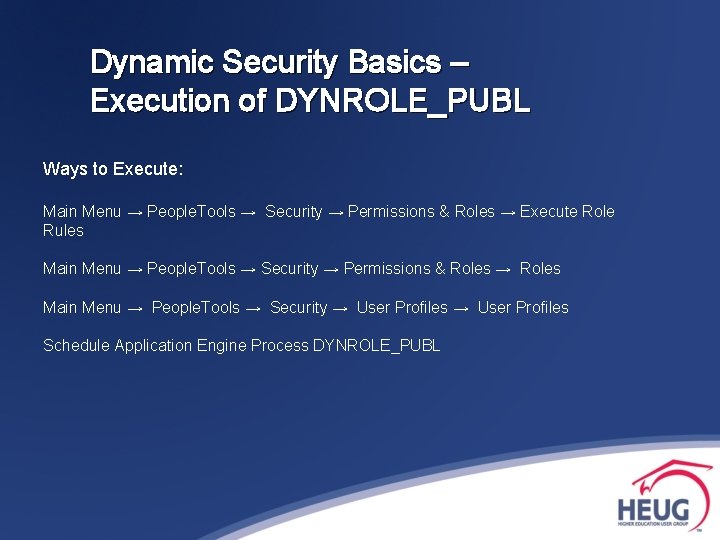
Dynamic Security Basics – Execution of DYNROLE_PUBL Ways to Execute: Main Menu → People. Tools → Security → Permissions & Roles → Execute Role Rules Main Menu → People. Tools → Security → Permissions & Roles → Roles Main Menu → People. Tools → Security → User Profiles Schedule Application Engine Process DYNROLE_PUBL

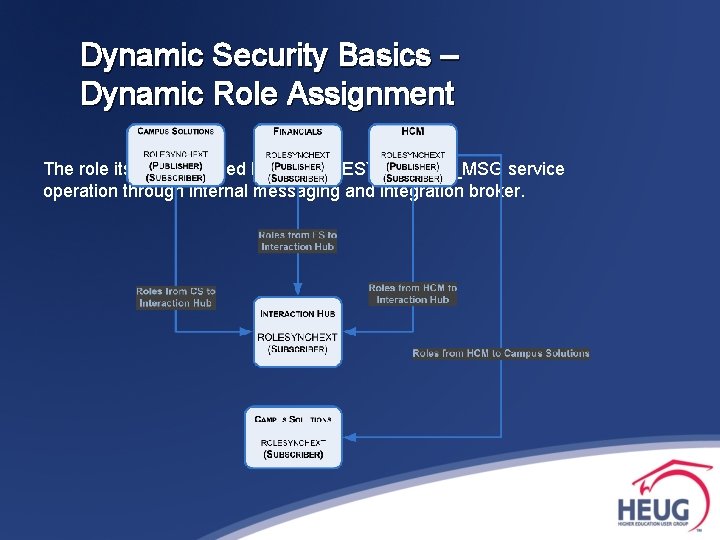
Dynamic Security Basics – Dynamic Role Assignment The role itself is assigned by the ROLESYNCHEXT_MSG service operation through internal messaging and integration broker.

DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications

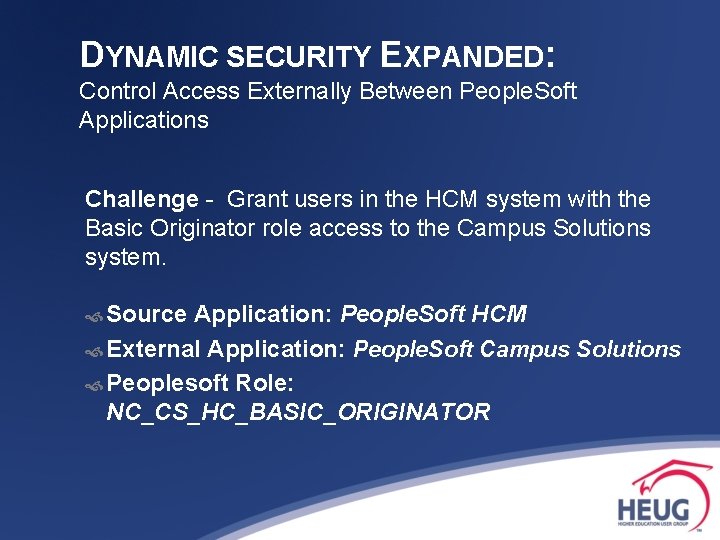
DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications Challenge - Grant users in the HCM system with the Basic Originator role access to the Campus Solutions system. Source Application: People. Soft HCM External Application: People. Soft Campus Solutions Peoplesoft Role: NC_CS_HC_BASIC_ORIGINATOR

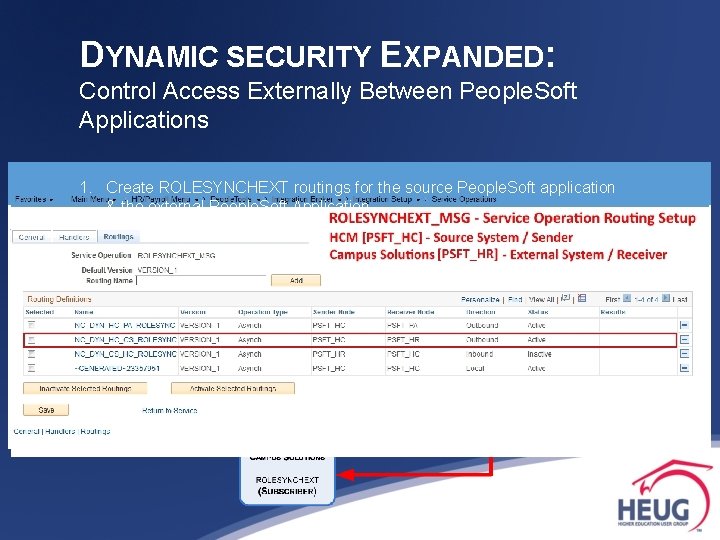
DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications 1. Create ROLESYNCHEXT routings for the source People. Soft application & the external People. Soft Application

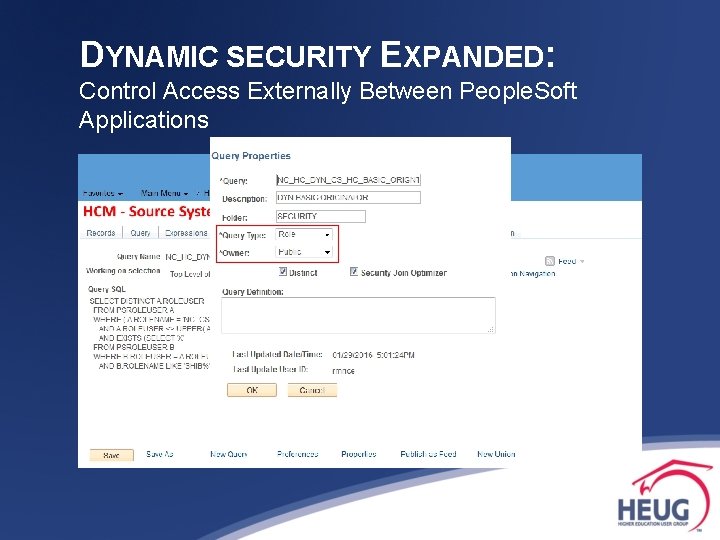
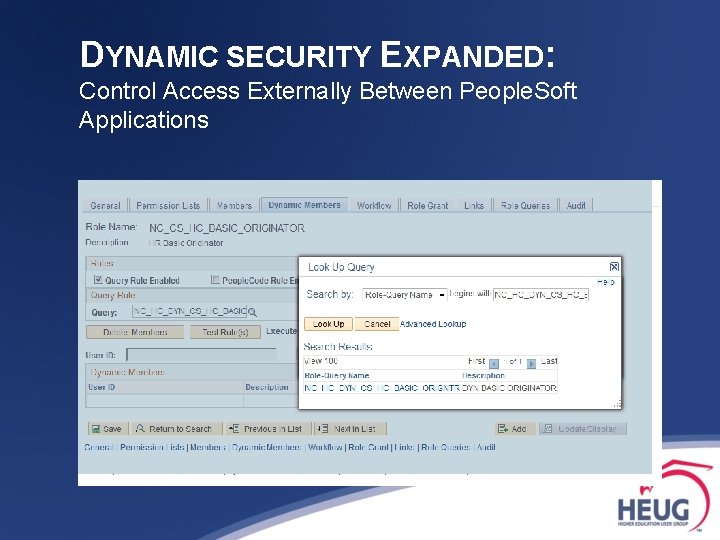
DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications 2. Create role rule for Dynamic Role in source system. § Dynamic Role Rules: ∙ PS/Query ∙ People. Code ∙ Directory (e. g. LDAP)

DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications 3. Create role [if new] & apply role rule in source system.

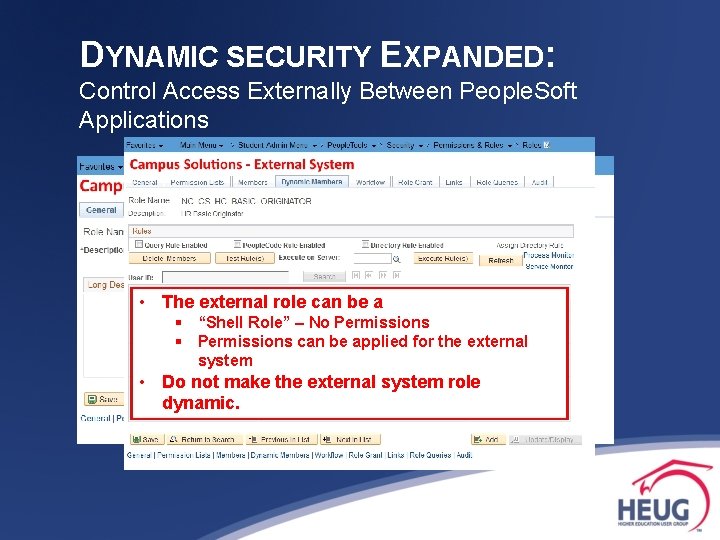
DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications 3. Create role [if new] & apply role rule in source system. 4. Create role in the external system with the same name as the source system. • The external role can be a § “Shell Role” – No Permissions § Permissions can be applied for the external system • Do not make the external system role dynamic.

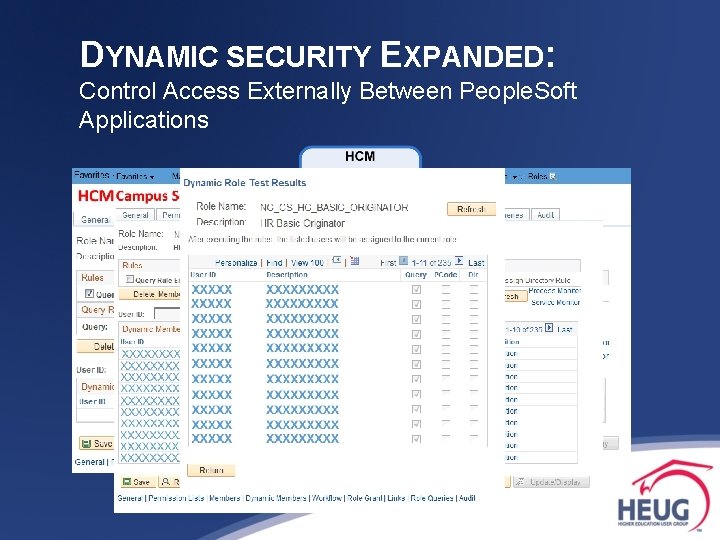
DYNAMIC SECURITY EXPANDED: Control Access Externally Between People. Soft Applications 3. Create role [if new] & apply role rule in source system. 4. Create role in the external system with the same name as the source system. 5. Test & Run Dynpub App Engine from Source

DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application

DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application Challenge - Grant users to the Web Travel, Fina$eer & Purchase Card applications based on People. Soft FSCM access. People. Soft Application: People. Soft FSCM External Applications: Web Travel, Fina$eer & Purchase Card

DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application • System for creating and maintaining institutional groups in a central repository • Goal: create a group once, but use it as often as necessary in as wide a range of systems as possible • At UNC: • Use Grouper for grouping users in one central repository • Sync grouper groups and their membership to LDAP/Shibboleth, Active Directory and many other systems For more information about the Grouper Toolkit go to: http: //www. internet 2. edu/products-services/trust-identity/grouper/

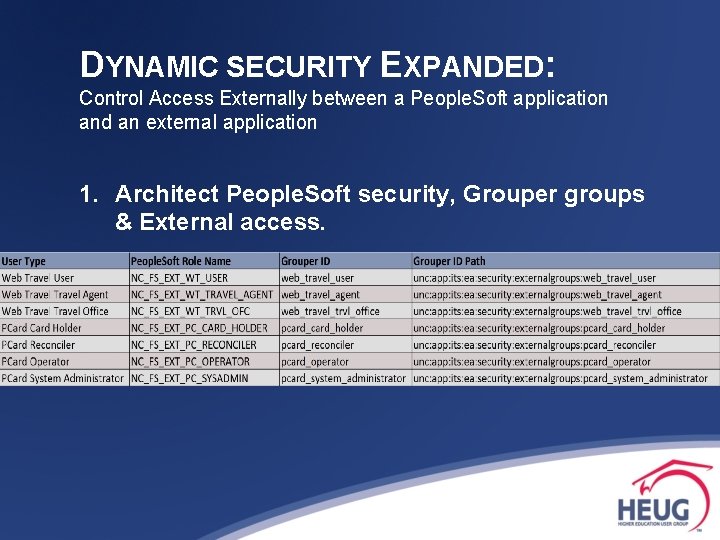
DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application 1. Architect People. Soft security, Grouper groups & External access.

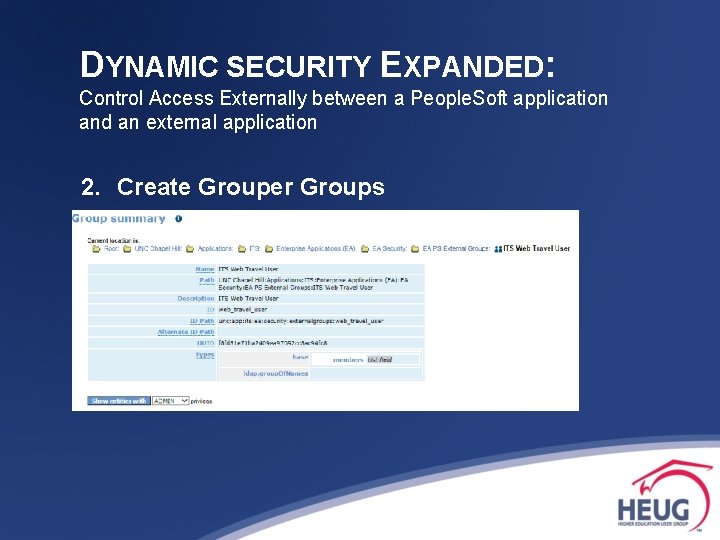
DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application 2. Create Grouper Groups

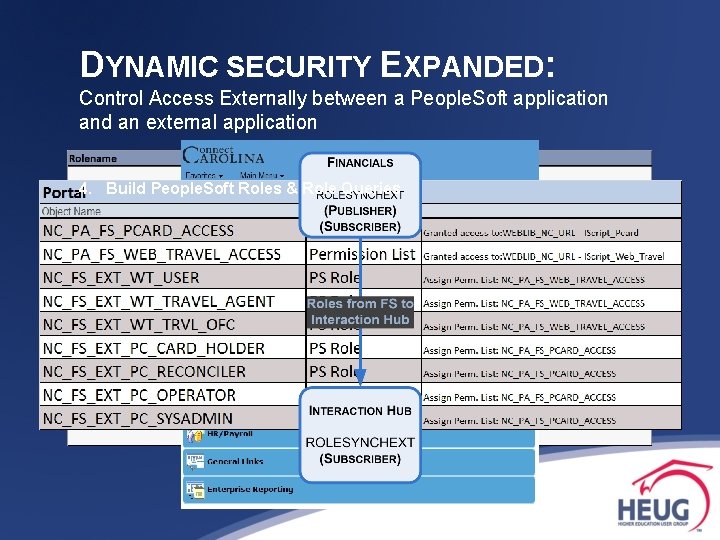
DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application 4. Build People. Soft Roles & Role Queries

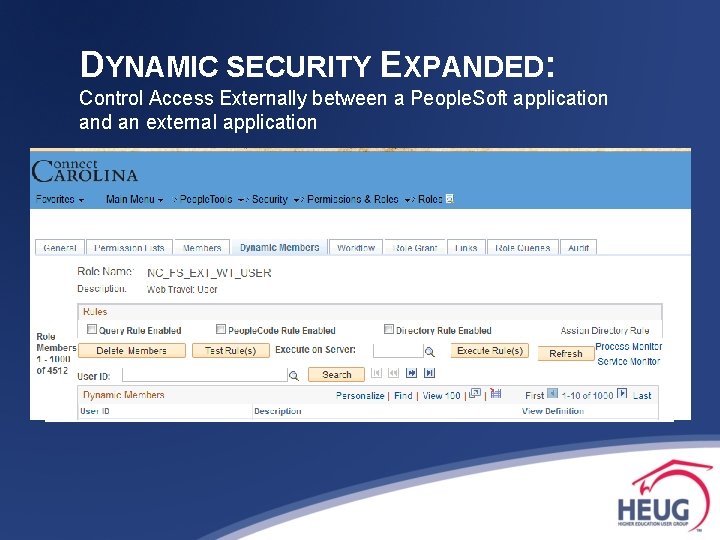
DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application

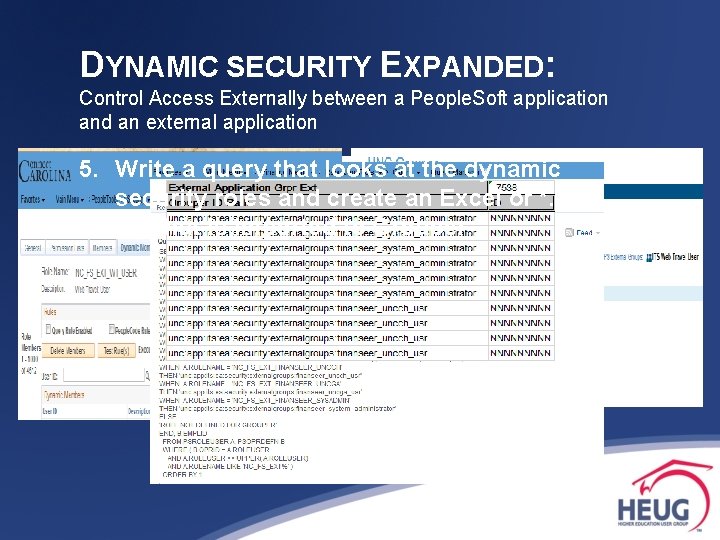
DYNAMIC SECURITY EXPANDED: Control Access Externally between a People. Soft application and an external application 5. Write a query that looks at the dynamic security roles and create an Excel or *. csv file that is imported to Grouper

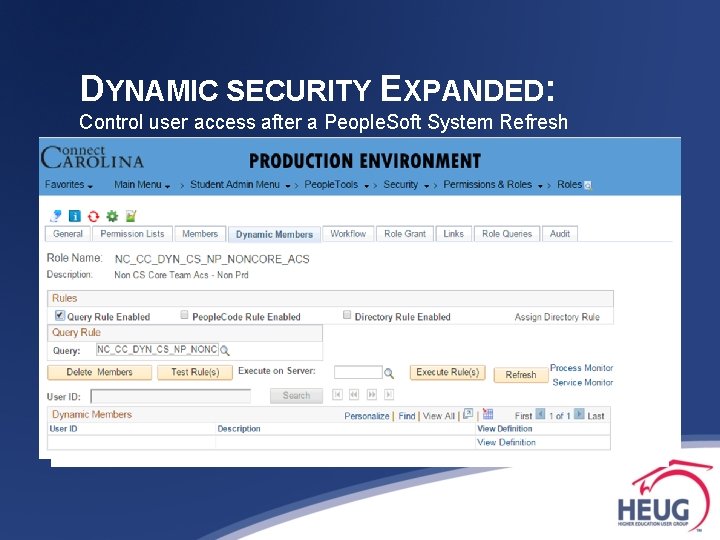
DYNAMIC SECURITY EXPANDED: Control user access after a People. Soft System Refresh

DYNAMIC SECURITY EXPANDED: Control user access after a People. Soft System Refresh Challenge - Grant users access to non-production environments without additional scripting based on Production security.

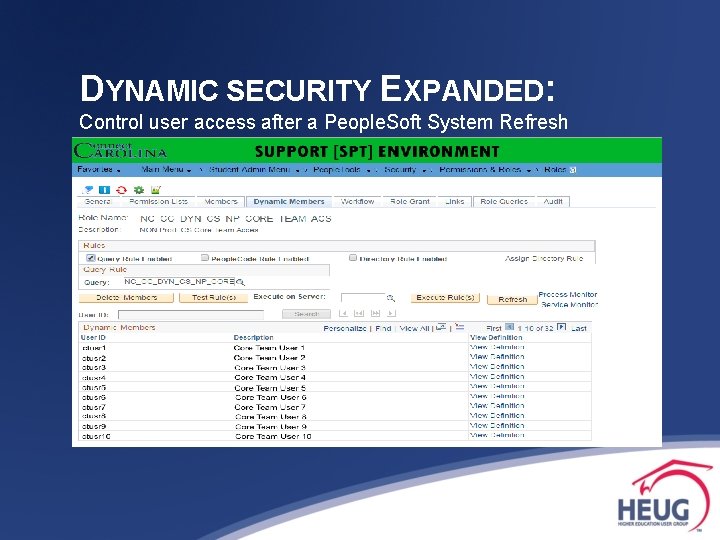
DYNAMIC SECURITY EXPANDED: Control user access after a People. Soft System Refresh

DYNAMIC SECURITY EXPANDED: Control user access after a People. Soft System Refresh

Questions?

Contact Information ROGER RICE SECURITY TEAM LEAD ENTERPRISE APPLICATIONS UNIVERSITY OF NORTH CAROLINA – CHAPEL HILL E-MAIL: roger_rice@unc. edu