DHCP Dynamic Host Configuration Protocol Goal allow host

- Slides: 17

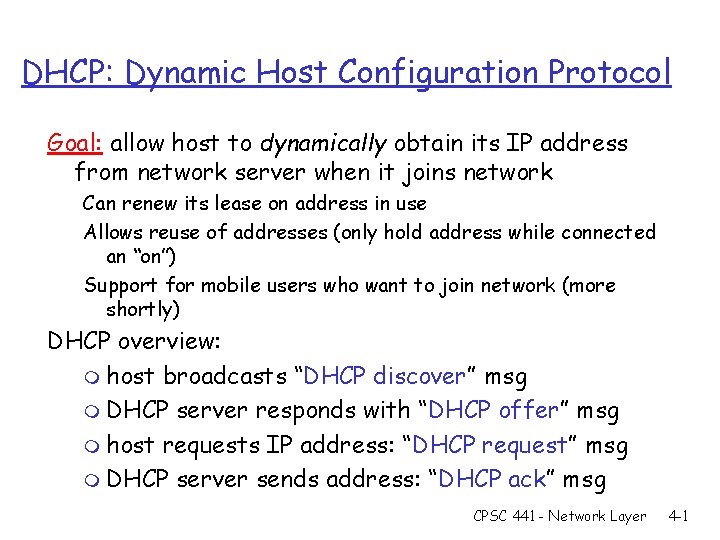
DHCP: Dynamic Host Configuration Protocol Goal: allow host to dynamically obtain its IP address from network server when it joins network Can renew its lease on address in use Allows reuse of addresses (only hold address while connected an “on”) Support for mobile users who want to join network (more shortly) DHCP overview: m host broadcasts “DHCP discover” msg m DHCP server responds with “DHCP offer” msg m host requests IP address: “DHCP request” msg m DHCP server sends address: “DHCP ack” msg CPSC 441 - Network Layer 4 -1

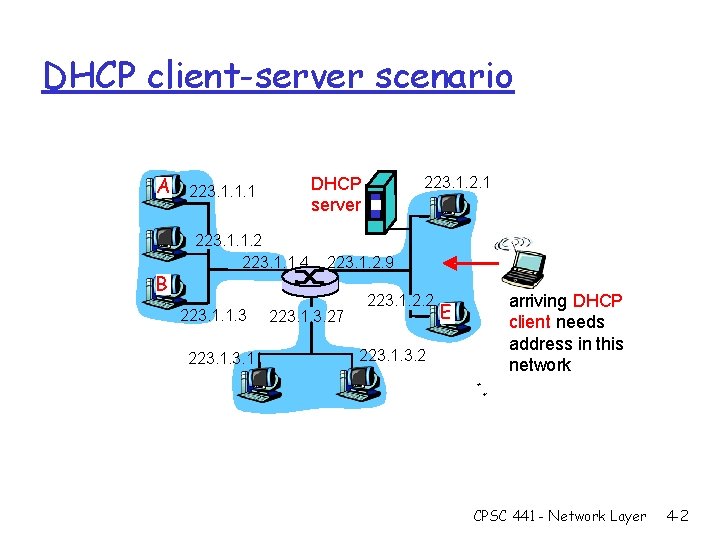
DHCP client-server scenario A B 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 DHCP server 223. 1. 1. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 223. 1. 3. 2 E arriving DHCP client needs address in this network CPSC 441 - Network Layer 4 -2

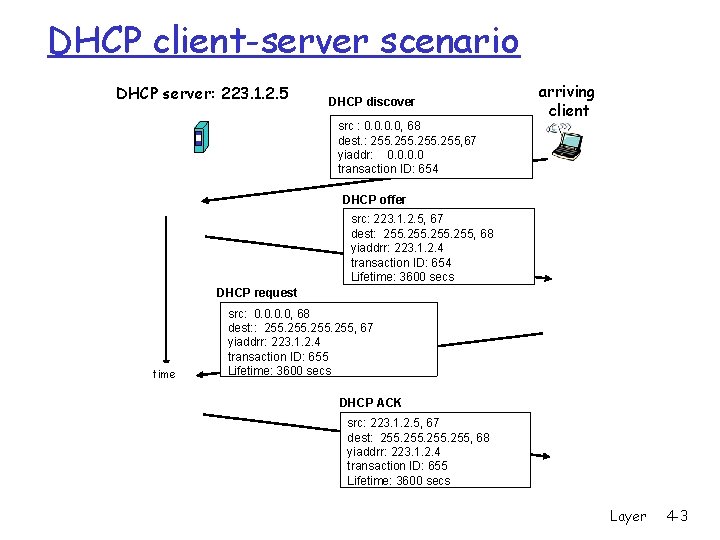
DHCP client-server scenario DHCP server: 223. 1. 2. 5 DHCP discover src : 0. 0, 68 dest. : 255, 67 yiaddr: 0. 0 transaction ID: 654 arriving client DHCP offer src: 223. 1. 2. 5, 67 dest: 255, 68 yiaddrr: 223. 1. 2. 4 transaction ID: 654 Lifetime: 3600 secs DHCP request time src: 0. 0, 68 dest: : 255, 67 yiaddrr: 223. 1. 2. 4 transaction ID: 655 Lifetime: 3600 secs DHCP ACK src: 223. 1. 2. 5, 67 dest: 255, 68 yiaddrr: 223. 1. 2. 4 transaction ID: 655 Lifetime: 3600 secs CPSC 441 - Network Layer 4 -3

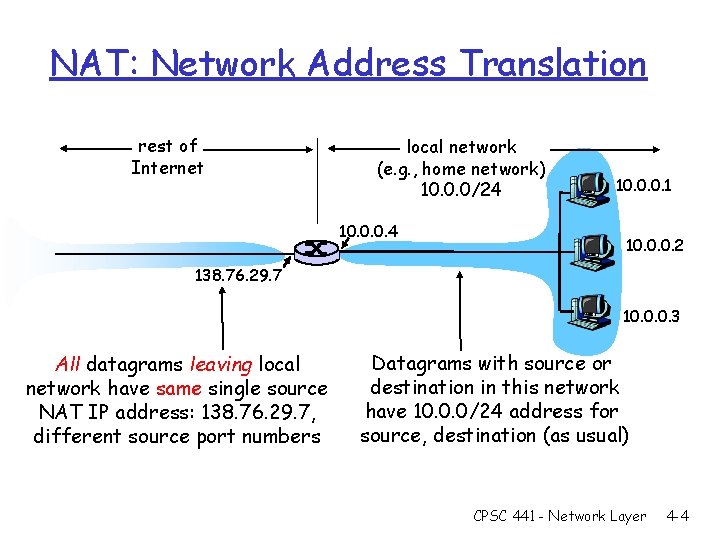
NAT: Network Address Translation rest of Internet local network (e. g. , home network) 10. 0. 0/24 10. 0. 0. 1 10. 0. 0. 2 138. 76. 29. 7 10. 0. 0. 3 All datagrams leaving local network have same single source NAT IP address: 138. 76. 29. 7, different source port numbers Datagrams with source or destination in this network have 10. 0. 0/24 address for source, destination (as usual) CPSC 441 - Network Layer 4 -4

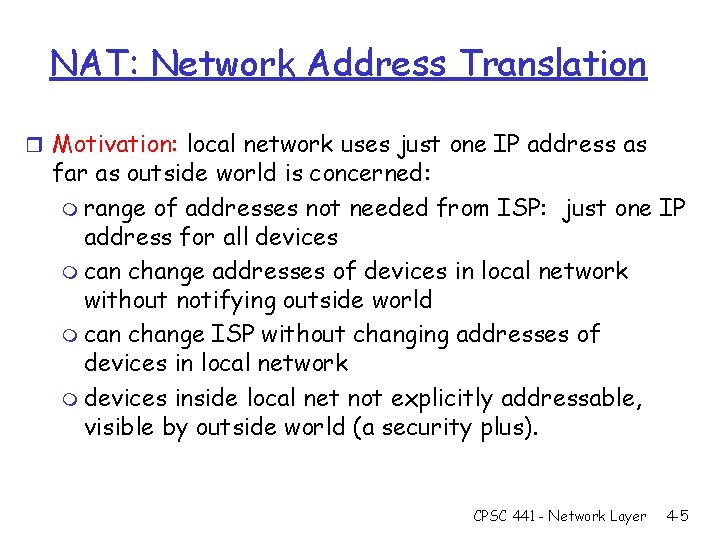
NAT: Network Address Translation r Motivation: local network uses just one IP address as far as outside world is concerned: m range of addresses not needed from ISP: just one IP address for all devices m can change addresses of devices in local network without notifying outside world m can change ISP without changing addresses of devices in local network m devices inside local net not explicitly addressable, visible by outside world (a security plus). CPSC 441 - Network Layer 4 -5

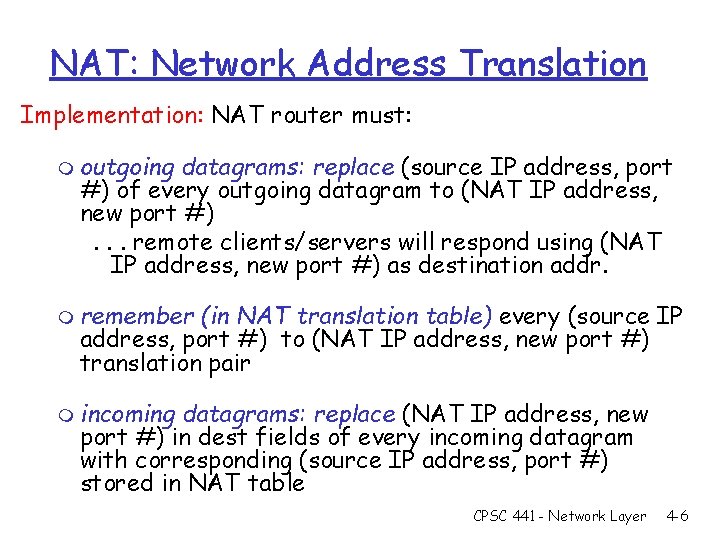
NAT: Network Address Translation Implementation: NAT router must: m outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #). . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. m remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair m incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table CPSC 441 - Network Layer 4 -6

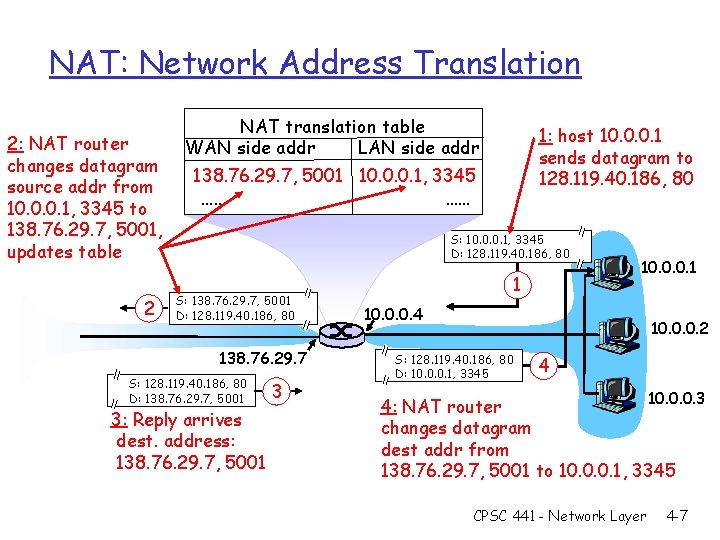
NAT: Network Address Translation 2: NAT router changes datagram source addr from 10. 0. 0. 1, 3345 to 138. 76. 29. 7, 5001, updates table 2 NAT translation table WAN side addr LAN side addr 1: host 10. 0. 0. 1 sends datagram to 128. 119. 40. 186, 80 138. 76. 29. 7, 5001 10. 0. 0. 1, 3345 …… …… S: 10. 0. 0. 1, 3345 D: 128. 119. 40. 186, 80 S: 138. 76. 29. 7, 5001 D: 128. 119. 40. 186, 80 138. 76. 29. 7 S: 128. 119. 40. 186, 80 D: 138. 76. 29. 7, 5001 3: Reply arrives dest. address: 138. 76. 29. 7, 5001 3 1 10. 0. 0. 4 10. 0. 0. 2 S: 128. 119. 40. 186, 80 D: 10. 0. 0. 1, 3345 4 10. 0. 0. 3 4: NAT router changes datagram dest addr from 138. 76. 29. 7, 5001 to 10. 0. 0. 1, 3345 CPSC 441 - Network Layer 4 -7

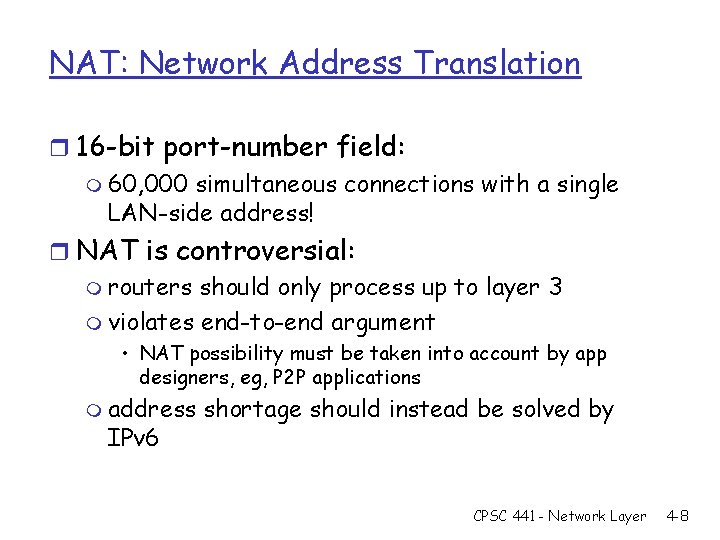
NAT: Network Address Translation r 16 -bit port-number field: m 60, 000 simultaneous connections with a single LAN-side address! r NAT is controversial: m routers should only process up to layer 3 m violates end-to-end argument • NAT possibility must be taken into account by app designers, eg, P 2 P applications m address IPv 6 shortage should instead be solved by CPSC 441 - Network Layer 4 -8

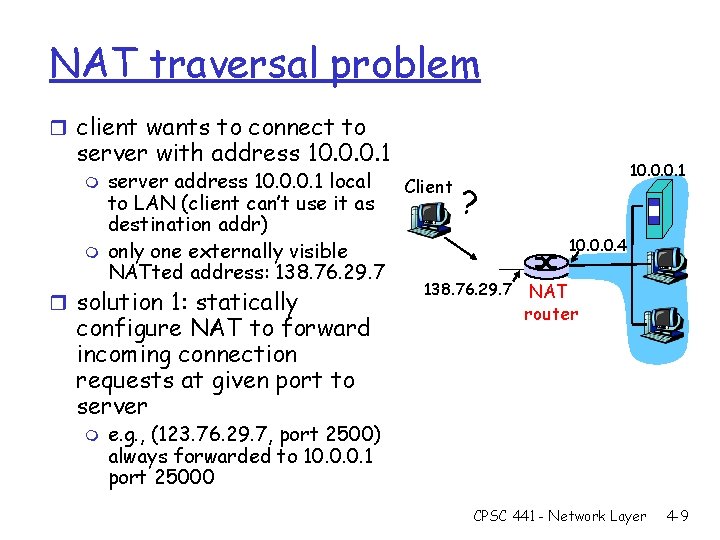
NAT traversal problem r client wants to connect to server with address 10. 0. 0. 1 m m server address 10. 0. 0. 1 local Client to LAN (client can’t use it as destination addr) only one externally visible NATted address: 138. 76. 29. 7 r solution 1: statically configure NAT to forward incoming connection requests at given port to server m 10. 0. 0. 1 ? 10. 0. 0. 4 138. 76. 29. 7 NAT router e. g. , (123. 76. 29. 7, port 2500) always forwarded to 10. 0. 0. 1 port 25000 CPSC 441 - Network Layer 4 -9

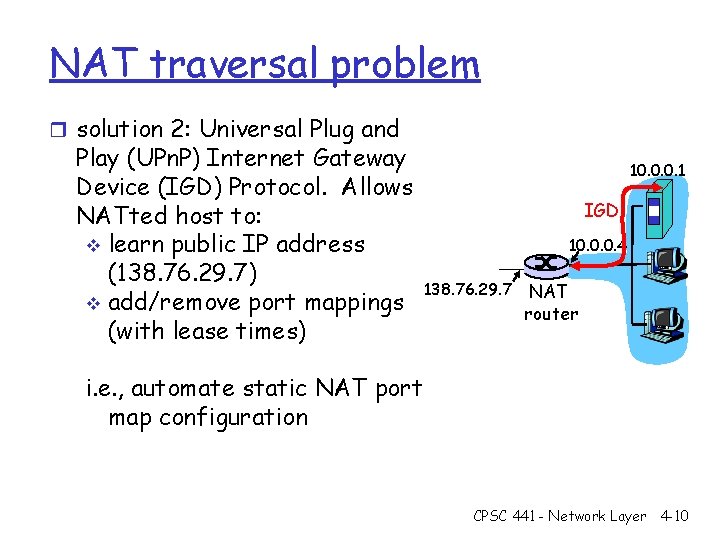
NAT traversal problem r solution 2: Universal Plug and Play (UPn. P) Internet Gateway Device (IGD) Protocol. Allows NATted host to: v learn public IP address (138. 76. 29. 7) v add/remove port mappings (with lease times) 10. 0. 0. 1 IGD 10. 0. 0. 4 138. 76. 29. 7 NAT router i. e. , automate static NAT port map configuration CPSC 441 - Network Layer 4 -10

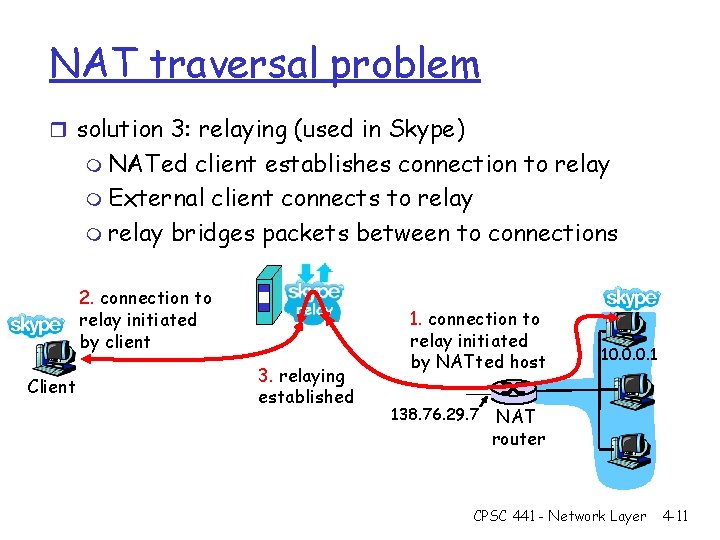
NAT traversal problem r solution 3: relaying (used in Skype) m NATed client establishes connection to relay m External client connects to relay m relay bridges packets between to connections 2. connection to relay initiated by client Client 3. relaying established 1. connection to relay initiated by NATted host 138. 76. 29. 7 10. 0. 0. 1 NAT router CPSC 441 - Network Layer 4 -11

IPv 6 r Initial motivation: 32 -bit address space soon to be completely allocated. r Additional motivation: m header format helps speed processing/forwarding m header changes to facilitate Qo. S IPv 6 datagram format: m fixed-length 40 byte header m no fragmentation allowed CPSC 441 - Network Layer 4 -12

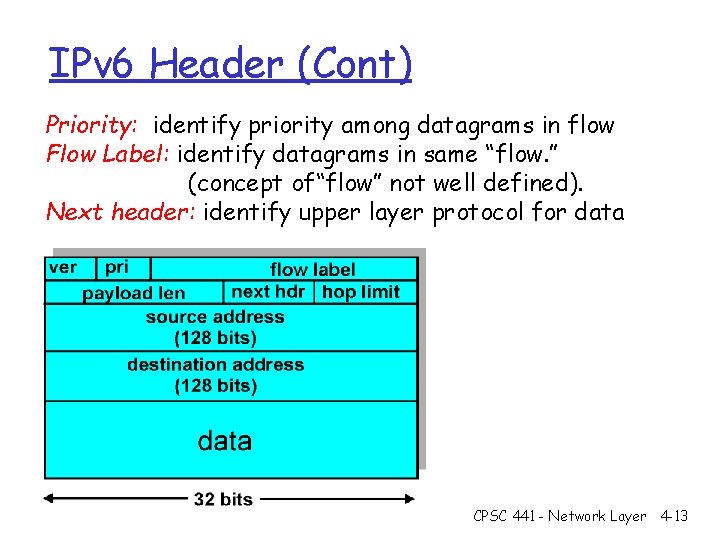
IPv 6 Header (Cont) Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow. ” (concept of“flow” not well defined). Next header: identify upper layer protocol for data CPSC 441 - Network Layer 4 -13

Other Changes from IPv 4 r Checksum: removed entirely to reduce processing time at each hop r Options: allowed, but outside of header, indicated by “Next Header” field r ICMPv 6: new version of ICMP m additional message types, e. g. “Packet Too Big” m multicast group management functions CPSC 441 - Network Layer 4 -14

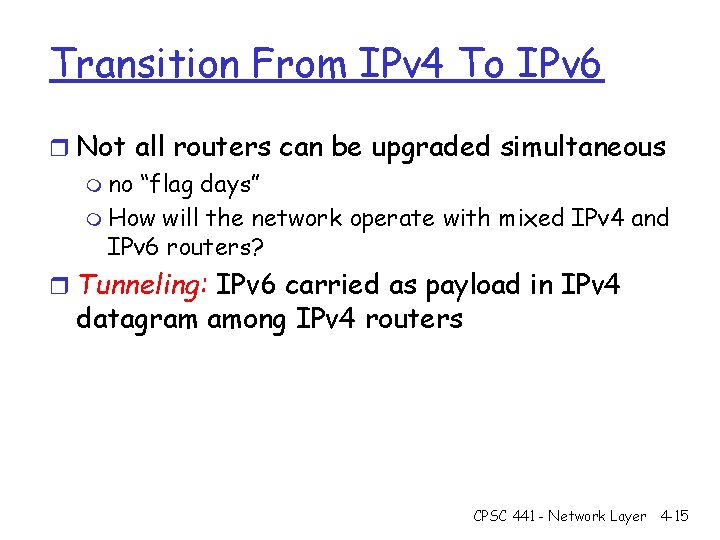
Transition From IPv 4 To IPv 6 r Not all routers can be upgraded simultaneous m no “flag days” m How will the network operate with mixed IPv 4 and IPv 6 routers? r Tunneling: IPv 6 carried as payload in IPv 4 datagram among IPv 4 routers CPSC 441 - Network Layer 4 -15

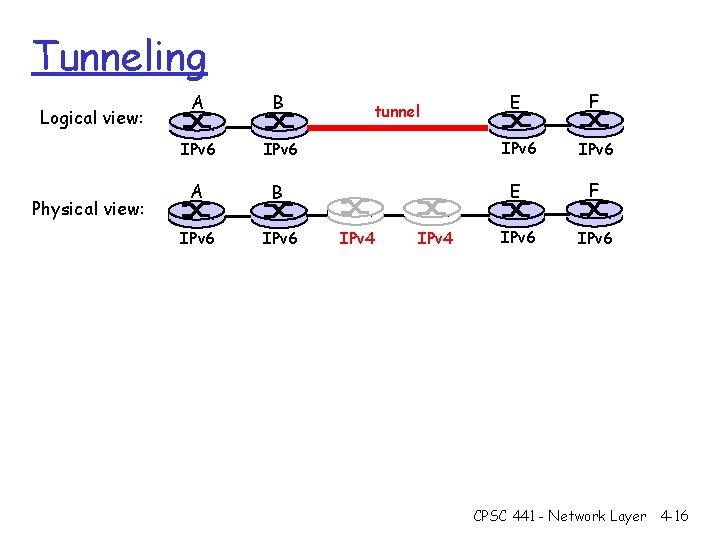
Tunneling Logical view: Physical view: E F IPv 6 IPv 6 A B IPv 6 tunnel IPv 4 CPSC 441 - Network Layer 4 -16

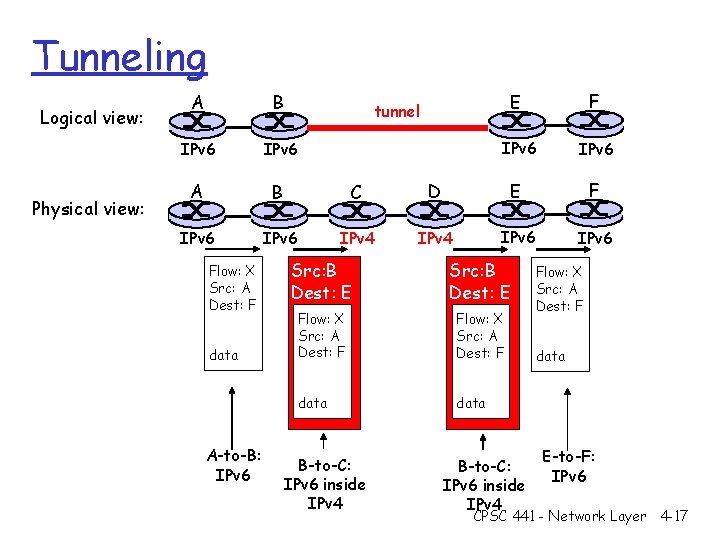
Tunneling Logical view: Physical view: A B IPv 6 A B C IPv 6 IPv 4 Flow: X Src: A Dest: F data A-to-B: IPv 6 E F IPv 6 D E F IPv 4 IPv 6 tunnel Src: B Dest: E Flow: X Src: A Dest: F data B-to-C: IPv 6 inside IPv 4 Flow: X Src: A Dest: F data E-to-F: IPv 6 CPSC 441 - Network Layer 4 -17