COVERT STORAGE CHANNEL MODULE Xenia Mountrouidou College of









- Slides: 13

COVERT STORAGE CHANNEL MODULE Xenia Mountrouidou College of Charleston Xiangyang Li Johns Hopkins University Information Security Institute

Outline • • • Start reserving your topology Learning Goals Audience Background Variations

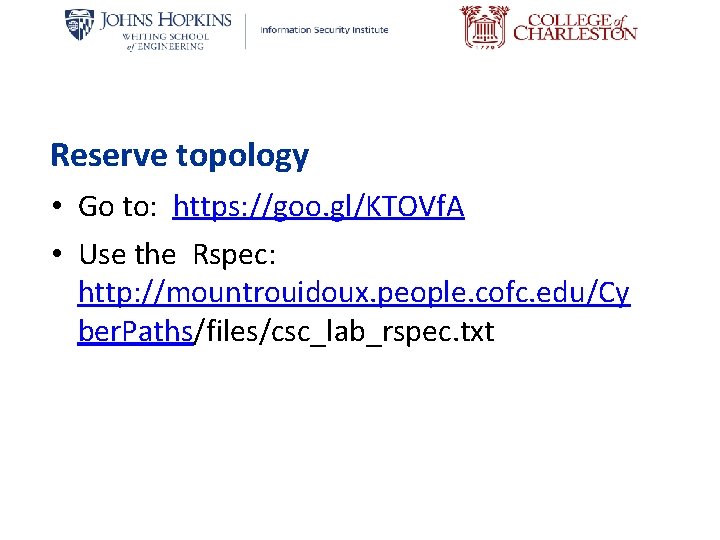
Reserve topology • Go to: https: //goo. gl/KTOVf. A • Use the Rspec: http: //mountrouidoux. people. cofc. edu/Cy ber. Paths/files/csc_lab_rspec. txt

Learning Goals • Generate regular traffic based on a distribution • Generate covert storage traffic channel traffic with TCP flag manipulation • Analyze the TCP packets • Detect the presence of covert storage traffic in a network using entropy • Use Wireshark, GENI

Audience • CS majors • Some background work is needed

Background • • Linux, SFTP and Wireshark Covert Storage Channels TCP Flags GENI

What are Covert Storage Channels? A Covert Storage Channel is a communications channel that is hidden within the medium of legitimate communications channel. Covert channels manipulate a communications medium in an unexpected or unconventional way by using resources that are not meant for communication in order to transmit information in an undetectable manner. How do we use TCP Flags as carriers? A Covert Storage Channel uses the TCP Flag (TF) header field in a network packet, a six-bit field used to set up TCP connection for transmitting messages. The two communicating parties, start exchanging messages based on pre-agreed coding scheme.

TCP Flags as Carriers

How Cybercrime Exploits Covert Storage Channels • Researchers focus on methods to more reliable CSC channels for the need of privacy and protection of communication parties. • Conspirators seek advanced steganographic tools for purposes of: • Data Exfiltration • Command • Control

CSC Lab for non-CS Majors • • • Draw Topology Generate regular traffic Use TCP flag manipulation Generate covert storage channel traffic Detect the presence of covert storage traffic Experiments on GENI: Virtual laboratory for networking and distributed systems research and education

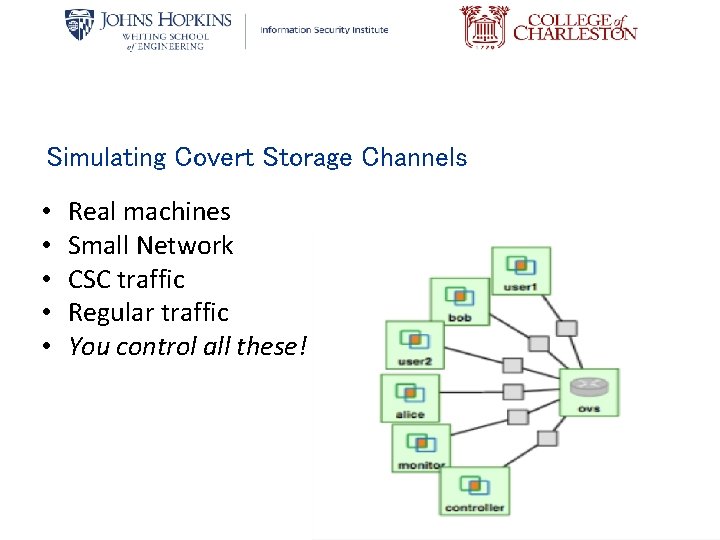
Simulating Covert Storage Channels • • • Real machines Small Network CSC traffic Regular traffic You control all these!

Variations • GENI Desktop • Usage of different TCP header field as CSC • Usage of Split-Join Network for transmitting CSC traffic

Questions? LET’S EXPERIMENT!
 Covert storage channel example
Covert storage channel example Xenia board of education
Xenia board of education Bebida lactea años dorados informacion nutricional
Bebida lactea años dorados informacion nutricional Xenia liashuk
Xenia liashuk Sniffing
Sniffing Xenia programming languages
Xenia programming languages Book 9 odyssey
Book 9 odyssey Xenia in the odyssey
Xenia in the odyssey Xenia resolution scaling
Xenia resolution scaling Tgi ventilacion mecanica
Tgi ventilacion mecanica Xenia labs
Xenia labs Definition of multi channel retailing
Definition of multi channel retailing Conversion of continuous awgn channel to vector channel
Conversion of continuous awgn channel to vector channel Determine id
Determine id






















