Covert Channels Eric Pennington COSC 480 Common Network















- Slides: 21

Covert Channels Eric Pennington COSC 480

Common Network Threats o Viruses, Trojans, Worms, etc. o Password Attacks o Eavesdropping o Port Scanning o Not typically Covert Channels

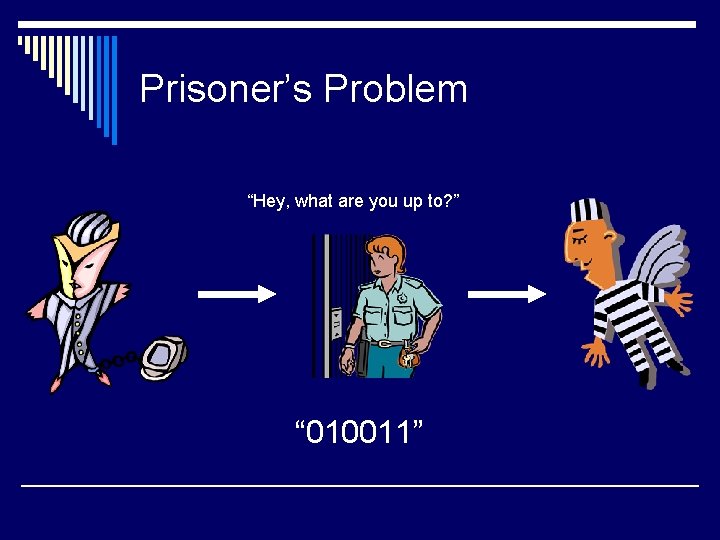
Prisoner’s Problem o Two prisoners want to escape jail. o They are in separate cells and need to communicate. o All messages between prisoners must go through the warden. o What should they do?

Prisoner’s Problem o They communicate their plans to each other in code. o Each word with an even number of letters represents a 1. o Each word with an odd number of letters represents a 0. o The actual message is the reassembled binary string.

Prisoner’s Problem “Hey, what are you up to? ” “ 010011”

Covert Channels

Covert Channels “A covert channel is any communication channel that can be exploited by a process to transfer information in a manner that violates the system's security policy. ”

Sending and Receiving Processes o The Sending Process is what transmits the covert data o The Sending Process typically has higher security privileges o The Receiving Process is what accepts the covert data o The Receiving Process typically has lower security privileges

Trojan Horses o A Trojan Horse is a backdoor disguised as legitimate software o Trojan Horses are the most common way to deploy the Sending process of a covert channel

Covert Storage Channels

Covert Storage Channels “Covert storage channels include all vehicles that would allow the direct or indirect writing of a storage location by one process and the direct or indirect reading of it by another. ”

Storage Channels Example o Sending process (S) creates a file on the Common Drive (N: ) o To signal a 1, S makes the file read-only o To signal a 0, S turns off read-only o Receiving process (R) polls to see if the file exists o When it exists, R reads the read-only value to receive the information

Covert Timing Channels

Covert Timing Channels “Covert timing channels include all vehicles that would allow one process to signal information to another process by modulating its own use of system resources in such a way that the change in response time observed by the second process would provide information. ”

Timing Channels Example o Sending process (S) and Receiving process (R) o o have access to the same movable-head I/O device S has access to the entire device while R only has access to a certain section The device processes all requests serially To signal a 1, S makes a request to the farthest area of the device from R’s section To signal a 0, S does nothing

Timing Channels Example o R makes a read request within its own section of the device o It measures the time it takes for the request to complete o If it takes a longer time, due to the head being so far away, it reads a 1 o If it takes a shorter time, because the head is closer, it reads a 0

Covert Channels vs. Steganography Channel Hiding Data Hiding

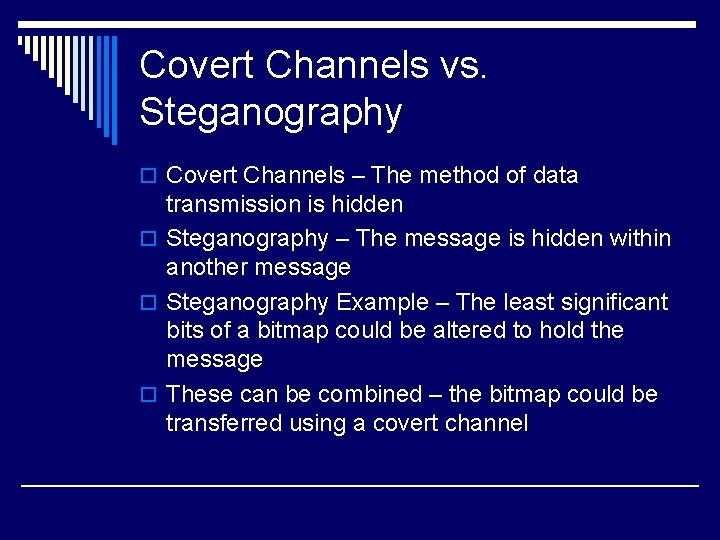
Covert Channels vs. Steganography o Covert Channels – The method of data transmission is hidden o Steganography – The message is hidden within another message o Steganography Example – The least significant bits of a bitmap could be altered to hold the message o These can be combined – the bitmap could be transferred using a covert channel

Noise in Covert Channels Noise occurs when something interferes with the transmission from the Sending process to the Receiving process

Noise in Covert Channels o In the Storage Channels example, what happens if another process modifies the read-only bit of the file? o The receiving process would still record the information and possibly become corrupted o This is a major problem in Covert Channels

Bibliography o Department of Defense. “Trusted Computer System Evaluation Criteria. ” 1985. o Owens, Mark. “A Discussion of Covert Channels and Steganography. ” 2002. o Simmons, Gustavus. “The Prisoners’ Problem and the Subliminal Channel. ” 1983.