Countering LargeScale Internet Pollution and Poisoning Aleksandar Kuzmanovic



- Slides: 15

Countering Large-Scale Internet Pollution and Poisoning Aleksandar Kuzmanovic Northwestern University http: //www. cs. northwestern. edu/~akuzma/

Problem and Approach (general) Denial of service (Do. S) attacks in the Internet – Serious problem – Becoming more and more sophisticated Approach I – Search for new classes of Do. S attacks and system vulnerabilities • It is interesting; it makes sense; it is relevant; Approach II – Exploit asymmetric costs • Small efforts by defenders will require attackers to multiply the amount of resources (e. g. , bandwidth, time, precision) Raise the bar high enough to make the attacks hard (vs. impossible) to conduct Aleksandar Kuzmanovic 2

Pollution in P 2 P File Sharing Systems Music industry vs. p 2 p networks Our work: – Denial-of-Service Resilience in Peer-to-Peer File Sharing Systems • In Proceedings of ACM SIGMETRICS 2005. Insight – Despite highly replicated content and a decentralized system design, pollution attacks can be highly effective Is it feasible to conduct similar type of attacks in the Internet at a large scale? Aleksandar Kuzmanovic 3

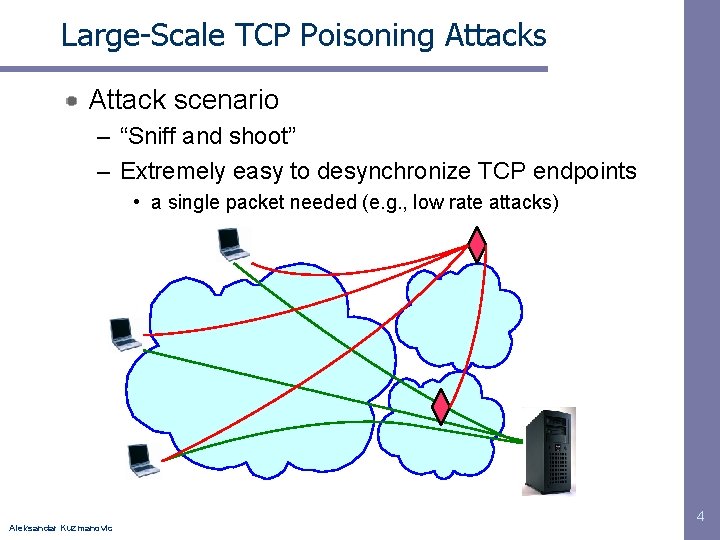
Large-Scale TCP Poisoning Attacks Attack scenario – “Sniff and shoot” – Extremely easy to desynchronize TCP endpoints • a single packet needed (e. g. , low rate attacks) Aleksandar Kuzmanovic 4

Aleksandar Kuzmanovic

Aleksandar Kuzmanovic

Aleksandar Kuzmanovic

Large-Scale TCP Poisoning Attacks (II) Our Approach – No explicit security association between endpoints – Protocol design • Raise the bar “high enough” to exploit asymmetric costs Solution-specific details – Deferred protocol reaction – Forward hashing – Self-clocking correlation method Kernel-level implementation in Free. BSD Aleksandar Kuzmanovic 8

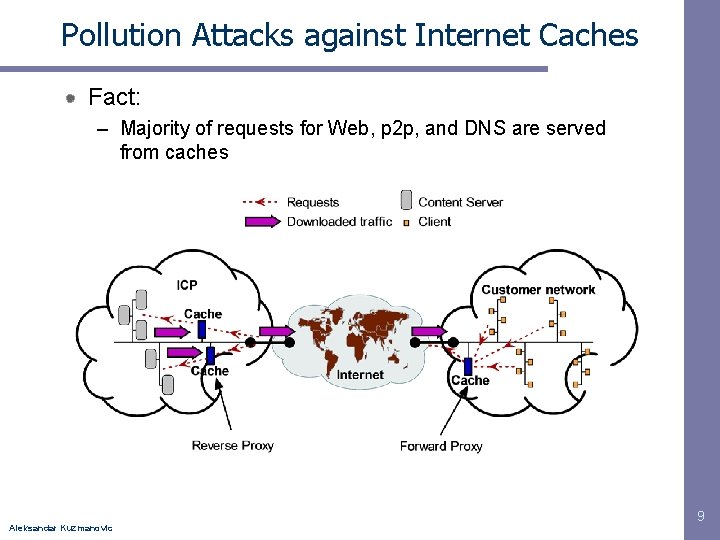
Pollution Attacks against Internet Caches Fact: – Majority of requests for Web, p 2 p, and DNS are served from caches Aleksandar Kuzmanovic 9

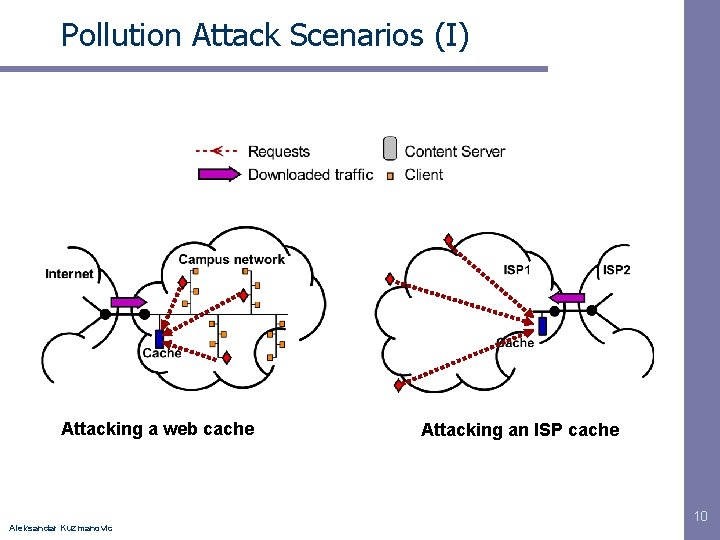
Pollution Attack Scenarios (I) Attacking a web cache Aleksandar Kuzmanovic Attacking an ISP cache 10

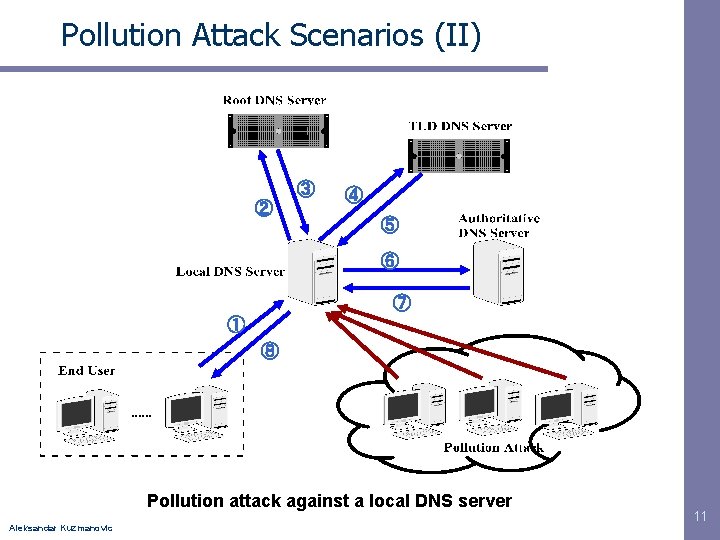
Pollution Attack Scenarios (II) ③ ② ④ ⑤ ⑥ ⑦ ① ⑧ Pollution attack against a local DNS server Aleksandar Kuzmanovic 11

Pollution Attack Classes (I) Before attack After attack New unpopular files Popular files …. . . . Cache Locality-disruption attacks Aleksandar Kuzmanovic 12

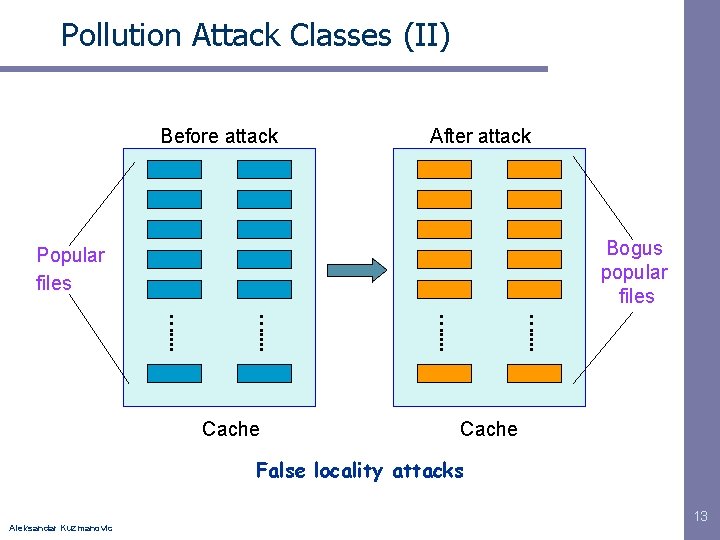
Pollution Attack Classes (II) Before attack After attack Bogus popular files Popular files …. . . . Cache False locality attacks Aleksandar Kuzmanovic 13

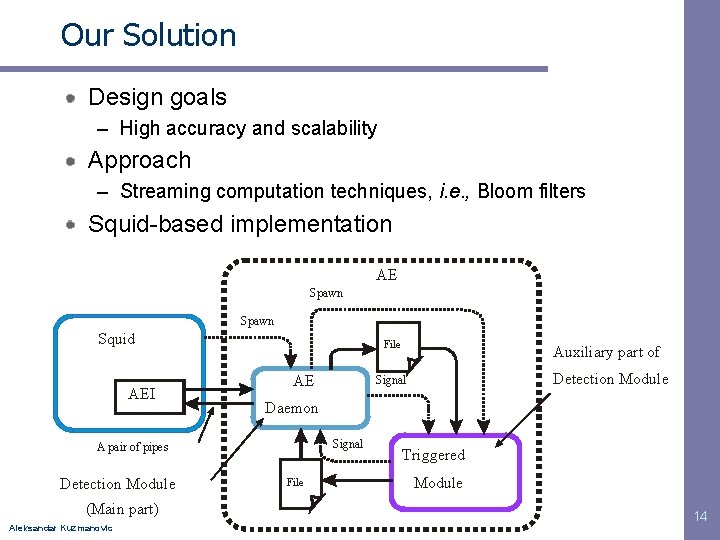
Our Solution Design goals – High accuracy and scalability Approach – Streaming computation techniques, i. e. , Bloom filters Squid-based implementation AE Spawn Squid AEI File AE (Main part) Aleksandar Kuzmanovic Detection Module Signal Daemon Signal A pair of pipes Detection Module Auxiliary part of File Triggered Module 14

Summary Actively searching (and developing solutions) for new types of Do. S attacks Pollution and poisoning – P 2 p networks, TCP, Internet caches Solutions – Exploit asymmetric costs between defenders and attackers – Prototype implementations Aleksandar Kuzmanovic 15
 Aleksandar kuzmanovic flashback
Aleksandar kuzmanovic flashback Aleksandar prokopec
Aleksandar prokopec Aleksandar kupusinac
Aleksandar kupusinac Aleksandar kupusinac
Aleksandar kupusinac Aleksandar plamenac
Aleksandar plamenac Aleksandar rakicevic
Aleksandar rakicevic Aleksandar tatalovic
Aleksandar tatalovic Aleksandar nikcevic
Aleksandar nikcevic Aleksandar baucal
Aleksandar baucal Configurator konica minolta
Configurator konica minolta Aleksandar kartelj
Aleksandar kartelj Vjenčanje europe i azije
Vjenčanje europe i azije Aleksandar prokopec
Aleksandar prokopec Aleksandar.krizo
Aleksandar.krizo Aleksandar stefanovic sorbonne
Aleksandar stefanovic sorbonne Franiza
Franiza





























