COT 4600 Operating Systems Spring 2011 Dan C




- Slides: 17

COT 4600 Operating Systems Spring 2011 Dan C. Marinescu Office: HEC 304 Office hours: Tu-Th 5: 00 – 6: 00 PM

Lecture 7 – Thursday, February 3, 2011 n Last time: n Memory ¨ Interpreters. ¨ Communication links. Today: ¨ ¨ Communication – The Internet Naming; n Use by: value/name n Binding and indirection Next time ¨ n n n n Generic naming model Name mapping algorithms Comparing names; name discovery Practical design of naming scheme Contexts Name overloading UNIX File System Lecture 7 2

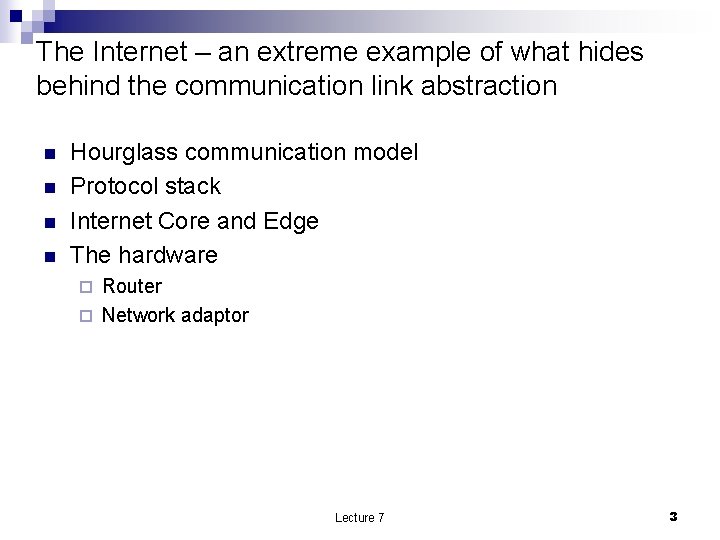
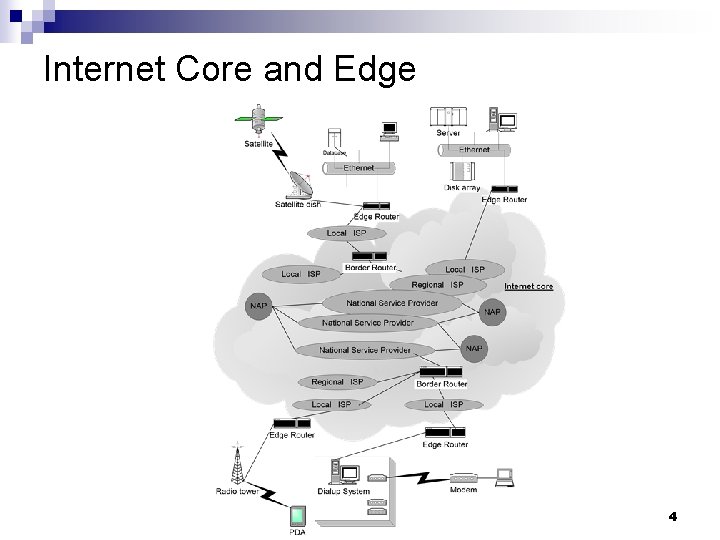
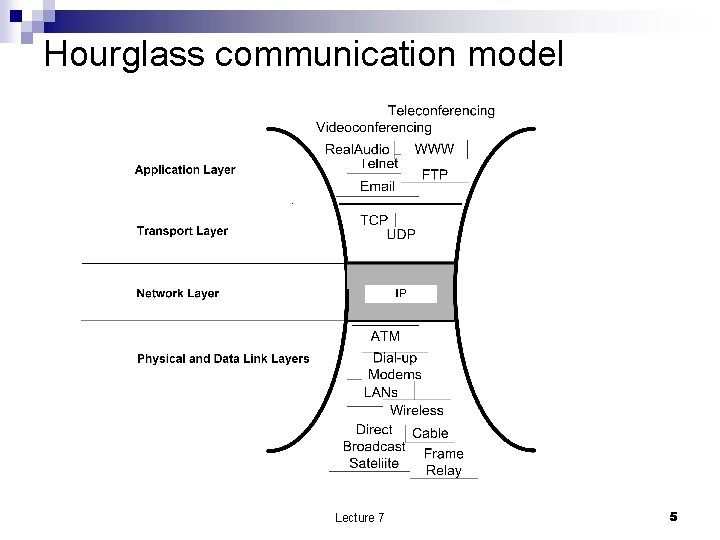
The Internet – an extreme example of what hides behind the communication link abstraction n n Hourglass communication model Protocol stack Internet Core and Edge The hardware Router ¨ Network adaptor ¨ Lecture 7 3

Internet Core and Edge Lecture 7 4

Hourglass communication model Lecture 7 5

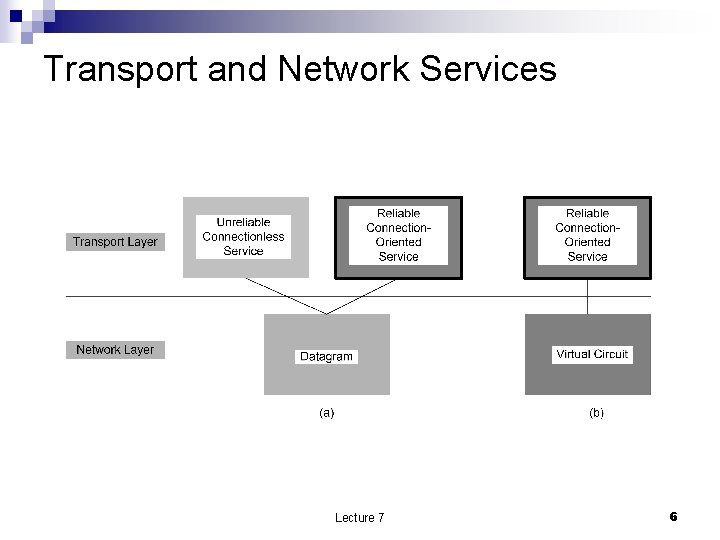
Transport and Network Services Lecture 7 6

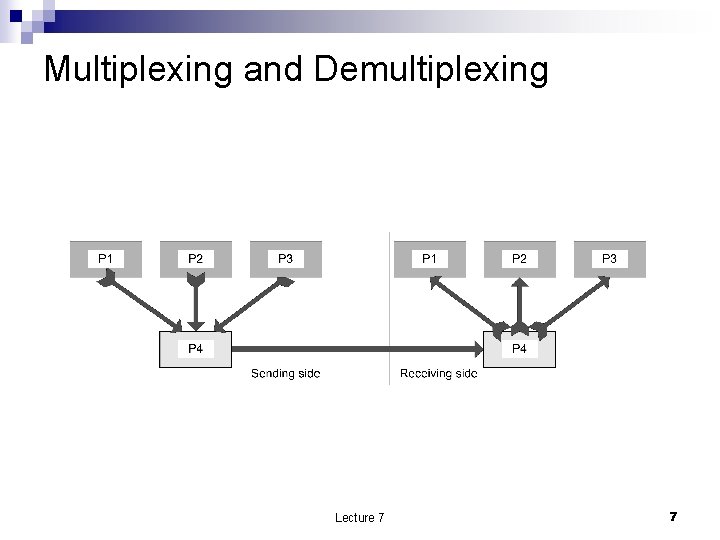
Multiplexing and Demultiplexing Lecture 7 7

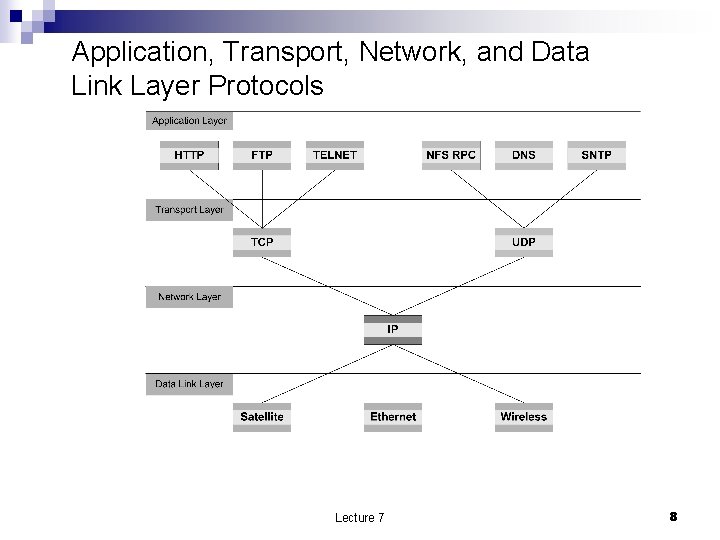
Application, Transport, Network, and Data Link Layer Protocols Lecture 7 8

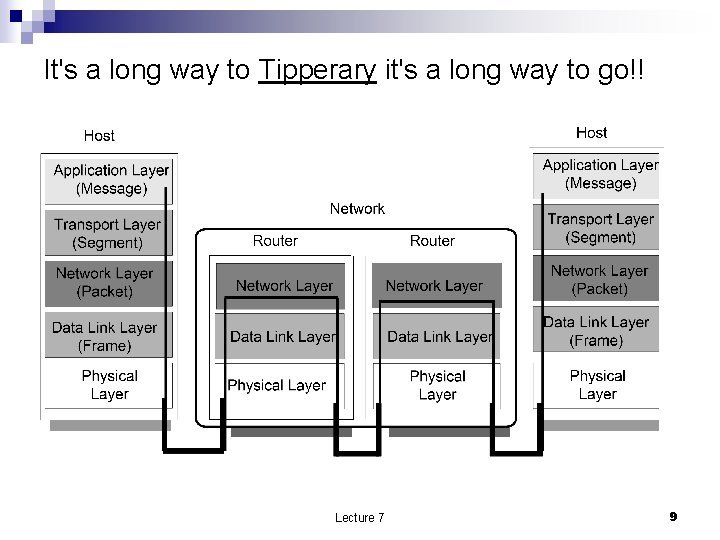
It's a long way to Tipperary it's a long way to go!! Lecture 7 9

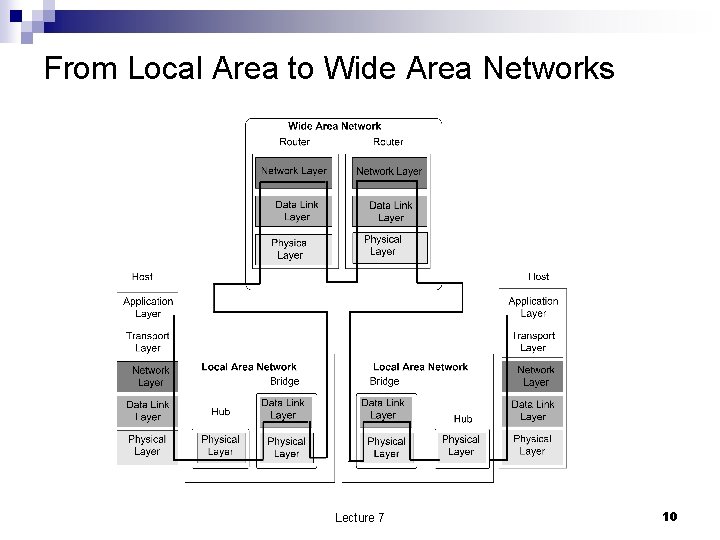
From Local Area to Wide Area Networks Lecture 7 10

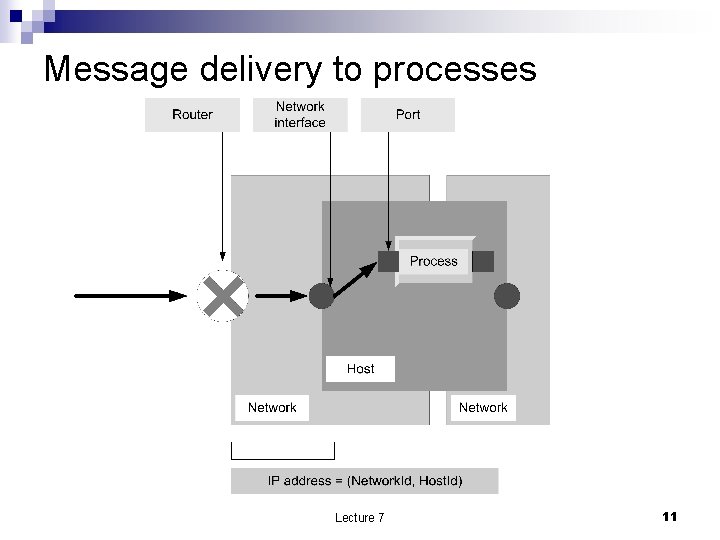
Message delivery to processes Lecture 7 11

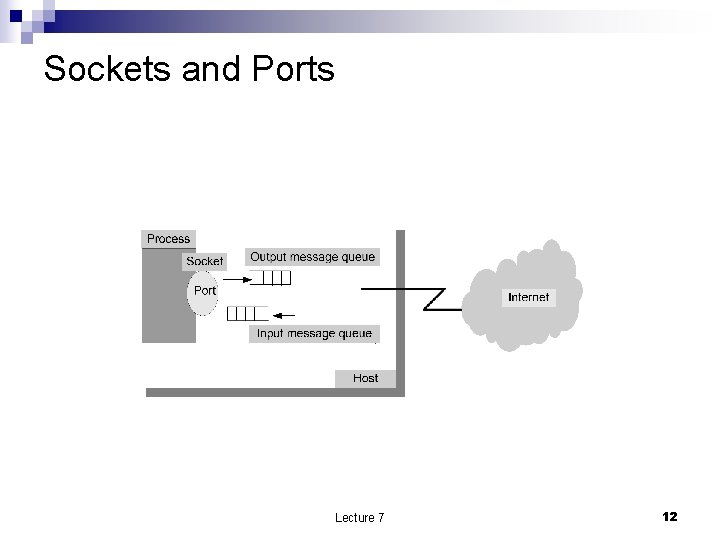
Sockets and Ports Lecture 7 12

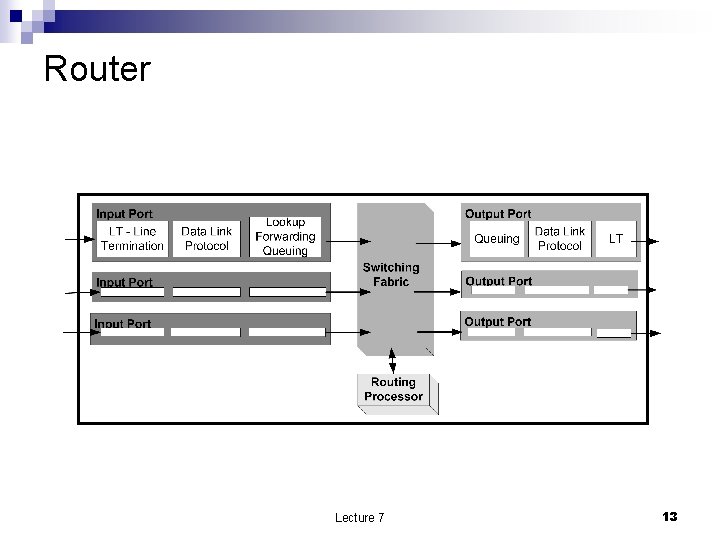
Router Lecture 7 13

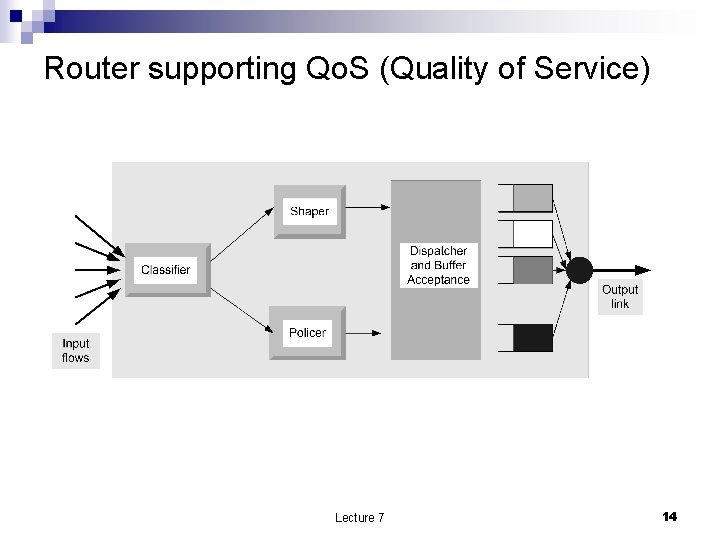
Router supporting Qo. S (Quality of Service) Lecture 7 14

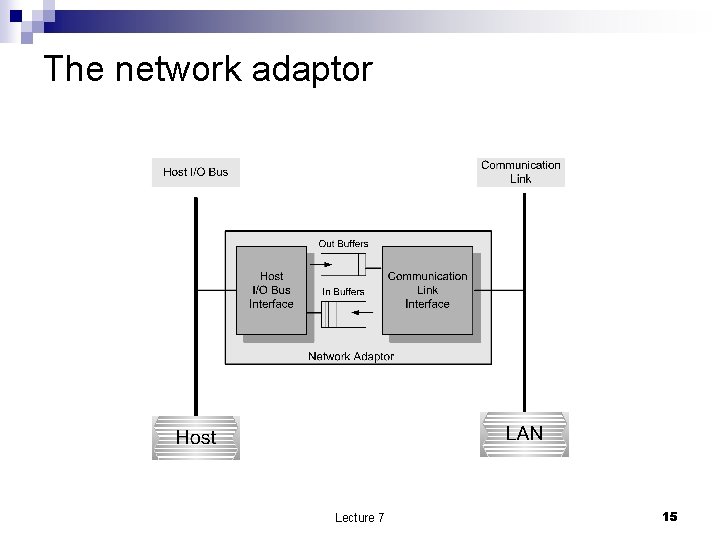
The network adaptor Lecture 7 15

Naming n n The three abstractions manipulate objects identified by name. How could object A access object B: ¨ Make a copy of object B and include it in A use by value n n ¨ Safe there is a single copy of B How to implement sharing of object B? Pass to A the means to access B using its name use by reference n Not inherently safe both A and C may attempt to modify B at the same time. Need some form of concurrency control. Lecture 7 16

Binding and indirection n Names allow the system designer to: organize the modules of a system and to define communication patterns among them 2. defer for a later time 1. n n to create object B referred to by object A select the specific object A wishes to use Indirection decoupling objects from their physical realization through names. Binding linking the object to names. Examples: ¨ A compiler constructs n n ¨ a table of variables and their relative address in the data section of the memory map of the process a list of unsatisfied external references A linker binds the external references to modules from libraries Lecture 7 17