COT 4600 Operating Systems Spring 2011 Dan C




- Slides: 14

COT 4600 Operating Systems Spring 2011 Dan C. Marinescu Office: HEC 304 Office hours: Tu-Th 5: 00 – 6: 00 PM

Lecture 9 – Thursday, February 10, 2011 n Last time: n n Binding and indirection Generic naming model ¨ ¨ n Practical design of naming scheme ¨ ¨ n Contexts Name overloading Today: n n Computer system organization; operating systems The hardware layer ¨ ¨ n n Bus sharing Optimization, DMA The software layer – the file abstraction Case studies ¨ ¨ n Name mapping algorithms Comparing names; name discovery UNIX File System URLs Next time ¨ Modularity Lecture 9 2

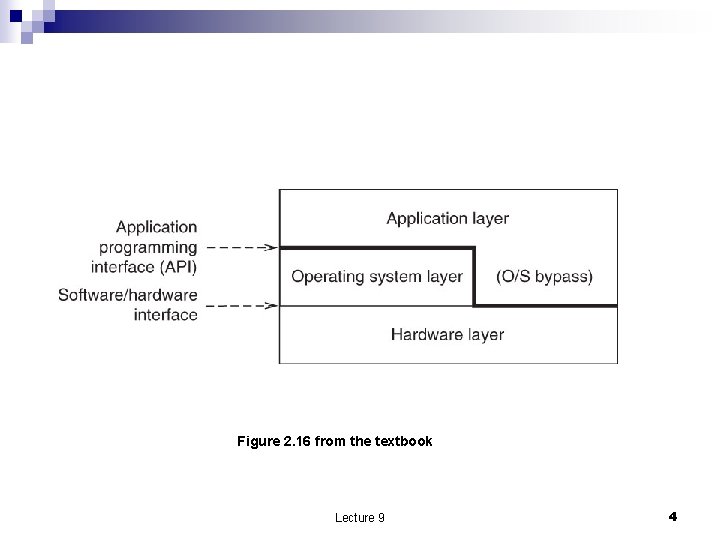
Computer System Organization n Operating Systems (OS) software used to Control the allocation of resources (hardware and software) ¨ Support user applications ¨ Sandwiched between the hardware layer and the application layer ¨ n OS-bypass: the OS does not hide completely the hardware from applications. It only hides dangerous functions such as I/O operations ¨ Management function ¨ n Names modularization Lecture 9 3

Figure 2. 16 from the textbook Lecture 9 4

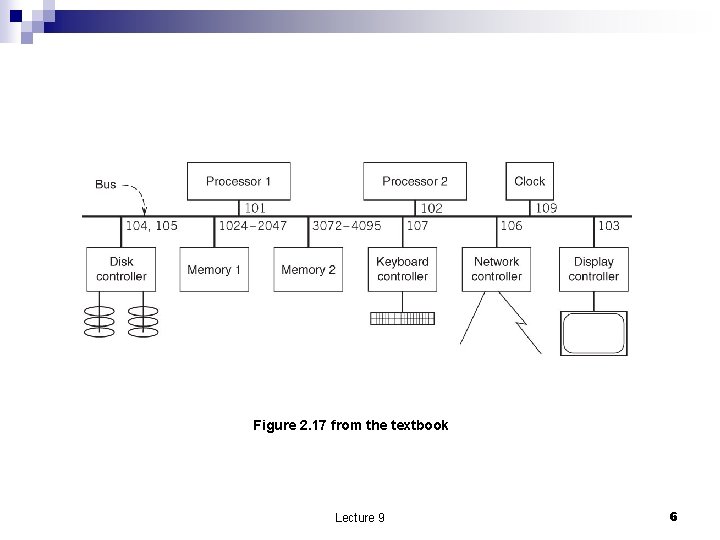
The hardware layer n n Modules representing each of the three abstractions (memory, interpreter, communication link) are interconnected by a bus. The bus a broadcast communication channel, each module hears every transmission. Control lines ¨ Data lines ¨ Address lines ¨ n Each module is identified by a unique address ¨ has a bus interface ¨ n Modules other than processors need a controller. Lecture 9 5

Figure 2. 17 from the textbook Lecture 9 6

Bus sharing and optimization n n Communication broadcast Arbitration protocol decide which module has the control of the bus. Supported by hardware: a bus arbiter circuit ¨ distributed among interfaces – each module has a priority ¨ daisy chaining ¨ n n Split-transaction a module uses the arbitration protocol to acquire control of the bus Optimization: ¨ hide the latency of I/O devices n n ¨ Channels dedicated processors capable to execute a channel program (IBM) DMA (Direct Memory Access) Support transparent access to files: n Memory Mapped I/O Lecture 9 7

Optimization n Direct Memory Access (DMA): supports direct communication between processor and memory; the processor provides the disk address of a block in memory where data is to be read into or written from. ¨ hides the disk latency; it allows the processor to execute a process while data is transferred ¨ n Memory Mapped I/O: ¨ LOAD and STORE instructions access the registers and buffers of an I/O module n n ¨ n bus addresses are assigned to control registers and buffers of the I/O module the processor maps bus addresses to its own address space (registers) Supports software functions such as UNIX mmap which map an entire file. Swap area: disk image of the virtual memory of a process. Lecture 9 8

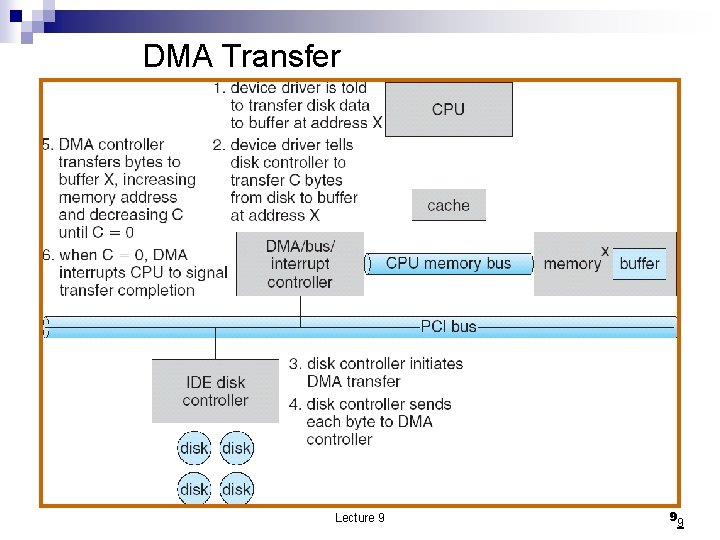
DMA Transfer Lecture 9 99

B. The software layer: the file abstraction n File: memory abstraction used by the application and OS layers linear array of bits/bytes ¨ properties: ¨ n n n durable information will not be changed in time has a name allows access to individual bits/bytes has a cursor which defines the current position in the file. The OS provides an API (Application Programming Interface) supporting a range of file manipulation operations. A user must first OPEN a file before accessing it and CLOSE it after it has finished with it. This strategy: allows different access rights (READ, WRITE, READ-WRITE) ¨ coordinate concurrent access to the file ¨ n Some file systems use OPEN and CLOSE to enforce before-or-after atomicity ¨ support all-or-nothing atomicity e. g. , ensure that if the system crashes before a CLOSE either all or none of WRITEs are carried out ¨ Lecture 9 10

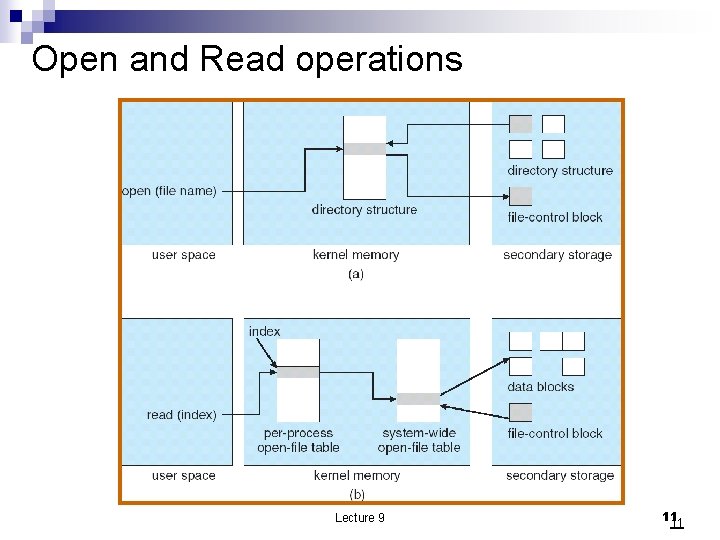
Open and Read operations Lecture 9 11 11

Unix and Unix File System n n n Developed in early 1970 s at Bell Labs for PDP computers made by Digital Lineage MULTICS developed at MIT in 1960 s Versions: ¨ ¨ ¨ n Berkeley Unix (BSD) GNU/Linux Darwin – part of MAC OS Unix file system – hierarchical data organization: blocks files directories file systems ¨ the objects: n n n ¨ files – linear arrays of blocks of data; each file has a cursor giving the current position directories – collections of files; tree structure metadata - useful information about the file, not contained in the file (e. g. , owner, access modes, last modified date, length, etc. ) supports: n n n creation, deletion, renaming of files and directories reading data from and writing data to a file reading and writing metadata describing a file Lecture 9 12

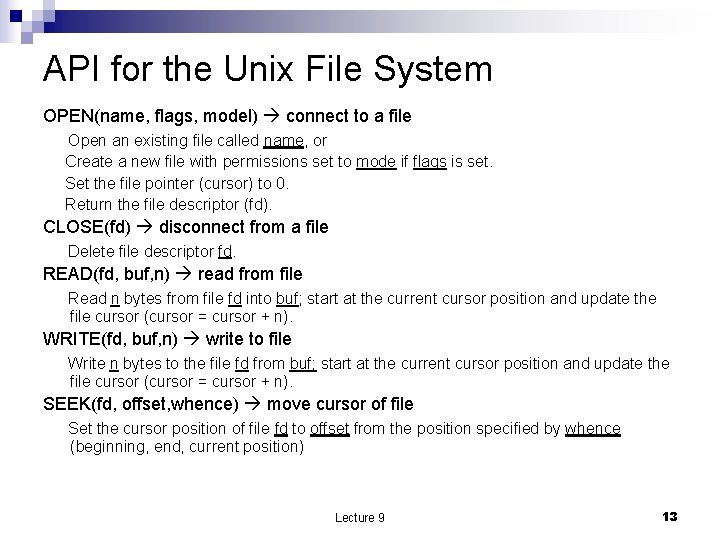
API for the Unix File System OPEN(name, flags, model) connect to a file Open an existing file called name, or Create a new file with permissions set to mode if flags is set. Set the file pointer (cursor) to 0. Return the file descriptor (fd). CLOSE(fd) disconnect from a file Delete file descriptor fd. READ(fd, buf, n) read from file Read n bytes from file fd into buf; start at the current cursor position and update the file cursor (cursor = cursor + n). WRITE(fd, buf, n) write to file Write n bytes to the file fd from buf; start at the current cursor position and update the file cursor (cursor = cursor + n). SEEK(fd, offset, whence) move cursor of file Set the cursor position of file fd to offset from the position specified by whence (beginning, end, current position) Lecture 9 13

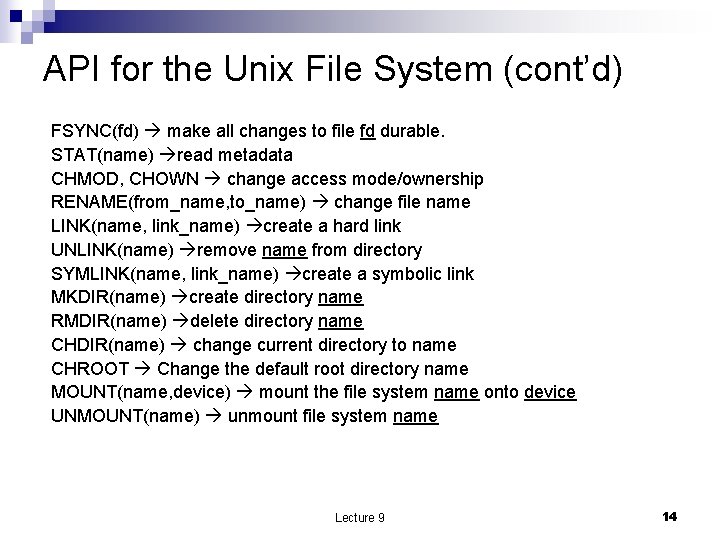
API for the Unix File System (cont’d) FSYNC(fd) make all changes to file fd durable. STAT(name) read metadata CHMOD, CHOWN change access mode/ownership RENAME(from_name, to_name) change file name LINK(name, link_name) create a hard link UNLINK(name) remove name from directory SYMLINK(name, link_name) create a symbolic link MKDIR(name) create directory name RMDIR(name) delete directory name CHDIR(name) change current directory to name CHROOT Change the default root directory name MOUNT(name, device) mount the file system name onto device UNMOUNT(name) unmount file system name Lecture 9 14