COS 433 Cryptography Lecture 12 Idiots Guide to



- Slides: 14

COS 433: Cryptography Lecture 12: Idiot’s Guide to Quantum Computing & Crypto Disclaimer Princeton University Fall 2005 Boaz Barak Princeton University • COS 433 • Cryptography • Fall 2005 • Boaz Barak

"Do not take the lecture too seriously. . . just relax and enjoy it. I am going to tell you what nature behaves like. If you will simply admit that maybe she does behave like this, you will find her a delightful, entrancing thing. Do not keep saying to yourself "But how can it be like that? " because you will get. . . into a blind alley from which nobody has yet escaped. Nobody knows how it can be like that. " Richard Feynmann on Quantum Mechanics. Strange aspects of quantum mechanics: v Superposition – object doesn’t have definite properties (location, speed) but has probabilities over them. v Interference – probabilities can be negative. v Entanglement – properties of many particles can be correlated. v Measurement – object’s properties collapse to definite value when measured, collapsing also properties of other entangled objects. 2

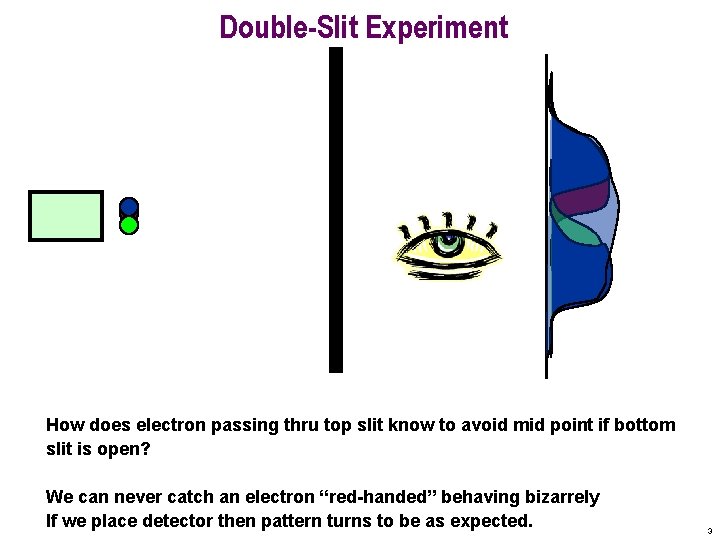
Double-Slit Experiment How does electron passing thru top slit know to avoid mid point if bottom slit is open? We can never catch an electron “red-handed” behaving bizarrely If we place detector then pattern turns to be as expected. 3

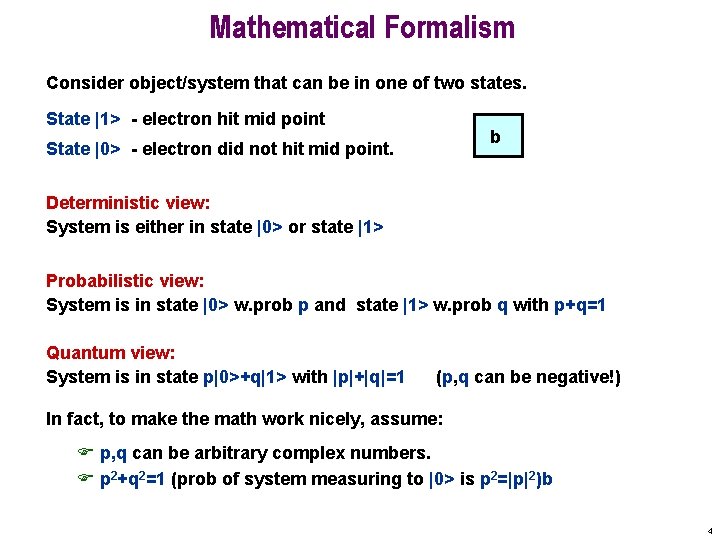
Mathematical Formalism Consider object/system that can be in one of two states. State |1> - electron hit mid point b State |0> - electron did not hit mid point. Deterministic view: System is either in state |0> or state |1> Probabilistic view: System is in state |0> w. prob p and state |1> w. prob q with p+q=1 Quantum view: System is in state p|0>+q|1> with |p|+|q|=1 (p, q can be negative!) In fact, to make the math work nicely, assume: F p, q can be arbitrary complex numbers. F p 2+q 2=1 (prob of system measuring to |0> is p 2=|p|2)b 4

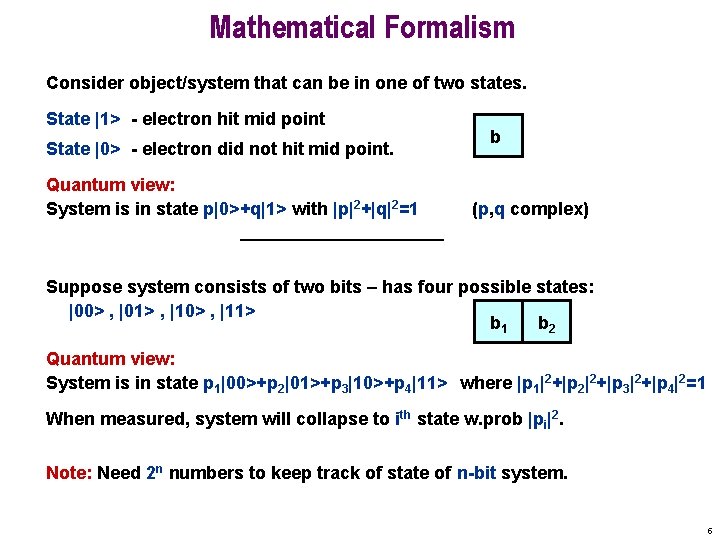
Mathematical Formalism Consider object/system that can be in one of two states. State |1> - electron hit mid point State |0> - electron did not hit mid point. Quantum view: System is in state p|0>+q|1> with |p|2+|q|2=1 b (p, q complex) Suppose system consists of two bits – has four possible states: |00> , |01> , |10> , |11> b 1 b 2 Quantum view: System is in state p 1|00>+p 2|01>+p 3|10>+p 4|11> where |p 1|2+|p 2|2+|p 3|2+|p 4|2=1 When measured, system will collapse to ith state w. prob |pi|2. Note: Need 2 n numbers to keep track of state of n-bit system. 5

World View Democritos Newton Einstein: Underlying everything are small particles interacting locally using simple well-defined rules (“billiard balls”). Quantum Mechanics: Nature has a secret HUGE piece of paper containing >2100000000 complex numbers, keeping track of a superposition of all particles in the world, but allows us only to make some specific measurements of these numbers. “Corollary”: We do not know how to simulate quantum system of n particles for t time units in time poly(n. t). Rephrase: There are some computations performed by quantum systems of n particles and t time units that we don’t know to perform in a classical computer in time poly(n, t) Maybe can use quantum system to solve hard computational problems? ? 6

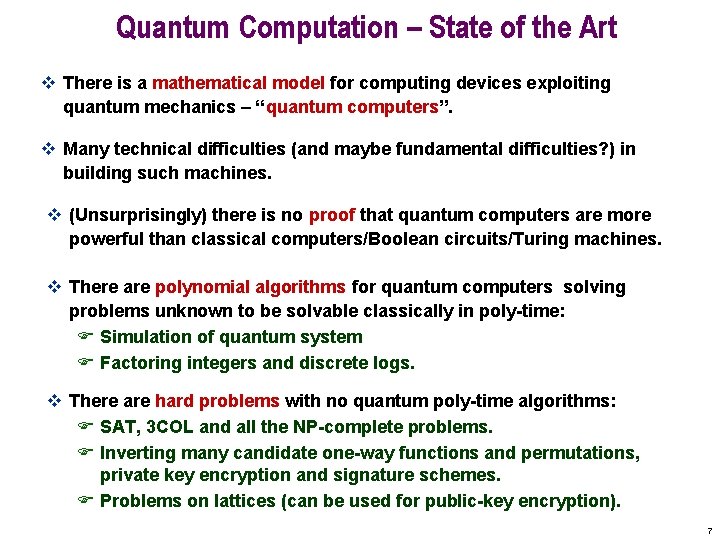
Quantum Computation – State of the Art v There is a mathematical model for computing devices exploiting quantum mechanics – “quantum computers”. v Many technical difficulties (and maybe fundamental difficulties? ) in building such machines. v (Unsurprisingly) there is no proof that quantum computers are more powerful than classical computers/Boolean circuits/Turing machines. v There are polynomial algorithms for quantum computers solving problems unknown to be solvable classically in poly-time: F Simulation of quantum system F Factoring integers and discrete logs. v There are hard problems with no quantum poly-time algorithms: F SAT, 3 COL and all the NP-complete problems. F Inverting many candidate one-way functions and permutations, private key encryption and signature schemes. F Problems on lattices (can be used for public-key encryption). 7

Quantum Computation And Cryptography v If quantum computers can be built, then many popular encryption and signature schemes can be broken (RSA, Diffie-Hellman) v However, there are still other candidates for encryption schemes not known to be broken. This is especially true for private key cryptography and signature schemes. v Many (but not all) of the proofs of security in crypto carry over from the classical model to the quantum model, as long as the underlying hard problem is assumed hard for quantum computers. v Exciting possibilities of using quantum mechanics to obtain perfectly unconditionally secure cryptography. Does not require full fledged quantum computers – prototype systems already being built. Quantum Key Distribution (QKD) 8

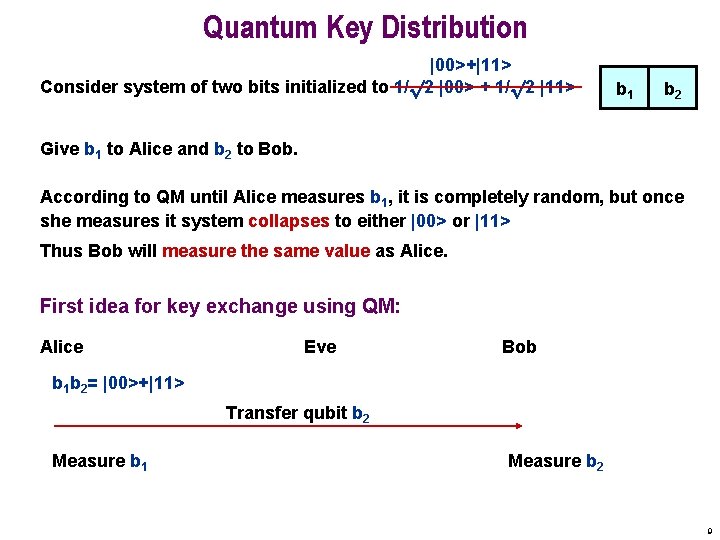
Quantum Key Distribution |00>+|11> Consider system of two bits initialized to 1/p 2 |00> + 1/p 2 |11> b 1 b 2 Give b 1 to Alice and b 2 to Bob. According to QM until Alice measures b 1, it is completely random, but once she measures it system collapses to either |00> or |11> Thus Bob will measure the same value as Alice. First idea for key exchange using QM: Alice Eve Bob b 1 b 2= |00>+|11> Transfer qubit b 2 Measure b 1 Measure b 2 9

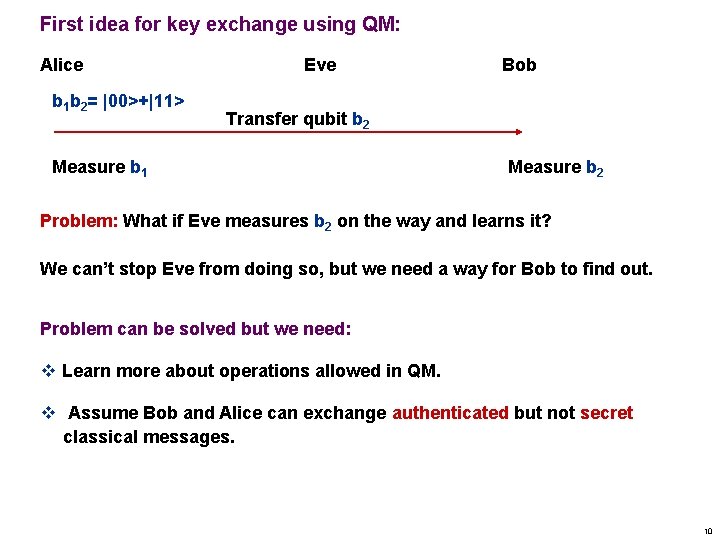
First idea for key exchange using QM: Alice b 1 b 2= |00>+|11> Eve Bob Transfer qubit b 2 Measure b 1 Measure b 2 Problem: What if Eve measures b 2 on the way and learns it? We can’t stop Eve from doing so, but we need a way for Bob to find out. Problem can be solved but we need: v Learn more about operations allowed in QM. v Assume Bob and Alice can exchange authenticated but not secret classical messages. 10

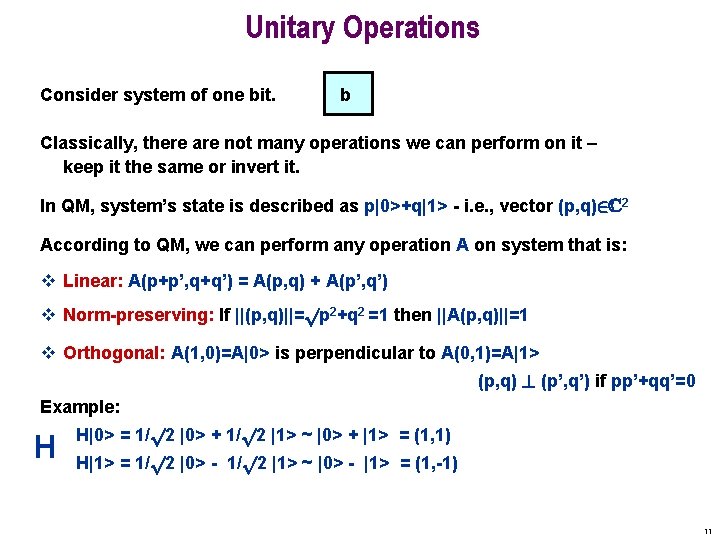
Unitary Operations Consider system of one bit. b Classically, there are not many operations we can perform on it – keep it the same or invert it. In QM, system’s state is described as p|0>+q|1> - i. e. , vector (p, q)2 C 2 According to QM, we can perform any operation A on system that is: v Linear: A(p+p’, q+q’) = A(p, q) + A(p’, q’) v Norm-preserving: If ||(p, q)||=pp 2+q 2 =1 then ||A(p, q)||=1 v Orthogonal: A(1, 0)=A|0> is perpendicular to A(0, 1)=A|1> (p, q) ? (p’, q’) if pp’+qq’=0 Example: H H|0> = 1/p 2 |0> + 1/p 2 |1> ~ |0> + |1> = (1, 1) H|1> = 1/p 2 |0> - 1/p 2 |1> ~ |0> - |1> = (1, -1) 11

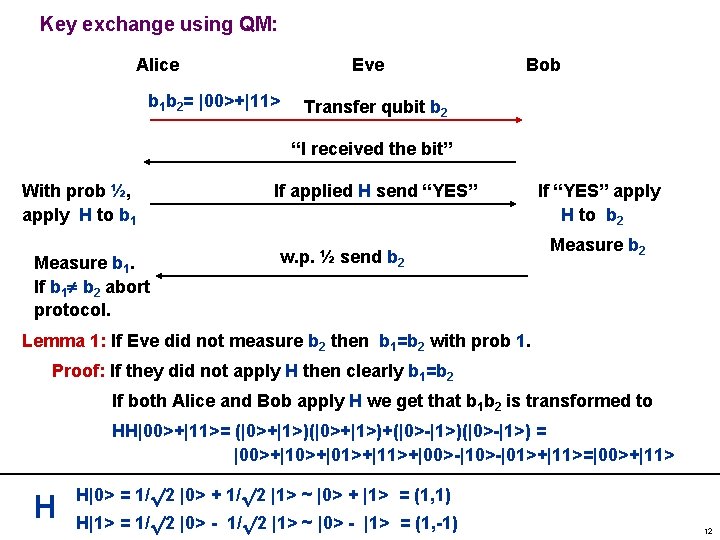
Key exchange using QM: Alice Eve b 1 b 2= |00>+|11> Bob Transfer qubit b 2 “I received the bit” With prob ½, apply H to b 1 Measure b 1. If b 1 b 2 abort protocol. If applied H send “YES” w. p. ½ send b 2 If “YES” apply H to b 2 Measure b 2 Lemma 1: If Eve did not measure b 2 then b 1=b 2 with prob 1. Proof: If they did not apply H then clearly b 1=b 2 If both Alice and Bob apply H we get that b 1 b 2 is transformed to HH|00>+|11>= (|0>+|1>)+(|0>-|1>) = |00>+|10>+|01>+|11>+|00>-|10>-|01>+|11>=|00>+|11> H H|0> = 1/p 2 |0> + 1/p 2 |1> ~ |0> + |1> = (1, 1) H|1> = 1/p 2 |0> - 1/p 2 |1> ~ |0> - |1> = (1, -1) 12

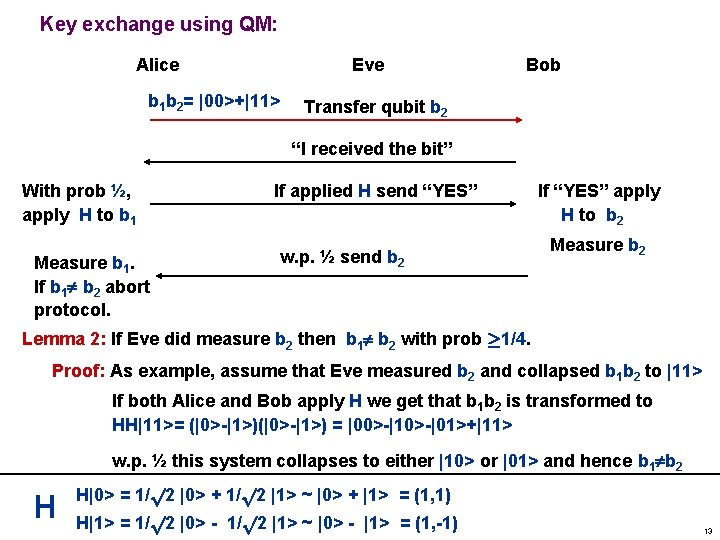
Key exchange using QM: Alice Eve b 1 b 2= |00>+|11> Bob Transfer qubit b 2 “I received the bit” With prob ½, apply H to b 1 Measure b 1. If b 1 b 2 abort protocol. If applied H send “YES” w. p. ½ send b 2 If “YES” apply H to b 2 Measure b 2 Lemma 2: If Eve did measure b 2 then b 1 b 2 with prob ¸ 1/4. Proof: As example, assume that Eve measured b 2 and collapsed b 1 b 2 to |11> If both Alice and Bob apply H we get that b 1 b 2 is transformed to HH|11>= (|0>-|1>) = |00>-|10>-|01>+|11> w. p. ½ this system collapses to either |10> or |01> and hence b 1 b 2 H H|0> = 1/p 2 |0> + 1/p 2 |1> ~ |0> + |1> = (1, 1) H|1> = 1/p 2 |0> - 1/p 2 |1> ~ |0> - |1> = (1, -1) 13

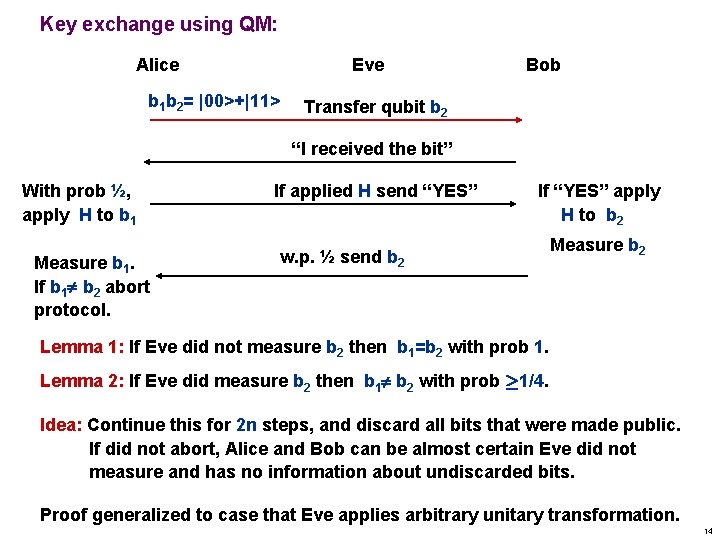
Key exchange using QM: Alice Eve b 1 b 2= |00>+|11> Bob Transfer qubit b 2 “I received the bit” With prob ½, apply H to b 1 Measure b 1. If b 1 b 2 abort protocol. If applied H send “YES” If “YES” apply H to b 2 w. p. ½ send b 2 Measure b 2 Lemma 1: If Eve did not measure b 2 then b 1=b 2 with prob 1. Lemma 2: If Eve did measure b 2 then b 1 b 2 with prob ¸ 1/4. Idea: Continue this for 2 n steps, and discard all bits that were made public. If did not abort, Alice and Bob can be almost certain Eve did not measure and has no information about undiscarded bits. Proof generalized to case that Eve applies arbitrary unitary transformation. 14