Computer Networks 20022003 Routing Johan Lukkien 12142021 Johan



- Slides: 33

Computer Networks 2002/2003 Routing Johan Lukkien 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 1

Layer tasks • Basic service – addressing, data format, fragmentation, congestion, error messages • Neighbor greeting – configuration: routers find out about their environment, (other routers, endstations) • Routing – forwarding, route computation & selection – methods, protocols • dynamic, based on metrics (e. g. , delay, bandwidth, link error rate) or static • Quality of the service • Requirements: – robustness, stability – preferable: automatic configuration (e. g. assigning addresses) • Slides following: assume connection-less service 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 2

Neighbor greeting • . . (Auto-)configuration • End nodes – find adjacent routers – see difference between locally accessible nodes and those accessible through a router – find link addresses of adjacent nodes – find out own network address • Routers, in addition – find network addresses of end nodes • Note – dependent on type of connection (point-to-point, LAN) 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 3

Soft state • Typically, state information that is only temporary valid – values of variables of other processes, machines – state of environment, connections • in principle, invalidation is interference • Note: making copies violates the principle: “never copy volatile information” – however, for scalability a replication strategy of shared objects is needed • Methods to maintain consistency – send updates & ‘keep-alive’ messages • depends on modification frequency & timers – only upon interaction, request ‘I’m alive’ message • e. g. refresh a router table entry only upon message sent 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 4

Finding things: service advertisement & discovery • Use a –local– database – e. g. look it up in a phone book • Use a special location to find that database – e. g. dial the telephone directory service • giving either the nearest or all service providers • Broadcast what you’re looking for – dial a number that rings all phones and tell what you ned • Broadcast the service that you provide – dial the same number and tell what you’ve got 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 5

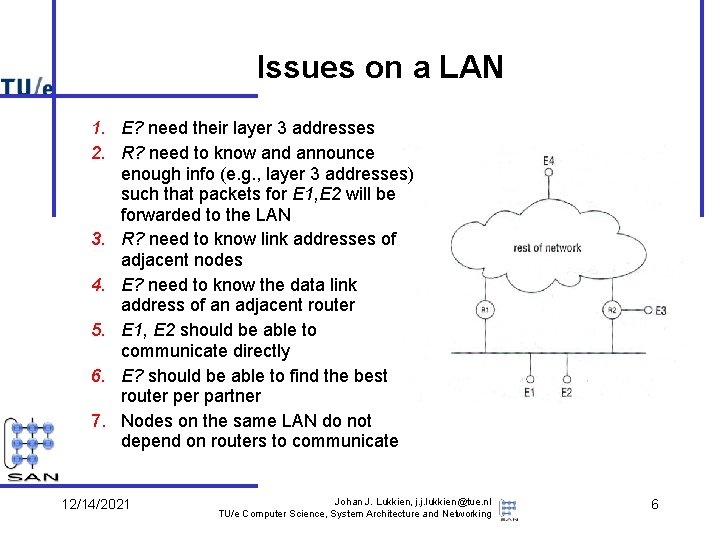
Issues on a LAN 1. E? need their layer 3 addresses 2. R? need to know and announce enough info (e. g. , layer 3 addresses) such that packets for E 1, E 2 will be forwarded to the LAN 3. R? need to know link addresses of adjacent nodes 4. E? need to know the data link address of an adjacent router 5. E 1, E 2 should be able to communicate directly 6. E? should be able to find the best router partner 7. Nodes on the same LAN do not depend on routers to communicate 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 6

IP solutions • Routers know network number and mask of each of their outgoing links (2) – manually configured • On that link you find the link address of the next hop (endnode or router) through the Address Resolution Protocol (3, 5, 7) • A router can send an ICMP ‘redirect’ message: “for D, use this router IP, not me” (6) – why IP and not data link address? 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 7

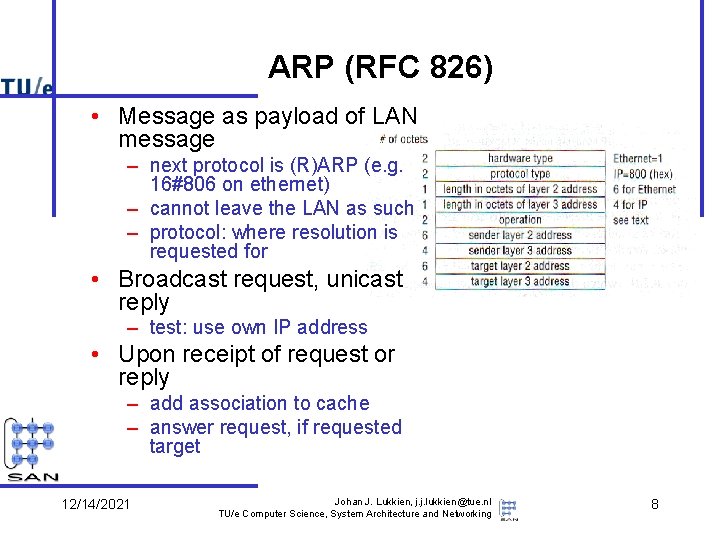
ARP (RFC 826) • Message as payload of LAN message – next protocol is (R)ARP (e. g. 16#806 on ethernet) – cannot leave the LAN as such – protocol: where resolution is requested for • Broadcast request, unicast reply – test: use own IP address • Upon receipt of request or reply – add association to cache – answer request, if requested target 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 8

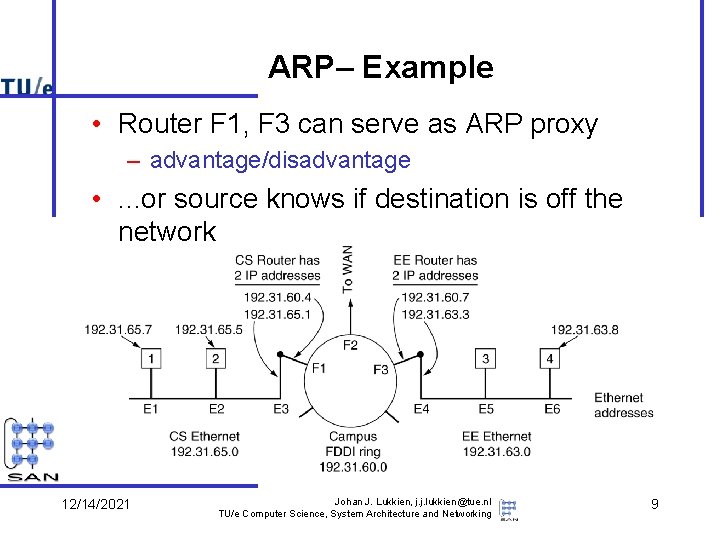
ARP– Example • Router F 1, F 3 can serve as ARP proxy – advantage/disadvantage • . . . or source knows if destination is off the network 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 9

Reverse ARP (RFC 903), BOOTP (RFC 951) • Find IP address corresponding to given data link address (1) – basic auto-configuration – although it needs a server that is configured with this association • Extended into BOOTP (1, 4) – message in IP packet • router (“relay agents”) can forward the message • how to deal with addressing? – can specify a host/bootfile combination – vendor specific options • rather than (type, length, value) encoded fields • repaired by the special vendor-specific field 63. 82. 53. 63 (4 bytes, hex. ). . “magic cookie” 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 10

DHCP (1, 4) • Extends BOOTP – packet includes magic cookie and option 16#53 • Extra’s – dynamic address assignment • • 12/14/2021 using leases re-use of addresses no database needed no addresses needed for powered-off nodes Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 11

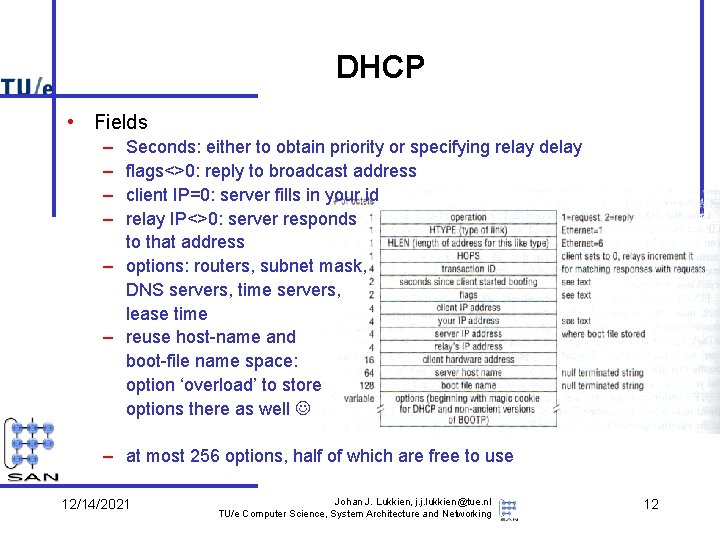
DHCP • Fields – – Seconds: either to obtain priority or specifying relay delay flags<>0: reply to broadcast address client IP=0: server fills in your id relay IP<>0: server responds to that address – options: routers, subnet mask, DNS servers, time servers, lease time – reuse host-name and boot-file name space: option ‘overload’ to store options there as well – at most 256 options, half of which are free to use 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 12

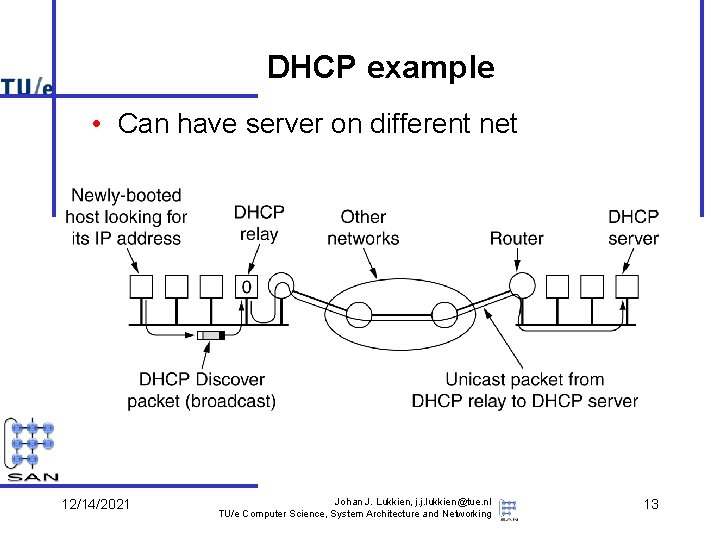
DHCP example • Can have server on different net 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 13

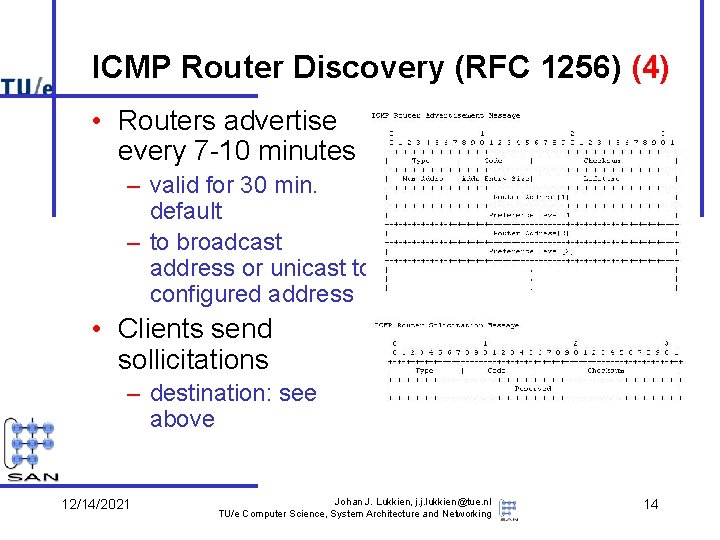
ICMP Router Discovery (RFC 1256) (4) • Routers advertise every 7 -10 minutes – valid for 30 min. default – to broadcast address or unicast to configured address • Clients send sollicitations – destination: see above 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 14

IPX solutions • Node number is link local address • Broadcast request for network number (1, 3, 5, 7) – no reply: 0 • Broadcast request for best router to given destination network (4, 6) – replying router is indeed alive 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 15

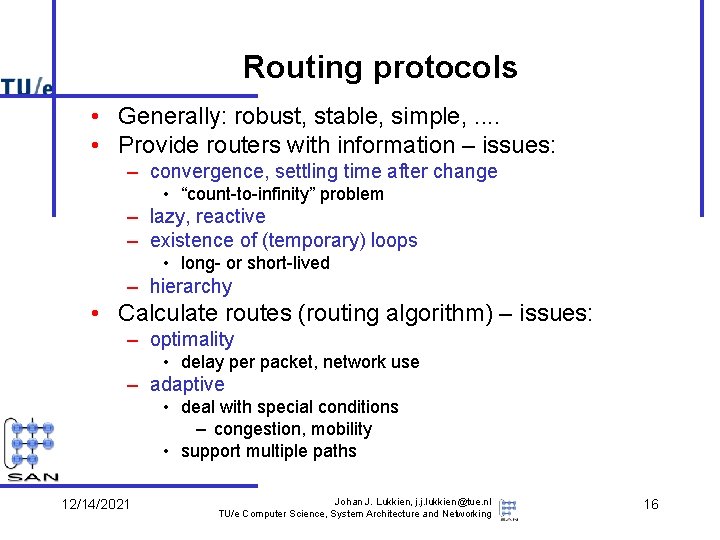
Routing protocols • Generally: robust, stable, simple, . . • Provide routers with information – issues: – convergence, settling time after change • “count-to-infinity” problem – lazy, reactive – existence of (temporary) loops • long- or short-lived – hierarchy • Calculate routes (routing algorithm) – issues: – optimality • delay per packet, network use – adaptive • deal with special conditions – congestion, mobility • support multiple paths 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 16

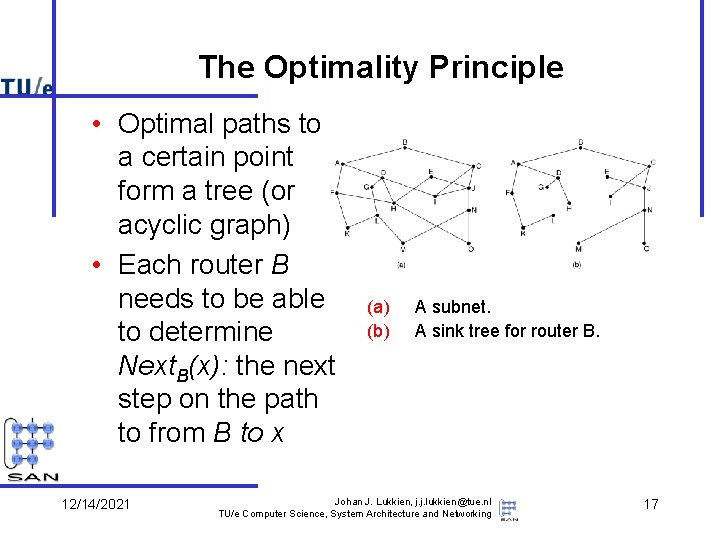
The Optimality Principle • Optimal paths to a certain point form a tree (or acyclic graph) • Each router B needs to be able to determine Next. B(x): the next step on the path to from B to x 12/14/2021 (a) (b) A subnet. A sink tree for router B. Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 17

Determine the tables • Using a distributed algorithm – distributed shortest path • similar to distributed spanning tree but now for each node as root – basis for “Distance Vector Routing” • Using a local, sequential algorithm – based on information obtained directly from the point of change • e. g. locally, the shortest path algorithm of Dijkstra – basis for “Link State Routing” 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 18

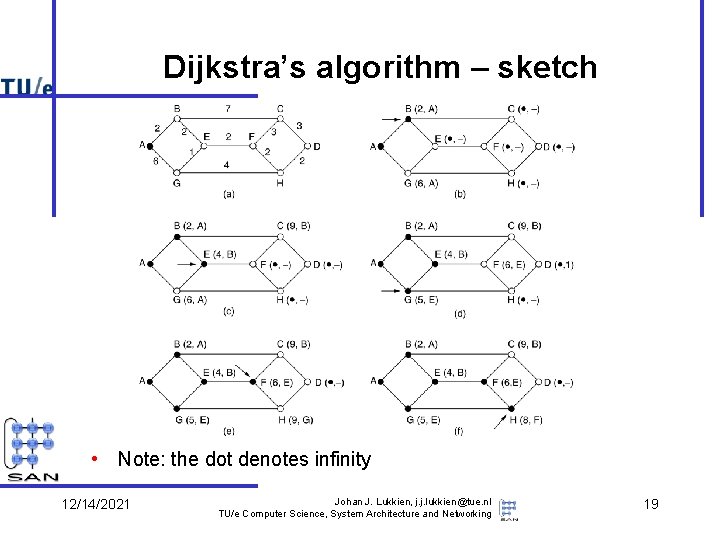
Dijkstra’s algorithm – sketch • Note: the dot denotes infinity 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 19

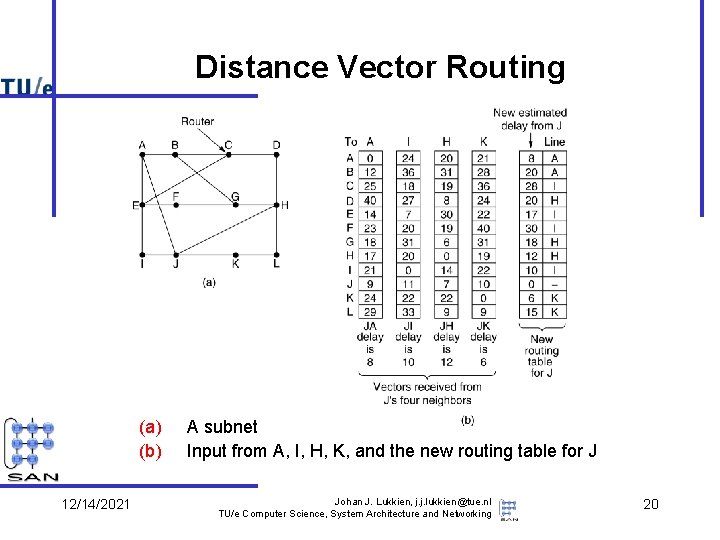
Distance Vector Routing (a) (b) 12/14/2021 A subnet Input from A, I, H, K, and the new routing table for J Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 20

“Counting to infinity” • Good news spreads rapidly • Bad news spreads slowly – since the distance to a destination D through a neighbor cannot differ very much from your own 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 21

Link State Routing • Each router does the following (repeatedly): – discover neighbors, particularly, learn their network addresses • using one of the neighbor discovery methods discussed before – measure cost to each neighbor • e. g. by exchanging a series of packets – construct a packet containing this – send this packet to all other routers • using what route information? chicken / egg • what if re-ordered? or delayed? – compute locally the shortest path to every other router when this information is received 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 22

Distributing the Link State Packets • Typically, flooding – routers recognize packets passed earlier • sequence number • thus avoiding the exponential packet explosion – first receivers start changes already while changes are being reported – sequence numbers wrap around or might be corrupted • add an additional age field that is decremented once a second – packets won’t be too long in the system • but, need additional robustness in order to deal with effect of packet forgeing – acknowledgements 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 23

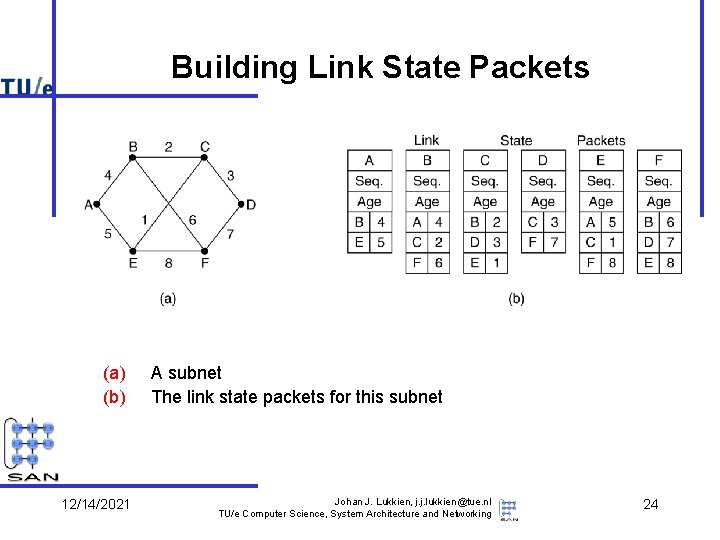
Building Link State Packets (a) (b) 12/14/2021 A subnet The link state packets for this subnet Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 24

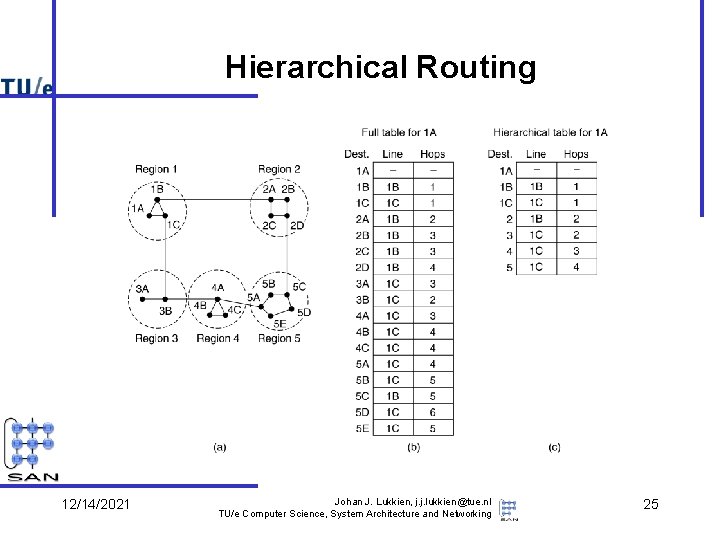
Hierarchical Routing 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 25

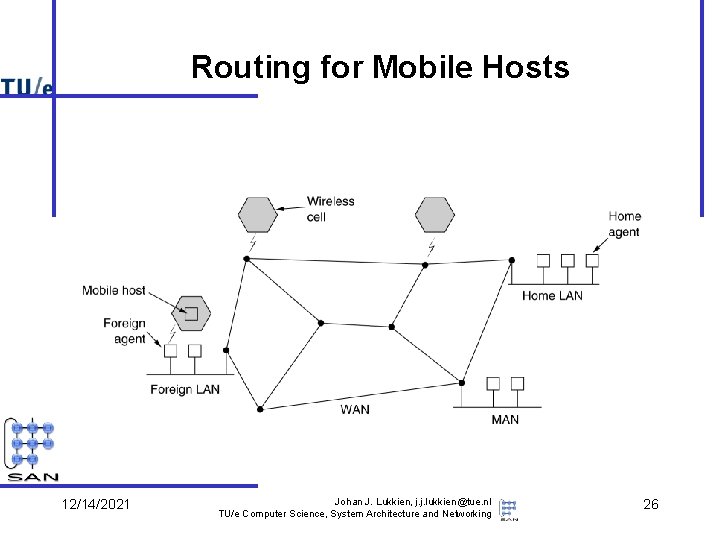
Routing for Mobile Hosts 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 26

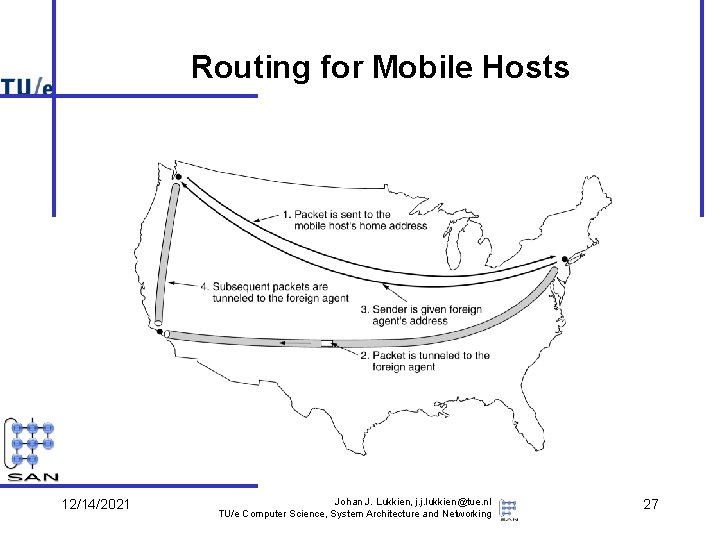
Routing for Mobile Hosts 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 27

The IP way • Internet is made up of autonomous systems (AS) – routing within an AS: interior gateway protocol • originally, RIP – routing information protocol – distance vector, derived from Bellman-Ford • first link state protocol was not robust enough • Open Shortest Path First: (OSPF) since ‘ 90 – routing between AS’s: exterior gateway protocol • Border Routing Protocol 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 28

OSPF • Resources assumed to be freely usable since within AS • Requirements – Open, known to everyone – Support several metrics – Dynamic adaptation • note: stability is important here – – 12/14/2021 Use multiple paths – load balancing Hierarchy Safeguard against forged routing info Tunneling support Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 29

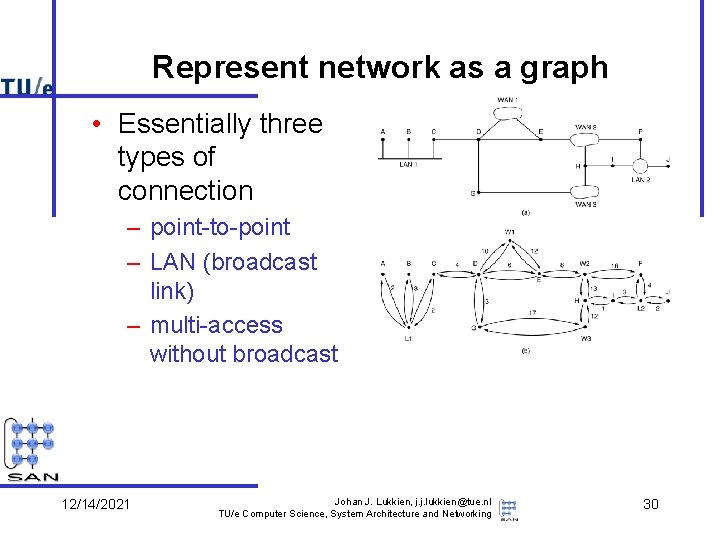
Represent network as a graph • Essentially three types of connection – point-to-point – LAN (broadcast link) – multi-access without broadcast 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 30

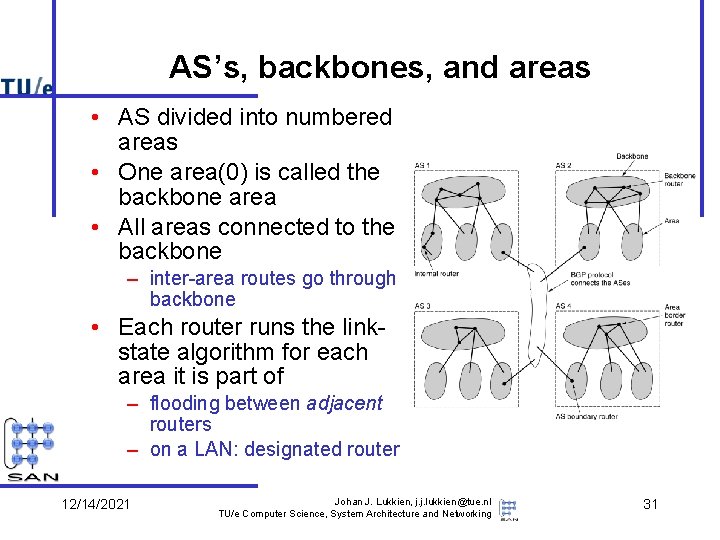
AS’s, backbones, and areas • AS divided into numbered areas • One area(0) is called the backbone area • All areas connected to the backbone – inter-area routes go through backbone • Each router runs the linkstate algorithm for each area it is part of – flooding between adjacent routers – on a LAN: designated router 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 31

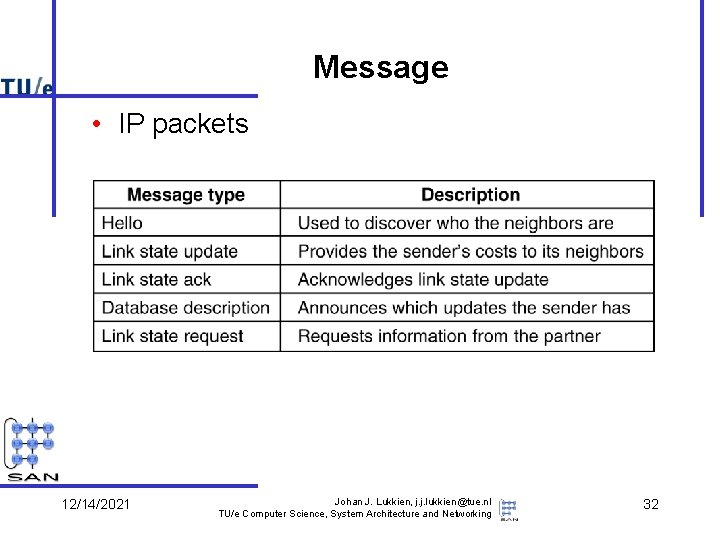
Message • IP packets 5 -66 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 32

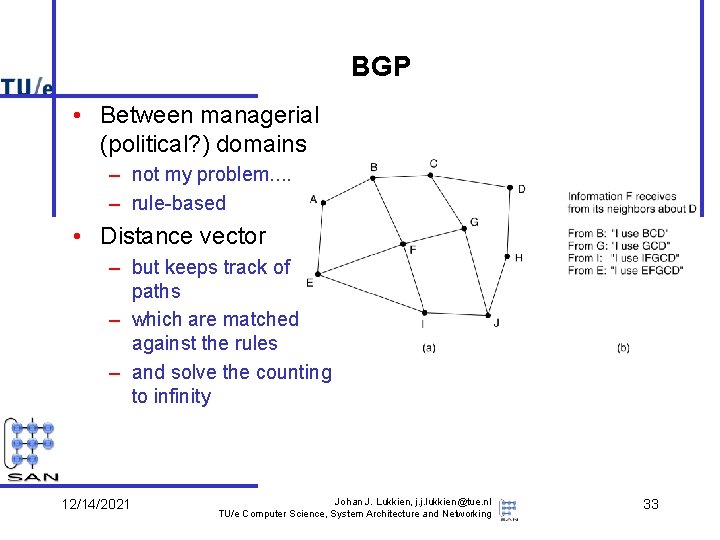
BGP • Between managerial (political? ) domains – not my problem. . – rule-based • Distance vector – but keeps track of paths – which are matched against the rules – and solve the counting to infinity 12/14/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 33
 Johan lukkien
Johan lukkien Johan lukkien
Johan lukkien Tunnel traffic
Tunnel traffic Johan lukkien
Johan lukkien 20022003 color
20022003 color Computer networks routing algorithms
Computer networks routing algorithms Broadcast routing in computer networks
Broadcast routing in computer networks Datagram vs virtual circuit
Datagram vs virtual circuit Backbone networks in computer networks
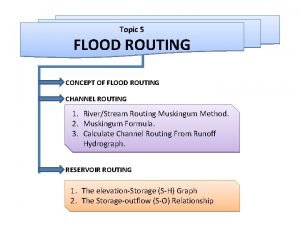
Backbone networks in computer networks Reservoir flood routing worked examples
Reservoir flood routing worked examples Mark tinka
Mark tinka Continuity equation hydrology
Continuity equation hydrology Comparison of clock routing and power routing
Comparison of clock routing and power routing Three generations of multicomputers
Three generations of multicomputers Crc in computer networks
Crc in computer networks Crc in computer networks
Crc in computer networks Traffic management in computer networks
Traffic management in computer networks Speed of a computer
Speed of a computer What is optimality principle in computer networks
What is optimality principle in computer networks Snmp ports
Snmp ports What is optimality principle in computer networks
What is optimality principle in computer networks Business application of computer network
Business application of computer network Classify computer networks based on transmission technology
Classify computer networks based on transmission technology Intro dns
Intro dns Diffserv vs intserv
Diffserv vs intserv Icmp in computer networks
Icmp in computer networks Http computer networks
Http computer networks Framing in computer network
Framing in computer network Dns in computer networks
Dns in computer networks Data communication and networking assignment questions
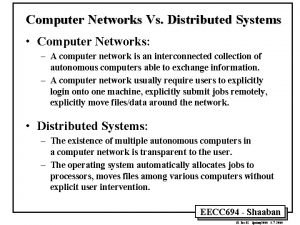
Data communication and networking assignment questions Distributed system in computer network
Distributed system in computer network Crc example
Crc example Error detection in computer networks
Error detection in computer networks Internet transport protocol in computer networks
Internet transport protocol in computer networks