Computer Networks 20022003 Connections Johan Lukkien 642021 Johan

- Slides: 22

Computer Networks 2002/2003 Connections Johan Lukkien 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 1

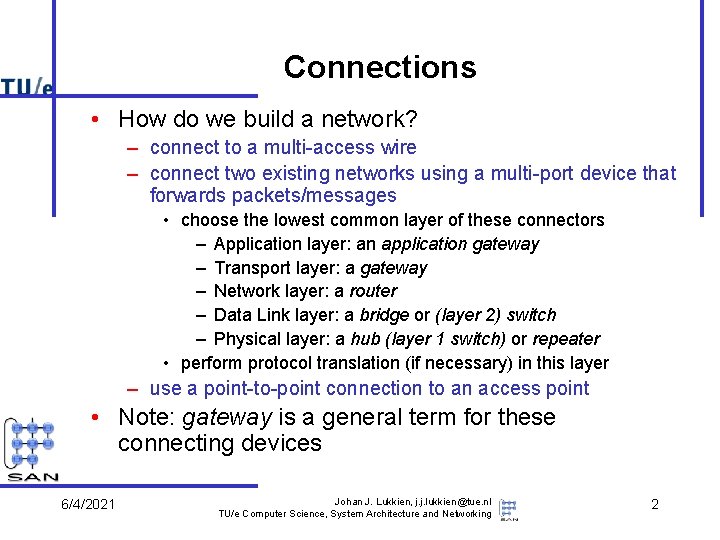
Connections • How do we build a network? – connect to a multi-access wire – connect two existing networks using a multi-port device that forwards packets/messages • choose the lowest common layer of these connectors – Application layer: an application gateway – Transport layer: a gateway – Network layer: a router – Data Link layer: a bridge or (layer 2) switch – Physical layer: a hub (layer 1 switch) or repeater • perform protocol translation (if necessary) in this layer – use a point-to-point connection to an access point • Note: gateway is a general term for these connecting devices 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 2

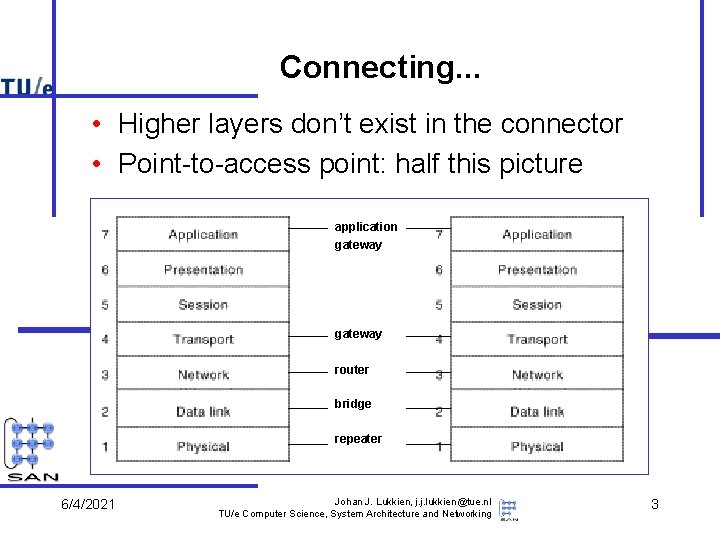
Connecting. . . • Higher layers don’t exist in the connector • Point-to-access point: half this picture application gateway router bridge repeater 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 3

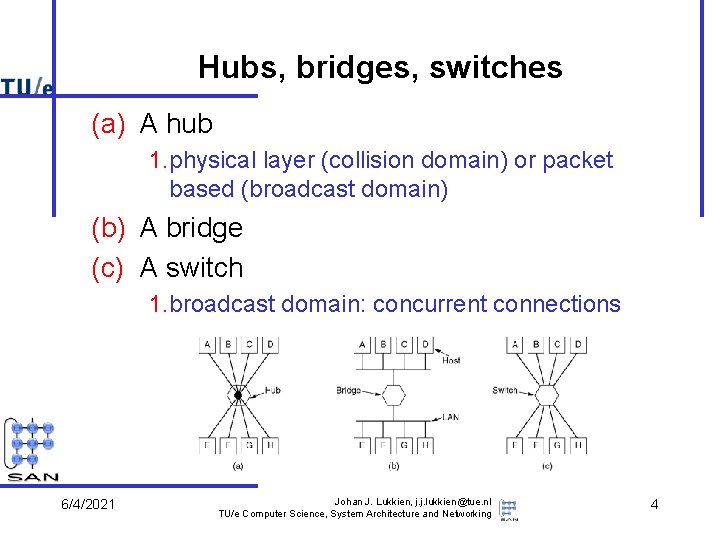
Hubs, bridges, switches (a) A hub 1. physical layer (collision domain) or packet based (broadcast domain) (b) A bridge (c) A switch 1. broadcast domain: concurrent connections 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 4

Bridge • Connect two networks through frame transport – transparently • invisible to connected stations • not entirely possible in case of different standards – need to buffer frames temporarily • speed, availability differences • leads to potential frame dropping – effectively, constructs a single broadcast domain out of several networks • flooding + adjustments – originally two, but currently many ports – distinction bridge-switch is floating 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 5

Bridge operation • Flooding: – “Promiscuous” listening on all ports – Upon receipt of a packet via a port p • transmit packet via each port q, q <> p • Notes – this bridge does not need a link layer address, in principle • though standard port hardware has it integrated 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 6

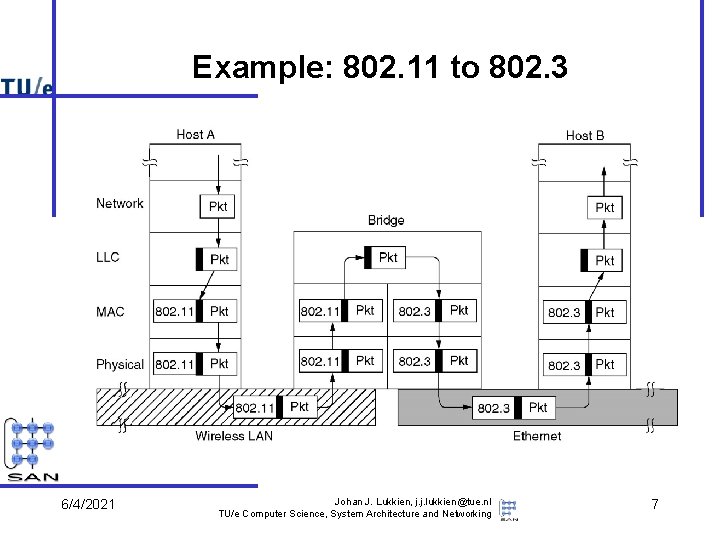
Example: 802. 11 to 802. 3 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 7

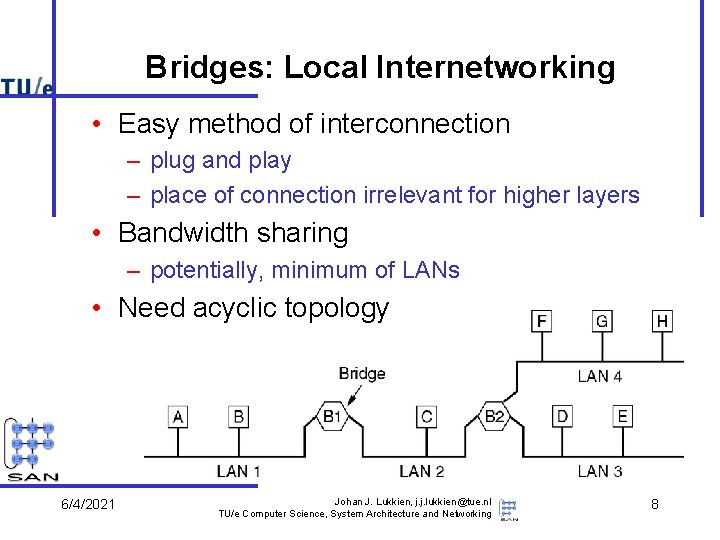
Bridges: Local Internetworking • Easy method of interconnection – plug and play – place of connection irrelevant for higher layers • Bandwidth sharing – potentially, minimum of LANs • Need acyclic topology 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 8

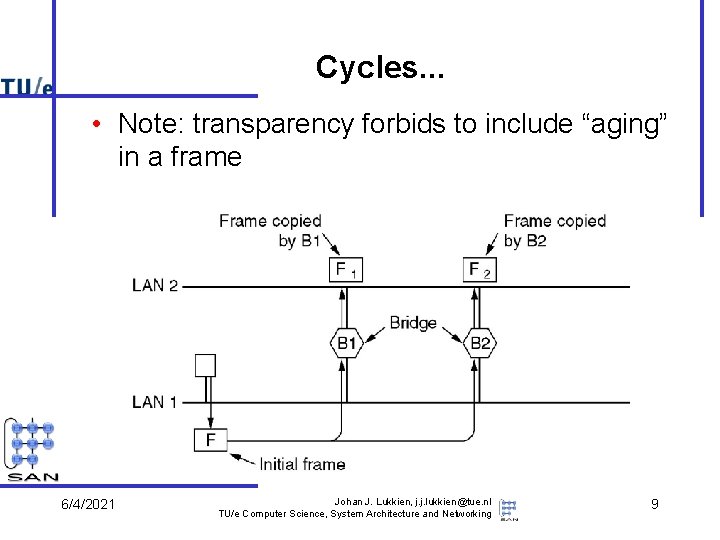
Cycles. . . • Note: transparency forbids to include “aging” in a frame 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 9

Limit the broadcasting • Configure – configuration database in bridge – assign address ranges to stations in a particular way • e. g. part of the address determines the LAN • difficult because of the MAC address structure – conflicts stability, auto-configuration requirements • Learning bridges – construct dynamically a mapping from MAC addresses to ports • inspect sources in packets and build table • needs a potentially large amount of memory – this information is only temporarily valid: “soft state” – same problem with cycles 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 10

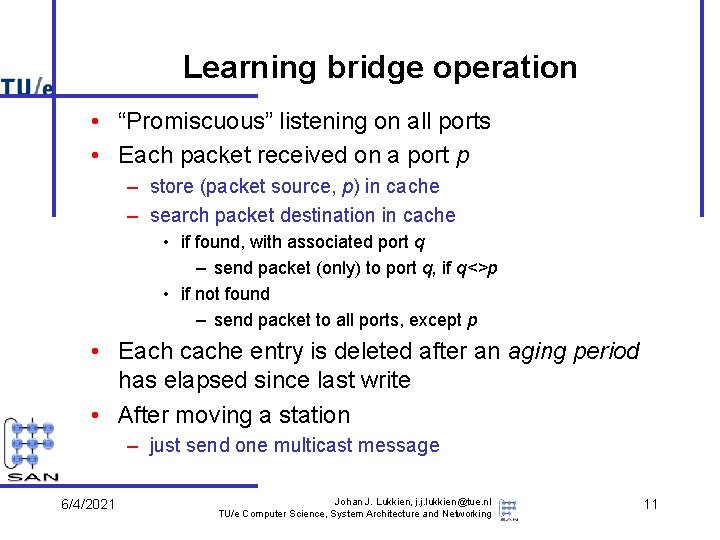
Learning bridge operation • “Promiscuous” listening on all ports • Each packet received on a port p – store (packet source, p) in cache – search packet destination in cache • if found, with associated port q – send packet (only) to port q, if q<>p • if not found – send packet to all ports, except p • Each cache entry is deleted after an aging period has elapsed since last write • After moving a station – just send one multicast message 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 11

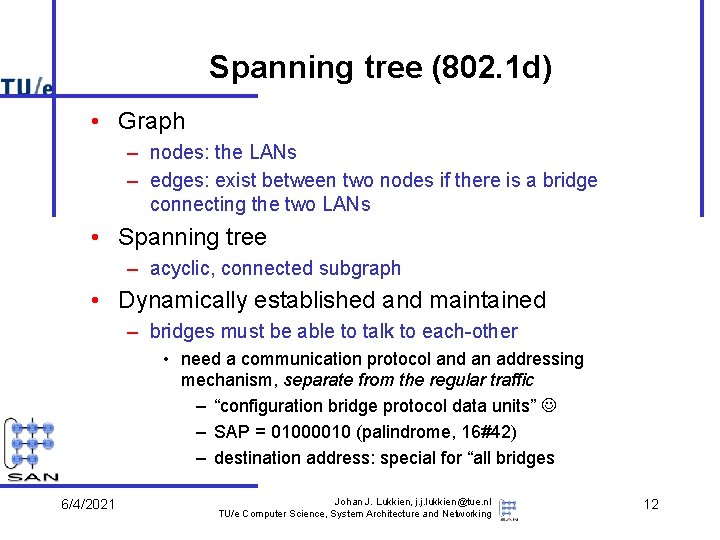
Spanning tree (802. 1 d) • Graph – nodes: the LANs – edges: exist between two nodes if there is a bridge connecting the two LANs • Spanning tree – acyclic, connected subgraph • Dynamically established and maintained – bridges must be able to talk to each-other • need a communication protocol and an addressing mechanism, separate from the regular traffic – “configuration bridge protocol data units” – SAP = 01000010 (palindrome, 16#42) – destination address: special for “all bridges 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 12

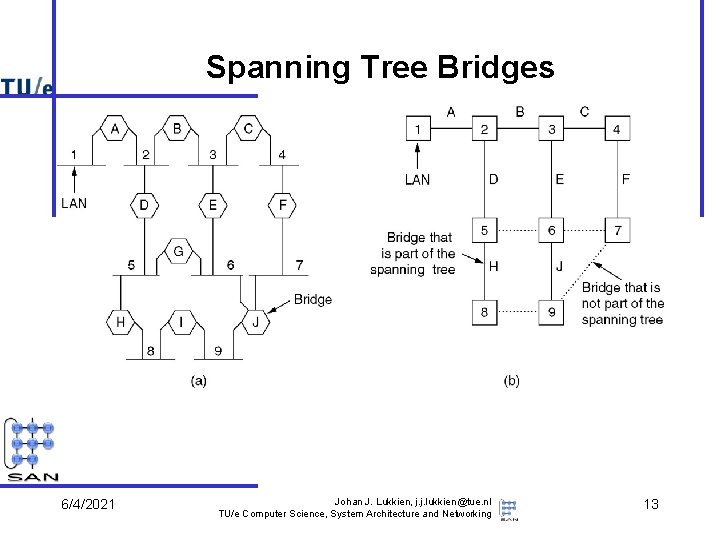
Spanning Tree Bridges 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 13

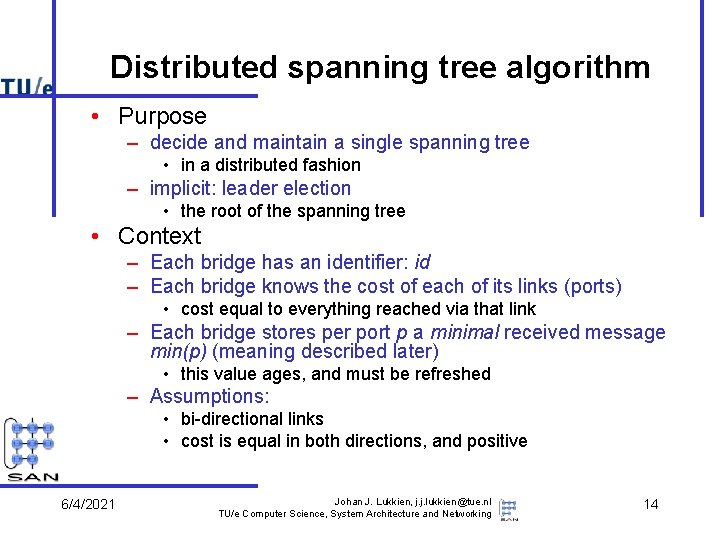
Distributed spanning tree algorithm • Purpose – decide and maintain a single spanning tree • in a distributed fashion – implicit: leader election • the root of the spanning tree • Context – Each bridge has an identifier: id – Each bridge knows the cost of each of its links (ports) • cost equal to everything reached via that link – Each bridge stores per port p a minimal received message min(p) (meaning described later) • this value ages, and must be refreshed – Assumptions: • bi-directional links • cost is equal in both directions, and positive 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 14

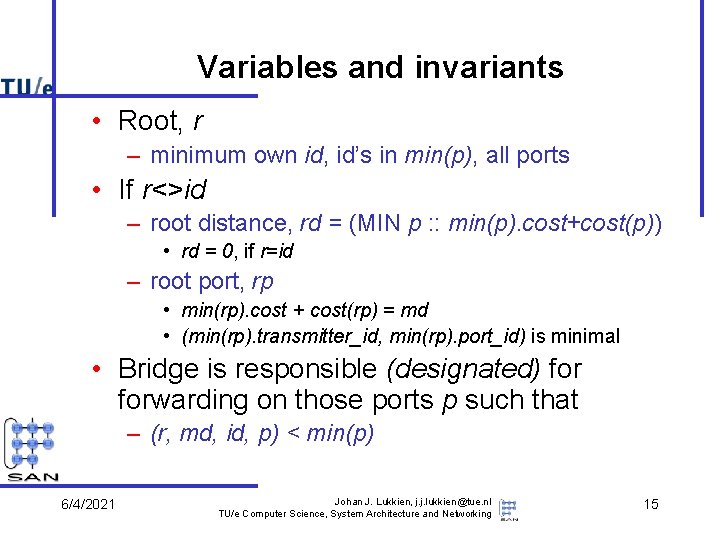
Variables and invariants • Root, r – minimum own id, id’s in min(p), all ports • If r<>id – root distance, rd = (MIN p : : min(p). cost+cost(p)) • rd = 0, if r=id – root port, rp • min(rp). cost + cost(rp) = md • (min(rp). transmitter_id, min(rp). port_id) is minimal • Bridge is responsible (designated) forwarding on those ports p such that – (r, md, id, p) < min(p) 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 15

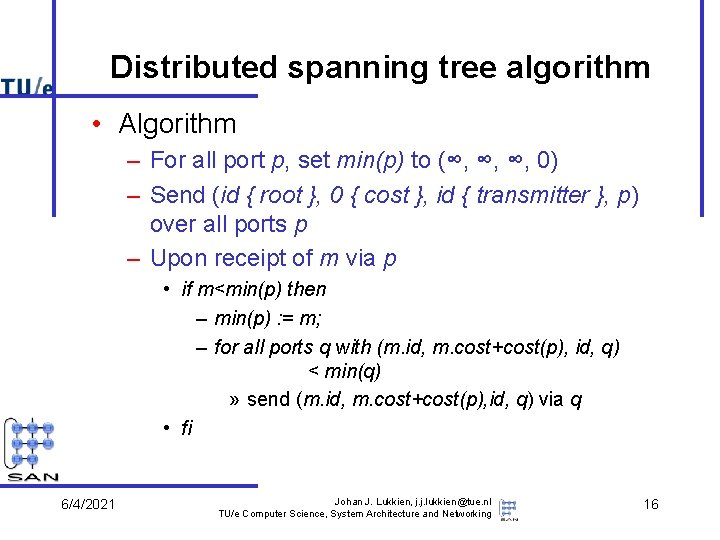
Distributed spanning tree algorithm • Algorithm – For all port p, set min(p) to (∞, ∞, ∞, 0) – Send (id { root }, 0 { cost }, id { transmitter }, p) over all ports p – Upon receipt of m via p • if m<min(p) then – min(p) : = m; – for all ports q with (m. id, m. cost+cost(p), id, q) < min(q) » send (m. id, m. cost+cost(p), id, q) via q • fi 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 16

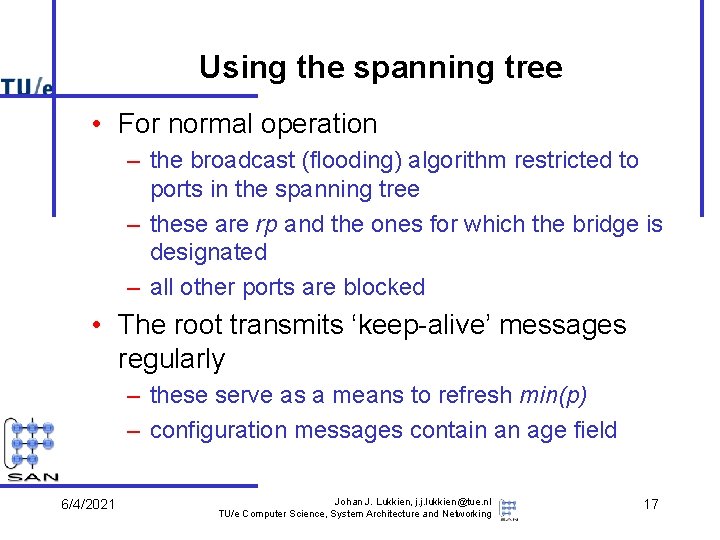
Using the spanning tree • For normal operation – the broadcast (flooding) algorithm restricted to ports in the spanning tree – these are rp and the ones for which the bridge is designated – all other ports are blocked • The root transmits ‘keep-alive’ messages regularly – these serve as a means to refresh min(p) – configuration messages contain an age field 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 17

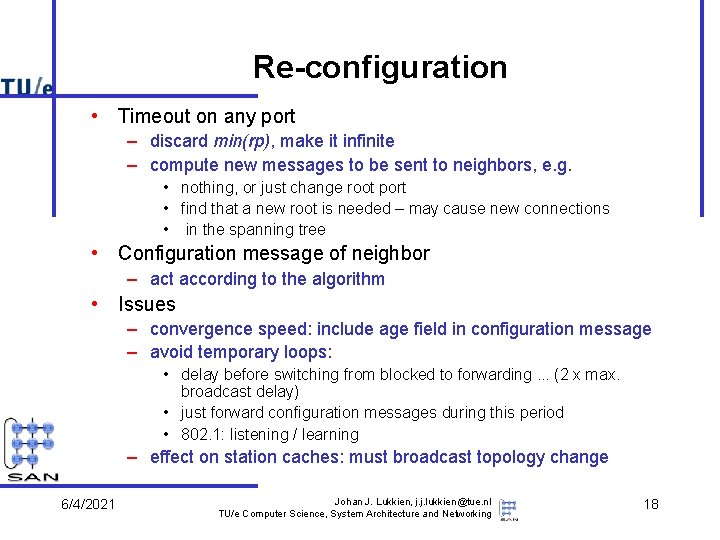
Re-configuration • Timeout on any port – discard min(rp), make it infinite – compute new messages to be sent to neighbors, e. g. • nothing, or just change root port • find that a new root is needed – may cause new connections • in the spanning tree • Configuration message of neighbor – act according to the algorithm • Issues – convergence speed: include age field in configuration message – avoid temporary loops: • delay before switching from blocked to forwarding. . . (2 x max. broadcast delay) • just forward configuration messages during this period • 802. 1: listening / learning – effect on station caches: must broadcast topology change 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 18

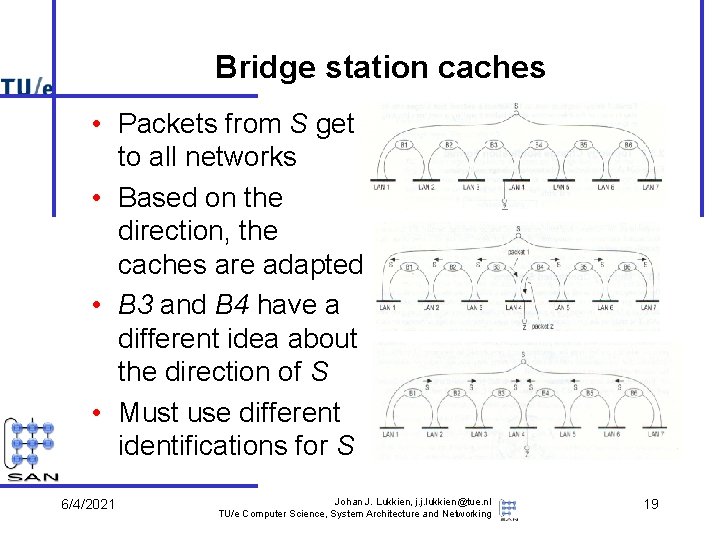
Bridge station caches • Packets from S get to all networks • Based on the direction, the caches are adapted • B 3 and B 4 have a different idea about the direction of S • Must use different identifications for S 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking Z 19

Transparent? • Increased probability of – packet loss – errors • packet reordering and duplicates may now occur • Increase of – delay – packet life time • Maximum packet size is LAN-dependent • LAN-specific information gets lost – e. g. ethernet / 802. 3 • Assumptions – MAC address unique – a receiving station will also transmit 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 20

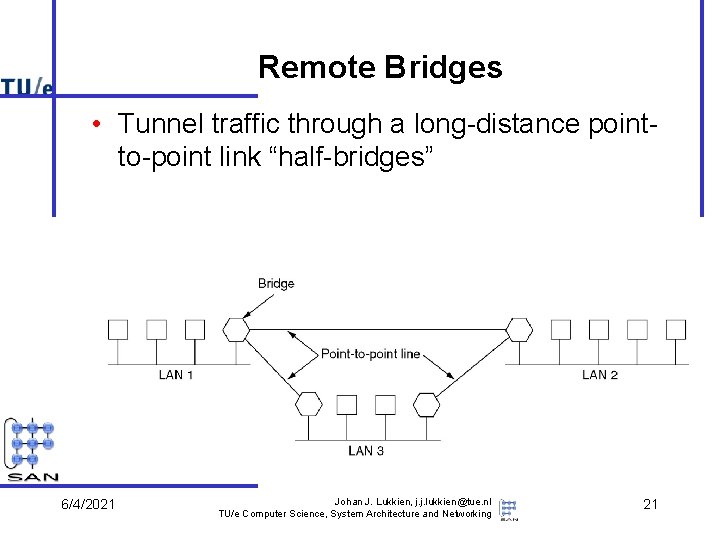
Remote Bridges • Tunnel traffic through a long-distance pointto-point link “half-bridges” 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 21

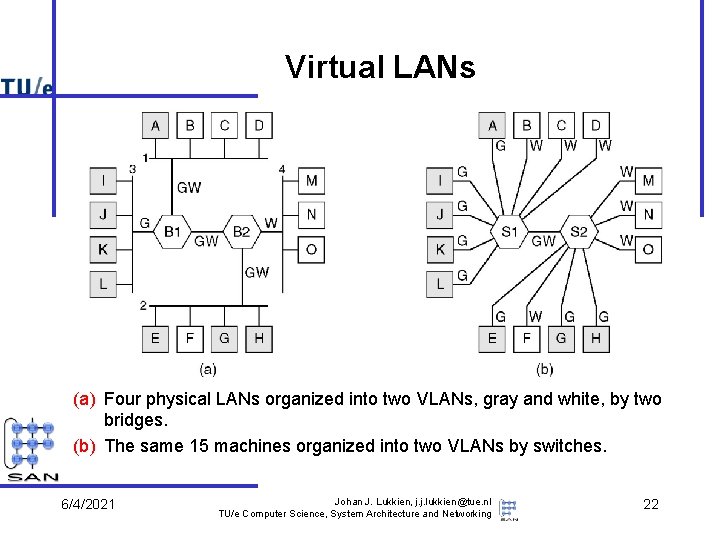
Virtual LANs (a) Four physical LANs organized into two VLANs, gray and white, by two bridges. (b) The same 15 machines organized into two VLANs by switches. 6/4/2021 Johan J. Lukkien, j. j. lukkien@tue. nl TU/e Computer Science, System Architecture and Networking 22
 Johan lukkien
Johan lukkien Johan lukkien
Johan lukkien Johan lukkien
Johan lukkien Johan lukkien
Johan lukkien 20022003 color
20022003 color Example of virtual circuit network
Example of virtual circuit network Backbone networks in computer networks
Backbone networks in computer networks Southern gas networks new connections
Southern gas networks new connections Crc in computer networks
Crc in computer networks Crc in computer networks
Crc in computer networks Traffic management in computer networks
Traffic management in computer networks Speed of a computer
Speed of a computer What is optimality principle in computer networks
What is optimality principle in computer networks In band management definition
In band management definition What is optimality principle in computer networks
What is optimality principle in computer networks Uses of computer in business
Uses of computer in business Classify computer networks based on transmission technology
Classify computer networks based on transmission technology Dns in computer networks
Dns in computer networks Diffserv vs intserv
Diffserv vs intserv Icmp in computer networks
Icmp in computer networks Web and http in computer networks
Web and http in computer networks Framing in computer network
Framing in computer network Dns in computer networks
Dns in computer networks