Computer Forensic Analysis Computer Crimes at the Computer



















- Slides: 22

Computer Forensic Analysis - Computer Crimes at the Computer - Excerpt from Investigating Computer-Related Crime By Peter Stephenson (2000) CRC Press LLC ‘“If only that [insert name of inanimate object here] could talk. ” With forensic analysis, computers can talk. And, they can tell us plenty!’ By Aaron Cheeseman

Computer Forensic Analysis Focus • The focus of this excerpt, was on the retrieval of information from a computer and techniques used by criminal investigators to gather evidence. • Content: – The ways for retrieving files and evidence from a suspects computer. – The methods used to secure and document the contents of the computer.

Computer Forensic Analysis Securing the Crime Scene • When an investigator first arrives on the scene there a few things that he would need to do. – Check for any remote connections (internet or direct) – Check devices and connections to the computer – Turn the computer off • Simply disconnect the computer

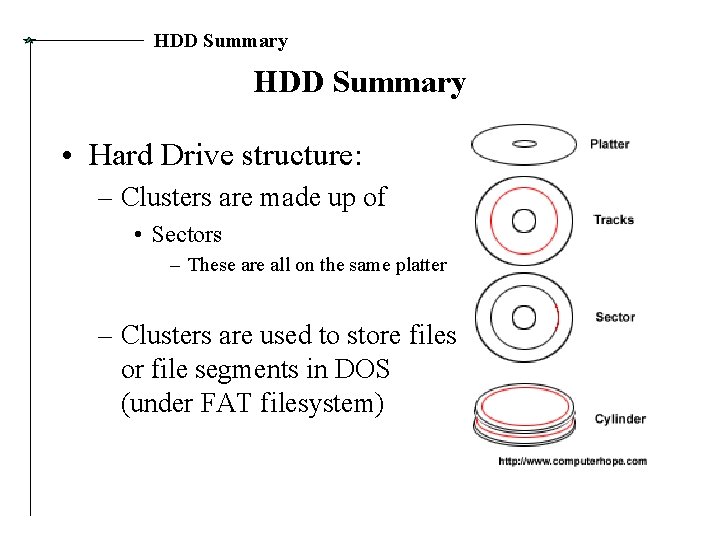
HDD Summary • Hard Drive structure: – Clusters are made up of • Sectors – These are all on the same platter – Clusters are used to store files or file segments in DOS (under FAT filesystem)

HDD Summary FAT File. System • Stores single files into separate clusters. – Clusters are usually ~ 32 k (depends size of drive). – Used in DOS / Win 95 / NT. – Has since been replaced by FAT 32 and NTFS.

DOS “Left to its own devices. DOS forgets nothing. ” • Every time you type a key on the keyboard, DOS will store the keypress. • When opening encrypted files, the plaintext will be stored on the drive somewhere. • Files are not erased when you ask them to be deleted, they are merely renamed, producing ‘unallocated space’.

DOS • Will store files contiguously (in order) until drive space fills up, then will place them where it can. • DOS can also become fragmented. This is when files and their fragments are littered across the disk space, and require multiple head reads to access the one file. – This means that the input/output time for files will be longer.

DOS • There are spaces left over, when files don’t completely fill clusters, this space is called ‘slack space. ’

Slack Space • Slack space, is the space unused by files in a cluster. – Whenever DOS clears its memory, it stores the garbage into a place on the hard drive, this is called the slack. – Slack is invisible to the file system on the local computer as there are no files in this space.

Slack Space What can we find out ? • There is a lot of information stored in ‘slack space’ this can be used to discover and uncover details about the computers activities. Such as : – – – Files (and their contents) Memory dumps Garbage Keyboard and other input / output Directory information

Slack Space e. g. Directory Information • If a floppy was in use on a computer, then the slack space can be used on the disk, instead of on the computer’s hard drive. • If directory information has been stored into the slack space on the floppy, it can be used to identify where the disk came from.

Unallocated Space • Unallocated space is the space which is used up by files which have been marked as deleted, but not actually deleted. • When DOS deletes a file, it is renamed (the first letter of the file is changed to a special character). The special character is recognized by DOS and is not displayed as a file.

Unallocated Space The Files • The files which make up this space will be entirely complete as long as no other file has been stored in its place. – When a file is stored across multiple clusters, a fragment of the file could be overwritten, but the file would still exist to be (mostly) extracted. • All the contents of this file (and the slack space around the file) are unaltered until a file is placed into the cluster.

Windows Temp Space Windows Swap Files • Usually exists in two types. – Permanent Swap Files • These would be stored for various reasons, and would remain even after rebooting. – Temporary Swap Files • This is volatile, so when windows shuts down, the information is removed or lost. • Could retain this information by disrupting the power to the computer.

Windows Temp Space Windows Swap File • The windows swap file will contain a plethora of information for the criminal investigator to discover and use. • This information includes : – Memory of running processes. – Programs when they were swapped out to disk. – Keyboard inputs.

Windows Temp Space Windows Browser Caches • The cache is where a browser stores recently accessed images and files, to allow the browser to quickly open pages that have been recently viewed • This information can be used to discover the web activities of the computer user prior to the seizure of the computer

Unix Disks Unix / *ix Operating Systems • Although Unix does not have Windows or DOS to provide it with swap files full of information, the drive may still contain information, and can contain ‘slack space’ • These operating systems have what is known as a swap drive, which is simply a partition of drive space allocated to the specific use for virtual memory, this is similar to Window’s swap space

Computer Forensic Analysis Collecting Evidence • Now that we know where to look for information, we need to know how we can look in these places, and the precautions we need to take before doing so. – As stated previously we need to ensure that there are no external connections being made to the computer which could cause information to be lost or altered. – We will also need copies made of the original data, to allow us to perform our searches.

Collecting Evidence Collecting information • The author presents tools for discovering information – Backup Software, to create a duplicate of the computer under investigation to search for evidence on. – Software to list the files and directory structure of the entire drive. – Programs to get the data from the slack and unallocated spaces. – A filtering program to search for specific keywords and filter out information which is deemed to be worthless.

Collecting Evidence e. g. Chaining • Chaining is a method used to find an entire file, (given that it does not all exist in one place) from unallocated and slack space. – In unallocated space, each sector has a pointer to the next and previous file fragments. – In slack space, given that this is continually overwritten, the file may be incomplete.

Collecting Evidence Final Steps • After the information is found, a criminal investigator has to sign and seal the evidence, as would a normal detective. • This involves: – Creating a unique fingerprint of the files or evidence that has been found. – Encryption of these new files, using a public key encryption program, with a trusted persons public key.

Computer Forensic Analysis Considerations • Times are changing in relation to computer security and privacy, in terms of hardware and software. – What effects do the larger hard drives have in terms of applying the techniques described? – Fat 32 was introduced to combat large space wastage on larger drives. Does this affect the way in which slack space can be accessed, does slack space still exist ?