Compliance EScience Mandates and Policies Sarah J White
























- Slides: 25

Compliance: E-Science Mandates and Policies Sarah J. White Director of Research Compliance Rice University April 4, 2012

Data, Who owns the Data? • This a contentious point: – Data is the life’s work of the researcher – The Institution has legal and ethical responsibilities which require custodial ownership – Unless the institution owns the data they cannot transfer it, need to consider compliance responsibilities – Data is an intangible asset (hardware is a tangible asset) – Bottom line is protection of research data is a shared responsibility

Data Sharing

Timing for data sharing • Data sharing should be timely and no later than acceptance for publication of the main findings • Data from large studies can be made available over time as data becomes available

NIH Data Sharing Policy • “Data should be made as widely and freely available as possible while safeguarding the privacy of participants, and protecting the confidential and proprietary data” – Final NIH Statement on Sharing Research Data – February 26, 2003

NIH Data Sharing Requirements • Plans must be includes in proposals which request $500 K or more per year if required in the RFA or PA: • Plans should provide a: – Schedule for data sharing – Format for the final data – Documentation – Analytical tools to be provided (is any) – Mode of data sharing

NSF Data Sharing Policy • Investigators are expected to share with other researchers, at no more than incremental cost and within a reasonable time, the primary data, samples, physical collections and other supporting materials created or gathered in the course of work under NSF grants. Grantees are expected to encourage and facilitate such sharing. See Award & Administration Guide (AAG) Chapter VI. D. 4. • Guide (GPG) Chapter II. C. 2. j for full policy implementation.

NSF Data Management Plan Requirements • Proposals submitted or due on or after January 18, 2011, must include a supplementary document of no more than two pages labeled “Data Management Plan”. This supplementary document should describe how the proposal will conform to NSF policy on the dissemination and sharing of research results.

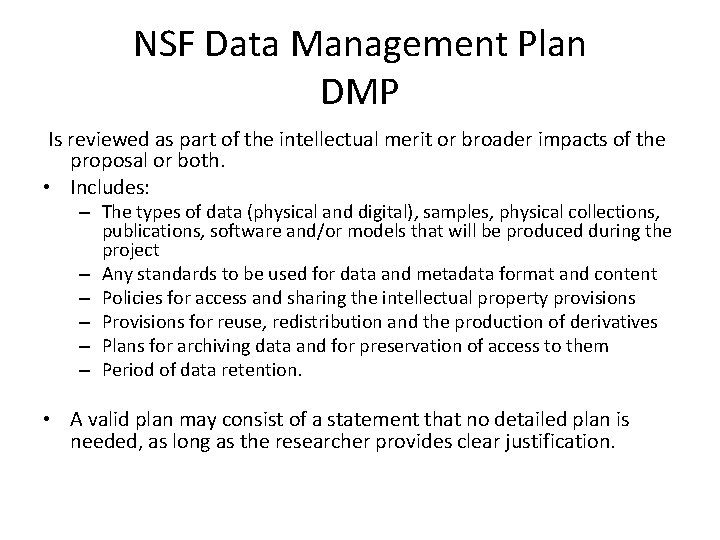
NSF Data Management Plan DMP Is reviewed as part of the intellectual merit or broader impacts of the proposal or both. • Includes: – The types of data (physical and digital), samples, physical collections, publications, software and/or models that will be produced during the project – Any standards to be used for data and metadata format and content – Policies for access and sharing the intellectual property provisions – Provisions for reuse, redistribution and the production of derivatives – Plans for archiving data and for preservation of access to them – Period of data retention. • A valid plan may consist of a statement that no detailed plan is needed, as long as the researcher provides clear justification.

Does all data need to be shared? • No--A key to working with data which involves human subjects is knowing when and how Privacy Rules apply. – HIPAA Health Insurance Portability and Accountability Act • Cannot disclose personally identifiable data • PI needs to identify the use of identifiable data in data sharing plan • Informed Consent plans must fully inform participants of the intended use of the data being collected

De-Identification of Data • Under Privacy rules the following must be removed from data sets: – Geographic information – Dates of birth, hospital admission/discharge, death – Address, e-mail, phone, SSN, license plate, or any other unique numbering – Finger prints, voice prints, photos or images

Other Data Access Issues • Freedom of Information ACT (FOIA) – Pertains to federally sponsored research – Research data may be requested under two circumstances: • It has been published in a peer reviewed scientific or technical or • The federal agency publically cites the research findings in support of an agency action • Family Educational Rights and Privacy Acts (FERPA) – Pertains to non-public student records and the data associated with them

Proprietary Data • Access to data collected may be restricted because of co-funding from private sources, or there are patent issues. • Any restrictions due to IP concerns must be identified in the data sharing plan

IP and Data • On March 16, 2013 • US Patent filing system switched from a “first to invent” to a “first inventor to file”to be in line with the rest of the world. • It will remain critical to be able to document their lab notebooks and back it up with supporting data. • Pate of the America Invents Act

Data and Copyright • Many Universities cede copyright to their faculty • Many journals require copyright ownership • Sometimes ownership of data is specified • Faculty should be aware that this is not in their best interests

Data Security

Sensitive Information Human Subjects Context • Information is considered sensitive if the loss of confidentiality, integrity, or availability could be expected to have a serious, severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals (definition from the Guide). • Guide for Identifying Sensitive Information at the NIH is intended to provide useful guidance on how to effectively identify sensitive information (including PII) and Privacy Act records. The publication suggests some insight into the complexity of identifying this type of data. While it’s not an exact science and requires some thinking on the part of the user, context is often a determining factor. • For example, a picture of an employee along with their name placed in a newsletter article recognizing their achievements is not sensitive. However, that same picture and name contained in a file named “Genetic screening results” or “Staff placed on probation” would be considered very sensitive. The same information in different contexts can make a tremendous difference in how the information needs to be protected

And Super Sensitive Unclassified Data National Security Context) • The term “sensitive but unclassified” (SBU) information was used before the terrorist attacks of September 11, 2001, even though there is no statutory definition for it. Since 9/11 more agencies have started to use • the term “SBU, ” or some variant of it, and to implement security systems to identify • and protect nonclassified information whose release might benefit terrorists • Department of Homeland Security: agriculture, chemical, biological, nuclear and radiological, cyber terrorism and the behavioral aspects of terrorism

Export Control • Although most research conducted at Universities will fall under the fundamental research exemption • The PI must comply with any restrictions pertaining to US laws and regulations controlling the export of: – Technical data – Computer software – Laboratory prototypes used in connection with their research

Fundamental Research Exemption • Basic and applied research in science and engineering, the results of which ordinarily are published and shared broadly within the scientific community, as distinguished from proprietary research and from industrial development, design, production, and product utilization, the results of which ordinarily are restricted for proprietary or national security reasons.

Export Control • Despite these generally useful exclusions, some university activities remain subject to export control. The following are examples of common situations in which these exclusions or exemptions will not apply. 1. Restricted Projects 2. Certain Federal Sponsors 3. International Travel 4. Sponsor of 3 rd party proprietary items or technical data 5. Physical exports 6. Deliverables to a foreign sponsor 7. Use, transfer, or development of a controlled item or technical data

(Your can’t) take it with you • The applicability of export control regulations will depend the following: – country(ies) you will be visiting; – what you'll be taking with you or sending to support your work; – what you will be doing abroad; and – who you will be working with.

Data Retention Okay, I’m done • Not so fast…. – How and when can you dispose of data? • Term is usually stipulated for sponsored research 3 years after the funding period ends for federal sponsors and 4 -6 years for state sponsors • University policy may stipulate a longer time frame • PI should make the determination after the minimum term expires • Some stricter guidelines depending upon the type of data; • FDA has longer timelines as well

Destroying Data • Best practices ensure that the data cannot be reconstructed.

Comments and Questions? Thank You!
 Gad laws and mandates
Gad laws and mandates Pronombres con mandatos
Pronombres con mandatos Fda data integrity presentation
Fda data integrity presentation Acrostic poem of english
Acrostic poem of english Ellen white biography
Ellen white biography Security program and policies principles and practices
Security program and policies principles and practices Recruitment selection and induction
Recruitment selection and induction Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Red green blue brown
Red green blue brown Manuel roxas contribution in the philippines
Manuel roxas contribution in the philippines National policies related to child health and welfare
National policies related to child health and welfare Classroom policies and procedures
Classroom policies and procedures Lending policies and procedures managing credit risk
Lending policies and procedures managing credit risk Trade and investment policies
Trade and investment policies Accounting principles and concepts
Accounting principles and concepts Chapter 11 school policies and their functions
Chapter 11 school policies and their functions Importance of policy and procedures
Importance of policy and procedures Policies and procedures presentation
Policies and procedures presentation Configuration policies and procedures
Configuration policies and procedures Objectives of hrm
Objectives of hrm What are hr policies
What are hr policies Human resource policy
Human resource policy Mughal dynasty
Mughal dynasty