Comodo Dome Data Protection What is Data Loss




- Slides: 14

Comodo Dome Data Protection

What is Data Loss ? Definition of Data Loss Prevention DLP solution is a system that is designed to detect potential data breach incidents in timely manner and prevent them by monitoring data while in-use (endpoint actions), in-motion (network traffic), and at -rest (data storage). © 2017 Comodo Group, Inc. All rights reserved. 2 2

What is Comodo Data Protection ? 4 Comodo Data Protection is an all-in-one data loss prevention software that runs with multi-site configurations on network servers and endpoint computers. CDP collects data and categorizes it in one of three vectors - Data in Motion, Data at Rest and Data in Use. 4 Comodo Dome Data Protection helps ensure regulatory compliance, controls who can access and move information, preventing data loss. © 2017 Comodo Group, Inc. All rights reserved. 3 3

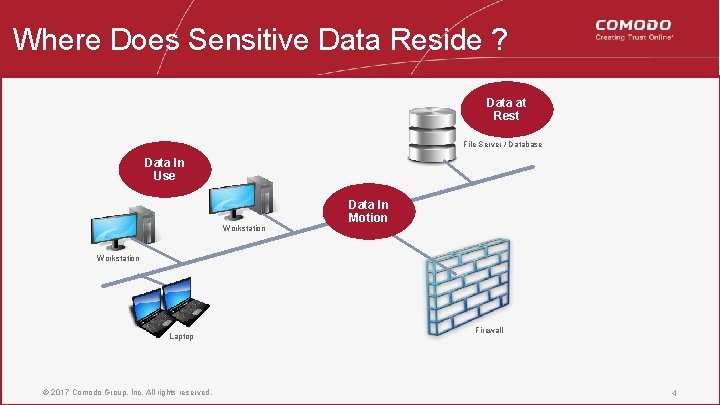
Where Does Sensitive Data Reside ? Data at Rest File Server / Database Data In Use Workstation Data In Motion Workstation Laptop © 2017 Comodo Group, Inc. All rights reserved. Firewall 4 4

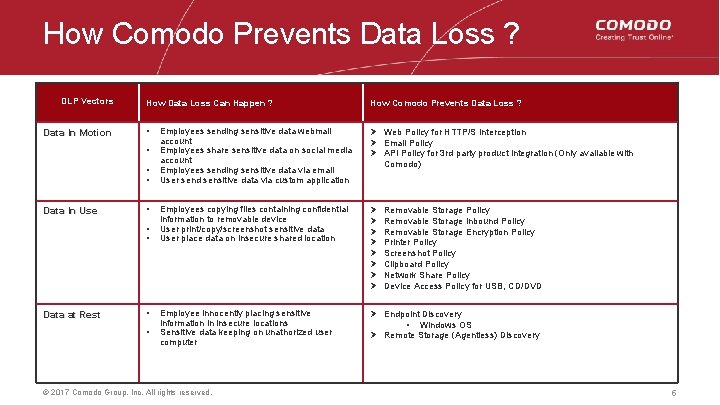
How Comodo Prevents Data Loss ? DLP Vectors Data In Motion How Data Loss Can Happen ? How Comodo Prevents Data Loss ? • Employees sending sensitive data webmail account Employees share sensitive data on social media account Employees sending sensitive data via email User send sensitive data via custom application Ø Web Policy for HTTP/S Interception Ø Email Policy Ø API Policy for 3 rd party product integration (Only available with Employees copying files containing confidential information to removable device User print/copy/screenshot sensitive data User place data on insecure shared location Ø Ø Ø Ø Employee innocently placing sensitive information in insecure locations Sensitive data keeping on unathorized user computer Ø Endpoint Discovery • Windows OS Ø Remote Storage (Agentless) Discovery • • • Data In Use • • • Data at Rest • • © 2017 Comodo Group, Inc. All rights reserved. Comodo) Removable Storage Policy Removable Storage Inbound Policy Removable Storage Encryption Policy Printer Policy Screenshot Policy Clipboard Policy Network Share Policy Device Access Policy for USB, CD/DVD 5 5

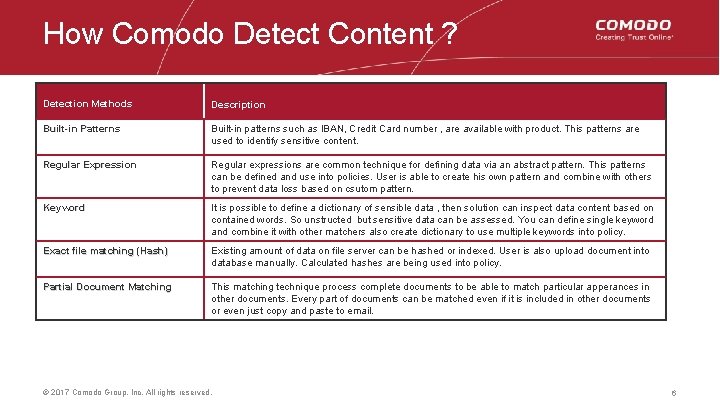
How Comodo Detect Content ? Detection Methods Description Built-in Patterns Built-in patterns such as IBAN, Credit Card number , are available with product. This patterns are used to identify sensitive content. Regular Expression Regular expressions are common technique for defining data via an abstract pattern. This patterns can be defined and use into policies. User is able to create his own pattern and combine with others to prevent data loss based on csutom pattern. Keyword It is possible to define a dictionary of sensible data , then solution can inspect data content based on contained words. So unstructed but sensitive data can be assessed. You can define single keyword and combine it with other matchers also create dictionary to use multiple keywords into policy. Exact file matching (Hash) Existing amount of data on file server can be hashed or indexed. User is also upload document into database manually. Calculated hashes are being used into policy. Partial Document Matching This matching technique process complete documents to be able to match particular apperances in other documents. Every part of documents can be matched even if it is included in other documents or even just copy and paste to email. © 2017 Comodo Group, Inc. All rights reserved. 6 6

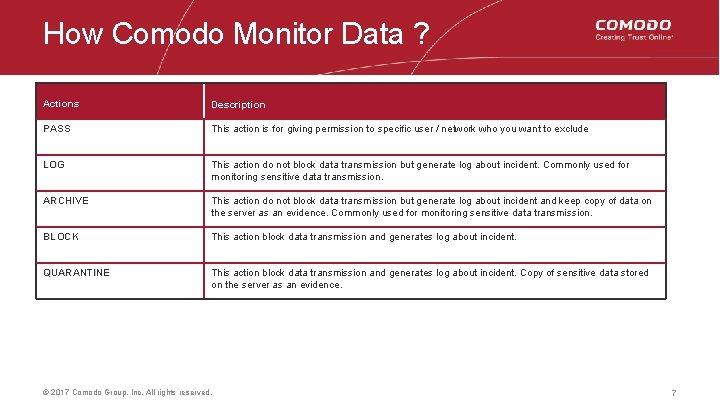
How Comodo Monitor Data ? Actions Description PASS This action is for giving permission to specific user / network who you want to exclude LOG This action do not block data transmission but generate log about incident. Commonly used for monitoring sensitive data transmission. ARCHIVE This action do not block data transmission but generate log about incident and keep copy of data on the server as an evidence. Commonly used for monitoring sensitive data transmission. BLOCK This action block data transmission and generates log about incident. QUARANTINE This action block data transmission and generates log about incident. Copy of sensitive data stored on the server as an evidence. © 2017 Comodo Group, Inc. All rights reserved. 7 7

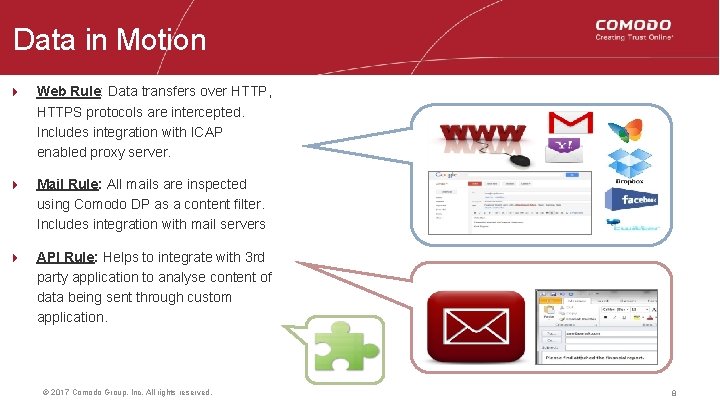
Data in Motion 4 Web Rule: Data transfers over HTTP, HTTPS protocols are intercepted. Includes integration with ICAP enabled proxy server. 4 Mail Rule: All mails are inspected using Comodo DP as a content filter. Includes integration with mail servers 4 API Rule: Helps to integrate with 3 rd party application to analyse content of data being sent through custom application. © 2017 Comodo Group, Inc. All rights reserved. 8 8

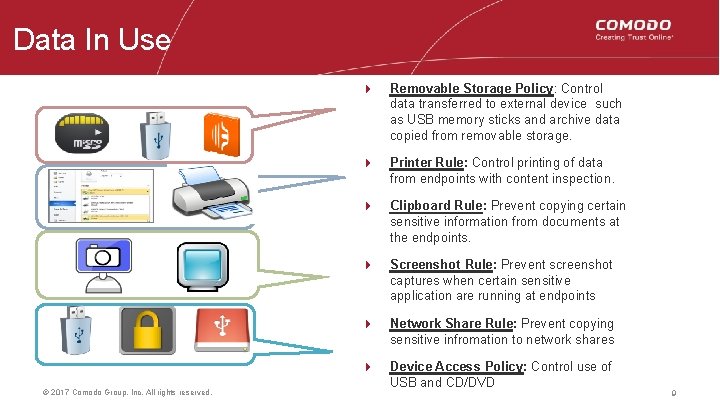
Data In Use © 2017 Comodo Group, Inc. All rights reserved. 4 Removable Storage Policy: Control data transferred to external device such as USB memory sticks and archive data copied from removable storage. 4 Printer Rule: Control printing of data from endpoints with content inspection. 4 Clipboard Rule: Prevent copying certain sensitive information from documents at the endpoints. 4 Screenshot Rule: Prevent screenshot captures when certain sensitive application are running at endpoints 4 Network Share Rule: Prevent copying sensitive infromation to network shares 4 Device Access Policy: Control use of USB and CD/DVD 9 9

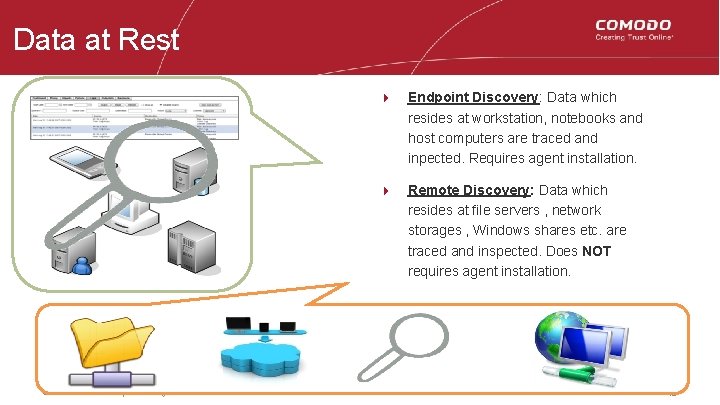
Data at Rest 4 Endpoint Discovery: Data which resides at workstation, notebooks and host computers are traced and inpected. Requires agent installation. 4 Remote Discovery: Data which resides at file servers , network storages , Windows shares etc. are traced and inspected. Does NOT requires agent installation. © 2017 Comodo Group, Inc. All rights reserved. 10 10

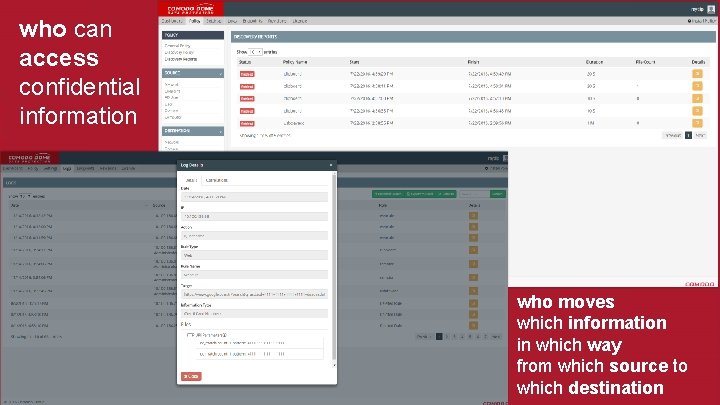
who can access confidential information who moves which information in which way from which source to which destination

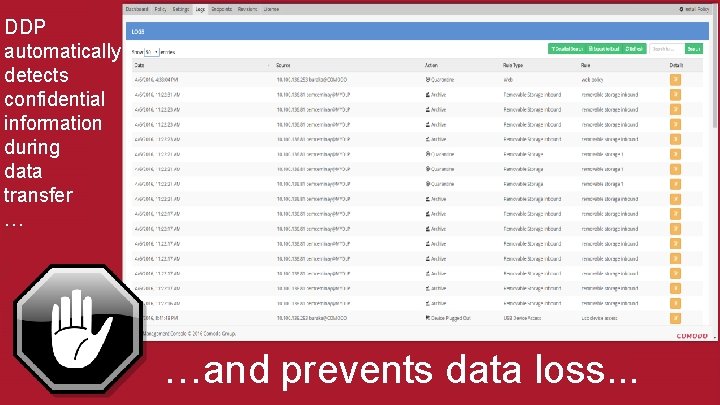
DDP automatically detects confidential information during data transfer … …and prevents data loss. . .

Why Comodo Data Protection ? 4 Easy implement without large upfront investments. Installed as on-prem or cloud environment such as AWS. 4 All-in one solution, provides a broad set of features for managing a multitude channels within a single solution 4 No Third Party License is required for installation such as MS SQL 4 Provides DLP functionality to custom application with API feature which is only available with Comodo Data Protection to analyse content of data transmitted over custom application. 4 Block or quarantine outgoing confidential data from your organization network via mail and web. Archive or Quarantine suspicious files. 4 Monitor removable device usage in your organization and block or quarantine confidential files copied onto these devices such as USB memory sticks 4 Monitor data movement stemming from actions taken by end users on their workstations. Monitor and prevent data loss through endpoint channels Clipboard, Removable Storage, Printer, Network Share 4 Discover confidential data on network storages, databases, workstations and laptops in your organization. © 2017 Comodo Group, Inc. All rights reserved. 13 13

Dome Data Protection Benefits 4 Protect sensitive business data and intellectual property 4 Reduce the data breach risk 4 Enhance training and awarness 4 Improve compliance 4 Improves incident response capabilities, helps organizations to respond effectively in the event of data loss © 2017 Comodo Group, Inc. All rights reserved. *Terms & conditions apply 14 14